A new piece of ransomware, called Ransom.a by most AV vendors, has been spotted in the wild.
Evidence received so far suggests that this Trojan can be found on P2P networks.
The malware poses as a Windows Mobile application, despite that description it will only work on Win32.
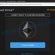
When the user is infected and reboots his machine, he will be greeted with a full screen message when he logs on.
The screen tries its best to stay on top of all windows and is highly annoying, it also shows pornographic images.
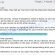
The message which is presented to the user is quite long, but in short:
Pay $10.99 via Western Union otherwise you will keep getting this screen.
One file per 30 minutes will be deleted from the hard drive. Deleted files will be restored when you have paid up and entered the proper unlock code.
Antivirus software can not detect this virus, nor can it detect the hidden folders in which the deleted files are stored.
When entering a false unlock code there’s also a message stating that the hard drive will crash in 3 days.
However there’s a catch: None of these destructive routines actually work!
I think we have an interesting development going on here, I think there are two different types of ransomware.
Real ransomware, which encrypts your data or does other nasty stuff.
And malware which claims to do all sorts of nasty stuff but actually doesn’t. It’s bluffing, like bluff poker.
How is an average user going to check if all of his files are still there? He’s not.
Losing a file every 30 minutes is a scary thought, made up by the criminal in an effort to pressure the user to act quickly and pay up.
Ransomware has gotten quite some media attention and now criminals are trying to simply bluff people into giving up their money, instead of having to write difficult code.
I just hope that people have remembered the most important thing about ransomware: Do not pay up, contact AV vendors for help.