Gorentos@bitmessage.ch ransomware is a malicious software that is made in order to encrypt documents, photos and music. It stealthily penetrates the computer, encrypts files that stored on system disks and demands a ransom in order to unlock (decrypt) them.
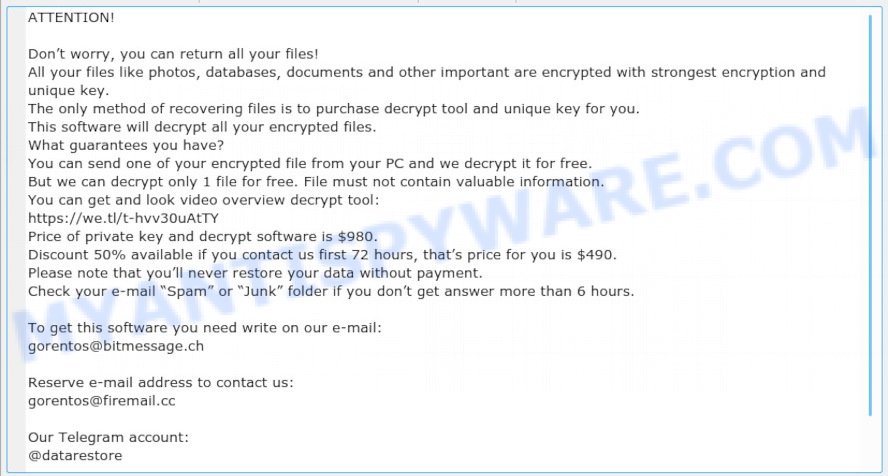
“gorentos@bitmessage.ch ransomware” – ransom note
The makers of ransomware have a strong financial motive to infect as many machines as possible. The files that will be encrypted include the following file extensions:
.wpg, .rofl, .1st, .flv, .menu, .m3u, .jpe, .wdb, .pst, .lrf, .lvl, .iwi, .bkf, .layout, .rar, .wbc, .wpa, .sql, .webdoc, .zw, .docx, .wbmp, .7z, .apk, .itm, .xdl, .wsh, .syncdb, .wpw, .xlgc, .snx, .vtf, .arw, .1, .p12, .wmd, .vfs0, .wma, .ptx, .w3x, .epk, .srw, .raw, .dba, .wps, .csv, .cfr, .dcr, .accdb, .fos, .bc6, .ysp, .wn, .bkp, .raf, .tax, .db0, .doc, .x, .das, .wp6, .wbz, .odc, .forge, .mov, .xld, .dwg, .xy3, .wma, .nrw, .map, .xyp, .xbdoc, .rb, .wgz, .gho, wallet, .dxg, .webp, .xlsx, .lbf, .sum, .t13, .xx, .txt, .xmind, .wpb, .psd, .big, .x3f, .crw, .css, .dmp, .xlsm, .hkx, .srf, .wdp, .ltx, .odt, .zabw, .wp, .wb2, .mrwref, .wsc, .bar, .sidd, .xlk, .y, .zip, .wmv, .mddata, .wire, .ztmp, .pem, .xpm, .kdb, .itdb, .sie, .xml, .dazip, .xlsx, .cas, .hvpl, .wpe, .wbk, .ws, .hkdb, .wri, .ppt, .wsd, .d3dbsp, .xlsm, .litemod, .pfx, .x3f, .zi, .ai, .mef, .kdc, .0, .x3d, .vdf, .wot, .sis, .ncf, .wpd, .wmo, .svg, .cdr, .pef, .p7b, .2bp, .m2, .xbplate, .vpp_pc, .xf, .bay, .zip, .z, .r3d, .erf, .zif, .bc7, .jpg, .xls, .der, .cr2, .mp4, .xlsb, .xmmap, .wmf, .mdbackup, .wpt, .mcmeta, .zdb, .sid, .itl, .fsh, .mpqge, .yal, .xll, .odb, .wps, .crt, .rwl, .ods, .icxs, .gdb, .orf, .wcf, .cer, .odp, .z3d, .jpeg, .sr2, .esm, .t12, .sidn, .mdf, .wpd, .pdd, .kf, .re4, .qdf, .bik, .dng, .p7c, .indd, .desc, .ybk, .rtf, .pak, .iwd, .js, .odm, .upk, .fpk, .hplg, .vpk, .wp5, .avi, .wbd, .sb, .eps, .tor, .3dm, .m4a, .xls, .3fr, .xar, .wotreplay, .pptx, .rw2, .pkpass
When the ransomware virus encrypts a file, it will append a new extension to every encrypted file. This means that a document file named ‘example.doc’, when encrypted, becomes ‘example.doc.locked’.
Once the ransomware virus finished enciphering of all personal files, it will create a file named ‘_readme.txt’ with ransomnote on how to decrypt all photos, documents and music. An example of the ransomnote is:
ATTENTION! Don’t worry, you can return all your files! All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key. The only method of recovering files is to purchase decrypt tool and unique key for you. This software will decrypt all your encrypted files. What guarantees you have? You can send one of your encrypted file from your PC and we decrypt it for free. But we can decrypt only 1 file for free. File must not contain valuable information. You can get and look video overview decrypt tool: https://we.tl/t-hvv30uAtTY Price of private key and decrypt software is $980. Discount 50% available if you contact us first 72 hours, that’s price for you is $490. Please note that you’ll never restore your data without payment. Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours. To get this software you need write on our e-mail: gorentos@bitmessage.ch Reserve e-mail address to contact us: gorentos@firemail.cc Our Telegram account: @datarestore Your personal ID:
Threat Summary
| Name | Gorentos@bitmessage.ch ransomware |
| Type | Crypto virus, Crypto malware, File locker, Filecoder, Ransomware |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch, gorentos@firemail.cc, @datarestore (telegram) |
| Ransom amount | $980, $490 in Bitcoins |
| Symptoms | When you try to open your file, Windows notifies that you do not have permission to open this file. Files are encrypted with a new file extension. Your file directories contain a ‘ransom note’ file that is usually a .html, .jpg or .txt file. You have received instructions for paying the ransom. |
| Distribution methods | Phishing Emails that is carefully developed to trick a victim into opening an attachment or clicking on a link that contains a malicious file. Drive-by downloading (when a user unknowingly visits an infected web site and then malicious software is installed without the user’s knowledge). Social media posts (they can be used to entice users to download malicious software with a built-in ransomware downloader or click a malicious link). Malicious web pages. |
| Removal | To remove Gorentos@bitmessage.ch ransomware use the removal guide |
| Decryption | To decrypt Gorentos@bitmessage.ch ransomware use the steps |
Use the step-by-step instructions below to remove Gorentos@bitmessage.ch ransomware and restore (decrypt) encrypted documents, photos and music for free.
Quick links
- How to remove Gorentos@bitmessage.ch ransomware
- How to decrypt encrypted files
- Use STOPDecrypter to decrypt Gorentos@bitmessage.ch ransomware
- How to restore encrypted files
- How to protect your PC system from Gorentos@bitmessage.ch crypto virus?
- Finish words
How to remove Gorentos@bitmessage.ch ransomware
Using a malware removal tool to scan for and remove ransomware hiding on your system is probably the easiest solution to remove the Gorentos@bitmessage.ch virus. We suggests the Zemana Anti Malware (ZAM) application for Windows computers. MalwareBytes and KVRT are other anti malware tools for MS Windows that offers a free malware removal.
Remove Gorentos@bitmessage.ch ransomware with Zemana Anti-malware
We advise you to use the Zemana Anti-malware that are completely clean your computer of this ransomware. Moreover, the utility will help you to remove trojans, malicious software, worms and spyware that your PC system can be infected too.
Visit the following page to download the latest version of Zemana for Windows. Save it to your Desktop.
164753 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
After downloading is finished, close all apps and windows on your computer. Double-click the set up file named Zemana.AntiMalware.Setup. If the “User Account Control” prompt pops up as on the image below, click the “Yes” button.
It will open the “Setup wizard” that will help you set up Zemana on your computer. Follow the prompts and don’t make any changes to default settings.
Once installation is complete successfully, Zemana Anti-Malware (ZAM) will automatically start and you can see its main screen like below.

Now press the “Scan” button to perform a system scan for the Gorentos@bitmessage.ch ransomware, other malware, worms and trojans. This task can take some time, so please be patient. While the Zemana tool is checking, you can see how many objects it has identified as being infected by malware.

When Zemana completes the scan, Zemana Free will show a scan report. When you’re ready, click “Next” button. The Zemana Anti-Malware will start to remove Gorentos@bitmessage.ch crypto malware and other security threats. When finished, you may be prompted to restart the PC.
Use MalwareBytes Anti Malware to remove Gorentos@bitmessage.ch ransomware
We suggest using the MalwareBytes Free. You can download and install MalwareBytes Anti-Malware (MBAM) to locate and remove Gorentos@bitmessage.ch virus from your PC system. When installed and updated, this free malicious software remover automatically finds and removes all threats present on the computer.
- Installing the MalwareBytes Free is simple. First you’ll need to download MalwareBytes Anti-Malware (MBAM) on your personal computer by clicking on the link below.
Malwarebytes Anti-malware
327020 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- At the download page, click on the Download button. Your browser will display the “Save as” dialog box. Please save it onto your Windows desktop.
- When the download is finished, please close all applications and open windows on your PC system. Double-click on the icon that’s named mb3-setup.
- This will start the “Setup wizard” of MalwareBytes onto your machine. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, the MalwareBytes Anti Malware will start and open the main window.
- Further, click the “Scan Now” button to perform a system scan for the Gorentos@bitmessage.ch crypto virus and other malicious software. This process can take quite a while, so please be patient. While the MalwareBytes Anti-Malware is checking, you can see how many objects it has identified either as being malware.
- After that process is done, MalwareBytes Free will open a screen which contains a list of malware that has been found.
- Review the results once the tool has finished the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply click the “Quarantine Selected” button. After finished, you may be prompted to restart the computer.
- Close the AntiMalware and continue with the next step.
Video instruction, which reveals in detail the steps above.
Use KVRT to delete Gorentos@bitmessage.ch crypto malware from the system
The KVRT utility is free and easy to use. It may scan and remove ransomware such as Gorentos@bitmessage.ch virus, other malware, trojans and worms. KVRT is powerful enough to find and get rid of malicious registry entries and files that are hidden on the PC.
Download Kaspersky virus removal tool (KVRT) from the link below. Save it directly to your Windows Desktop.
129221 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
When the download is finished, double-click on the KVRT icon. Once initialization procedure is done, you’ll see the KVRT screen like below.
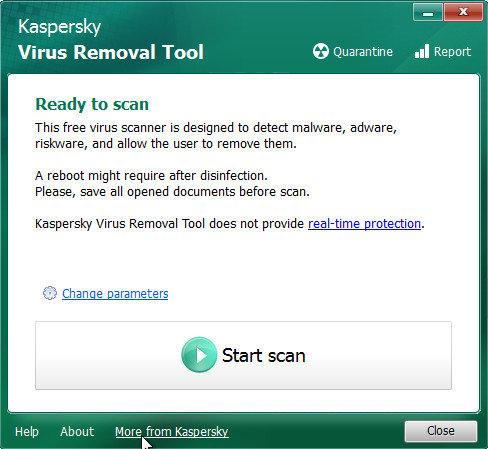
Click Change Parameters and set a check near all your drives. Press OK to close the Parameters window. Next click Start scan button to perform a system scan for the Gorentos@bitmessage.ch crypto malware and other trojans and harmful apps. This task may take quite a while, so please be patient. While the utility is scanning, you can see how many objects and files has already scanned.
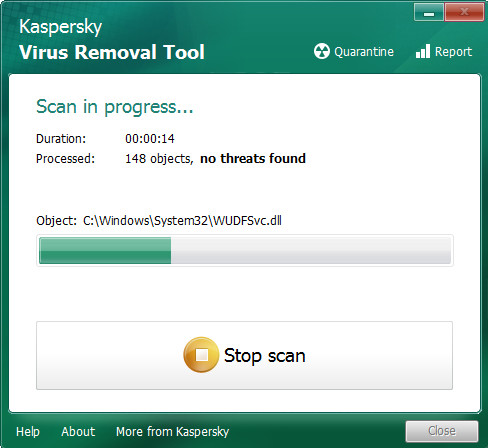
When that process is complete, KVRT will show a list of found items as displayed in the following example.
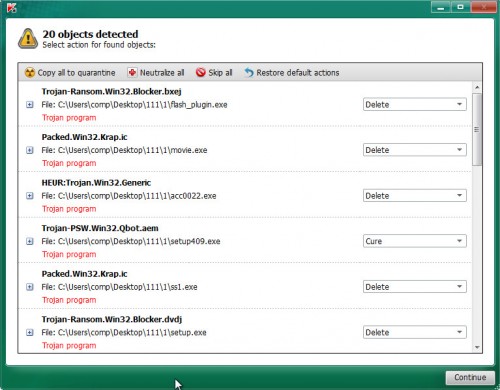
Next, you need to click on Continue to start a cleaning procedure.
How to decrypt encrypted files
The Gorentos@bitmessage.ch crypto virus encourages victim to contact it’s developers in order to decrypt all personal files. These persons will require to pay a ransom (usually demand for $980 or $480 in Bitcoins).

Never pay the ransom! You might feel that you have no other choice but to pay up and decrypt encrypted files quickly. There is no guarantee that the creators of Gorentos@bitmessage.ch ransomware virus will live up to the word and give back your personal files.
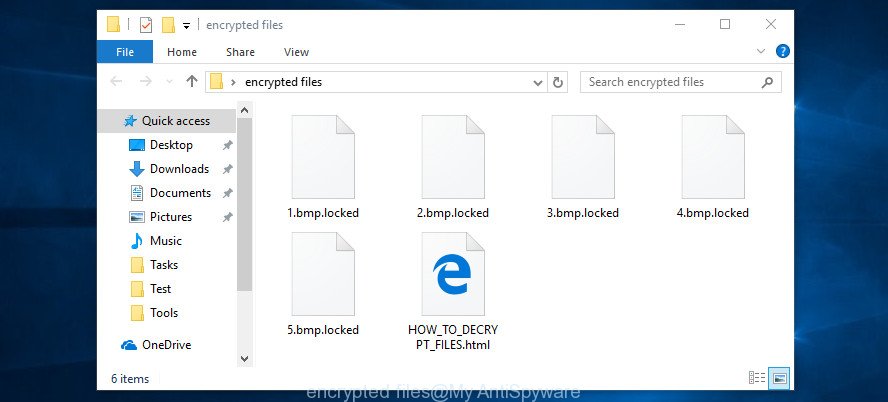
With some variants of the Gorentos@bitmessage.ch ransomware, it is possible to decrypt or restore encrypted files using free tools such as STOPDecrypter, ShadowExplorer and PhotoRec.
Use STOPDecrypter to decrypt Gorentos@bitmessage.ch ransomware
Michael Gillespie (@) released a free decryption tool named STOPDecrypter (download from download.bleepingcomputer.com/demonslay335/STOPDecrypter.zip).
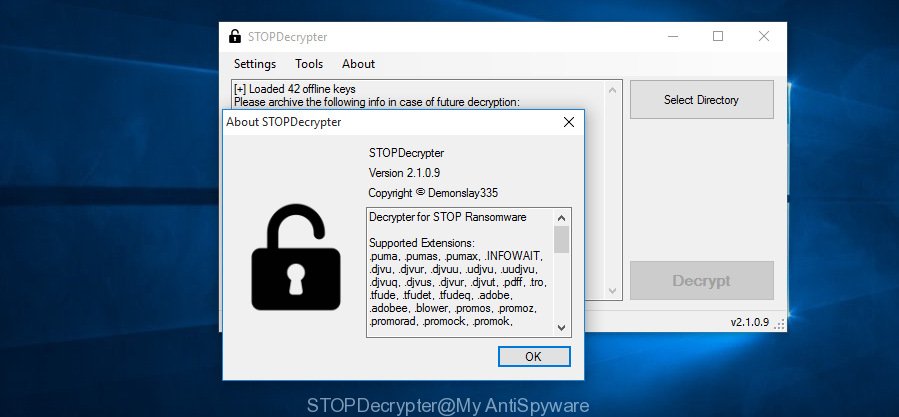
STOPDecrypter
STOPDecrypter has been updated to include decryption support for the following .djvu* variants (.djvu, .djvuu, .udjvu, .djvuq, .djvur, .djvut, .pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .dotmap. STOPDecrypter will work for any extension of the Djvu* variants including new extensions.
Please check the twitter post for more info.
How to restore encrypted files
In some cases, you can recover files encrypted by Gorentos@bitmessage.ch ransomware. Try both methods. Important to understand that we cannot guarantee that you will be able to restore all encrypted files.
Recover encrypted files using Shadow Explorer
If automated backup (System Restore) is enabled, then you can use it to recover all encrypted files to previous versions.
ShadowExplorer can be downloaded from the following link. Save it to your Desktop.
439386 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
After the download is finished, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as shown on the screen below.
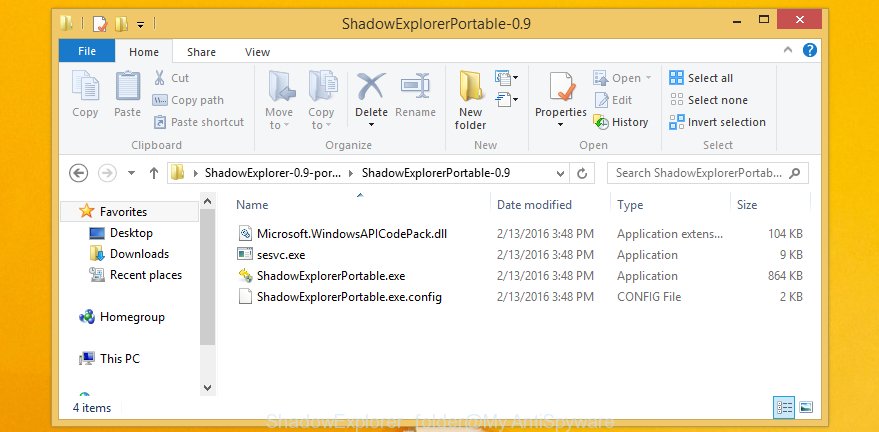
Launch the ShadowExplorer tool and then select the disk (1) and the date (2) that you want to restore the shadow copy of file(s) encrypted by the Gorentos@bitmessage.ch ransomware like below.
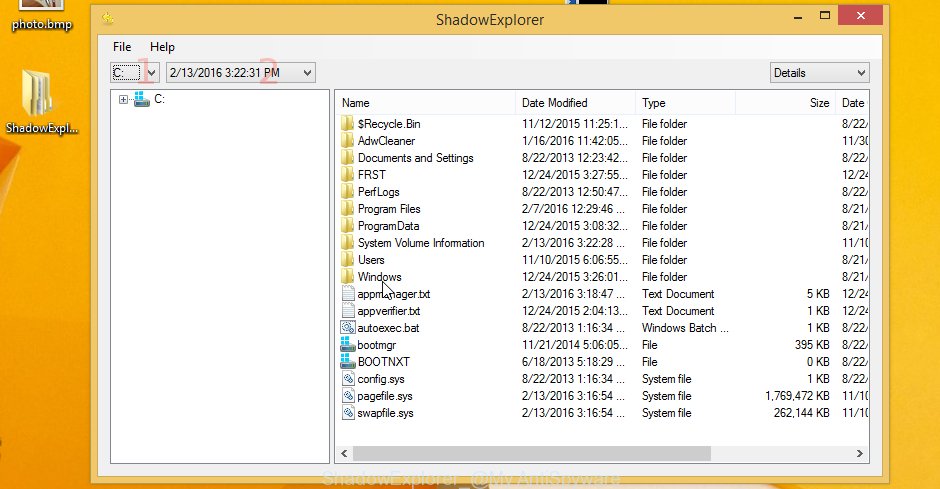
Now navigate to the file or folder that you want to recover. When ready right-click on it and click ‘Export’ button as displayed on the screen below.

Restore encrypted files with PhotoRec
Before a file is encrypted, the Gorentos@bitmessage.ch ransomware makes a copy of this file, encrypts it, and then deletes the original file. This can allow you to restore your personal files using file restore apps like PhotoRec.
Download PhotoRec on your PC from the following link.
After the downloading process is complete, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as on the image below.

Double click on qphotorec_win to run PhotoRec for Microsoft Windows. It’ll show a screen as displayed below.
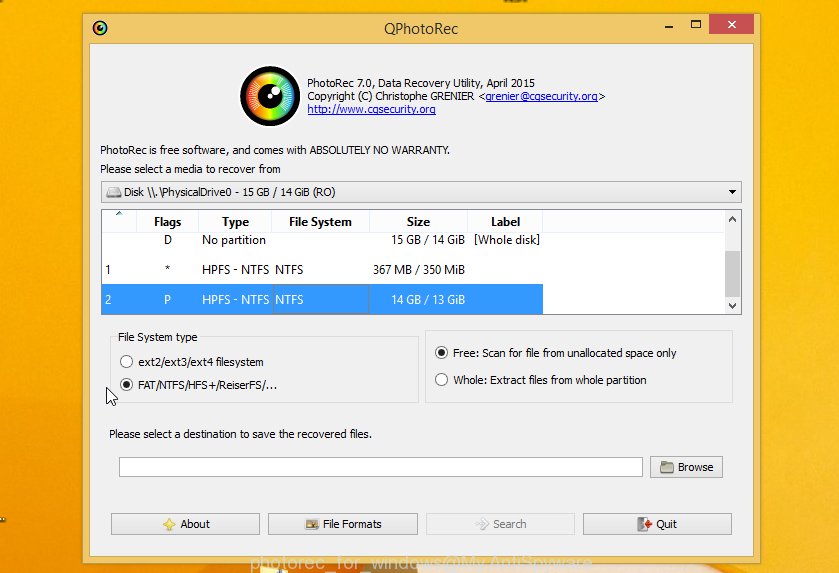
Select a drive to recover as displayed below.
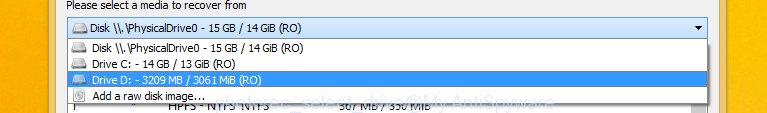
You will see a list of available partitions. Choose a partition that holds encrypted documents, photos and music as shown on the screen below.
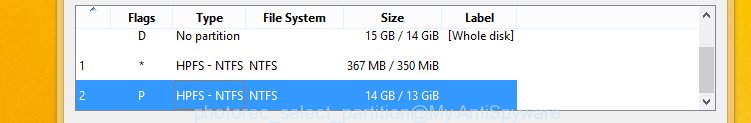
Press File Formats button and choose file types to recover. You can to enable or disable the restore of certain file types. When this is done, press OK button.
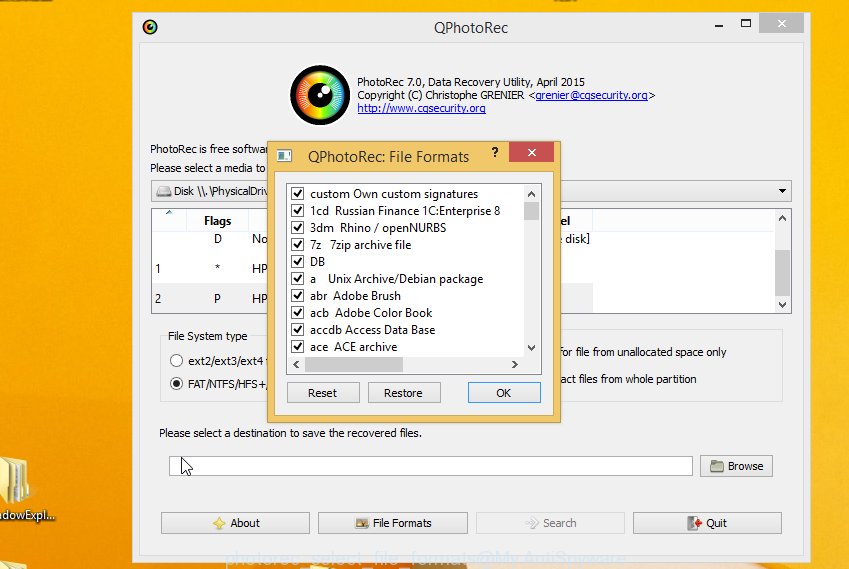
Next, click Browse button to choose where recovered photos, documents and music should be written, then press Search.
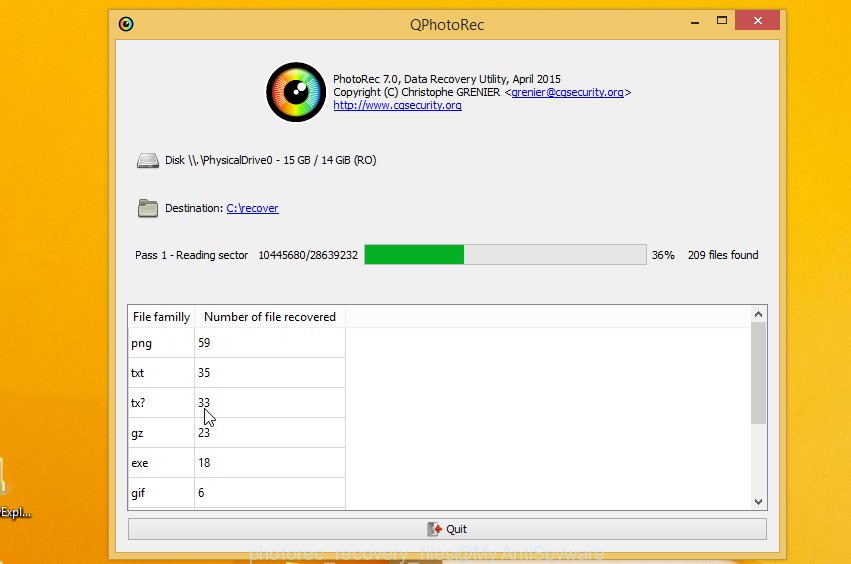
Count of restored files is updated in real time. All recovered personal files are written in a folder that you have chosen on the previous step. You can to access the files even if the restore process is not finished.
When the restore is finished, press on Quit button. Next, open the directory where restored personal files are stored. You will see a contents as displayed in the following example.
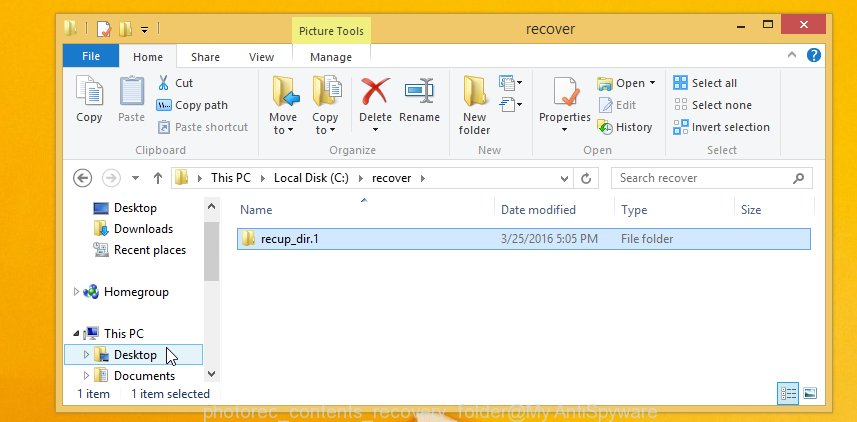
All restored documents, photos and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re searching for a specific file, then you can to sort your restored files by extension and/or date/time.
How to protect your PC system from Gorentos@bitmessage.ch crypto virus?
Most antivirus programs already have built-in protection system against the crypto malware. Therefore, if your PC does not have an antivirus program, make sure you install it. As an extra protection, use the HitmanPro.Alert.
Use HitmanPro.Alert to protect your PC from Gorentos@bitmessage.ch crypto malware
HitmanPro.Alert is a small security tool. It can check the system integrity and alerts you when critical system functions are affected by malware. HitmanPro.Alert can detect, remove, and reverse ransomware effects.
Download HitmanPro Alert on your PC by clicking on the link below.
After the download is done, open the file location. You will see an icon like below.

Double click the HitmanPro.Alert desktop icon. After the tool is launched, you’ll be displayed a window where you can choose a level of protection, as displayed in the figure below.
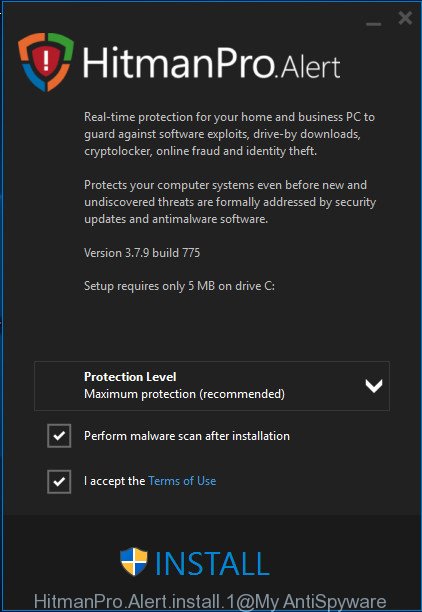
Now click the Install button to activate the protection.
Finish words
Once you have finished the steps outlined above, your computer should be free from Gorentos@bitmessage.ch ransomware and other malware. Your computer will no longer encrypt your documents, photos and music. Unfortunately, if the few simple steps does not help you, then you have caught a new crypto malware, and then the best way – ask for help here.














Here is my situation:
After knowing that my computer had a virus, I removed it from Control Pannel, and opened msconfig and disabled all applications and software running with Windows. And I saw the location of some strange files. But cannot enter to delete manually. Also because I turned off msconfig and restarted, the computer was not paralyzed. Next I try to use System Restore, but I can’t because the system constantly reports an error. And my hope is turned off when Antivirus AVG Tunel Up is also infected, because I plan to use System Restore in AVG. And at the most desperate time, I know your post. I always thought it was impossible to save files, my important application (I had this error 1 year ago), even though I successfully removed this virus.
I first downloaded Malawaretes (I use Premium, who needs to contact me, I will send a free Code to you). However, it seems that the virus is too strong, and so the software scans 3 hours, finds 181 viruses. I deleted all. Although I haven’t finished scanning yet, I’m still out in Malawaretes to check. I felt it was okay temporarily, and I reinstalled AVG. And after 2 times System Restore, I returned to the program 2 days ago. I thought to myself, “I finally managed to defeat you.” But when checking again, all files, files, applications on the computer have turned into unimaginable pictures, with the extension @*.txt.
Then I had to do the following presented here. And finally I was able to feel light, comfortable when I recovered them. I think that “ShadowExplore” easier to use, and very fast. The 1.75 GB file (1,884,807,168 bytes) recovered takes only 5 seconds. However, it also has the disadvantages of Time. Example software takes time: 1h, 23-6-2019 – 4h, 23-6-2019 | 7h, 23-6-2019- 12h, 23-06-2019 …. I have a number of files that appear and fail in the middle of 7am to 12pm, which leads to the inability to check those files when not yet error Luckily for me when those files are not important. Anyway, I would like to thank the article that helped me recover almost completely. Thank you very much for posting this very meaningful article. Can I share it on my FB? If allowed, once again send you a sincere thank you.
Thanks, I had issues from this new virus and followed your method. It looks it gone all virus. I use Malware remove softwere mentioned here. Thanks again..I still have readme. file whihc is in every folder. I don’t know that I need to remove one by one.
hello sir,
I am from india and i belong to a very poor family ,the ransom you are asking is too huge , i dont have any income as i have just started working and my family income cannot fill the ransom. please kind sir return my data as i have my job at stake and will loose it if I dont submit the files from that data. please do consider sir it is a humble request.
thanking you.
Sir my id is- 106Asdj475yiudfJDJuMI1pjfFwXsLQz4UOcMKPfRdDvBxUdaQVryBw
I am from Algeria. Please, I will rewrite my encrypted files because I can not pay any extra money. I am just a simple worker
my ID : 097Asudh743uifdgdHIqDimLxHysKVrCOrHHbAYCylInGffRgdefE5VEA
I am from india and i belong to a very poor family ,the ransom you are asking is too huge , i dont have any income as i have just started working and my family income cannot fill the ransom. please kind sir return my data as i have my job at stake and will loose it if I dont submit the files from that data. please do consider sir it is a humble request. PLZZ PLZ SIR
thanking you.
MY ID:- 111Asd3i74yih3gkdfYdiAhuxqrrqll1ySFTT98Lb2z2vgoMZ6EKVtHvh
Please return my files to me …iam a teenage and in a high school and my parents cant even pay this ransom
please return my files to me..i have a important files that have been with me more than 5 years when i was young..please help me 🙁
MY ID : 122Asdd5456dfgNw41BzsxEVNKV1VbT9NgZMldn3clPMuLWu4PYmgT
Try STOPDecrypter. If STOPDecrypter does not help you to decrypt encrypted files, in some cases, you have a chance to restore your files using ShadowExplorer and PhotoRec. Follow the steps above.
Rakibul Islam
I am from Bangladesh and i belong to a very poor family ,the ransom you are asking is too huge , i dont have any income as i have just started working and my family income cannot fill the ransom. please kind sir return my data as i have my job at stake and will loose it if I dont submit the files from that data. please do consider sir it is a humble request. PLZZ PLZ SIR
thanking you.
MY ID:-
119Asd3768237IhsdfYc0V3zmpPR1n9ncoDtXnvIFtskA3gs06hO9D0sid
my id is this (150uyGgdLdfN61odQsjTidgZVZk7BbQkHbcoNApklmMjP2GKo37J) infected by vesrato gorentos
Hi bro
I’m from Egypt and have no money
This city wants money because it is a poor country and you know this and iam sry for that :S
thats my id 0159Iuihiuer7f3hfGf1nyBHEoO57KstcLSoLDSPv2PRWRkl9LSURIgDJ :S
I’m a student and that ransom fees I can’t get it ,please return my files my ID is 0160psdfjh7gdfgalqod7v7V9coOCk9UHuCwnRepYhgPiJzujbLT8LC
I am from Pakistan. Please, I will not recover my encrypted files because I can not pay any extra money. I am just a simple worker please help me
my ID : 0161psdfjH7gdfgEf3JfwuAIZHiVaHN2YoL4YXa3IJSh3I80MriXfmh
Unfortunately, at the moment, the only way to recover encrypted files is to use the ShadowExplorer and PhotoRec.
i was attacked today by ransomware i cant pay money i am very poor please help me to recover my files
my id is :162Ad768734uygjdfgyR9cj1DVwPtghV46JfvnaeRb3Xtjm5qRHWHZEiC5
I AM INDIA PLS REMOVE IT.. I AM WORKING MY ID IS 162Ad768734uygjdfgC8HRRfDNxCNKa6U5CQoFaagVN4aFT3ejipDF0Iin
ple ope my file
this is my id
162Ad768734uygjdfgHqEWPalAVVmhAuEvL1mrFn3KjbWtFHCqbCpB52T3
rudraravalji , ANBU , ajay – to date, there is no way to decrypt your files. The only way to restore them is to use the steps described above in our article.
hello sir,
I am from Pakistan and i belong to a very poor family ,the ransom you are asking is too huge , i dont have any income as i have just started working and my family income cannot fill the ransom. please kind sir return my data as i have my job at stake and will loose it if I dont submit the files from that data. please do consider sir it is a humble request.
thanking you.
First of all, you need to try to recover encrypted files using the steps described above. In addition to the above, at the moment a method has been found that allows you to decrypt files that have been encrypted using an offline key. It is not difficult to determine which key was used in the encryption process, just look at the personnal ID in file ‘_readme.txt’. If it ends with ‘t1’, then the files can be decrypted, that is, an offline key was used to encrypt them. Additional verification can be performed using the STOPDecrypter v2.2.0.0 (download.bleepingcomputer.com/demonslay335/STOPDecrypter.zip).
So, how to decrypt files.
1. Download the decrypter from here (we.tl/t-2XN0Rj4cXu). VirusTotal scan results here (link).
2. Unzip the downloaded file, carefully read and follow the instructions (“instructions for gero peta hese meds and moka.txt” file).
hello guys i hope someone help me please i want to back my data and files and photos etc
really i don’t know from where i got this virus
if someone know anything to do to back my files please tell me,
thanks with respect !!
this my id
0157HydtUdjsFFs1ybPuBJYyh2NR4EfmmDnafXmbkwVdfOypk05srJY
help me please:
my ID: 0164fshYSf73ygdUimScheNqlavRcf7hDCtzNpweHkykC6wo0URzMKX
Try a new free decryptor. Read more here – Emsisoft STOP Djvu Ransomware Decryptor – Free way to decrypt encrypted files.
Please return my files to me …iam a teenage and in a high school and my parents cant even pay this ransom
please return my files to me..i have a important files that have been with me more than 5 years when i was young..please help me 🙁
151hTdLhhGtmrC3Q1E91et3xT9ltjomQWQrixcZyE8xrCxfBbq