STOP Djvu Ransomware Decryptor is a free decryptor created by Emsisoft and Michael Gillespie that allows everyone to decrypt files that were encrypted with the STOP ransomware. Currently, this decryptor can decrypt most variants of this ransomware (148 variants). Part of other versions of this ransomware, namely, cases when encrypted files have the extension: .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, can be decrypted using STOP Puma decryptor. Unfortunately, in most cases, it is impossible to decrypt files that are encrypted with new versions of this ransomware (starting from August 2019). If you become a victim of one of these new variants, then at the moment you can only decrypt files that were encrypted with offline keys.
What is STOP Djvu Ransomware
STOP Djvu Ransomware is the most active and widespread ransomware. Like other ransomware, it is designed to encrypt files that can only be decrypted after payment of the ransom. According to the ID Ransomware, to date, more than 450,000 victims have already been discovered, and their number is increasing by approximately 1,500 people every day. The reason for this is that this ransomware is mainly distributed through adware, cracks, free programs and key generators, allowing users to activate paid software. Children, students and many other users, are looking for freeware, download and run it, not knowing that in this way they can allow the ransomware to penetrate on the computer.
Summary
| Name | STOP (Djvu) ransomware |
| Type | Crypto virus, Filecoder, Crypto malware, File locker, Ransomware |
| Encryption algorithm | The ransomware encrypts files using a strong encryption algorithm, which is called Salsa20. |
| Encrypted files extension | .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, .shadow, .djvu, .djvuu, .udjvu, .djvuq, .uudjvu, .djvus, .djvur, .djvut .pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promock, .promoks, .promorad, .promorad2, .kroput, .kroput1, .charck, .pulsar1, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .verasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .forasom, .berost, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidon, .heroset, .myskle, .boston, .muslat, .gerosan, ,vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .tocue, .darus, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, prandel, .zatrov, .masok, .brusaf, londec, .krusop, .mtogas, .coharos, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .stare, .cetori, .carote, .shariz, .gero, .hese, .geno, .xoza, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .noos, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, .grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, .kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt, .cdmx , .cdqw |
| Ransom note | In each directory where the ransomware encrypted the files, it drops a new file (ransom demand message). The very first versions of STOP used the following file names: !!!YourDataRestore!!!.txt, !!!RestoreProcess!!!.txt, !!!INFO_RESTORE!!!.txt, !!RESTORE!!!.txt, !!!!RESTORE_FILES!!!.txt, !!!DATA_RESTORE!!!.txt, !!!RESTORE_DATA!!!.txt, !!!KEYPASS_DECRYPTION_INFO!!!.txt, !!!WHY_MY_FILES_NOT_OPEN!!!.txt, !!!SAVE_FILES_INFO!!!.txt and !readme.txt. Starting with the version that, after encryption, added the .djvu * extension, the ransom note had the following file name: _openme.txt, _open_.txt or _readme.txt. The most recent versions of the STOP Djvu Ransomware use only one file name: _readme.txt. |
| Contacts | STOP ransomware developers often change the email addresses that are used to contact victims, the last of them are listed below: support@freshingmail.top, datarestorehelp@airmail.cc, support@bestyourmail.ch, admin@helpdata.top, manager@time2mail.ch, supportsys@airmail.cc, support@sysmail.ch, helprestoremanager@airmail.cc, manager@mailtemp.ch, supporthelp@airmail.cc, helpteam@mail.ch, restoremanager@airmail.cc, restoreadmin@firemail.cc, restoremanager@firemail.cc, helpdatarestore@firemail.cc, helpmanager@mail.ch, helpmanager@firemail.cc , helpmanager@iran.ir, helprestore@firemail.cc, datarestore@iran.ir, datarestorehelp@firemail.cc, datahelp@iran.ir, restorealldata@firemail.cc, restorefiles@firemail.cc, restoredatahelp@firemail.cc, salesrestoresoftware@firemail.cc, salesrestoresoftware@gmail.com, gorentos@bitmessage.ch |
| Ransom amount | $1999, $999 (if paid within 72 hours) |
| Encryption keys | Security researchers have determined that STOP Djvu Ransomware uses two types of encryption keys. The first one is online keys, the ransomware uses these keys if during encryption it has access to the network and can connect to its command-and-control server. These keys are unique to each computer. The second group is offline keys. The ransomware uses these keys if it does not have a connection to its command-and-control server. These keys are the same for different computers. That is, the same key can be used to decrypt files regardless of which computer they were encrypted on. To date, security researchers have found offline keys for some variants of STOP Djvu Ransomware. |
How to decrypt files encrypted by STOP Djvu Ransomware
Depending on the version of STOP Djvu Ransomware, you need to perform different steps to decrypt files. The version of STOP Djvu can be determined by the extension of the encrypted files. Before decrypting files, you need to be 100% sure that the ransomware is completely removed. We recommend that you use several tools (with different anti-virus engines) to scan your computer and remove STOP Ransomware and other malware. Some of the best and free malware removal tools are listed in this article – Best Free Malware Removal Tools.
1. Old STOP ransomware
A variant of STOP ransomware using the extension: .puma, .pumas, .pumax. All known variants of this ransomware can be decrypted using STOP Puma decryptor. Also, with this decryptor, in some cases, files with the following extension can be decrypted: .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT.
Download the decryptor from the link below
https://www.emsisoft.com/ransomware-decryption-tools/stop-puma
Right-click on the downloaded file (decrypt_STOPPuma.exe) and select “Run as Administartor”. You will be shown the license terms, click yes to continue. The program starts, you will see a window, as in the example below.
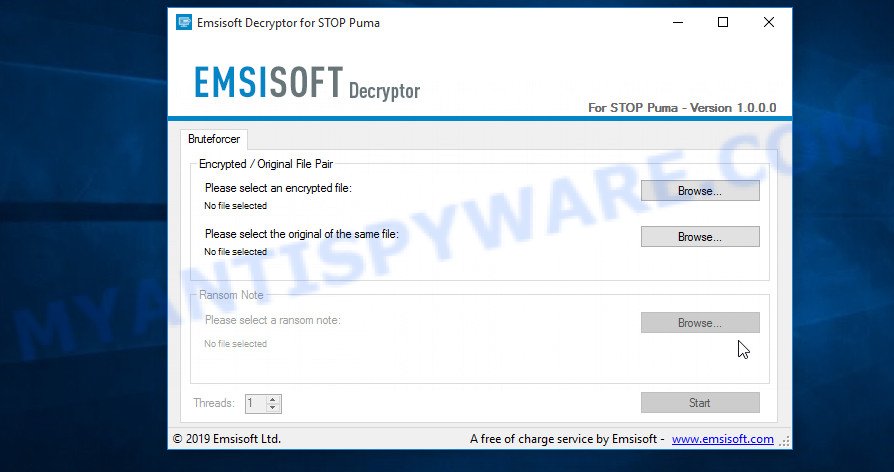
STOP Puma decryptor
As we already reported above, in order to use this decryptor you need one, or better, several pairs of files, one of which is encrypted, and the other is its original version. Having prepared the corresponding pairs, then you need to select them using the corresponding buttons in the program window. When ready, press the Start button. As soon as the key is found, the decryptor will immediately inform you. In some cases, an error may occur while searching for a key, therefore we recommend using several pairs of files to be sure that the correct key has been found.
After the correct key is found, you will be able to decrypt the files. Select the location where the encrypted files are located and click the Decrypt button.
2. STOP Djvu ransomware
A variant of the STOP Djvu ransomware using the extension: .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote.
In order to decrypt files you need to find several pairs of files. Each pair of files consists of an encrypted file and its original copy. File size over 150kb. After you find several pairs of files, do the following. Open the following link in a new window.
https://decrypter.emsisoft.com/submit/stopdjvu/
You will see a page called STOP Djvu Decryption. An example of this page is given below.
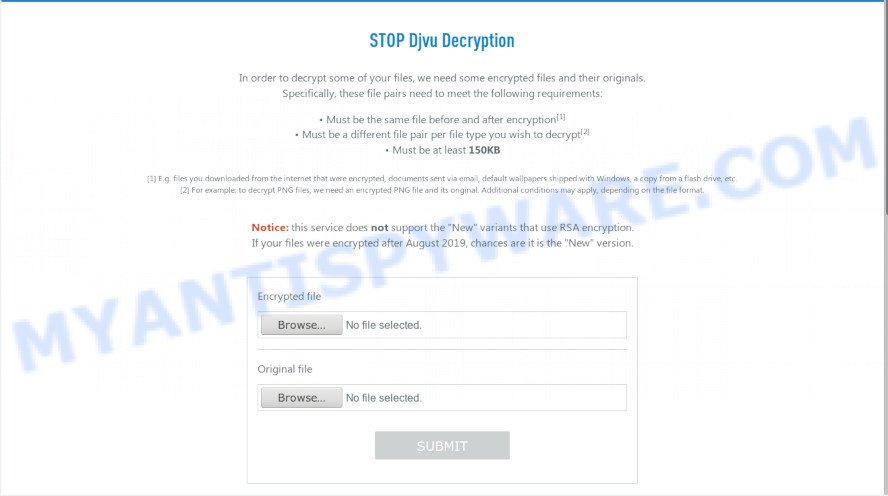
STOP Djvu Decryption
On this page using the Browse button, enter the path to the encrypted file and its original copy, then click the Submit button. After clicking on the Submit button, your files will be uploaded to the server. Then the key search process starts. Please be patient, this process may take some time. As soon as the key is found, an appropriate message will appear on the page and you will be asked to download the decryptor.
Click on the link called “Click here to download the decryptor“. The page from which you can download the decryptor will load. Click the Download button and save the decrypt_STOPDjvu.exe file to your computer.
When the file is downloaded, start it by right-clicking on it and selecting item “Run as Administrator”. When it starts, the Windows can show you UAC Promt, then click Yes. After that, you will be shown the license terms and a small instruction, please read this information to continue.
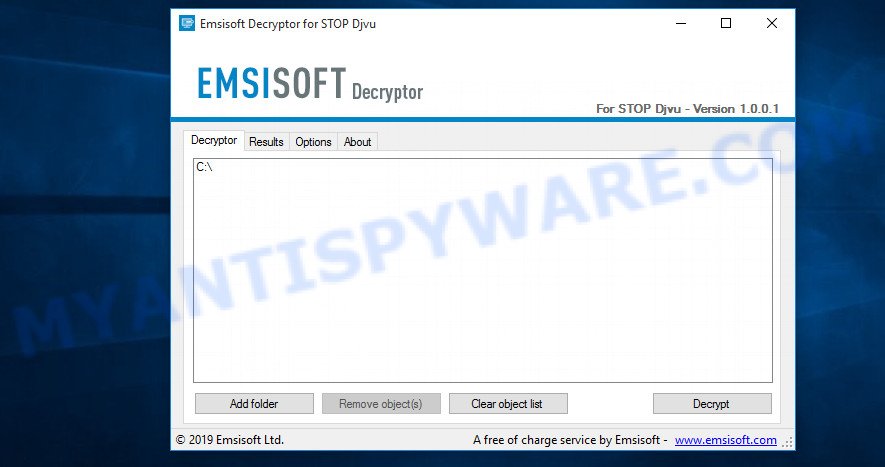
STOP Djvu decryptor
In the main window, select the disk or directory where the encrypted files are located, and then click Decrypt. After that, the decryptor will begin to decrypt the files for which the key was found at the previous stage. If the decryptor skips files, saying that it cannot decrypt them, then you need to again find a couple of files, one of which is encrypted, and the second is its original copy. Then use them to find the decryption key.
3. New Djvu ransomware
The latest version of STOP Djvu ransomware uses the following file extensions: .coharos, .shariz, .gero, .hese, .geno, .xoza, .seto, peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, gcyi, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt. An updated variant of this version appears every few days, the main difference between all variants is the extension of encrypted files. The last variant encrypts files with the .qqmt extension; the personal ID of the victims of this variant starts with 0540.
At the moment, it is possible to decrypt files only in some cases when they are encrypted using an offline key. To decrypt files, download the decryptor using the following link.
https://www.emsisoft.com/ransomware-decryption-tools/stop-djvu
Click the Download button and save the decrypt_STOPDjvu.exe file to your computer. Right click to it and select ‘Run as Administrator’. Confirm permission to run the program by pressing the Yes button. Read the license terms and brief instructions. In the main window that opens, select the disk or folder where the encrypted files are located and click the Decrypt button. If the decryptor skips files without decrypting them, then the offline key for them is unknown or they are encrypted with an online key.
This video step-by-step guide will demonstrate How to decrypt files locked by STOP Djvu ransomware.
Finish words
We hope that the set of utilities and services developed by Emsisoft and Michael Gillespie helped you decrypt all the files. If the decryption of the files failed, then do not forget that there is another way to recover your files – is to use data recovery tools. Details on how to recover encrypted files without a key and decryptor are described in the article:
How To Recover Encrypted Files (Ransomware file recovery).










To get this software you need write on our e-mail:
helpdatarestore@firemail.cc
Reserve e-mail address to contact us:
helpmanager@mail.ch
Your personal ID:
0216OIWojlj48dhZkx7JFklrYKxQtkVUoGfAAjoSPDW5TjdsFax5a
what can be done with it?
my 300 gbs data encrypted
The “0216OIWojlj48dhZkx7JFklrYKxQtkVUoGfAAjoSPDW5TjdsFax5a” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-PHJh5SU4jT
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpdatarestore@firemail.cc
Reserve e-mail address to contact us:
helpmanager@mail.ch
Your personal ID:
0217OIWojlj488TaHEsq5r7cNJKbYdWseLEB2pW1FuZKoKjKg5tt1
It looks like your files are encrypted with an offline key, because your personal id ends with ‘t1’. Your files can be decrypted using the free decryptor. But unfortunately, at the moment, the security researchers have not yet determined the offline key, so right now it will not be possible to decrypt the files. So you need to wait, once a week try to decrypt your files.
Pls help me.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-nb2ThWY25i
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
helpdatarestore@firemail.cc
Your personal ID:
0221yiuduy6S5d2dnYmJewJfOa6JvZwJQbfiWJapb8pOCDcMofvLOv
The “0221yiuduy6S5d2dnYmJewJfOa6JvZwJQbfiWJapb8pOCDcMofvLOv” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-svMd2A4k89
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
helpdatarestore@firemail.cc
Your personal ID:
0222yiuduy6S5drm7Qdt7wTiwQaaCrpGrnos6N65y5lE29aTb9yvt1
– Sir, what about my case?
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-BxcdyO2dt7
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
helpdatarestore@firemail.cc
Your personal ID:
0223yiuduy6S5daA1AJUyEaKgSsYERp8kWwNTzOwKW5Zo0Gm6og6CC
help me please
File: A:\musics\bo phyu3\BOPHYU ( TAUNGHSA) (7).m4a.lezp
No key for New Variant online ID: sNROgM9d1RNmKS4HlvdvXJ126bTaDLOhHZs3EXFX
Notice: this ID appears to be an online ID, decryption is impossible
The “sNROgM9d1RNmKS4HlvdvXJ126bTaDLOhHZs3EXFX” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
ATTENTION! Help Me.
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-Be28TGxMAy
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helprestore@firemail.cc
Reserve e-mail address to contact us:
datarestore@iran.ir
Your personal ID:
0194Asd374y5iuhldPlPRiENN3L3VEU9hJcq3VbF9bCQPUhMyZ1t7t7xX
The “0194Asd374y5iuhldPlPRiENN3L3VEU9hJcq3VbF9bCQPUhMyZ1t7t7xX” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
I can not recover my files from .sqpc.KJHslgjkjdfg
It looks like your files have been encrypted twice, by different types of ransomware. Therefore, it is unlikely that you can decrypt your files, but there is little hope that you will be able to recover the contents of the encrypted files. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
PLEASE HELP ME
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-28bBaI3ZOZ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@firemail.cc
Your personal ID:
0227yiuduy6S5dCWi4oLdtIpusbbMtycrIeZ3XIVc4G0xgM3TRcie0
The “0227yiuduy6S5dCWi4oLdtIpusbbMtycrIeZ3XIVc4G0xgM3TRcie0” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0228OIdshyeFO8C23DZ3lReQ1fdfiS7ZKdpvkNKRyqGhVXhuG8xe
Please is there a way to restore the lost files, so this virus has taken over all the files so very important that it is for study and I do not have this amount
The “0228OIdshyeFO8C23DZ3lReQ1fdfiS7ZKdpvkNKRyqGhVXhuG8xe” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0228OIdshyeFmXskoIZ6Oc5S6wHPo7mMWSTmllehNCDeWELvzbFD
The “0228OIdshyeFmXskoIZ6Oc5S6wHPo7mMWSTmllehNCDeWELvzbFD” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0228OIdshyeFn3wVQQxbGwkYNCuQUF1Q2nHbLI9UG3NEB3Amcmyu
The “0228OIdshyeFn3wVQQxbGwkYNCuQUF1Q2nHbLI9UG3NEB3Amcmyu” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
0229yiuduy6S5dYNU1A2FW3Y29wfbulMnxYPV7Sh1ff107Sh9rOVyG online or offline?
The “0229yiuduy6S5dYNU1A2FW3Y29wfbulMnxYPV7Sh1ff107Sh9rOVyG” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0229yiuduy6S5dsSPkKCjgQeU5tOm5c2WsVGtDTdXbck9LJEfHYuY3
Online or offline?
The “0229yiuduy6S5dsSPkKCjgQeU5tOm5c2WsVGtDTdXbck9LJEfHYuY3” ID is related to an online key, so files cannot be decrypted.
I get this message:
File: G:\Fotos Recuerdo Fam Moya\Neco.jpg.redl
No key for New Variant online ID: syh7Kcu5h2MDTnKpx2wfOSs2lw2E9FpTIXWPqFOJ
Notice: this ID appears to be an online ID, decryption is impossible
How decrypt this, help me
The “syh7Kcu5h2MDTnKpx2wfOSs2lw2E9FpTIXWPqFOJ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Please Help me to Decrypt Data
Your personal ID:
0229yiuduy6S5dqvPIEIoqOJQhH7wxeKQypporjBLOyybR1mC540pp
The “0229yiuduy6S5dqvPIEIoqOJQhH7wxeKQypporjBLOyybR1mC540pp” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0233yiuduy6S5dSw174j7Cx895T2yzs6yw69a4vhQLz1rxRrgbRyDb
The “0233yiuduy6S5dSw174j7Cx895T2yzs6yw69a4vhQLz1rxRrgbRyDb” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Hello
Please help me, I got all file encrypted by .btos and I already reformat the windows and backup all files from “D” to my portable disk. Is it possible to decrypt this?
To get this software you need write on our e-mail:
helpmanager@firemail.cc
Reserve e-mail address to contact us:
helpmanager@iran.ir
Your personal ID:
0202a7d6a8sda52T8sTfFXbzP7HatoDerXODiUia2zLAqiGwmW6mG
The “0202a7d6a8sda52T8sTfFXbzP7HatoDerXODiUia2zLAqiGwmW6mG” ID is related to an online key, so files cannot be decrypted. Decryption will be possible as soon as the security researchers obtain a master key that the btos ransomware authors have.
Your personal ID:
0234yiuduy6S5dmpUq1hFj8qrgipZbvOWZ3wTYu13cxFrRm5QTB6Nm
How can I Decrypt my files ??
The “0234yiuduy6S5dmpUq1hFj8qrgipZbvOWZ3wTYu13cxFrRm5QTB6Nm” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
how to decrypt .usam file plzzzhelp me
To decrypt .usam files, use EmsiSoft decryptor, but .usam files can be decrypted only if the files are encrypted with an offline key. If the files are encrypted with an online key, then they cannot be decrypted. But there is a chance to restore the contents of encrypted files, for this, use the following guide: How to recover encrypted files.
please held me to decrypt data
personal ID:
0233yiuduy6S5dvRJ8slDPoMhm8b6TDz4GvhrjDsVfZWoXvsGAEr7X
The “0233yiuduy6S5dvRJ8slDPoMhm8b6TDz4GvhrjDsVfZWoXvsGAEr7X” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0235yiuduy6S5dErRUjcEsrUPUKuZTeehNSkRXfJAvtv1nfePjC3OZ
Is it online or offline id
The “0235yiuduy6S5dErRUjcEsrUPUKuZTeehNSkRXfJAvtv1nfePjC3OZ” ID is related to an online key.
Your personal ID:
0236yiuduy6S5dNI7vuebSWKlFwAWe2aZTehT4Pjymuqfxe0faYIlm
The “0236yiuduy6S5dNI7vuebSWKlFwAWe2aZTehT4Pjymuqfxe0faYIlm” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
ID: 0236yiuduy6S5dWP1E0b5UeghgK0raCXVQcsrI8NOZLkOngWOSj4kK extension ransomware .moba can you help me
The “0236yiuduy6S5dWP1E0b5UeghgK0raCXVQcsrI8NOZLkOngWOSj4kK” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0233yiuduy6S5deg2A9oFAUrDH6ljqMRggqCfEYRqZzPTG5c3tiXsi
what is my case sir ..?
The “0233yiuduy6S5deg2A9oFAUrDH6ljqMRggqCfEYRqZzPTG5c3tiXsi” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Hello
Please help me, I got all file encrypted by .btos and I already reformat the windows and backup all files from “D” to my portable disk. Is it possible to decrypt this?
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
restoremanager@airmail.cc
Your personal ID:
0236yiuduy6S5dQohavPJddGoAOd2S8ov3wbjZ6qee7OWqEH11y2wL
The “0236yiuduy6S5dQohavPJddGoAOd2S8ov3wbjZ6qee7OWqEH11y2w” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
File: C:\$SysReset\Logs\PushButtonReset.etl.koti
No key for New Variant online ID: uZ8CNC7jv6gpkyu8nwQPupaNdddacyjaMOOU7u9f
Notice: this ID appears to be an online ID, decryption is impossible.
got 300Gb+ of school files 🙁
The “uZ8CNC7jv6gpkyu8nwQPupaNdddacyjaMOOU7u9f” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
how can i decrypt my data my id is 361IQWGs9YDR5sZEo3Zc6j5arusOIWhTRDtf1BPU my data is not dycrypted
Help me, My Id is 0236yiuduy6S5djTaV6IbBkmMA1IpdOSJdyS97C8vvniCLD5J6ncQ3. Is it Online or Offline key? Can i decrypt it?
The “0236yiuduy6S5djTaV6IbBkmMA1IpdOSJdyS97C8vvniCLD5J6ncQ3” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.