 InSysSecure is a rogue antispyware program that installed through the use of trojans which usually pretend to be flash player updates or even video codecs required to watch a video online.
InSysSecure is a rogue antispyware program that installed through the use of trojans which usually pretend to be flash player updates or even video codecs required to watch a video online.
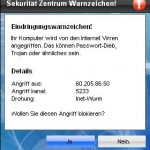
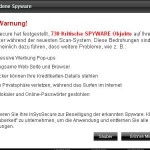
Once started, the trojan will download and install the rogue onto your computer and configure it to run automatically when your PC loads. The trojan will also create numerous fake “infected” files in Windows folder with random names, which later during the scan, InSysSecure will determine as worms, trojans, spyware and malware. Then it will ask you to pay for a full version of the program to remove them. However, this is a scam, all of these infections cannot harm you computer! InSysSecure displays the false scan result to scare you into think that your computer in danger.
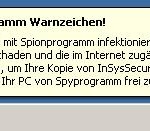
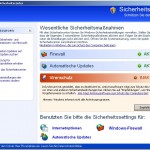
What is more, the installer of InSysSecure will download and install a trojan FakeAlert. Once running, the trojan will display a fake Windows Security Center and numerous fake security alerts from Windows task bar. Of course, all of these alerts are fake and like false scan results should be ignored! InSysSecure is unable to detect or remove any infections nor will be protect you from legitimate future threats. The program is designed with one purpose to trick you into purchasing so-called “full” version of the software.
If you find that your computer is infected with this malware, please use the removal guide below to remove InSysSecure from your computer for free.
More screen shoots of InSysSecure
Symptoms in a HijackThis Log
O4 – HKLM\..\Run: [InSysSecure] C:\Program Files\InSysSecure Software\InSysSecure\InSysSecure.exe
O4 – HKCU\..\Run: [
Use the following instructions to remove InSysSecure (Uninstall instructions)
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
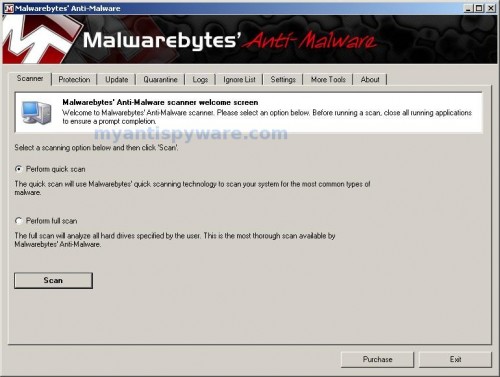
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer for InSysSecure infection. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
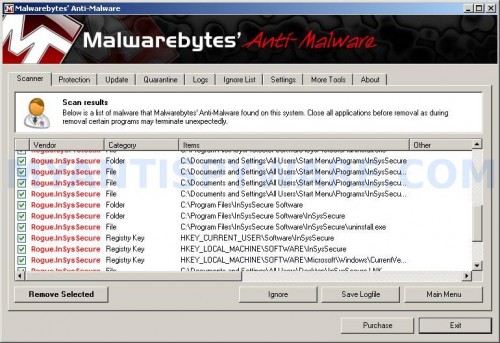
Malwarebytes Anti-malware, list of infected items
Make sure that everything is checked, and click Remove Selected for start InSysSecure removal process. When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
InSysSecure creates the following files and folders
C:\Documents and Settings\All Users\Start Menu\Programs\InSysSecure
C:\Program Files\InSysSecure Software
C:\Program Files\InSysSecure Software\InSysSecure
C:\Program Files\InSysSecure Software\InSysSecure\InSysSecure.exe
C:\WINDOWS\system32\
C:\Documents and Settings\All Users\Start Menu\Programs\InSysSecure\1 InSysSecure.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\InSysSecure\2 Homepage.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\InSysSecure\3 Uninstall.lnk
C:\Program Files\InSysSecure Software\InSysSecure\uninstall.exe
C:\Documents and Settings\All Users\Desktop\InSysSecure.LNK
InSysSecure creates the following registry keys and values
HKEY_CURRENT_USER\Software\InSysSecure
HKEY_LOCAL_MACHINE\SOFTWARE\InSysSecure
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\InSysSecure
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\









 (Quick & Easy) in 2024
(Quick & Easy) in 2024


