Websense® Security Labs™ has received reports of a malicious website, which is hosting a Trojan Horse keylogger. This keylogger is designed to steal end-user information for popular online games. The malicious code’s filename is main_n80.scr and was discovered on a site, which appears to be a fraudulent version of the Nokia Taiwan website.
The site uses a cousin domain name and simply has an image screenshot of the real Nokia Taiwan website. It is hosted in Hong Kong and appears to have been registered with fraudulent information.
The main_80.scr file is an SFX self-extracting executable file that contains four files:
* download.exe
* winlogin.exe
* server.exe
* error.jpg
When the main_80.scr file is executed, it will use download.exe to copy the extracted files to the system32 dir and execute its version of run32dll.exe. The rundll32.exe file will show error.jpg. Once the user closes the .jpg file,rundll32.exe will execute the rest of the extracted .exe files.
These extracted .exe files modify the registry, as detailed below, to ensure that it starts on restart, and checks for the existence of the application Lineage.
* Modifies or creates files and stores in system32 directory
* Kerne0110.exe is a copy of winlogin.exe
* Rundll32.exe is a copy of download.exe
* gg.bat is created
* _2dll.dll is created
* microsoftie0110.dll is created
* msabc.dll is created
* pKerme123.dll is created
* RegistryInfo.dll is created

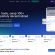









Evidence of a website that appears to be hosting a malicious keylogger trojan horse
Trojan horses (software that includes “features” that may work against the user’s intentions) are hardly…
Thanks for the interesting website – keep up the good work.
Trojan report.
Just picked up the following warning:
Websense® Security Labs™ has received reports of a malicious website, which is hosting a Trojan Horse keylogger. This keylogger is designed to steal end-user information for popular online games. The malicious…