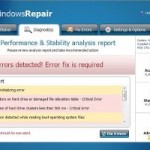
 Windows Restore is a malicious program that pretends to be a computer defragmenter and system analysis software. It hijacks your computer, blocks Windows legitimate applications from running, presents various fake critical errors alerts that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Do not pay for the bogus software! Simply ignore all that it will display you and remove Windows Restore from your computer as quickly as possible!
Windows Restore is a malicious program that pretends to be a computer defragmenter and system analysis software. It hijacks your computer, blocks Windows legitimate applications from running, presents various fake critical errors alerts that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Do not pay for the bogus software! Simply ignore all that it will display you and remove Windows Restore from your computer as quickly as possible!
Windows Restore from same family of malware as Windows Repair, Windows Recovery, Windows Diagnostic, Windows Disk, etc which has already caused much damage to many computes. It is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software. Moreover, the scammers may also distribute this malware on Twitter, My Space, Facebook, and other social networks. Remember, “Windows Restore” name is only a trick. Cyber criminals uses legitimate names in order to get trust from computer users as most of them do not pay attention to what they download from the Internet. Thus, please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC.
When WindowsRestore is installed, it will state that your computer has some critical problems. It will imitate a scan computer`s hard disks, Windows registry and computer memory for errors. The rogue will report that “Read time of hard drive clusters less than 500 ms”, “32% of HDD space is unreadable”, “Bad sectors on hard drive or damaged file allocation table”, etc. The scan look legitimate, but you should never trust anything that the fake diagnostic tool will display you. Remember, all of these errors are a fake! So, simply ignore the false scan results.
Windows Restore will block legitimate Windows applications on your computer and won’t let you download anything from the Internet. Last, but not least, the rogue will display numerous fake warnings and nag screens. Some of the warnings are:
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Windows – No Disk
Exception Processing Message 0×0000013
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Of course, all of these warnings are a fake. This is an attempt to make you think your computer in danger. Like false scan results you can safely ignore them.
What is more, Windows Restore hides the folders on your system drive (disk C by default). To see your files and folders again, you need to open Folder options (Windows Vista/7: Organize->”Folder and search options”->View tab; Windows 2000/XP: Tools->Folder Options->View tab). Select “Show hidden files and folders” option and click OK button.
As you can see, WindowsRestore is a totally scam, which created with one purpose to scare you into purchasing so-called “full” version of the program. Most important do not purchase it! Please use the removal guide below in order to remove Windows Restore and any associated malware from your computer for free. If you have already purchase the program, contact your credit card company and tell them what has happened.
Automated Removal Instructions for Windows Restore
Step 1. Reboot your computer in Safe mode with networking
Restart your computer.
After hearing your computer beep once during startup, start pressing the F8 key on your keyboard. On a computer that is configured for booting to multiple operating systems, you can press the F8 key when the Boot Menu appears.
Instead of Windows loading as normal, Windows Advanced Options menu appears similar to the one below.
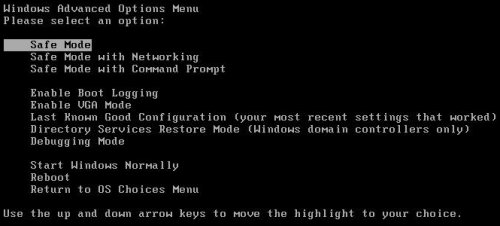
Windows Advanced Options menu
When the Windows Advanced Options menu appears, select Safe mode with networking and then press ENTER.
Step 2. Stop Windows Restore from running
Download HijackThis from here. Run HijackThis.
Note: if you cannot run HijackThis, then re-download it, but before saving, in the Save dialog, rename HijackThis.exe to iexplore.exe and click Save button to save it to desktop.
Click Scan button to perform a system scan. Once scan in complete, place a checkmark against each of lines:
O4 – HKCU\..\Run: [{RANDOM}.exe] %CommonAppData%\{RANDOM}.exe
O4 – HKCU\..\Run: [{RANDOM}] %CommonAppData%\{RANDOM}.exe
Example:
O4 – HKCU\..\Run: [CvdCEPoYRb.exe] C:\DOCUME~1\ALLUSE~1\APPLIC~1\CvdCEPoYRb.exe
O4 – HKCU\..\Run: [SaMFLunm] C:\DOCUME~1\ALLUSE~1\APPLIC~1\SaMFLunm.exe
O4 – HKCU\..\Run: [SaMFLunm] C:\ProgramData\SaMFLunm.exe
Note: list of infected items may be different. Template of the malicious entries:
Variant 1: O4 – HKCU\..\Run: [{random string}] %CommonAppData%\{random string}.exe;
Variant 2: O4 – HKCU\..\Run: [{random string}.exe] %CommonAppData%\{random string}.exe;
%CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista).
If you unsure, then check it in Google. Skip this step, if you does not find any malicious lines.
Place a checkmark against each of them. Once you have selected all entries, close all running programs then click once on the “fix checked” button. Close HijackThis.
Step 3. Clean Windows temp folder
WindowsRestore may store its files in Windows temp folder. You need to clean the folder manually or automatically using ATF-Cleaner (the program is used to cleanout temporary files & temp areas used by Windows and internet browsers).
Please download ATF Cleaner by Atribune from here, saving it to your desktop. Start ATF-Cleaner.exe to run the program.
Under Main choose: Select All and click the Empty Selected button.
Step 4. Remove Windows Restore associated malware
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
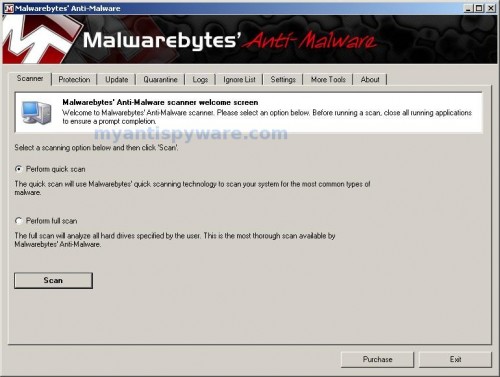
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer for Windows Restore associated malware. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
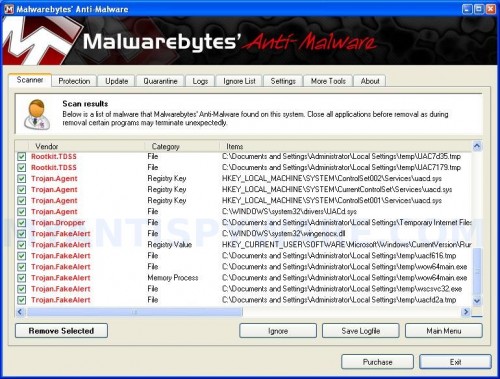
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove Windows Restore. MalwareBytes Anti-malware will now remove all of associated WindowsRestore files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Windows Restore removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Windows Restore creates the following files and folders
%UserProfile%\Desktop\Windows Restore.lnk
%UserProfile%\Start Menu\Programs\Windows Restore\Windows Restore.lnk
%UserProfile%\Start Menu\Programs\Windows Restore\Uninstall Windows Restore.lnk
%CommonAppData%\{RANDOM}.exe
%CommonAppData%\{RANDOM}
%CommonAppData%\{RANDOM}.dat
Note: %CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista)
Windows Restore creates the following registry keys and values
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | {RANDOM}
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | {RANDOM}.exe










Thanks for your help! The folksnwho put this stuff on our pcs need to be caught and prosecuted or worse! It looks lime u saved me a trip to the “geek squad”. Thanks!!!!