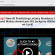
F-secure labs have found a phishing scam exploiting this vulnerability. This scam works by sending out emails, urging customers of the global HSBC bank to visit a site called www[dot]jhsbc[dot]com. This domain, naturally, has nothing to with the real bank but it sounds close enough.
The site is running on a owned home computer somewhere in Illinois. This machine, connected to the net via a high-speed cable connection, is hosting or has been hosting several other phishing-related domains, including these gems that administrators might want to filter at their gateways: www[dot]i7tgg4rv[dot]com and www[dot]ll67ffgsp[dot]com, www[dot]mrhpd74e[dot]com and www[dot]pph4e32q[dot]com.
The WMF connection comes from the fact that if you visit this site (and please don’t), the front page contains an IFRAME that will try to push an exploit file called tr.wmf to your system. When that is executed, it will download a file called update.exe from the same server. This unexpected gift turns out to be a variant of the Trojan-Spy.Win32.Goldun family, which will start to collect information from the system.