Security researchers discovered a new variant of ransomware which named GANDCRAB 5.2 ransomware. It appends random extension to encrypted file names. This post will provide you a brief summary of information related to this new virus and how to recover all encrypted photos, documents and music for free.
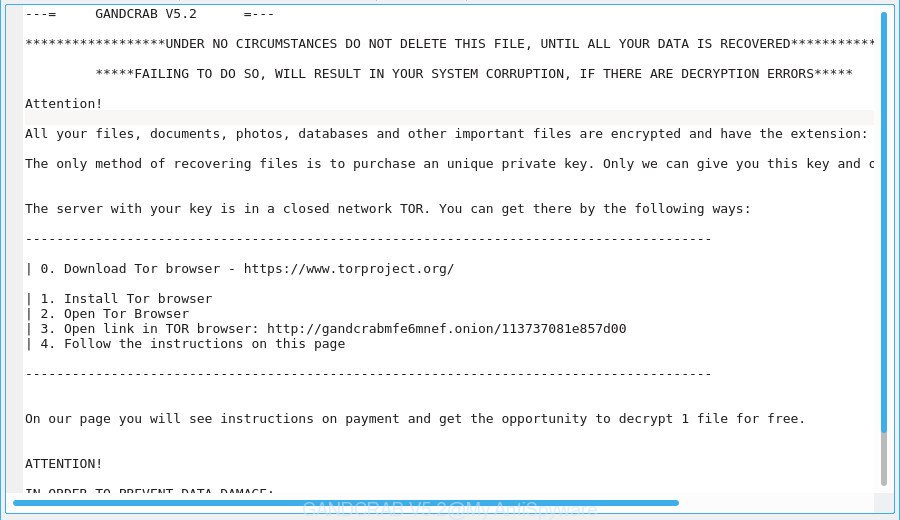
GANDCRAB V5.2 – ransom note
The GANDCRAB 5.2 is a variant of crypto viruses. It affects all current versions of Windows operating system like the Windows 10, Windows 8, Windows 7, Windows Vista and Windows XP. This ransomware uses a strong encryption algorithm with 2048-bit key to eliminate the possibility of brute force a key that will allow to decrypt encrypted files. The GANDCRAB 5.2 virus encrypts almost of files, including common as:
.r3d, .wdb, .rim, .itl, .der, .wmf, .bc6, .pem, .m3u, .odt, .srf, .pdd, .dng, .itm, .slm, .bc7, .ncf, .zip, .mdf, .icxs, .wpe, .mp4, .gdb, .jpg, .sidd, .wmv, .m2, .sie, .x3f, .das, .esm, .xlk, .xld, .wri, .odb, .bar, .3fr, .bay, .ai, .odc, .arw, .xlsx, .wpd, .p12, .dwg, .wpl, .txt, .snx, .itdb, .dcr, .xmmap, .vcf, .wp5, .cas, .webdoc, .zif, .blob, .indd, .hkdb, .sav, .mddata, .x3f, .mdbackup, .sum, .wdp, .wbc, .wmv, .xbplate, .jpe, .raw, .p7b, .ods, wallet, .wma, .xdl, .bkf, .fpk, .desc, .zw, .xar, .iwd, .z, .wpw, .ws, .lrf, .xf, .py, .vpp_pc, .ybk, .apk, .zabw, .gho, .wotreplay, .wav, .dazip, .xlgc, .xll, .wma, .zip, .srw, .crt, .iwi, .js, .psd, .cfr, .mpqge, .wbm, .kdb, .wbd, .pfx, .erf, .qdf, .zi, .bik, .sis, .layout, .pptx, .wpd, .vtf, .0, .bkp, .cr2, .dxg, .accdb, .2bp, .t13, .odp, .3ds, .wmd, .wp7, .xml, .sql, .sr2, .mef, .ysp, .wp, .t12, .doc, .yal, .epk, .fos, .wpg, .hvpl, .wp4, .dba, .xmind, .raf, .zdb, .p7c, .cer, .xpm, .wsd, .rb, .cdr, .ptx, .xx, .svg, .wm, .x, .wps, .hplg, .sb, .1st, .xyw, .ntl, .3dm, .m4a, .rofl, .pdf, .arch00, .wbmp, .rwl, .xdb, .psk, .forge, .avi, .tor, .wn, .xbdoc, .xy3, .litemod, .mrwref, .re4, .xls, .ztmp, .wpt, .big, .zdc, .lvl, .xlsm, .tax, .kdc, .css, .rtf, .xyp, .pst, .rw2, .wgz, .eps, .syncdb, .xls, .xxx, .wpb, .ff, .vfs0, .pkpass, .sid, .vdf
When the ransomware encrypts a file, it will append random extension to each encrypted file. Once the ransomware virus finished enciphering of all photos, documents and music, it will create a file called “DECRYPT.txt” with ransom note on how to decrypt all files. An example of the ransom demanding message is:
---= GANDCRAB V5.2 =---
******************UNDER NO CIRCUMSTANCES DO NOT DELETE THIS FILE, UNTIL ALL YOUR DATA IS RECOVERED*******************
*****FAILING TO DO SO, WILL RESULT IN YOUR SYSTEM CORRUPTION, IF THERE ARE DECRYPTION ERRORS*****
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension:
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
----------------------------------------------------------------------------------------
| 0. Download Tor browser - https://www.torproject.org/
| 1. Install Tor browser
| 2. Open Tor Browser
| 3. Open link in TOR browser: http://gandcrabmfe6mnef.onion/113737081e857d00
| 4. Follow the instructions on this page
----------------------------------------------------------------------------------------
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
We recommend you to remove GANDCRAB 5.2 ransomware sooner, until the presence of the virus has not led to even worse consequences. You need to follow the steps below that will allow you to completely remove GANDCRAB 5.2 virus from your computer as well as restore (decrypt) encrypted files for free.
Table of contents
- How to remove GANDCRAB 5.2 ransomware
- How to decrypt files encrypted by GANDCRAB 5.2
- Use Bitdefender GandCrab decryptor to decrypt files
- How to restore files encrypted by GANDCRAB 5.2
- How to protect your computer from GANDCRAB 5.2
How to remove GANDCRAB 5.2 ransomware
There are not many good free antimalware programs with high detection ratio. The effectiveness of malicious software removal tools depends on various factors, mostly on how often their virus/malware signatures DB are updated in order to effectively detect modern malware, adware, ransomware viruses and other security threats. We recommend to run several applications, not just one. These applications that listed below will help you remove all components of the GANDCRAB 5.2 ransomware from your disk and Windows registry.
Use Zemana Anti-malware to remove GANDCRAB 5.2 virus
We suggest using the Zemana Anti-malware which are completely clean your PC of the GANDCRAB 5.2 virus. The utility is an advanced malicious software removal program developed by (c) Zemana lab. It’s able to help you remove PUPs, viruss, ad supported software, malicious software, toolbars, ransomware and other security threats from your PC for free.
Installing the Zemana is simple. First you will need to download Zemana by clicking on the link below. Save it to your Desktop so that you can access the file easily.
164814 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
When the download is finished, close all windows on your personal computer. Further, open the install file named Zemana.AntiMalware.Setup. If the “User Account Control” dialog box pops up as displayed below, press the “Yes” button.
It will show the “Setup wizard” that will assist you install Zemana Anti Malware on the PC system. Follow the prompts and do not make any changes to default settings.
Once setup is finished successfully, Zemana AntiMalware (ZAM) will automatically launch and you may see its main window as displayed below.

Next, click the “Scan” button to scan for the GANDCRAB 5.2 ransomware and other security threats. Depending on your computer, the scan can take anywhere from a few minutes to close to an hour. When a threat is detected, the count of the security threats will change accordingly. Wait until the the scanning is complete.

Once Zemana Free completes the scan, Zemana Anti Malware will open a screen that contains a list of malware that has been found. Make sure all items have ‘checkmark’ and click “Next” button.
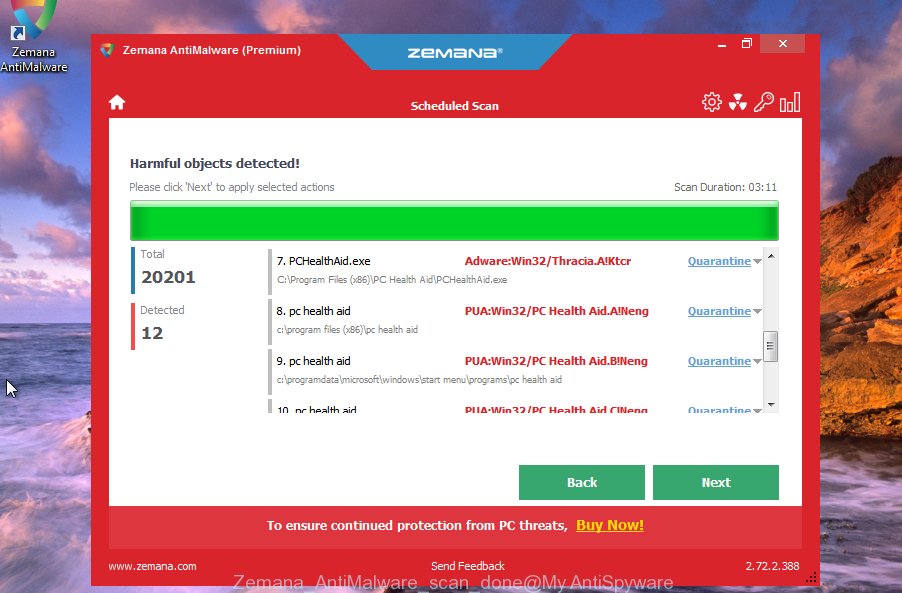
The Zemana Anti Malware will remove GANDCRAB 5.2 ransomware and other security threats and add items to the Quarantine. After the clean-up is finished, you can be prompted to restart your PC system.
Use MalwareBytes Anti Malware to remove GANDCRAB 5.2 ransomware
We recommend using the MalwareBytes. You can download and install MalwareBytes to search for and remove GANDCRAB 5.2 ransomware from your PC system. When installed and updated, this free malicious software remover automatically scans for and removes all threats exist on the computer.
Download MalwareBytes Free on your PC system by clicking on the link below.
327071 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When downloading is done, close all programs and windows on your computer. Double-click the set up file called mb3-setup. If the “User Account Control” dialog box pops up as shown on the image below, click the “Yes” button.
It will open the “Setup wizard” that will help you install MalwareBytes Anti-Malware (MBAM) on your computer. Follow the prompts and don’t make any changes to default settings.
Once setup is complete successfully, click Finish button. MalwareBytes Free will automatically start and you can see its main screen as displayed on the image below.
Now press the “Scan Now” button to perform a system scan with this tool for the GANDCRAB 5.2 ransomware virus and other malware. While the MalwareBytes Free program is checking, you can see number of objects it has identified as threat.
As the scanning ends, MalwareBytes Free will open a list of all items detected by the scan. When you’re ready, click “Quarantine Selected” button. The MalwareBytes will get rid of GANDCRAB 5.2 ransomware virus and other security threats. Once finished, you may be prompted to restart the machine.
We recommend you look at the following video, which completely explains the procedure of using the MalwareBytes to remove ad supported software, browser hijacker and other malware.
If the problem with GANDCRAB 5.2 ransomware virus is still remained
KVRT is a free portable application that scans your personal computer for malware, trojans, worms and viruses such as the GANDCRAB 5.2 and helps remove them easily. Moreover, it will also help you delete any harmful web-browser extensions and add-ons.
Download Kaspersky virus removal tool (KVRT) on your computer from the following link.
129234 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
Once the download is finished, double-click on the KVRT icon. Once initialization procedure is finished, you will see the KVRT screen as displayed in the following example.
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next click Start scan button . Kaspersky virus removal tool program will scan through the whole personal computer for the GANDCRAB 5.2 ransomware virus and other known infections. When a threat is found, the number of the security threats will change accordingly. Wait until the the scanning is complete.
When the scan is finished, Kaspersky virus removal tool will prepare a list of unwanted applications ad supported software like below.
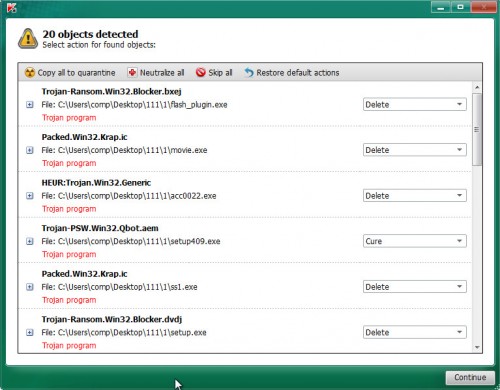
Review the report and then press on Continue to start a cleaning task.
How to decrypt files encrypted by GANDCRAB 5.2
The ransom note encourages victim to contact GANDCRAB 5.2’s authors via the http://gandcrabmfe6mnef.onion/113737081e857d00 web-site in order to decrypt all personal files. These persons will require to pay a ransom in Bitcoins.
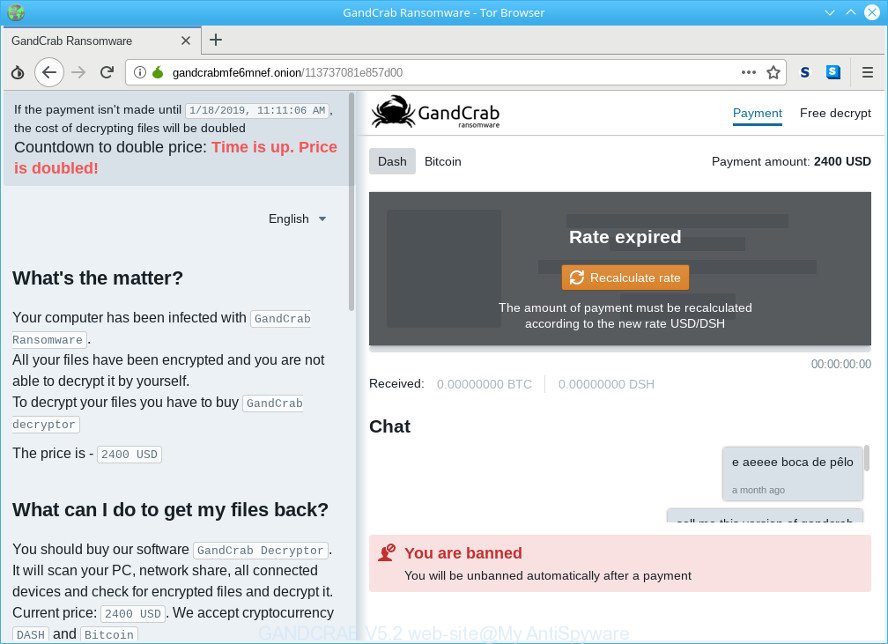
GANDCRAB V5.2 web-site
There is absolutely no guarantee that after pay a ransom to the authors of the GANDCRAB 5.2 virus, they will provide the necessary key to decrypt your files. In addition, you must understand that paying money to the cyber criminals, you are encouraging them to create a new ransomware.
We don’t recommend paying a ransom, as there is no guarantee that you will be able to decrypt your personal files. Especially since you have a chance to decrypt or restore your files using free tools such as Bitdefender GandCrab decryptor, ShadowExplorer and PhotoRec.
Use Bitdefender GandCrab decryptor to decrypt files
Bitdefender released a free decryption tool named “Bitdefender GandCrab decryptor“.
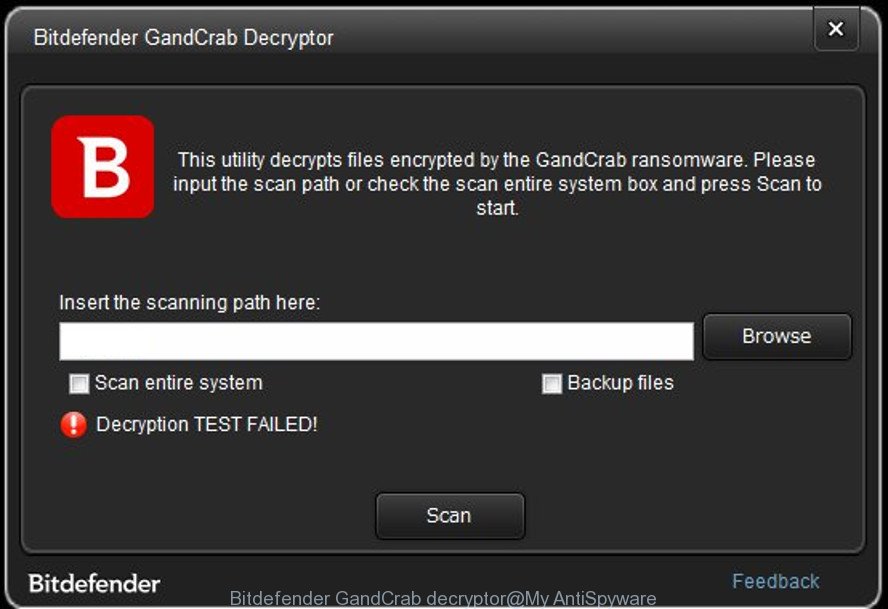
Bitdefender GandCrab decryptor
Bitdefender GandCrab decryptor has been updated to include decryption support for the following GandCrab variants (V1, V4, and all V5 versions).
Please check this article for more info and download free GandCrab decryptor.
How to restore files encrypted by GANDCRAB 5.2
In some cases, you can recover files encrypted by GANDCRAB 5.2 ransomware virus. Try both methods. Important to understand that we cannot guarantee that you will be able to restore all encrypted files.
Use ShadowExplorer to restore files encrypted by GANDCRAB 5.2 ransomware
An alternative is to recover encrypted files from their Shadow Copies. The Shadow Volume Copies are copies of files and folders that Microsoft Windows 10 (8, 7 and Vista) automatically saved as part of system protection. This feature is fantastic at rescuing photos, documents and music that were encrypted by GANDCRAB 5.2 virus. The guide below will give you all the details.
Installing the ShadowExplorer is simple. First you will need to download ShadowExplorer on your computer from the link below.
439461 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
Once downloading is done, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as displayed in the following example.
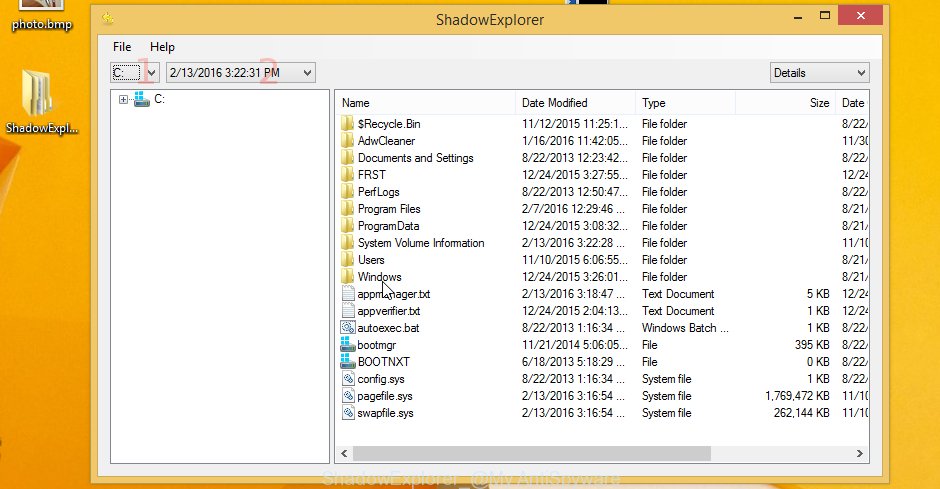
Launch the ShadowExplorer tool and then choose the disk (1) and the date (2) that you wish to restore the shadow copy of file(s) encrypted by the GANDCRAB 5.2 virus as shown on the screen below.
Now navigate to the file or folder that you want to restore. When ready right-click on it and click ‘Export’ button as displayed in the figure below.

Recover encrypted files with PhotoRec
Before a file is encrypted, the GANDCRAB 5.2 virus makes a copy of this file, encrypts it, and then deletes the original file. This can allow you to restore your personal files using file restore software such as PhotoRec.
Download PhotoRec from the link below. Save it on your Desktop.
When the download is finished, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as shown below.

Double click on qphotorec_win to run PhotoRec for Microsoft Windows. It’ll display a screen as on the image below.
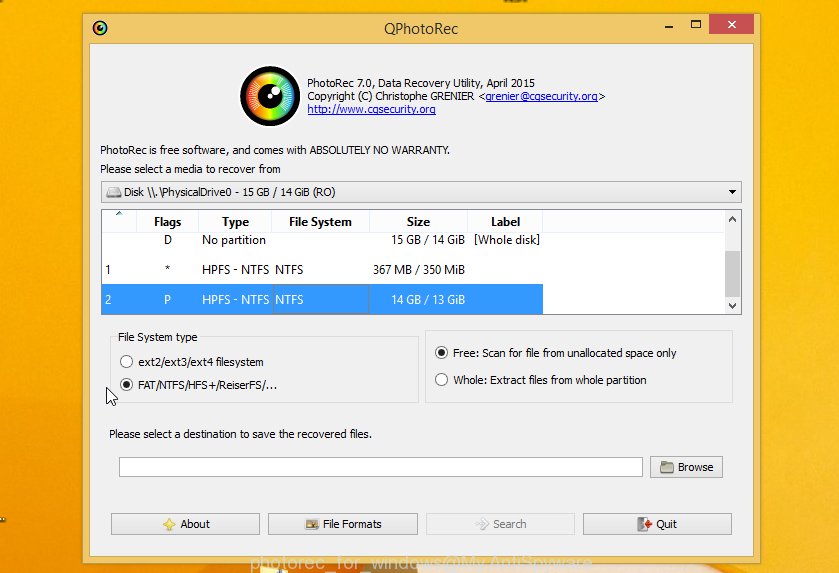
Choose a drive to recover as shown below.
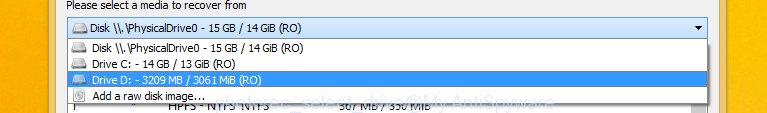
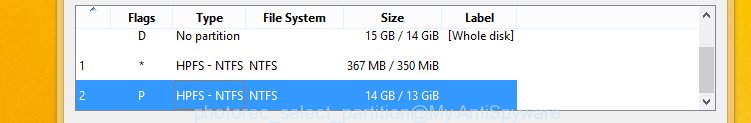
You will see a list of available partitions. Choose a partition that holds encrypted personal files as displayed below.
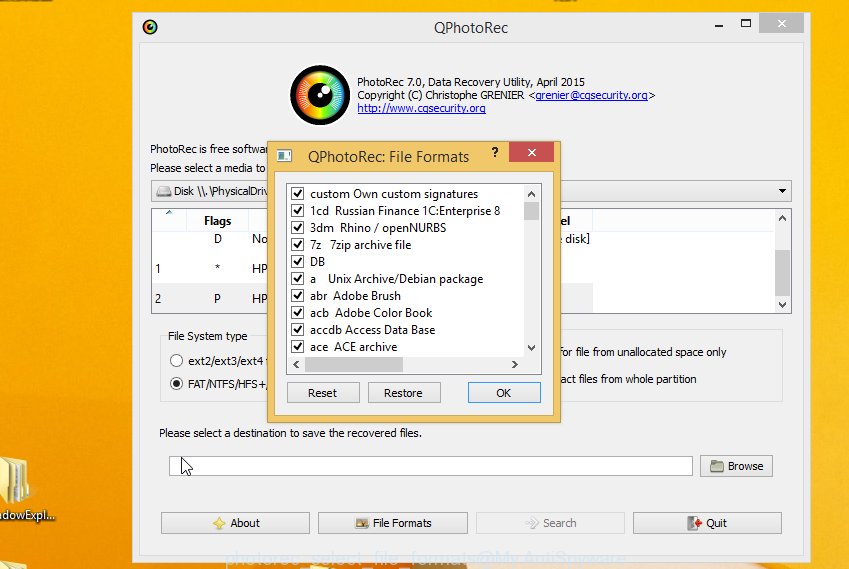
Click File Formats button and choose file types to restore. You can to enable or disable the restore of certain file types. When this is complete, press OK button.
Next, press Browse button to choose where restored photos, documents and music should be written, then click Search.
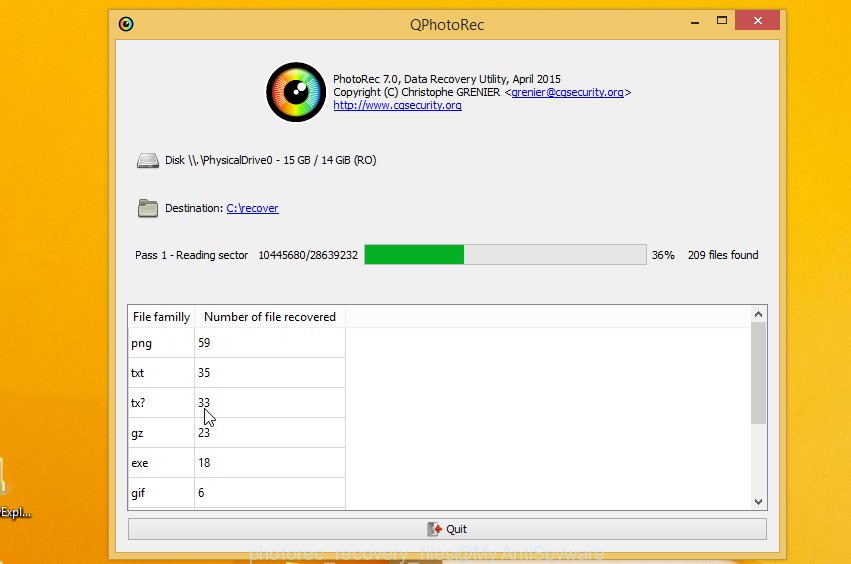
Count of restored files is updated in real time. All recovered personal files are written in a folder that you have selected on the previous step. You can to access the files even if the recovery process is not finished.
When the recovery is complete, press on Quit button. Next, open the directory where recovered photos, documents and music are stored. You will see a contents as shown on the image below.
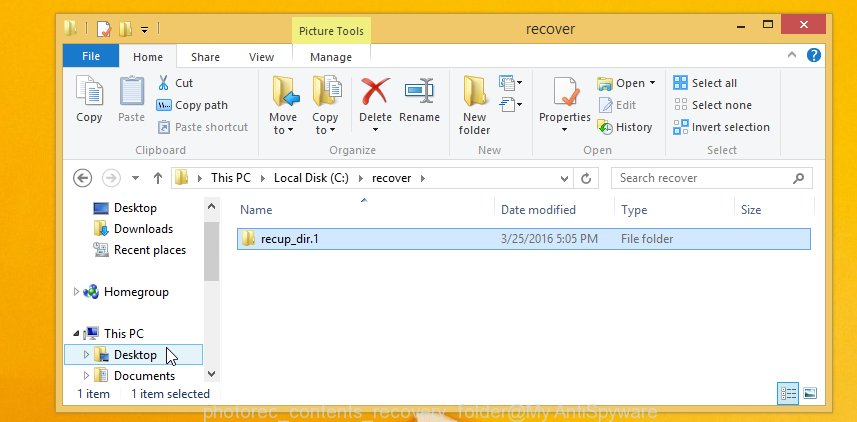
All restored files are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re searching for a specific file, then you can to sort your recovered files by extension and/or date/time.
How to protect your computer from GANDCRAB 5.2 ransomware
Most antivirus programs already have built-in protection system against the virus. Therefore, if your personal computer does not have an antivirus program, make sure you install it. As an extra protection, run the CryptoPrevent.
Run CryptoPrevent to protect your machine from GANDCRAB 5.2 ransomware
Download CryptoPrevent by clicking on the link below.
www.foolishit.com/download/cryptoprevent/
Run it and follow the setup wizard. Once the setup is finished, you’ll be shown a window where you can choose a level of protection, as shown in the figure below.
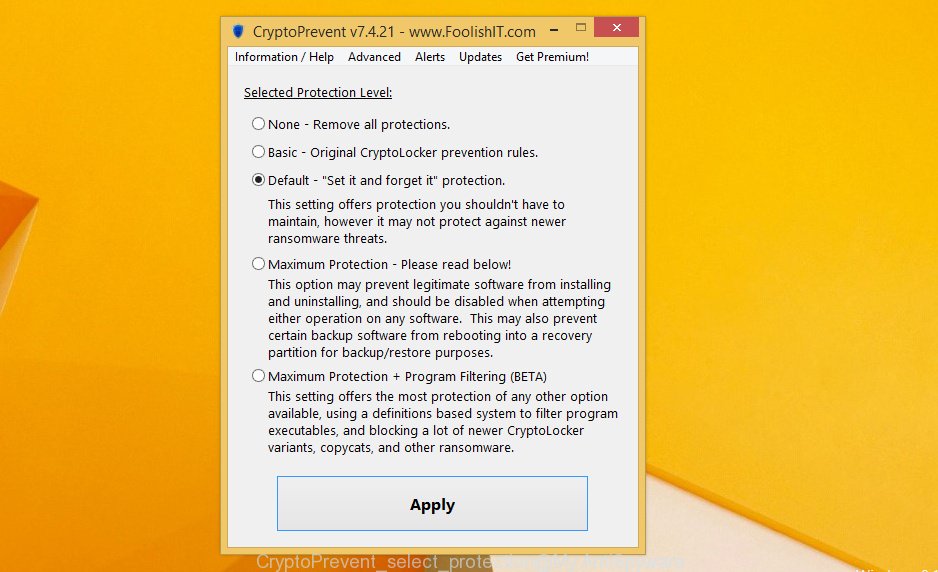
Now click the Apply button to activate the protection.
Finish words
Now your personal computer should be clean of the GANDCRAB 5.2 ransomware virus. Delete MalwareBytes AntiMalware (MBAM) and KVRT. We suggest that you keep Zemana Free (to periodically scan your machine for new malware). Make sure that you have all the Critical Updates recommended for Microsoft Windows operating system. Without regular updates you WILL NOT be protected when new ransomware, malicious programs and adware are released.
If you are still having problems while trying to delete GANDCRAB 5.2 ransomware from your personal computer, then ask for help here.












Place help!!!
I cannot decrypt file *.utymy from GandCrab 5.2.
Thank you!
If Bitdefender GandCrab decryptor does not work, then you can try to recover your files using data recovery software such as ShadowExplorer or Photorec.
Place help!!!!!!
How to decrypt “hxcntd”