 XP Antivirus 2012 is a rogue antispyware program from the same family of malware as XP Anti-Virus 2011, etc. The program is installed via trojans without your permission and knowledge and uses misleading methods such false scan results and fake security warnings in order to trick you into purchasing its paid version. Thus, do not trust anything that this malware will display you and remove XP Antivirus 2012 from your system as soon as possible. Read below what you’ll want to know though is what does this malware do and how to remove it from your PC for free.
XP Antivirus 2012 is a rogue antispyware program from the same family of malware as XP Anti-Virus 2011, etc. The program is installed via trojans without your permission and knowledge and uses misleading methods such false scan results and fake security warnings in order to trick you into purchasing its paid version. Thus, do not trust anything that this malware will display you and remove XP Antivirus 2012 from your system as soon as possible. Read below what you’ll want to know though is what does this malware do and how to remove it from your PC for free.
During installation, XP Antivirus 2012 will register itself in the Windows registry so, it will run automatically every time when you start an application (files with “exe” extension). The rogue also uses this method of running to block the ability to run any programs, including legitimate antivirus and antispyware tools.
Once installed, XP Antivirus 2012 will imitate a system scan and report a large amount of infections. It hopes that you will then purchase its full version to clean your computer. Important to know, all of these infections found are fake, so you can safely ignore them!
While the rogue is running, it will display various nag screens and fake security warnings. Some of the alerts are:
Attention: DANGER!
ALERT! System scan for spyware, adware, trojans and viruses is complete.
XP Antivirus 2012 detected 29 critical system objects.
Security breach!
Beware! Spyware infection was found. Your system security is
at risk. Private information may get stolen, and your PC
activity may get monitored. Click for an anti-spyware scan.
System danger!
Your system is in danger. Privacy threats detected.
Spyware, keyloggers or Trojans may be working in the
background right now. Perform an in-depth scan and removal
now, click here.
Moreover, XP Antivirus 2012 will hijack your browser, so it will show a fake warning page instead a site that you want to visit. The fake warning state:
XP Antivirus 2012 ALERT
Internet Explorer alert. Visiting this site may pose a security threat to your system
Of course, all of these messages, warnings and alerts are a fake and supposed to scare you into thinking your computer in danger! Just like false scan results, ignore all of them!
As you can see, XP Antivirus 2012 is a scam which created with one purpose to scare you into thinking that your computer in danger as method to trick you into purchasing the full version of the program. If your computer is infected with this malware, then most importantly, do not purchase it! Uninstall the rogue from your PC as soon as possible. Use the removal guide below to remove XP Antivirus 2012 and any associated malware from your computer for free.
Use the following instructions to remove XP Antivirus 2012 (Uninstall instructions)
Step 1. Repair “running of .exe files”.
Method 1
Click Start, Run. Type command and press Enter. Type notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\pezfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
Save this as fix.reg to your Desktop (remember to select Save as file type: All files in Notepad.)
Double Click fix.reg and click YES for confirm.
Reboot your computer.
Method 2
Click Start, Run. Type command and press Enter. Type notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
[Version]
Signature="$Chicago$"
Provider=www.myantispyware.com
[DefaultInstall]
DelReg=regsec
AddReg=regsec1
[regsec]
HKCU, Software\Classes\.exe
HKCU, Software\Classes\pezfile
HKCR, .exe\shell\open\command
[regsec1]
HKCR, exefile\shell\open\command,,,"""%1"" %*"
HKCR, .exe,,,"exefile"
HKCR, .exe,"Content Type",,"application/x-msdownload"
Save this as fix.inf to your Desktop (remember to select Save as file type: All files in Notepad.)
Right click to fix.inf and select Install. Reboot your computer.
Step 2. Remove XP Antivirus 2012 associated malware.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
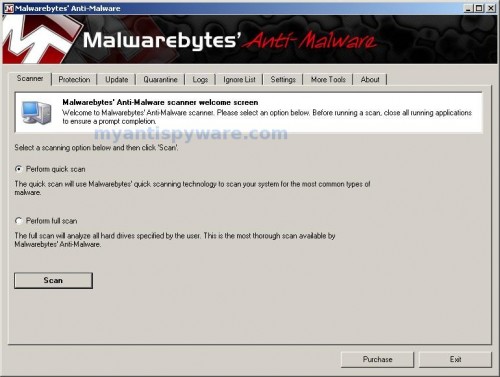
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for XP Antivirus 2012 infection. This procedure can take some time, so please be patient.
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
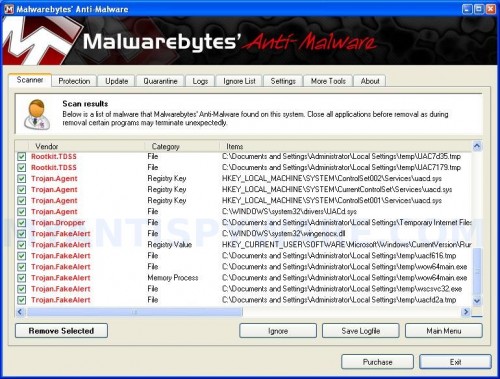
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove XP Antivirus 2012. MalwareBytes Anti-malware will now remove all of associated XP Antivirus 2012 files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
XP Antivirus 2012 removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
XP Antivirus 2012 creates the following files and folders
%AppData%\yun.exe
XP Antivirus 2012 creates the following registry keys and values
HKEY_CURRENT_USER\Software\Classes\.exe
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\.exe\shell
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start\command
HKEY_CURRENT_USER\Software\Classes\pezfile
HKEY_CURRENT_USER\Software\Classes\pezfile\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\pezfile\shell
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\runas
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\start
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\start\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | @ = “”%AppData%\yun.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | IsolatedCommand = “”%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe | @ = “pezfile”
HKEY_CURRENT_USER\Software\Classes\.exe | Content Type = “application/x-msdownload”
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command | @ = “”%AppData%\yun.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command | IsolatedCommand = “”%1″ %*”
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command | “(Default)” = ‘”%AppData%\yun.exe” -a “C:\Program Files\Mozilla Firefox\firefox.exe”‘
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command | “(Default)” = ‘”%AppData%\yun.exe” -a “C:\Program Files\Mozilla Firefox\firefox.exe” -safe-mode’
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command | “(Default)” = ‘”%AppData%\yun.exe” -a “C:\Program Files\Internet Explorer\iexplore.exe”‘











Thank You. The Reg patch worked exactly as described.
I really need help on this, remote assistance perhaps? please contact me at a.lex at live.co.uk
Thank you. One question. Is there anything that should be done with the register entries made with fix.reg?
Again, thank you.
Thanks so much. That virus hid files, blocked restore,and wouldn’t allow me to run the files I needed toclean things up. Right now i’m in the Malware scan phase. I’mhoping to get back to normal.
P.S. What’s with McAfee? I pay for that service and was still hosed. Next computer will be an Apple.
Worked beautifully!
THANKS!!!
Wow. I’ve been battling this garbage for days trying to figure out how to get rid of it. This did it in a matter of seconds. You guys are awesome, whoever you are. Thanks so much. I have my computer back.
Wow method 1 worked perfectly!!
thank you so much
I tried both of these and the virus is blocking me even here, the first option doesn’t work because it tells me the specified file is not a registry script… The second option gives me the virus pop-up when I try to install. I’ve got nothing showing up in my processes and am unable to locate any affected files. I’m unable to access my restore system, unable to launch MalWare… I’m at wit’s end – I don’t know what to do.
THANKS WELL DESCRIBED!!!!!IM GOOD HERE
Thank you so much!
From Portugal.
Splendid!! Thank you.
fix didn t work.
ill do it now with an other comp with a hard disk reader.
this is the 2d comp that was infected.
malwarebytes works perfect.
thanks
Worked well. I wonder why I’m paying for McAfee when it had nothing on this and didn’t detect it.
Thank you very much guys ! Splendid !
Failed to work. It did not find the xp antivirus on scan. I then was unable to get to website because it intrerupted shortly after web page came up. with the exployer page showing warnings forom the xp antivirus 2012. internet exployer alert system.
Thank you! I tried another patch but the virus kept stopping Malwarebytes’ from starting the scan. This one finally worked!
McAfee is the worst antivirus program in my opinion. I got it for free when I bought my computer and then I deleted it immediately.
Make sure you have Secunia PSI on your computer along with Malwarebytes’ Anti-Malware. My computer stopped the XP Antivirus 2012 but it got my dad’s because it wasn’t protected.
Worked well !!
Thank to share
Supply
had to ucreate a new user on windows to install malwarebytes from a usb drive, and had to run the program 2x to get the sucker, but after all that, method 1 worked!
i did have to add
REGEDIT4
to the first line of the registry file to get it to work, as a previous commenter mentioned.
Another way to deal wiht this kind of viruses is.If your computer has many accounts, you can use the Administrator account to backup the data from infected account by going to c>documents and settings> user name.Once you finish backing up the user data, eliminate that account (the virus will go with the account).
Restart that computer login with user account and put the data back.
Thank you i went through three sites and two videos trying to figure this out and you got it done with a copy and past. again thank you
Worked! I had run Malware several times w/out success. Once I applied the registry changes advised and then Malware, it killed the bugger. Also, in my prior attempts to clean, somehow my print spooler became affected and would not stay running. However, now that the malware is eliminated, my printer works again!
The second fix worked for me, thank you so much.
Avast’s boot scan didn’t even find it, such a waste.
Yall are fantastic. Thank you so much for posting this. I’ve been wrestling through a number of removal advice sites and this is the first one to take care of the registry damage. Much appreciated!
The second fix worked perfectly, thanks!
Thanks! worked well. Not sure how it got me. I had Malwarebutes Anit but could not access it due to the virus. The first method worked very well. Thanks gain!
The reg thing worked perfectly, but the malwarebytes thing hasn’t been working as well. I’ve done the scan 4 times and each time it removes something else, but my computer still won’t start in any mode but safe mode. Troubleshooting tips? I have a computer technical certificate, but this problem has got me stumped! Please help!!!
Worked exactly as described. Thank you so much!
I tried the first step and 1st method. It worked out as the pop ups stopped. However, I rebooted and then I am not able to open any exe file so I cant install Malwarebytes. What can I do now?
If you want to install malwarebytes and the virus will not allow it simply get a jump drive download it on another non infected pc with internet access and save it to the jump drive. Then return to your pc and run the pc in safe mode without networking and run the mbam setup from the jump drive and then let it do its magic and bam virus fixed 😉
I tried both fixes… and ran Malwarebytes. All of the registry entries and files appear to be gone but I still can’t start the firewall service or connect to the internet… (I am connected but no apps can access it) When I try to start the Windows Firewall/Internet Connection Sharing (ICS) service, I get a message that says “Could not start the Windows Firewall/Internet Connection Sharing (ICS) service on Local Computer. Error 2: The system cannot find the file specified. The executable is C:\WINDOWS\system32\svchost.exe -k netsvcs and svchost.exe does exist in that folder. Any ideas???