.Domn file extension on your documents, images and other files means only one thing – you have become a victim of a ransomware attack. During this attack, ransomware was installed on your computer, and all files were encrypted. Many users, like you, have become victims of this virus. Unfortunately, at the moment, there is no way to decrypt files. But, there is one possibility that can allow you to completely restore all encrypted files (files with .Domn extension) to their original state, and you do not need to buy any programs or use difficult steps. Below in our instructions, we will describe in detail how to recover files without decryption.
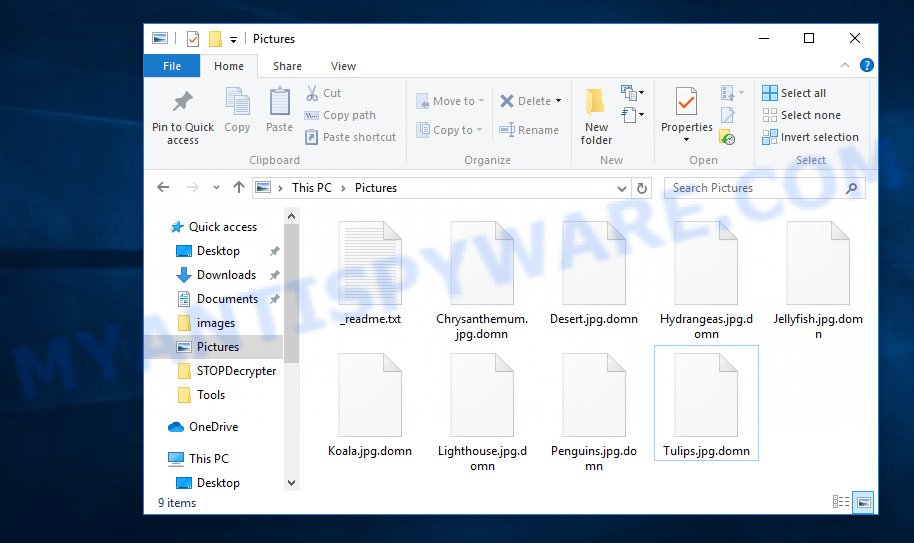
Files encrypted by .Domn virus
According to users who became victims of this virus, each of them installed a program that he had previously downloaded from the Internet. After a short time, they noticed that unexpectedly the extension of their files changed to .domn, e.g. ‘document.doc‘, suddenly became a ‘document.doc.domn‘. Security experts confirm that that this virus is distributed through hacked games, infected free programs, key generators. Immediately after launching the infected program, the virus is activated and begins to encrypt files sequentially, and then change their extension to ‘.domn’. In this way, the virus indicates that the files are encrypted. The virus can encrypt many of the most common file types, such as:
.xls, .xbplate, .wp5, .dbf, .y, .wbmp, .mdb, .zdb, .bc6, .crt, .dcr, .x3d, .dazip, .epk, .xll, .ybk, .cdr, .bkp, .js, .jpeg, .rwl, .jpe, .mddata, .3fr, .rim, .3dm, .ai, .x, .rgss3a, .wp7, .erf, .1, .syncdb, .wpg, .wmv, .hplg, .sis, .ff, .wmf, .desc, .bc7, .odt, .cfr, .wp, .odp, .wmd, .bay, .wgz, .wpd, .wdp, .rtf, .wma, .sav, .wpd, .xar, .menu, .wot, .itl, .rb, .ptx, .p7b, .xpm, .bkf, .big, .m2, .pem, .hkx, .webp, .wri, .sie, .pdf, .rofl, .sql, .vpk, .vcf, .wbz, .t13, .zabw, .wm, .1st, .docx, .forge, .slm, .sum, .xx, .dwg, .bar, .psd, .fsh, .nrw, .itm, .qdf, .ztmp, .iwd, .yml, .cr2, .wp6, .mlx, .py, .mcmeta, .pst, .der, .wbd, .wmv, .wav, .sr2, .w3x, .ods, .pkpass, .sidd, .wsc, .apk, .t12, .wpl, .xlsx, .ppt, .wp4, .indd, .mef, .esm, .dba, .xlgc, .wpw, .wpb, .ltx, .d3dbsp, .mdbackup, .ws, .xlsm, .map, .xld, .eps, .blob, .odb, .p7c, .upk, .png, .xyw, .xml, .mp4, .raw, .srf, .wire, .yal, .wotreplay, .litemod, .mdf, .csv, .wbk, .0, .xmind, .xlsm, .odm, .qic, .xmmap, .gdb, .jpg, .vpp_pc, .xxx, .pak, .orf, .wpt, .xdb, .re4, .docm, .xlk, .lbf, .xlsx, .fos, .rar, .pptx, .xbdoc, .dmp, wallet, .x3f, .asset, .pfx, .avi, .gho, .dng, .ysp, .bik, .itdb, .lrf, .arw, .kdb, .layout, .mov, .xwp, .zdc, .wn, .snx, .wpa, .x3f, .z, .kdc, .pef, .wma, .accdb, .wsh, .hkdb, .zip
When the files are encrypted, in the same directory, the virus creates a file with the name ‘_readme.txt‘, in which the authors of the virus report that all documents are encrypted and require ransom. The authors of the virus suggest that the user write them an email letter in which he will inform his personal code. Upon receiving this email, the attackers will send the address of the Bitcoin wallet to which the ransom must be transferred.
Threat Summary
| Name | Domn virus |
| Type | Ransomware, Crypto malware, Filecoder, File locker, Crypto virus |
| Encrypted files extension | .domn |
| Ransom note | _readme.txt |
| Ransom amount | $980 in Bitcoins |
| Symptoms | Your files fail to open. Your documents, photos and music now have a new extension. Files called like ‘_readme.txt’, ‘READ-ME’, ‘_open me’, _DECRYPT YOUR FILES’ or ‘_Your files have been encrypted” in every folder with an encrypted file. Ransom note in every folder. |
| Distribution methods | Spam mails that contain malicious links. Drive-by downloads from a compromised web page. Social media, such as web-based instant messaging applications. Misleading web sites. |
| Removal | To remove Domn ransomware use the removal guide |
| Decryption | To decrypt Domn ransomware use the free STOP Djvu Ransomware Decryptor |
If you become a victim of the Domn ransomware attack, then the first – do not panic. If you did not have an antivirus, or if your antivirus skipped this virus, and in all other cases, we advise you to check your computer for malware. There is a possibility that the virus is still active on your computer.
Quick links
- How to remove Domn virus
- Is it possible to decrypt .domn files?
- How to restore .domn files (without decryption)
How to remove Domn virus
Most experts say that removing ransomware virus manually without using special tools is very difficult, as it requires special knowledge. If you find instructions where you can press a few ‘magic’ buttons, use safe mode, and so on, then you should know that this is a hoax. We suggest you use several malware removal tools that will allow you to find and remove the Domn virus.
Remove Domn ransomware with Zemana Anti Malware
To find and remove Domn virus, use Zemana Anti Malware. It has powerful capabilities, it can detect and remove a variety of malware, including ransomware. This tool has a simple interface, a quick scanner, and most importantly, all found malware can be removed for free. That is, you do not need to buy anything.

Using the Zemana Anti Malware to remove Domn ransomware is very simple, follow these simple steps.
- Download Zemana AntiMalware from the following link:
Zemana AntiMalware
164813 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- Open a directory in which you saved it and run Zemana.AntiMalware.Setup.
- You will see the “Setup wizard”, follow the prompts.
- Once setup is complete, click the “Scan” button.
- When the scan is complete, simply click “Next” button.
Use KVRT to remove Domn virus
if the Zemana AntiMalware did not find anything, then use the Kaspersky virus removal tool. This program was developed by (c) Kaspersky anti-virus company and has great capabilities. It can easily identify and remove various malicious programs and ransomware. As in the case of Zemana, found malware can be removed completely free of charge.
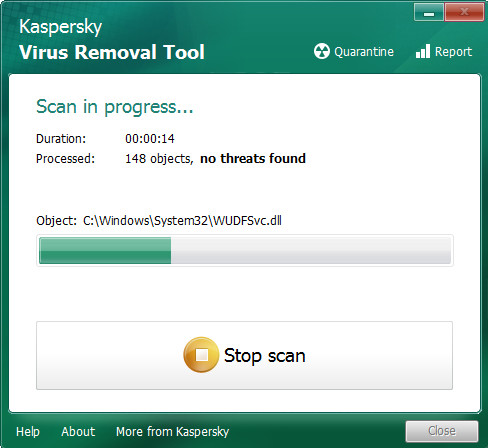
Using the Kaspersky virus removal tool to remove Domn virus is very simple, use the steps below.
- Download Kaspersky virus removal tool (KVRT) from the link:
Kaspersky virus removal tool
129233 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
- Run KVRT.
- Press Start scan button.
- After that process is done, Kaspersky virus removal tool will display a scan report.
- Press Continue to remove detected malware.
Is it possible to decrypt .domn files?
At the moment, all experts say one thing, files encrypted with ‘.domn file extension’ cannot be decrypted. But you must not despair! And of course, do not pay the ransom that attackers demand. All experts are united in this. There is no guarantee that after the transfer of the ransom, your files will be decrypted. Moreover, by paying the ransom, you will push the creators of the virus to develop new ransomware, the victims of which will be even more people. So you need to follow these steps:
- Do not panic
- Do not pay ransom
- Report ransomware attack to the police
- Remove ransomware
- Look for backups of encrypted files
- Try to restore .domn files (without decryption)
Update: good news! A few days ago a free decryptor was released. Below I provide a link where you will find detailed information on where to download it and how to use it to decrypt .domn files.
STOP Djvu Ransomware Decryptor – Free way to decrypt encrypted files
How to restore .domn files (without decryption)
Although it is impossible to decrypt files without an unique key and decryptor, you have a chance to recover all your files for free. Several programs, which are listed below, can help you with this. Once again, I want to note, before you start recovering files, you definitely need to check your computer for malware! Before using the file recovery process, try to use your computer as little as possible, otherwise the chance of successful file recovery will greatly decrease.
Use ShadowExplorer to recover .domn files
If you are sure that there are no active malware on your computer, then it’s time to try to recover the encrypted files. First try the tool, which is named ShadowExplorer. It uses the standard feature of the Windows OS 10 (8, 7 , Vista), which is called ‘Previous Versions’. Using this method, you can recover all your files. There is bad news here, unfortunately, most often the virus disables this feature and deletes all previous versions of files. This may lead to the fact that this method of file recovery may not be suitable for you. But you must try it!
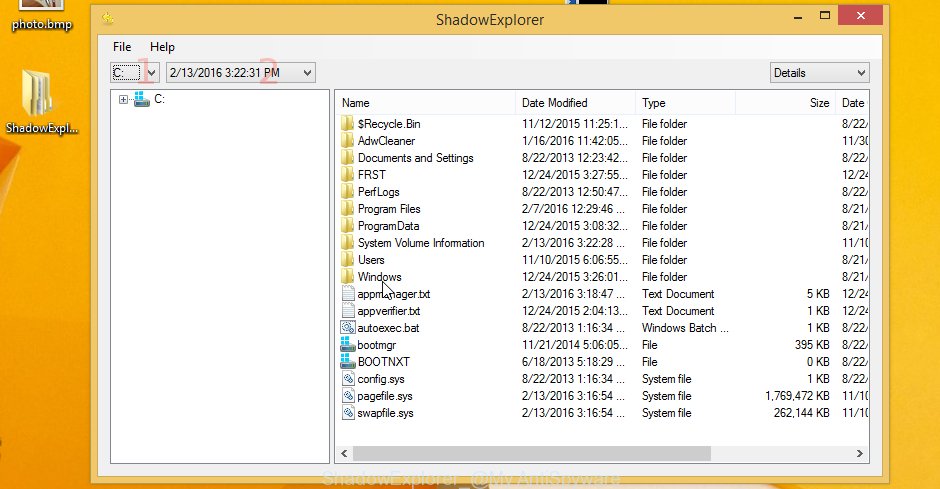
- Download the ShadowExplorer.
ShadowExplorer
439456 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
- Right click to ShadowExplorer-0.9-portable and select Extract all.
- Open the ShadowExplorerPortable folder and run the ShadowExplorer
- Select the disk (1) and the date (2).
- Now navigate to the file or folder that you wish to recover. When ready right-click on it and click ‘Export’ button.
Restore .domn files with PhotoRec
There is another way to recover encrypted files. This is to use a program that is able to find old, deleted and lost files. One such program is a utility called PhotoRec. It has great features, a simple interface, and can recover files for free.
Download PhotoRec from the link below.
Right click to testdisk-7.0.win and choose Extract all. Open the testdisk-7.0 folder as on the image below.

Double click on qphotorec_win to run PhotoRec for Microsoft Windows. It’ll display a screen such as the one below.
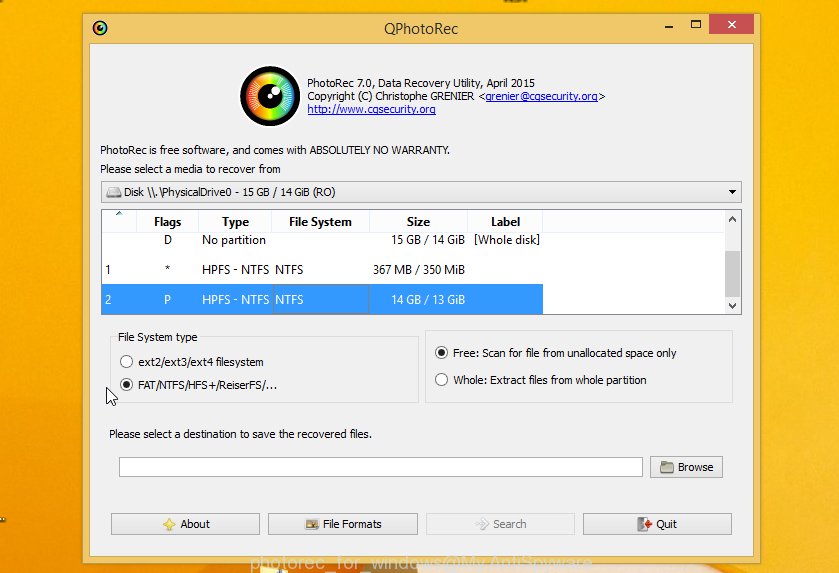
Select a drive to recover as shown in the figure below.
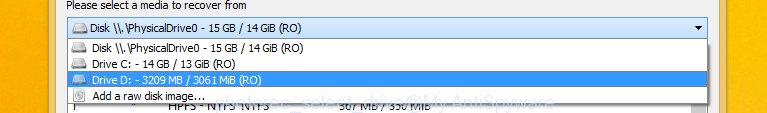
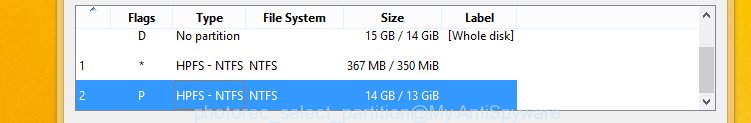
You will see a list of available partitions. Choose a partition that holds encrypted photos, documents and music as displayed in the figure below.
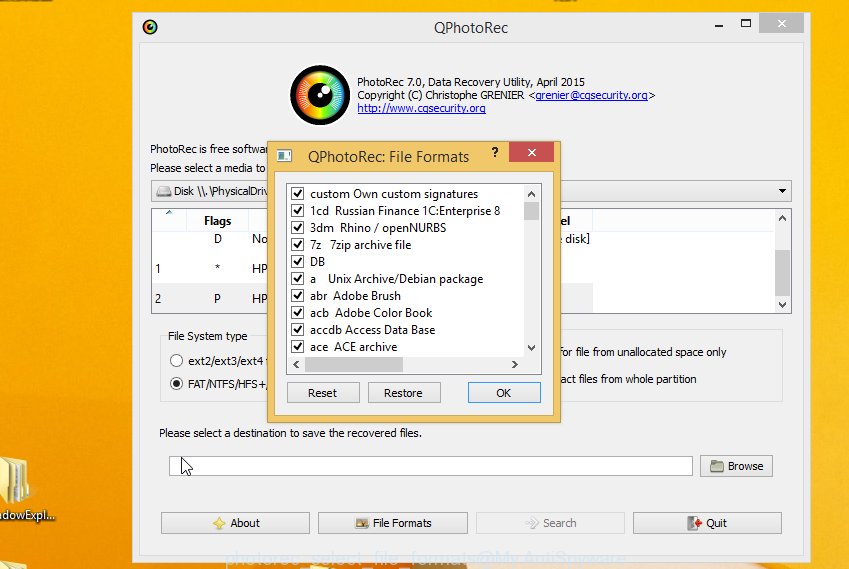
Click File Formats button and select file types to restore. You can to enable or disable the recovery of certain file types. When this is complete, press OK button.
Next, press Browse button to choose where restored documents, photos and music should be written, then click Search.
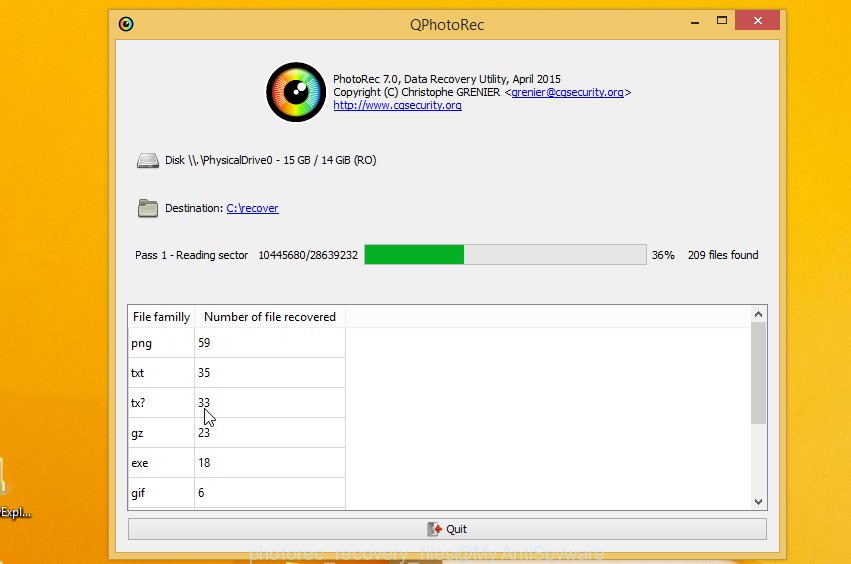
Count of recovered files is updated in real time. All restored personal files are written in a folder that you have chosen on the previous step. You can to access the files even if the recovery process is not finished.
When the recovery is complete, click on Quit button. Next, open the directory where recovered documents, photos and music are stored. You will see a contents as shown on the image below.
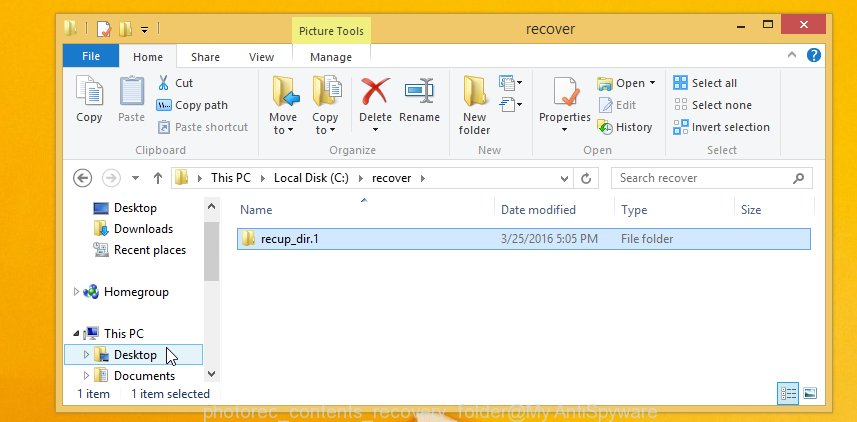
All restored files are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re searching for a specific file, then you can to sort your recovered files by extension and/or date/time.
Finish words
We hopes that these instructions was able to remove the virus and restore the encrypted files. If you have any questions, or you could find another way to recover or decrypt .domn files, then write to us about it. If you need more help with Domn virus related issues, go to here.











The problem got resolved!!!! ” A thing discovered and kept to oneself must be discovered again by others.” Thank you for shared … Thanks a Lot!!! I really appreciate !!!