What is .Lokf file
.Lokf file extension is an extension that is associated with a new variant of dangerous ransomware called STOP (djvu). Variant ‘Lokf’ (v0181) was released this week, a few days after the previous version, called Mosk. It encrypts data on victim’s computer and appends filenames with .Lokf extension. All encrypted files become useless, their contents cannot be read without decryption. The criminals who created the ransomware demand a ransom in exchange for a key and a decryptor. Fortunately, a free decryptor was created that can decrypt files in some cases. Scroll through this article below to learn more about how to decrypt .lokf files.
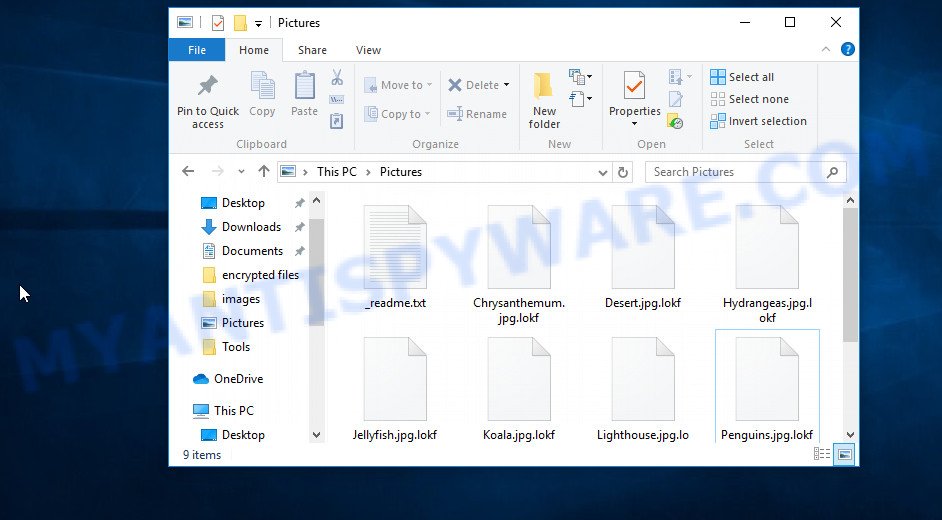
Screenshot of files encrypted by Lokf virus (‘.lokf’ file extension)
Lokf virus encrypts files using a strong encryption algorithm. The virus uses a long key to encrypt files. This key is unique for each victim, therefore it excludes the possibility of using the same key to decrypt files on different computers. In some cases, when the virus cannot establish a connection to the command server (C&C), it uses the so-called offline key. This key is the same for all victims.

Lokf does not encrypt absolutely all files, as it will cause the computer to stop working. Therefore, the virus skips and does not encrypt Windows system files as well as files with the name ‘_readme.txt’. All other contents of the victim’s computer will be encrypted. It makes no difference where the files are located, on a hard drive or cloud storage. If at the time of the ransomware attack the device is connected to the computer and there are files on it, then they will be encrypted. For example, the following file types can be encrypted:
.dazip, .iwd, .yml, .srf, .zif, .wbd, .wbm, .wpb, .wri, .sis, .xmmap, .docm, .m3u, .rofl, .xwp, .wps, .crw, .bkp, .vtf, .eps, .dxg, .icxs, .t13, .qic, .zip, .svg, .wcf, .hplg, .pdd, .syncdb, .flv, .r3d, .wdb, .xlk, .wpe, .cdr, .kf, .z, .wp4, wallet, .rwl, .x3d, .wire, .z3d, .pptx, .webp, .mrwref, .wpl, .wmd, .wb2, .wmv, .xll, .wsc, .pdf, .ltx, .js, .upk, .rim, .vfs0, .wmf, .wma, .bc6, .mdb, .litemod, .lrf, .xpm, .zdb, .ff, .das, .y, .rb, .wp7, .xlsx, .odt, .dcr, .p7b, .bar, .gho, .der, .mef, .vpk, .xlgc, .forge, .kdc, .mov, .png, .fos, .xyw, .cas, .epk, .wp5, .ybk, .xls, .sid, .0, .xls, .pptm, .bsa, .dwg, .pak, .m2, .xml, .wpd, .ai, .xxx, .wpa, .sie, .dng, .qdf, .1st, .dmp, .wotreplay, .itm, .zi, .sav, .wgz, .wp, .tor, .rar, .zw, .x3f, .wps, .apk, .csv, .xdl, .xlsm, .gdb, .itdb, .wmo, .mp4, .psd, .desc, .xlsb, .hvpl, .jpg, .hkdb, .sum, .x, .mcmeta, .1, .raf, .xbdoc, .vpp_pc, .fsh, .pef, .arw, .p7c, .ibank, .jpe, .dba, .odp, .psk, .wbk, .vcf, .xf, .bkf, .xdb, .t12, .xlsm, .sidd, .wbz, .erf, .wm, .wdp, .py, .map, .yal, .wsh, .docx, .wsd, .doc, .w3x, .webdoc, .ptx, .bc7, .bik, .orf, .pst, .xlsx, .d3dbsp, .re4, .sb, .raw, .cer, .3fr, .fpk, .slm, .big, .db0, .odc, .wpg, .avi, .ztmp, .kdb, .sr2, .wp6, .wot, .pkpass, .wma, .vdf, .iwi, .txt, .nrw, .snx, .xld, .xmind, .sql, .xar, .zdc, .wmv, .css, .zabw, .indd, .pfx, .blob, .xyp, .xy3, .tax, .mdf, .cfr, .ppt, .xbplate, .esm, .wbc, .wpt, .srw, .mdbackup, .lbf, .dbf, .rtf, .xx, .accdb, .2bp, .itl, .ntl, .wav, .ncf, .mpqge
When the encryption is completed, all documents, pictures, databases and other files will be completely blocked. All encrypted files have a new .lokf extension, which clearly indicates that they were affected by the ransomware. If the file previously had the name ‘picture.jpeg’, now, after encryption, it has the name ‘picture.jpeg.lokf’. In each directory where the files were encrypted, the virus places a file named ‘_readme.txt’.
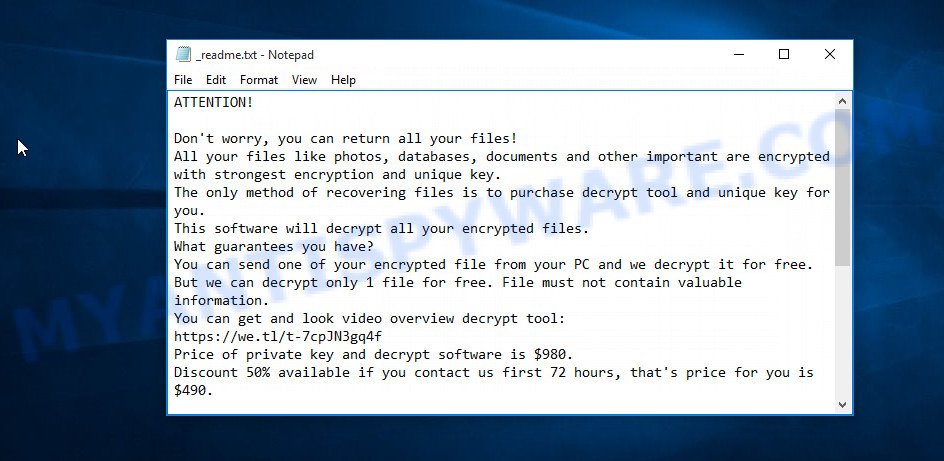
Screenshot of the contents of ‘_readme.txt’ file (Lokf ransom note).
The information in this file is a message from Lokf authors, in which they inform the victim that the files were encrypted and the only way to decrypt them is to buy a key and a decryptor. Criminals demand a ransom of $490, if the victim does not transfer the money within 72 hours, the amount of the ransom will increase by two to 980. To confirm that decryption of the victim’s files is possible, the attackers behind Lokf virus offer to decrypt one file for free. An important condition is that this file should not contain important information and should be small in size. For communication with criminals, this message also contains a pair of addresses.
Threat Summary
| Name | Lokf |
| Type | Ransomware, Crypto virus, File locker, Filecoder, Crypto malware |
| Encrypted files extension | .lokf |
| Ransom note | _readme.txt |
| Contact | restoredatahelp@firemail.cc, gorentos@bitmessage.ch |
| Ransom amount | $490,$980 in Bitcoins |
| Detection Names | Trojan:Win32/Kryptik, FileRepMalware, TR/Crypt.Agent, Malware/Win32.NemtyRansom, Trojan.Encoder, Trojan-Ransom.Crypted, UDS:DangerousObject.Multi.Generic |
| Symptoms | Files encrypted with .lokf extension. Your file directories contain a ‘ransom note’ file that is usually a _readme.txt file. |
| Distribution ways | Adware, Setup files, Phishing Emails, Drive-by downloads, Adware, Torrents, Misleading websites. |
| Removal | Lokf virus removal guide |
| Decryption | Free Lokf Decryptor |
The message of criminals that the files cannot be decrypted is, for the most part, true. Encrypted files cannot be decrypted without a decryptor. Fortunately, Emsisoft has developed a free decryptor. This utility can help everyone decrypt files and thus unlock their contents. Unfortunately, this decryptor is suitable only for those victims whose files are encrypted with an offline key. In other cases, this decryptor will skip files without decrypting them. In this situation, we recommend using alternative methods of data recovery.
If you became a victim of Lokf virus and your files were encrypted, we recommend using the following action plan, which will allow you to remove the ransomware and decrypt (restore) the encrypted files. Read this entire manual, then bookmark it, print it, or open it on your smartphone. So it will be more convenient for you to carry out all the necessary actions.
Remove Lokf ransomware virus
The first step that you must perform is to scan your computer, find and remove Lokf ransomware virus. Do not try to immediately start decrypting files, skipping the first step, you risk losing all your files. To identify all components of Lokf virus, we recommend using free malware removal tools. Some of them, with brief instructions, are given below. If you have an antivirus, then perform a full scan using it, then use the programs offered below. Each of these programs can locate and remove various malware, including ransomware, but these tools cannot recover and decrypt files. To decrypt .lokf files, you need to complete this step, and then go to step 2.
Remove Lokf with Zemana Anti-Malware
Zemana Anti-Malware (ZAM) highly recommended, because it can scan for security threats such Lokf crypto virus, other malware and trojans that most ‘classic’ antivirus apps fail to pick up on. Moreover, if you have any Lokf removal problems which cannot be fixed by this tool automatically, then Zemana provides 24X7 online assistance from the highly experienced support staff.
- Download Zemana from the link below.
Zemana AntiMalware
164814 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- Close all apps and windows on your computer. Run the downloaded file named Zemana.AntiMalware.Setup.
- Click Next and follow the prompts.
- Once install is complete, press the “Scan” button to perform a system scan for Lokf virus and other security threats.
- Review the scan results and then press “Next” to remove the ransomware.
Remove Lokf with MalwareBytes
If you are having issues with the Lokf virus removal, then download MalwareBytes AntiMalware (MBAM). It is free for home use, and identifies and removes various malware that attacks your PC. MalwareBytes Free can remove ransomware, adware, spyware, PUPs, trojans, worms and other malware.
- Download MalwareBytes Anti-Malware by clicking on the link below.
Malwarebytes Anti-malware
327071 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- Close all programs. Double-click the install file called mb3-setup.
- Follow the prompts and don’t make any changes to default settings.
- Once setup is finished successfully, click Finish button. MalwareBytes will automatically start.
- Click the “Scan Now” button to perform a system scan for Lokf crypto malware.
- When the scanning is finished, MalwareBytes Anti-Malware will prepare a list of malware. Click “Quarantine Selected” button.
We recommend you look at the following video, which completely explains the process of using the MalwareBytes to remove malicious software.
Remove Lokf ransomware using Kaspersky virus removal tool
If MalwareBytes anti-malware or Zemana anti-malware cannot delete Lokf, then we suggests to use Kaspersky virus removal tool (KVRT). It is a free removal tool for ransomware, adware, trojans, worms, PUPs and other malware.
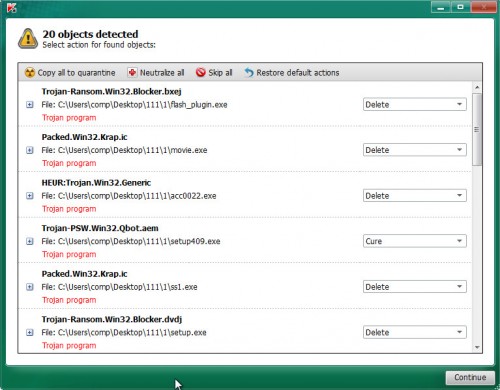
- Download Kaspersky virus removal tool (KVRT) by clicking on the link below.
Kaspersky virus removal tool
129234 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
- Run the downloaded file.
- Click Start scan button to perform a system scan for Lokf crypto virus.
- Review the report and then click on Continue.
How to decrypt .lokf files
Files with the extension .lokf are files that have been encrypted by the ransomware. The only way to decrypt them is to have a key and a decryptor. There is no guarantee that even after paying the ransom, the criminals will allow the victim to recover their files. Fortunately, Emsisoft created a decryptor that can use every victim of the virus to decrypt .lokf files.
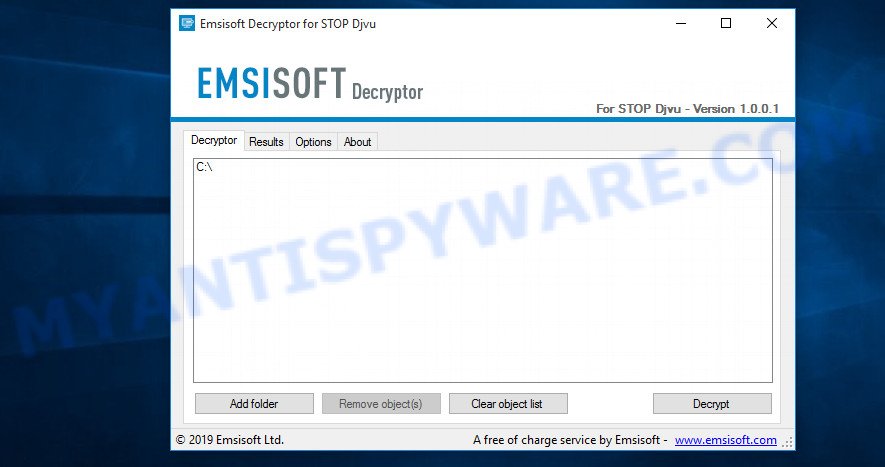
STOP Djvu decryptor
To decrypt .lokf files, follow the easy steps below:
- Go to the following link to download STOP Djvu decryptor.
STOP Djvu decryptor - Scroll down to ‘New Djvu ransomware’ section.
- Click the download link and save the ‘decrypt_STOPDjvu.exe’ file to your desktop.
- Run decrypt_STOPDjvu.exe, read the license terms and instructions.
- On the ‘Decryptor’ tab, using the ‘Add a folder’ button, add the directory or disk where the encrypted files are located.
- Click the ‘Decrypt’ button.
Today, this decryptor only decrypts files encrypted with offline key. Files that are encrypted with an online key will be skipped, their decryption is impossible (at least for today). If in your case the decryptor skips files, then you do not need to despair right away. Since Lokf vaiant appeared recently, researchers may not yet have found the offline key. Therefore, the decryptor, at first, can skip files, even encrypted with the offline key. Remember, even if the decryptor cannot help you, there is always the opportunity to restore files using alternative methods.
How to find out which key was used to encrypt files
Every victim of Lokf needs to know which key the virus used to encrypt files. It is easy to determine with what key the virus encrypted files, below we will describe two methods.
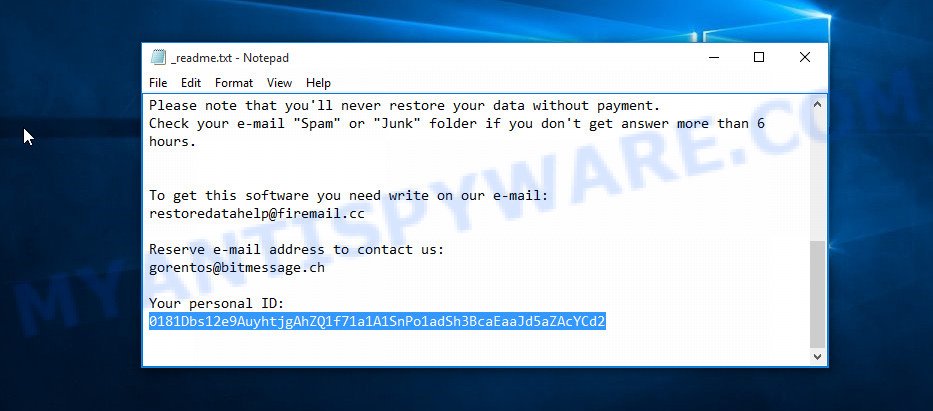
Personal ID is highlighted here
Method 1.
- Open the ransom note (‘_readme.txt’ file).
- Scroll down to the end of the file.
- There you will see a line with the text ‘Your personal ID’.
- Below is a line of characters that starts with ‘0181’ – this is your personal id.
Method 2.
- Open disk C.
- Open directory ‘SystemID’.
- Open file named PersonalID.txt. This file lists ‘Personal ID’s that match the keys that the virus used to encrypt files.
If your Personal ID ends with ‘t1’, then your files are encrypted using an offline key. If your Personal ID does not end with ‘t1’, then Lokf used an online key. Even in this case, it is possible to restore the content of encrypted files. We will talk about this in the next section of this article.
If you determine that your files are encrypted with an offline key, but the decryptor does not decrypt them, then you just need to wait a while. Try decrypting your files every day. There is no need to update the decryptor, as it downloads keys automatically.
How to restore .lokf files
Fortunately, there are some alternative ways to recover encrypted files. Each of them does not suggest the use of a decryptor and a key, so these methods will suit all victims regardless of which key Lokf virus used to encrypt files. In addition, the use of these methods will not affect in any way the decryption of files using a free decoder. The only thing is that before you proceed with file recovery, be sure to check your computer for malware, you need to be 100% sure that the ransomware has been completely removed.
Run ShadowExplorer to recover .lokf files
A free utility named ShadowExplorer is a simple solution to use the ‘Previous Versions’ feature of Microsoft Windows 10 (8, 7 , Vista). You can recover your files encrypted by Lokf crypto virus from Shadow Copies for free.
Download ShadowExplorer on your Windows Desktop by clicking on the link below.
439461 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
Once downloading is finished, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder like the one below.
Double click ShadowExplorerPortable to start it. You will see the a window as displayed in the following example.
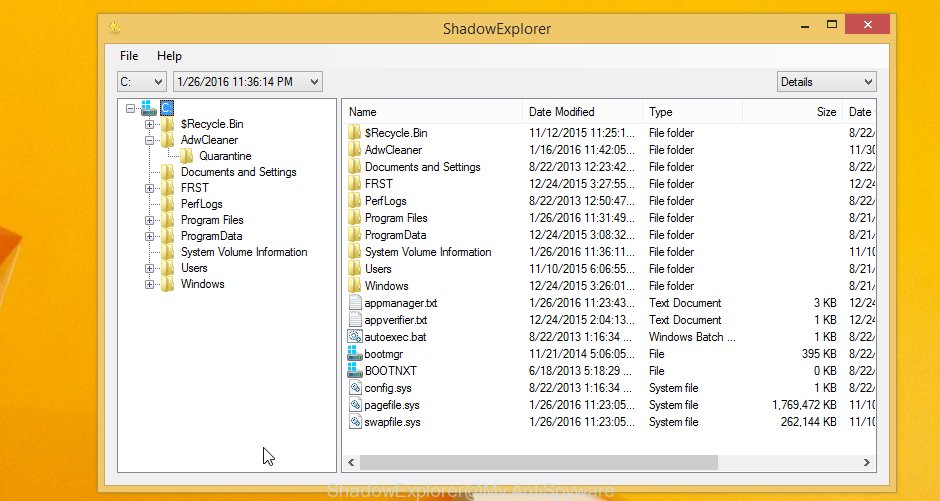
In top left corner, select a Drive where encrypted photos, documents and music are stored and a latest restore point as displayed on the image below (1 – drive, 2 – restore point).
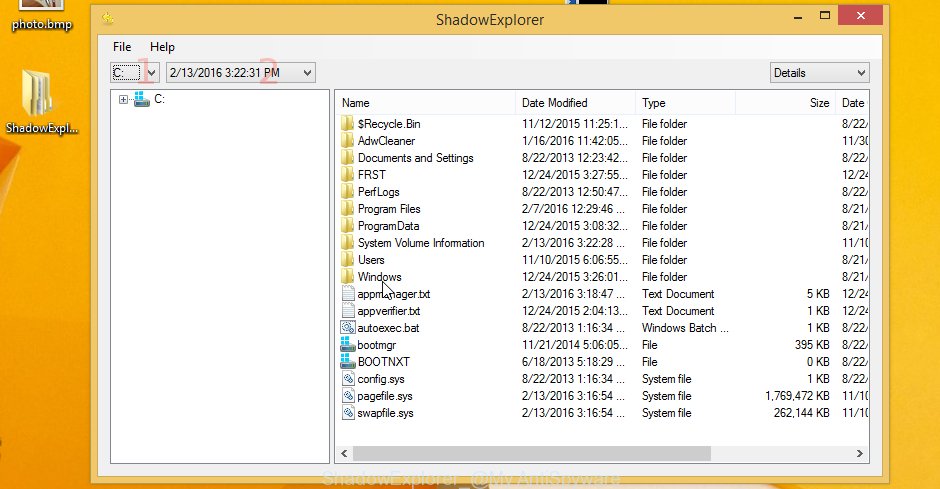
On right panel look for a file that you want to restore, right click to it and select Export as displayed on the image below.

Restore .lokf files with PhotoRec
The last chance to restore encrypted files to their original state is using data recovery tools. We recommend a free tool called PhotoRec. It has all the necessary functions to restore the contents of encrypted files. It helped many victims recover data when it seemed like there was no more hope.
Download PhotoRec on your MS Windows Desktop from the link below.
After the downloading process is finished, open a directory in which you saved it. Right click to testdisk-7.0.win and choose Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as shown on the screen below.

Double click on qphotorec_win to run PhotoRec for Microsoft Windows. It’ll show a screen as on the image below.
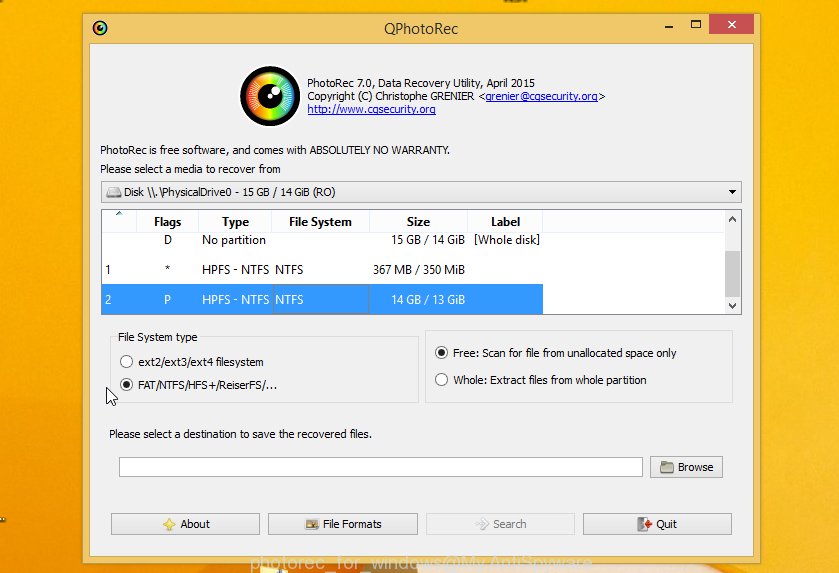
Choose a drive to recover like below.
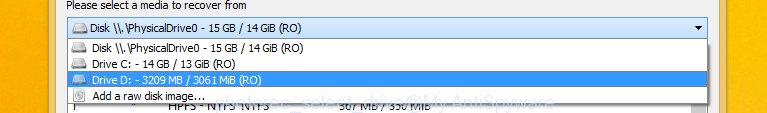
You will see a list of available partitions. Select a partition that holds encrypted photos, documents and music like below.
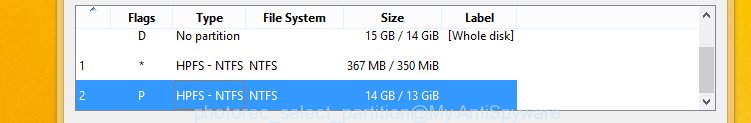
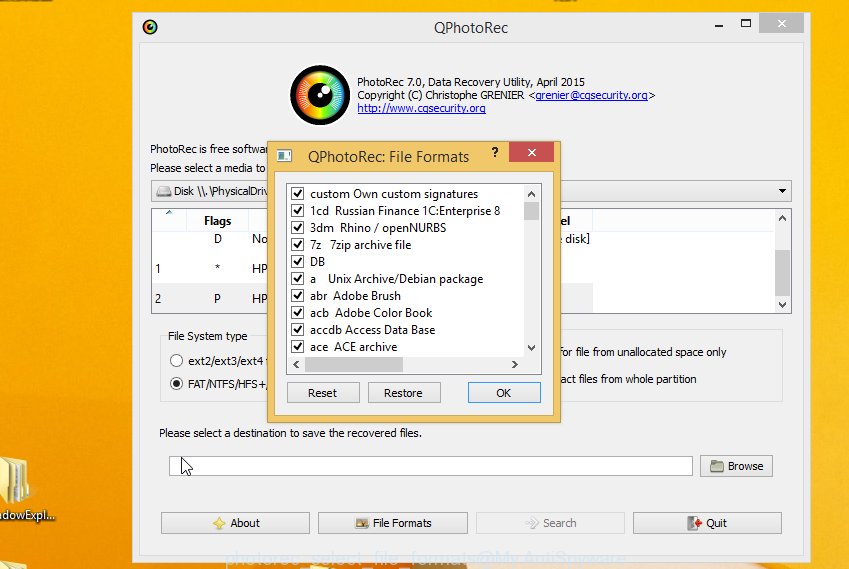
Click File Formats button and specify file types to recover. You can to enable or disable the restore of certain file types. When this is done, click OK button.
Next, click Browse button to choose where restored photos, documents and music should be written, then press Search.
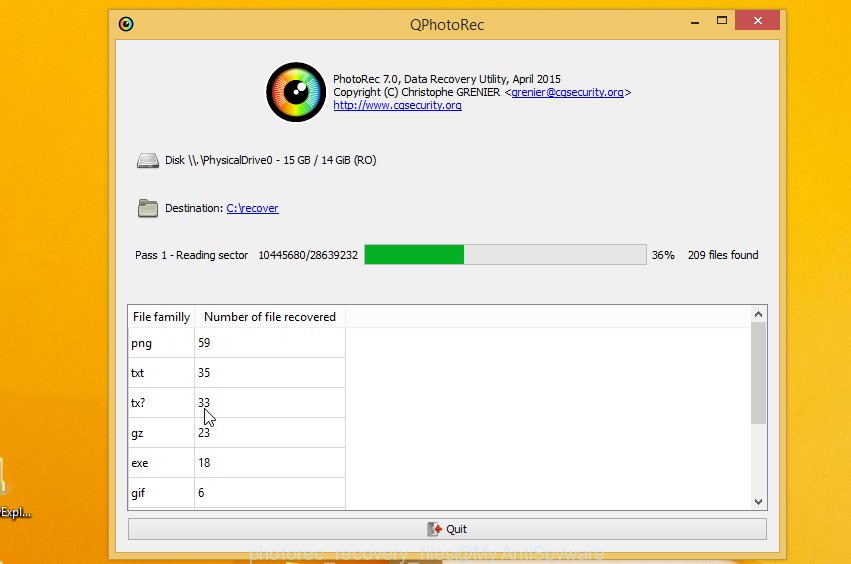
Count of recovered files is updated in real time. All restored documents, photos and music are written in a folder that you have selected on the previous step. You can to access the files even if the restore process is not finished.
When the restore is finished, press on Quit button. Next, open the directory where restored personal files are stored. You will see a contents as on the image below.
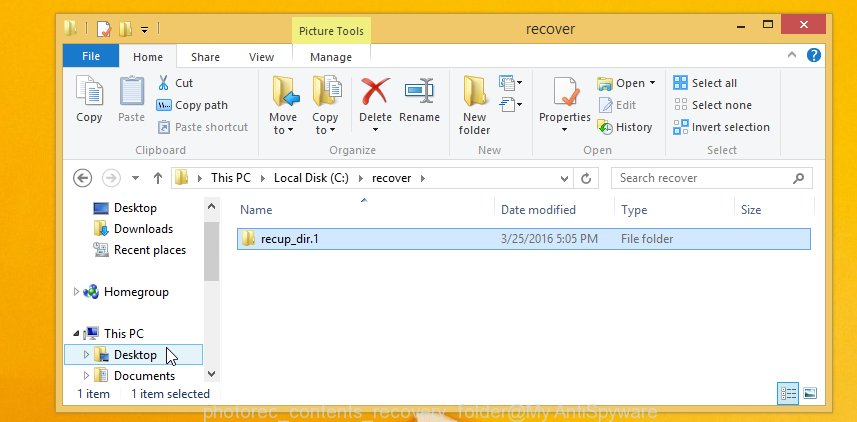
All recovered files are written in recup_dir.1, recup_dir.2 … sub-directories. If you are searching for a specific file, then you can to sort your restored files by extension and/or date/time.
Finish words
This article was created to help all victims of Lokf virus. We tried to give answers to the following questions: how to remove ransomware; how to decrypt .lokf files; how to recover files, if the decryptor does not help; what is an online key and what is an offline key. We hope that the information presented in this article has helped you. If you have questions, then write to us, leaving a comment below. If you need more help with Lokf related issues, go to here.











Hello sir, i am not able to decrypt the .lokf file please give me a better solution.
Unfortunately, there is no better solution. At the moment there is only one free decryptor and it can decrypt files encrypted with offline key. Alternative methods are using Shadow copies and data recovery programs.
Hello sir, i am not able to decrypt the .lokf file
i can do what
thanks
I need help. Suddenly, all my files were renamed, they now have the extension ‘.lokf’. I also found a file that says that my files were encrypted. Google search does not find any free decryptor. Can you tell me if there is a way to decrypt .lokf files?
The better solution is restore your windows.
Hello sir,
My Filew were encrypted with .lokf online key … is there any hope to unlock these files with a decryptor
Hello.
I have followed the steps using PhotoRec tool, after scanning process, it has created a file with the name Recup_dir.1 as it was mentioned in the article, but witch has only a few dll files. However, I cannot access it.
Is there something else I should try?
Mohamed Elsayed, hope always remains. But you probably have to wait a long time.
Andrei, at the step where you need to choose the ‘file formats’, have you selected all or specific file types?
0181jYgs9f6sXcQBAGFsugQm8E2RNxtBhvV5rmQXZZWyCOoypV66
This is my Personal ID
Please, someone help me…
Getting frustated right now…please someone help
HARD CRY
Can you contact STOP djvu decryptor and ask them when will they make option for recovery of offline keys? And where can I report this .lokf malwer? To police, some expert or what? I don’t understand part with police.
Oh sorry, that part with police is on another site, nevermind about that. But still, my question about stop djvu decryptor team remains…
And yes, before ecrypting part, can check which keys are offline and which are online? And how to find disk C, and/or ransome note?
How to enter disc C/ransom note? And can I check that before decrypting? Or I must exactly by your order?
To date, the offline key is still not found. Therefore, if the files are encrypted with the offline key, you just have to wait.
Billy, ‘0181jYgs9f6sXcQBAGFsugQm8E2RNxtBhvV5rmQXZZWyCOoypV66’ id means the files were encrypted with an online key.
con PhotoRec recuperé parte de los archivos, gracias y estaré revisando para poder ver si termino de recuperar todo lo demás, gracias por el artículo y muy bien explicado