 TDSS trojan also known as Backdoor.Tidserv [PCTools], Backdoor.Tidserv.I!inf [Symantec], Rootkit.Win32.TDSS.y [Kaspersky Lab], Patched-SYSFile.a [McAfee], Mal/TDSSRt-A [Sophos], Virus:Win32/Alureon.F [Microsoft] is very dangerous. It installs onto your computer through a vulnerability in an already installed programs (mostly in InternetExplorer) or with the help of a rogue antispyware programs. Trojan TDSS uses rootkit-specific techniques designed to hide the software presence in the system. It is practically not detected by standard means Windows, you will not find its files on the disk, as well as writing about it in the Windows registry.
TDSS trojan also known as Backdoor.Tidserv [PCTools], Backdoor.Tidserv.I!inf [Symantec], Rootkit.Win32.TDSS.y [Kaspersky Lab], Patched-SYSFile.a [McAfee], Mal/TDSSRt-A [Sophos], Virus:Win32/Alureon.F [Microsoft] is very dangerous. It installs onto your computer through a vulnerability in an already installed programs (mostly in InternetExplorer) or with the help of a rogue antispyware programs. Trojan TDSS uses rootkit-specific techniques designed to hide the software presence in the system. It is practically not detected by standard means Windows, you will not find its files on the disk, as well as writing about it in the Windows registry.
When installed, it will be configured to start automatically when Windows starts. While is running, TDSS (Backdoor.Tidserv, Alureon) trojan may:
- display a lot of popups and fake security alerts
- hijack Internet Explorer
- redirect search results in Google, Yahoo, MSN to non related sites
- block an access to security websites
- disable Windows Task Manager, Windows Security Center and Registry editor
What is more, TDSS, Backdoor.Tidserv, Alureon trojan blocks the ability to run a lot of antivirus and antispyware programs, including Malwarebytes Anti-Malware. Also it is usually installed in conjunction with a rogue antispyware programs.
If your computer is infected with the trojan, then use these removal instructions below, which will remove TDSS, Backdoor.Tidserv, Alureon trojan and any associated malware for free.
Symptoms in a RootRepeal Log
Hidden Services
——————-
Service Name: H8SRTd.sys
Image Path: C:\WINDOWS\system32\drivers\H8SRTnfvywoxwtx.sys
Service Name: _VOIDd.sys
Image PathC:\WINDOWS\system32\drivers\_VOIDaabmetnqbf.sys
Use the following instructions to remove TDSS, Backdoor.Tidserv, Alureon trojan.
1. Use TDSSKiler by Kaspersky lab to detect and remove a rootkit.
2. Use Malwarebytes Anti-malware to remove TDSS, Backdoor.Tidserv, Alureon rootkits associated malware.
1. Use TDSSKiler by Kaspersky lab to detect and remove the TDSS rootkit.
Download TDSSKiller from th link above.
Right click to it and select Extract all. Follow the prompts.
Open TDSSKiller folder. Double click the TDSSKiller icon to run it. You will a screen like below.

Click Start scan button to start scanning and disinfection process. Once the process is complete, your computer will be rebooted.
2. Use Malwarebytes Anti-malware to remove TDSS, Backdoor.Tidserv, Alureon rootkits associated malware.
Download MalwareBytes Anti-malware from the following link.
MalwareBytes Anti-malware download link.
Close all programs and Windows on your computer. Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
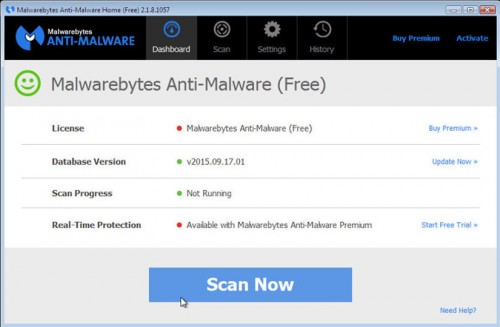
Click Scan Now button. It will start scanning your computer for TDSS, Backdoor.Tidserv, Alureon infection associated malware. This procedure can take some time, so please be patient.
When the scan is complete you will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
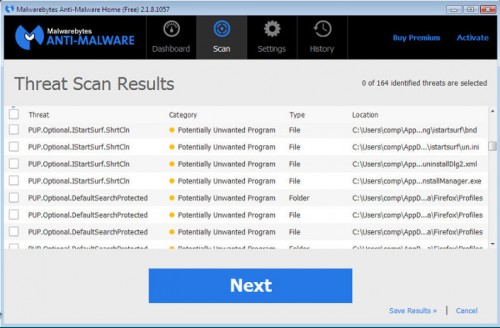
Make sure that everything is checked, and click Remove Selected for start TDSS, Backdoor.Tidserv, Alureon associated malware removal process. When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
TDSS, Backdoor.Tidserv, Alureon trojan creates the following files:
C:\Windows\System32\TDSS[RANDOM CHARACTERS].tmp
C:\Windows\System32\drivers\TDSS[RANDOM CHARACTERS].sys
C:\Windows\System32\TDSS[RANDOM CHARACTERS].sys
C:\Windows\System32\TDSS[RANDOM CHARACTERS].dat
C:\Windows\System32\TDSS[RANDOM CHARACTERS].log
C:\Windows\System32\TDSSserv.sys
C:\Windows\System32\TDSSerrors.log
C:\Windows\System32\TDSSservers.dat
C:\Windows\System32\TDSSl.dll
C:\Windows\System32\TDSSlog.
C:\Windows\System32\TDSSmain.dll
C:\Windows\System32\TDSSinit.dll
C:\Windows\System32\TDSSlog.dll
C:\Windows\System32\TDSSadw.dll
C:\Windows\System32\TDSSpopup.dll
TDSS, Backdoor.Tidserv, Alureon trojan creates the following registry keys and values
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\connections
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\disallowed
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\injector
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\versions
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\TDSSserv.sys






 (Quick & Easy) in 2024
(Quick & Easy) in 2024

THANK YOU!!!!
after downloading every other software known to man, i found this site. followed your easy to follow instructions and with the help of Avenger/Malware i got rid of “spyware protect 2009”. i really appreciate your time and effort you have put into this!
my sanity…..you saved it
Thanks for the fix! You said their goal was to trick us into buying their fake antispyware right? So why can’t we track where the money is sent to and catch them?
i use Stopzille and it find Vundo.p How can i remove it?
Derek, its not simple task. They use offshore billing.
AJ, if your computer infected with trojan Vundo, then follow these steps.
LOOKS GOOD
i LIKE IT
Love you man!
Very straight forward.
Thank you so much. My pc got so jammed up I couldnt download Avanger or Malware. So I downloaded them to a USB memory stick on another PC and then booted them on the infected PC from stick… Brilliant got on and followed your excellent instructions. Now working again properly.
Thank you very much for sharing!
-Rondo-
from Budapest (HUNGARY)
Ok, I took everything written above into account, downloaded mbam and spyware doctor (mbam finds nothing, spyware doc finds Trojan.TDSServ but is completely incapable of fixing it). Interesting thing is that there are no drivers to disable at all (in no plug n play drivers). I even did full win xp reinstall afterwards (formatted C only though, other two partitions were left as before – is that the trick?). Anyway, after reinstall I still can`t acess disks through shortcuts (says something like cannot find RECYCLER\\S-8-3-79-10009757-100013345-100016285-5959.com), though explore works on them nicely though. Spyware doc still detects same trojan. All this happens on another desktop that has no link to the internet, but my computer does so I downloaded programs and installed them on that machine using USB stick.
How can this thing be so persistent? I`m thinking about completely replacing that machune`s HDD with a new one (it is only 80Gb and quite old). Just don`t tell me that this stupid Trojan hides itself on the motherboard through some incredible hacker`s magic…
Anyway, some info can be useful, and well, I`m mostly interested if full format of all 3 partitions can remove that pest. Luckily, that other machine was mostly gaming desktop, so it didn`t have much in a way of important data…
Looks like your computer was reinfected with autorun.inf trojan (probably you have attached infected usb drive). Please follow these steps.
It was actually a innocent looking keygen that caused the infection. And about steps to solution…there are no drivers (in non plug n play drivers), avenger reports an error (could not set driver image path) after reboot in txt file, then computer reboots itself all of a sudden (really fast after i see avenger`s report) BUT!, mbam finds 2 infections afterward and i removed them…do I have to manually remove those %system%TDsomething files too? (where to find them anyway?)
Yeah I found where those files on the list are supposed to be, and there are none of those listed in step 3…mbam supposedly removed infections, but spyware doc still reports them. Also, now it sometimes reports that it blocked access attempt to some Trojan-PWS.Bancos.PWN…
What is going on? The TDSServ that I`m tampering with, is like some ghost version, I can`t find any drivers or files mentioned in steps 1 and 3…Symptoms persist. Just tell me if full disk format will do the trick, it is perfectly viable option for me.
Rexus, please follow these steps. I will check you computer.
hi there, it’s been a while now that i get this TDSSERV thing coming back everyday and i keep deleting it, i get registry entries that keeps coming back, none of the files listed in step 1 and step 3 are present… please help!
DrumHeadz83, please follow these steps.
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 8:21:51 AM, on 2/4/2009
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v7.00 (7.00.6000.16762)
Boot mode: Normal
…
DrumHeadz83, please make a new topic at Spyware removal forum and include your HijackThis log in to your message.
It would seem that blasted thing is removed; machine is working without problems for several days now…seems that mbam combined with spyware doc fixed it, though I still can`t acess disk partitions via shortcuts (must use explore). Other than that, it`s OK. Oh, and I did have an infected USB (ended up in trash can, it`s several years old 256 mb stick) that I used to transfer stuff to the other computer… lack of antivirus program on that machine complicated things. Anyway if things go haywire again I`ll post HijackThis log on the forum…thanks for the help
Okay. So again what if the list of files/drivers given at the top aren’t listed? This is frustrating. Why does nobody simply tell you what files are to be found instead of saying …
Leech, looks like a new version of TDSSserv trojan is not listed in the drivers list. Skip step 1 and go to step2 or follow these steps.
Thanks for the great help, one new thing to add, rename the installer .exe and the program .exe to a random name.exe of the Malware’s util
I’m trying to follow this procedure but fail at the first step as I can’t access the device manager. When I ‘right click’ my computer I can click the properties section but nothing happens so I can’t even do step one. Any help would be great as this is getting horrendous. Thanks
Paul, skip first step.
Everythings going fine apart from needing to purchase MalwareremovalBot, now I’ve got no qualms about doing that but for some reason my payment can’t be processed so I’m stuck again. is there a free trial version I can use?
MalwareremovalBot is not Malwarebytes Anti-malware. When you have opened Malwarebytes Antimalware page, then scroll down for a download link.
My bad, I’ve d/l the proper one & its fixed some problems but there’s still nothing in the control panel
I’ve pasted a hijackthis log here http://myantispyware.com/forum/post6344.html#6344
Any help would be greatly accepted, thanks
Very strange I post here & it appears that I’ve double posted but my posts disappear until I post a new one then they all show up again (until I visit the page again & they’ve gone again)
We have gotten to the point where the malwarebytes is to remove the offenses but it wants us to buy the program to do so. Did the rest of you have to buy the $30 program to remove this mess?
Anna, you have made a mistake, looks like you have downloaded a Malwareremovalbot, its not Malwarebytes Anti-malware. When you have opened Malwarebytes Anti-malware page, then scroll down for a download link.