Vista Defender 2013 also known as Vista Defender, Vista Antivirus 2012, Vista Antivirus 2011, Vista Antivirus 2010, Vista Guardian, Vista Antivirus Pro, Vista Internet Security 2010, etc is a rogue antispyware program that reports false infections and shows numerous fake security alerts as an attempt to trick you into buying the software. This program is installed through the use of trojans. When the trojan is started, it will download and install Vista Defender onto your computer.
During installation, Vista Defender 2013 will register itself in the Windows registry to run automatically every time when you start an application (files with “exe” extension). The rogue also uses this method of running to block the ability to run any programs, including security applications.
Once running, Vista Defender 2013 virus will start a system scan and list a large amount of infections. All of these infections are fake, so you can safely ignore them. What is more, while the rogue is running, it will display fake security alerts and notifications with “Spyware infection has been found” or “Tracking software found” header. However, all of these alerts are fake.
Last but not least, Vista Defender will hijack Internet Explorer and Firefox and display fake warnings when you opening a web site.
As you can see, Vista Defender 2013 is scam, it is designed with one purpose to scare you into thinking that your computer in danger as a method to trick you into purchasing the full version of the program. If your computer is infected with this malware, then most importantly, do not purchase it! Uninstall the rogue from your PC as soon as possible. Use the removal guide below to remove Vista Defender 2013 virus from your computer for free.
Use the following instructions to remove Vista Defender 2013
Step 1. Repair “running of .exe files”.
Method 1
Click Start. Type in Search field command and press Enter. It will open the command prompt. Type into it notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\pezfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
Save this as fix.reg to your Desktop (remember to select Save as file type: All files in Notepad.)
Double Click fix.reg and click YES for confirm.
Reboot your computer.
Method 2
Click Start. Type in Search field command and press Enter. It will open the command prompt. Type into it notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
[Version]
Signature="$Chicago$"
Provider=www.myantispyware.com
[DefaultInstall]
DelReg=regsec
AddReg=regsec1
[regsec]
HKCU, Software\Classes\.exe
HKCU, Software\Classes\pezfile
HKCR, .exe\shell\open\command
[regsec1]
HKCR, exefile\shell\open\command,,,"""%1"" %*"
HKCR, .exe,,,"exefile"
HKCR, .exe,"Content Type",,"application/x-msdownload"
Save this as fix.inf to your Desktop (remember to select Save as file type: All files in Notepad.)
Right click to fix.inf and select Install. Reboot your computer.
Note: if Windows returns error message “Installation failed”, then you need disable UAC control. Click Start, Control Panel, User accounting, Click “Turn User Account Control on or off”. Uncheck “Use User Account Control (UAC)” and click OK. Now try install fix.inf once again.
Step 2. Remove Vista Defender 2013 associated malware.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
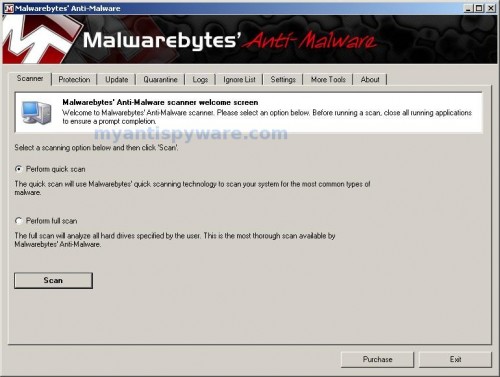
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for Vista Home Security 2012 infection. This procedure can take some time, so please be patient.
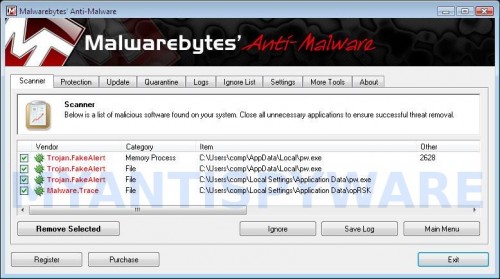
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove Vista Defender 2013. MalwareBytes Anti-malware will now remove all of associated Vista Defender 2013 files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Vista Defender 2013 creates the following files and folders
%UserProfile%\AppData\Local\{RANDOM}.exe
Vista Defender 2013 creates the following registry keys and values
HKEY_CURRENT_USER\Software\Classes\.exe
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\.exe\shell
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start\command
HKEY_CURRENT_USER\Software\Classes\pezfile
HKEY_CURRENT_USER\Software\Classes\pezfile\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\pezfile\shell
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\runas
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\start
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\start\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | @ = “”%UserProfile%\AppData\Local\{RANDOM}.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | IsolatedCommand = “”%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe | @ = “pezfile”
HKEY_CURRENT_USER\Software\Classes\.exe | Content Type = “application/x-msdownload”
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command | @ = “”%UserProfile%\AppData\Local\{RANDOM}.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command | IsolatedCommand = “”%1″ %*”









This is not a fix. This is an ad designed to make you think this is a quick fix and then the command prompt does not work. Do not buy this. The software they want to sell you is from the same people that create this OS overlay.
I have used the above way to remove Vista Defender 2013 virus from a PC that had been infected in France. The removal is performed in Denmark.
It works excellently when it is followed and is highly recommended.
A note, however, that it may be necessary to have to retrieve data and programs from another computer, just as the production of fix.reg and fix.inf easiest place on one another computer and then transferred with a USB stick.