STOP Djvu Ransomware Decryptor is a free decryptor created by Emsisoft and Michael Gillespie that allows everyone to decrypt files that were encrypted with the STOP ransomware. Currently, this decryptor can decrypt most variants of this ransomware (148 variants). Part of other versions of this ransomware, namely, cases when encrypted files have the extension: .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, can be decrypted using STOP Puma decryptor. Unfortunately, in most cases, it is impossible to decrypt files that are encrypted with new versions of this ransomware (starting from August 2019). If you become a victim of one of these new variants, then at the moment you can only decrypt files that were encrypted with offline keys.
What is STOP Djvu Ransomware
STOP Djvu Ransomware is the most active and widespread ransomware. Like other ransomware, it is designed to encrypt files that can only be decrypted after payment of the ransom. According to the ID Ransomware, to date, more than 450,000 victims have already been discovered, and their number is increasing by approximately 1,500 people every day. The reason for this is that this ransomware is mainly distributed through adware, cracks, free programs and key generators, allowing users to activate paid software. Children, students and many other users, are looking for freeware, download and run it, not knowing that in this way they can allow the ransomware to penetrate on the computer.
Summary
| Name | STOP (Djvu) ransomware |
| Type | Crypto virus, Filecoder, Crypto malware, File locker, Ransomware |
| Encryption algorithm | The ransomware encrypts files using a strong encryption algorithm, which is called Salsa20. |
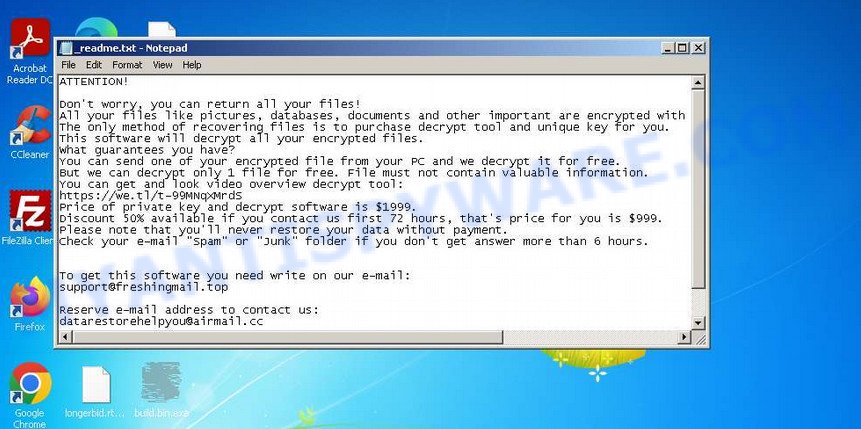
| Encrypted files extension | .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT, .puma, .pumax, .pumas, .shadow, .djvu, .djvuu, .udjvu, .djvuq, .uudjvu, .djvus, .djvur, .djvut .pdff, .tro, .tfude, .tfudeq, .tfudet, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promock, .promoks, .promorad, .promorad2, .kroput, .kroput1, .charck, .pulsar1, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .verasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .forasom, .berost, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidon, .heroset, .myskle, .boston, .muslat, .gerosan, ,vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .tocue, .darus, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, prandel, .zatrov, .masok, .brusaf, londec, .krusop, .mtogas, .coharos, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .stare, .cetori, .carote, .shariz, .gero, .hese, .geno, .xoza, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .noos, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, .grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, .kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt, .cdmx , .cdqw |
| Ransom note | In each directory where the ransomware encrypted the files, it drops a new file (ransom demand message). The very first versions of STOP used the following file names: !!!YourDataRestore!!!.txt, !!!RestoreProcess!!!.txt, !!!INFO_RESTORE!!!.txt, !!RESTORE!!!.txt, !!!!RESTORE_FILES!!!.txt, !!!DATA_RESTORE!!!.txt, !!!RESTORE_DATA!!!.txt, !!!KEYPASS_DECRYPTION_INFO!!!.txt, !!!WHY_MY_FILES_NOT_OPEN!!!.txt, !!!SAVE_FILES_INFO!!!.txt and !readme.txt. Starting with the version that, after encryption, added the .djvu * extension, the ransom note had the following file name: _openme.txt, _open_.txt or _readme.txt. The most recent versions of the STOP Djvu Ransomware use only one file name: _readme.txt. |
| Contacts | STOP ransomware developers often change the email addresses that are used to contact victims, the last of them are listed below: support@freshingmail.top, datarestorehelp@airmail.cc, support@bestyourmail.ch, admin@helpdata.top, manager@time2mail.ch, supportsys@airmail.cc, support@sysmail.ch, helprestoremanager@airmail.cc, manager@mailtemp.ch, supporthelp@airmail.cc, helpteam@mail.ch, restoremanager@airmail.cc, restoreadmin@firemail.cc, restoremanager@firemail.cc, helpdatarestore@firemail.cc, helpmanager@mail.ch, helpmanager@firemail.cc , helpmanager@iran.ir, helprestore@firemail.cc, datarestore@iran.ir, datarestorehelp@firemail.cc, datahelp@iran.ir, restorealldata@firemail.cc, restorefiles@firemail.cc, restoredatahelp@firemail.cc, salesrestoresoftware@firemail.cc, salesrestoresoftware@gmail.com, gorentos@bitmessage.ch |
| Ransom amount | $1999, $999 (if paid within 72 hours) |
| Encryption keys | Security researchers have determined that STOP Djvu Ransomware uses two types of encryption keys. The first one is online keys, the ransomware uses these keys if during encryption it has access to the network and can connect to its command-and-control server. These keys are unique to each computer. The second group is offline keys. The ransomware uses these keys if it does not have a connection to its command-and-control server. These keys are the same for different computers. That is, the same key can be used to decrypt files regardless of which computer they were encrypted on. To date, security researchers have found offline keys for some variants of STOP Djvu Ransomware. |
How to decrypt files encrypted by STOP Djvu Ransomware
Depending on the version of STOP Djvu Ransomware, you need to perform different steps to decrypt files. The version of STOP Djvu can be determined by the extension of the encrypted files. Before decrypting files, you need to be 100% sure that the ransomware is completely removed. We recommend that you use several tools (with different anti-virus engines) to scan your computer and remove STOP Ransomware and other malware. Some of the best and free malware removal tools are listed in this article – Best Free Malware Removal Tools.
1. Old STOP ransomware
A variant of STOP ransomware using the extension: .puma, .pumas, .pumax. All known variants of this ransomware can be decrypted using STOP Puma decryptor. Also, with this decryptor, in some cases, files with the following extension can be decrypted: .STOP, .SUSPENDED, .WAITING, .PAUSA, .CONTACTUS, .DATASTOP, .STOPDATA, .KEYPASS, .WHY, .SAVEfiles, .DATAWAIT, .INFOWAIT.
Download the decryptor from the link below
https://www.emsisoft.com/ransomware-decryption-tools/stop-puma
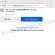
Right-click on the downloaded file (decrypt_STOPPuma.exe) and select “Run as Administartor”. You will be shown the license terms, click yes to continue. The program starts, you will see a window, as in the example below.
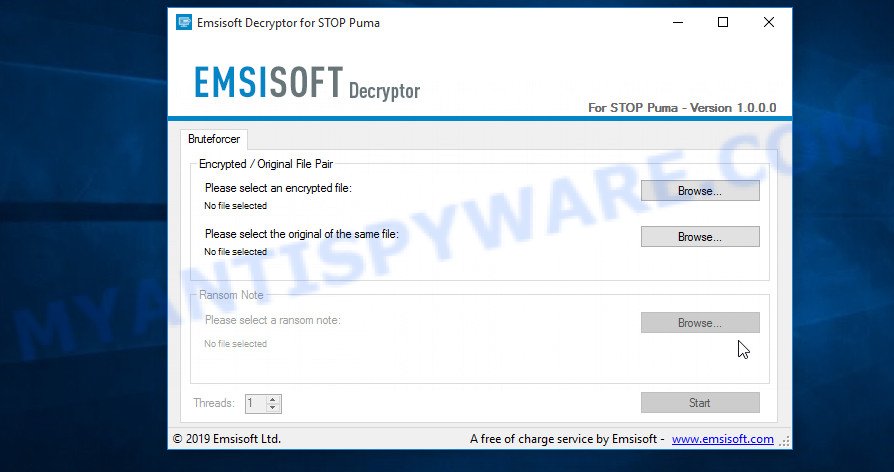
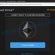
STOP Puma decryptor
As we already reported above, in order to use this decryptor you need one, or better, several pairs of files, one of which is encrypted, and the other is its original version. Having prepared the corresponding pairs, then you need to select them using the corresponding buttons in the program window. When ready, press the Start button. As soon as the key is found, the decryptor will immediately inform you. In some cases, an error may occur while searching for a key, therefore we recommend using several pairs of files to be sure that the correct key has been found.
After the correct key is found, you will be able to decrypt the files. Select the location where the encrypted files are located and click the Decrypt button.
2. STOP Djvu ransomware
A variant of the STOP Djvu ransomware using the extension: .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote.
In order to decrypt files you need to find several pairs of files. Each pair of files consists of an encrypted file and its original copy. File size over 150kb. After you find several pairs of files, do the following. Open the following link in a new window.
https://decrypter.emsisoft.com/submit/stopdjvu/
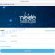
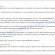
You will see a page called STOP Djvu Decryption. An example of this page is given below.
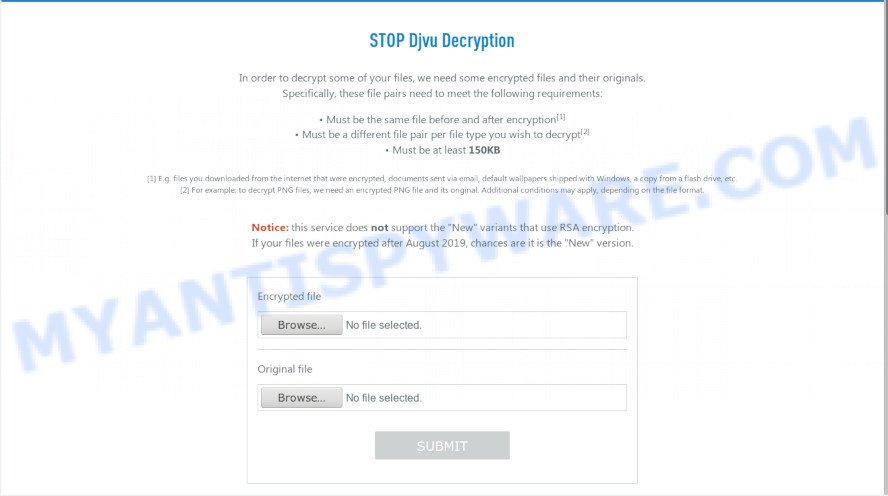
STOP Djvu Decryption
On this page using the Browse button, enter the path to the encrypted file and its original copy, then click the Submit button. After clicking on the Submit button, your files will be uploaded to the server. Then the key search process starts. Please be patient, this process may take some time. As soon as the key is found, an appropriate message will appear on the page and you will be asked to download the decryptor.
Click on the link called “Click here to download the decryptor“. The page from which you can download the decryptor will load. Click the Download button and save the decrypt_STOPDjvu.exe file to your computer.
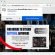
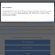
When the file is downloaded, start it by right-clicking on it and selecting item “Run as Administrator”. When it starts, the Windows can show you UAC Promt, then click Yes. After that, you will be shown the license terms and a small instruction, please read this information to continue.
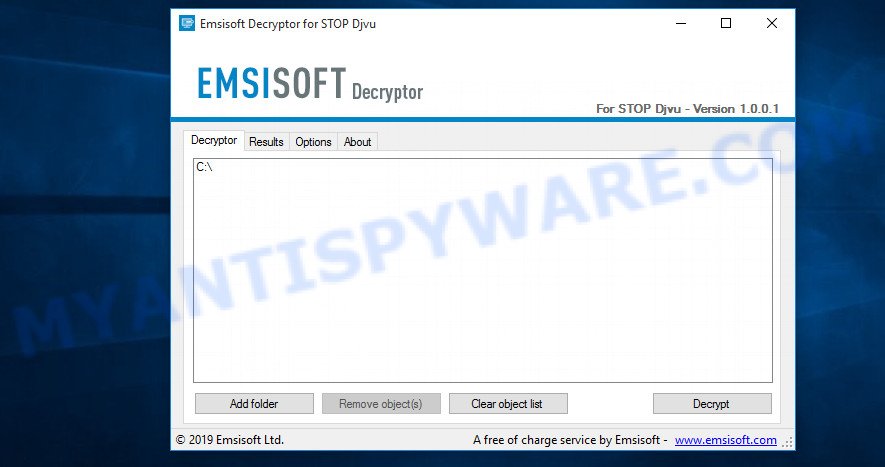
STOP Djvu decryptor
In the main window, select the disk or directory where the encrypted files are located, and then click Decrypt. After that, the decryptor will begin to decrypt the files for which the key was found at the previous stage. If the decryptor skips files, saying that it cannot decrypt them, then you need to again find a couple of files, one of which is encrypted, and the second is its original copy. Then use them to find the decryption key.
3. New Djvu ransomware
The latest version of STOP Djvu ransomware uses the following file extensions: .coharos, .shariz, .gero, .hese, .geno, .xoza, .seto, peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .boot, .kuub, .reco, .bora, .leto, nols, werd, .coot, .derp, .nakw, .meka, .toec, .mosk, .lokf, .peet, grod, .mbed, .kodg, .zobm, .rote, .msop, .hets, .righ, .gesd, .merl, .nbes, .mkos, .piny, .redl, kodc, .nosu, .reha, .topi, .npsg, .btos, .repp, .alka, .bboo, rooe, .mmnn, .ooss, .mool, .nppp, .rezm, .lokd, .foop, .remk, .npsk, opqz, .mado, jope, .mpaj, .lalo, .lezp, .qewe, .mpal, .sqpc, .mzlq, .koti, .covm, .pezi, .nlah, .kkll, .zwer, .nypd, .usam, .tabe, .vawe, .moba, .pykw, .zida, .maas, .repl, .kuus, .erif, .kook, .nile, .oonn, .vari, .boop, .kasp, .ogdo, .npph, .kolz, .copa, .lyli, .moss, .foqe, .mmpa, .efji, .iiss, .jdyi, .vpsh, .agho, .vvoa, .epor, .sglh, .lisp, .weui, .nobu, .igdm, .booa, .omfl, igal, .qlkm, .coos, .wbxd, .pola, .cosd, .plam, .ygkz, .cadq, .ribd, .tirp, .reig, .enfp, .ekvf, .ytbn, .fdcz, .urnb, .lmas, .wrui, .rejg, .pcqq, .igvm, .nusm, .ehiz, .paas, .pahd, .mppq, .qscx, .sspq, .iqll, .ddsg, .piiq, .miis, .neer, .leex, .zqqw, .pooe, .lssr, .zzla, .wwka, .gujd, .ufwj, .moqs, .aeur, .guer, .nooa, .reqg, .hoop, .orkf, .lqqw, .efdc, .wiot, .koom, .rigd, .tisc, .nqsq, .irjg, .vtua, .maql, .zaps, .rugj, .cool, .palq, .stax, .irfk, .qdla, .futm, .utjg, .iisa, .pqgs, .rigj, .robm, .moia, .wnlu, .hgsh, .nnqp, .miia, .loov, .dehd, .nqhd, .vfgj, .maak, .qqqw, .yoqs, .avyu, .cuag, .iips, .qnty, .ccps, .ckae, gcyi, .eucy, .ooii, .rtgf, .fgui, .fgnh, .iiof, .vyia, .vtym, .kqgs, .bpqd, .rguy, .kkia, .mmuz, .wdlo, .kxde, .udla, .mpag, .gtys, .tuid, .uyjh, .msjd, .jhdd, .dmay, .jhbg, .dewd, .sijr, .bbnm, .byya, .ifla, .errz, .dfwe, .fdcv, .nnuz, .qlln, .rrbb, .rryy, .bbyy, .bbii, .bbzz, .hkgt, .efvc, .lltt, .lloo, .llee, .dkrf, .eiur, .ghsd, .jjll, .hhew, .hhwq, .ggew, .ggeo, .ggwq, .ggyu, .ooxa, .oori, .vvew, .vvyu, .vvwq, .vveo, .vvyu, .qqmt. An updated variant of this version appears every few days, the main difference between all variants is the extension of encrypted files. The last variant encrypts files with the .qqmt extension; the personal ID of the victims of this variant starts with 0540.
At the moment, it is possible to decrypt files only in some cases when they are encrypted using an offline key. To decrypt files, download the decryptor using the following link.
https://www.emsisoft.com/ransomware-decryption-tools/stop-djvu
Click the Download button and save the decrypt_STOPDjvu.exe file to your computer. Right click to it and select ‘Run as Administrator’. Confirm permission to run the program by pressing the Yes button. Read the license terms and brief instructions. In the main window that opens, select the disk or folder where the encrypted files are located and click the Decrypt button. If the decryptor skips files without decrypting them, then the offline key for them is unknown or they are encrypted with an online key.
This video step-by-step guide will demonstrate How to decrypt files locked by STOP Djvu ransomware.
Finish words
We hope that the set of utilities and services developed by Emsisoft and Michael Gillespie helped you decrypt all the files. If the decryption of the files failed, then do not forget that there is another way to recover your files – is to use data recovery tools. Details on how to recover encrypted files without a key and decryptor are described in the article:
How To Recover Encrypted Files (Ransomware file recovery).










I forgot to write my personal ID = 0300ewgfDdhwb1IM9fCNtHCrBW48pFJ826Rw0zqyNBCVIQ8XPs
Please help me with this ID
Thank you
key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
ID
0300ewgfDdpostKmHvGyq3qS4X5veNFaQHXglpkwrbT8tCqSTA
Hello,can u tell me is this online or offline
id:
0300ewgfDdmJl7xjAhONiAmOBFlgZX7wxBcaU0cmqP5IyB3bJ9
Reserve e-mail address to contact us:
helpmanager@airmail.cc
is encrypted files with PAHD extension
Your personal ID:
0301ewgfDdP2YqUoKIZTRA3xdMGOkHCNgNvmVa2RlAs3qG4DMo
Is it possible to decrypt it?
thanks for this help and information.
The “0301ewgfDdP2YqUoKIZTRA3xdMGOkHCNgNvmVa2RlAs3qG4DMo” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
I have encrypted files with ‘.zwer’ extension with personal id “0300ewgfDd5Ss4T6j69i1QvXEQFvNAh6BU8ExhCMdtgNMydgel”. Is it possible to decrypt it?
The “0300ewgfDd5Ss4T6j69i1QvXEQFvNAh6BU8ExhCMdtgNMydgel” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
my files has .qscx please help my personal ID:0303ewgfDdXTlKYyV0kRohntC8wc7d5eZD6mLCdRFTOMKVszgP
The “0303ewgfDdXTlKYyV0kRohntC8wc7d5eZD6mLCdRFTOMKVszgP” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
hello how i find my personal id was online or offline
Your personal ID:
0303ewgfDdnVT49jKrLmZhTQ6uSlnIX5DnZQgxYswy5moGQO1C
How to decrypt .neer ransomware files affected by online id.?
Kindly please provide me the solution because i need all my file back, as Emisoft doesn’t has the solution for online key id..
if the files are encrypted with an online key, it is impossible to decrypt them, since only the authors of the virus have the decryption key. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
i have encrypted files with .mppq
Personal ID : 0302ewgfDdCAHqSDPEdM7NuTEJqwUgeScxRqVsEJ73XBXLQq1R
Can I recover my file?
My ID is: 0303ewgfDdMtviBkRLqAFHgcMkfHg0CJeDl7JCh8zpL720zC9c
Hello,
Help me my all file encrypted
I’m worried about my all data was encrypted
I have encrypted with ‘.sspq.’ extension. Is it possible to decrypt it??
my files has .iqll
please help
Your personal ID:
0305ewgfDdppmn5q6DzrybvhIkCuuqaearFxJ8Rc3difSaWft1
Can it be decripted?
Your files are encrypted with an offline key. Therefore, first try this decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec. If these utilities did not help to recover the files, then you just have to wait for the moment when decryption becomes possible.
need help, i’ve try that tool, but isnt work for me. i’ve infected with .ddgs (djvu) virus and i’ve the offline-key: “ppmn5q6DzrybvhIkCuuqaearFxJ8Rc3difSaWft1” can u help?
oh sorry, that wasnt my key, thats my key: 0306ewgfDdppmn5q6DzrybvhIkCuuqaearFxJ8Rc3difSaWft1
Your files are encrypted with an offline key. Therefore, first try this decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec. If these utilities did not help to recover the files, then you just have to wait for the moment when decryption becomes possible.
i only have my study files and some pics
this was happened when i wanted to install an app
guys can anyone tell me how to solve this problem
Your personal ID:
0310ewgfDdLTYv5JAYPKU9SqYbMp9sbHbkMoA4JlKc46dTaLt1
Your files are encrypted with an offline key. Therefore, first try this decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec. If these utilities did not help to recover the files, then you just have to wait for the moment when decryption becomes possible.
“0310ewgfDdyyf4051m72slBdmejb5AG2dIJtsGNo1cOSko4r6b”
This is my personal id,
My file extension is .neer
The “0310ewgfDdyyf4051m72slBdmejb5AG2dIJtsGNo1cOSko4r6b” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
I read the .neer files are decryptable using the Stop Decryptor. I tried the decryptor but it says it is not decryptable. The extension of my encrypted files are ( .neer ). The personal ID is
Your personal ID:
0310ewgfDdiBD2KWf5p77rwUAEplzG4r3nQE9NQVXq2cTZtlln
The “0310ewgfDdiBD2KWf5p77rwUAEplzG4r3nQE9NQVXq2cTZtlln” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0310ewgfDdyC7GEoaKfDva2itrSdQPyjrh1Qtc1zii0LhlYfWd
is it posible to re
The “0310ewgfDdyC7GEoaKfDva2itrSdQPyjrh1Qtc1zii0LhlYfWd” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
sir i was encrypted with “.neer” extension with personal id
“0310ewgfDdOCemdDVx4nujbPxfEJVdRAuRvTICRYX0c2O5YXga”
plz help me sir
The “0310ewgfDdOCemdDVx4nujbPxfEJVdRAuRvTICRYX0c2O5YXga” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Hi, I really need help. How can I decrypt my files? all my files are “.neer” now.
It’s Offline Key, with t1 at the last words.
My personal ID:
0310ewgfDdLTYv5JAYPKU9SqYbMp9sbHbkMoA4JlKc46dTaLt1
thank you
Your files are encrypted with an offline key. Therefore, first try this decryptor, if it fails to decrypt encrypted files, then security researchers have not yet obtained the offline key. In this case, it remains only to use ShadowExplorer and PhotoRec. If these utilities did not help to recover the files, then you just have to wait for the moment when decryption becomes possible.
my files were encrypted. iD… 0312ewgfDdKzkqxq7TsFBOluaU1QzMIC3a45yu8TR6DWXY4EoA
please can you help?
.PCQQ ayuda para desifrar esta extension
Hi
This is my personal ID is
0312ewgfDdvm44NzSFuQur9eHkIQ3YBUraVfy1szN1yvv5Jwt1
hello. im just asking if there’s any solution for this encryptor. it says no key for new variant online id. and this id appears tobe an online ID. decryption is impossible. thank you
hello, my files’ extention are “zzla”,
my ID is:
0314ewgfDdS0NNWh4jvMhHsvIhZbw7i2VKVXYvHih4FugRg9uB
is it decryptable right now? I really need your help
Thank you
The “0314ewgfDdS0NNWh4jvMhHsvIhZbw7i2VKVXYvHih4FugRg9uB” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Hello
I have all my files encripted with .zzla
Please, what can I do ..?
Use the following guide: https://www.myantispyware.com/2021/07/07/how-to-remove-zzla-ransomware-decrypt-zzla-files/
Te4r7RqtPsoqZfXr6X0lT5ck8H25m2i59Q4YCzHA
My files in laptop have got .zzla extension. I tried to decrypt the files with the help of quick heal anivirus decryptor. it failed. Then I used Emsisoft Stop Djvu Rasomware Decryptor but it gave following message:-
File: C:\Users\pc\mpuaxgxk.exe.zzla
Error: No key for New Variant online ID: KNvoktneRYdl3AarcYm7T8aBYQLMy6VvfR6nmFK0
Notice: this ID appears to be an online ID, decryption is impossible
Your personal ID:
0314ewgfDdKNvoktneRYdl3AarcYm7T8aBYQLMy6VvfR6nmFK0
Please help in decrypting the files.
Kuldeep Singh Negi
I have encrypted files with .zqqw
I would like to know if I can decrypt them with offline key.
Personal ID:
0312ewgfDdcwxIwxtqnTIFAigesKdtD5ncxfF0AI3SUaE6jYwd
Please help me, sir. I was encrypted with .gujd extensions
My Personal ID:
0316ewgfDdWy2jZEa51rg35lktIuknV1J5v6y4Y8EDdQUhp6vs
Thank you
P.s. I have killed the running malware by the task manager then delete all those files, but when I checked the Task Scheduler, I couldn’t find the time trigger (based on the tutorial I found). Is this safe? and if I insert a USB device, this device can be infected or not?
Thanks in advance
skip this step and go straight to removing the virus. Then scan your computer for malware.
Thanks, sir. I think the virus is gone, but all my files are still encrypted with the .gujd extension. I tried decrypt_STOPDJVU and got the message:
Error: No key for New Variant online ID: Wy2jZEa51rg35lktIuknV1J5v6y4Y8EDdQUhp6vs
Notice: this ID appears to be an online ID, decryption is impossible
does this mean that it can not be decrypted?
The “Wy2jZEa51rg35lktIuknV1J5v6y4Y8EDdQUhp6vs” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using ShadowExplorer and PhotoRec: https://www.myantispyware.com/2019/12/04/how-to-recover-encrypted-files-ransomware-file-recovery/
what about my files, sir? because there are already many files that have already become .gujd