Restorealldata@firemail.cc is an email address that cyber criminals use to contact victims of STOP (DJVU) ransomware. Ransomware is a type of malware that blocks access to files by encrypting them, until the victim pays a ransom.
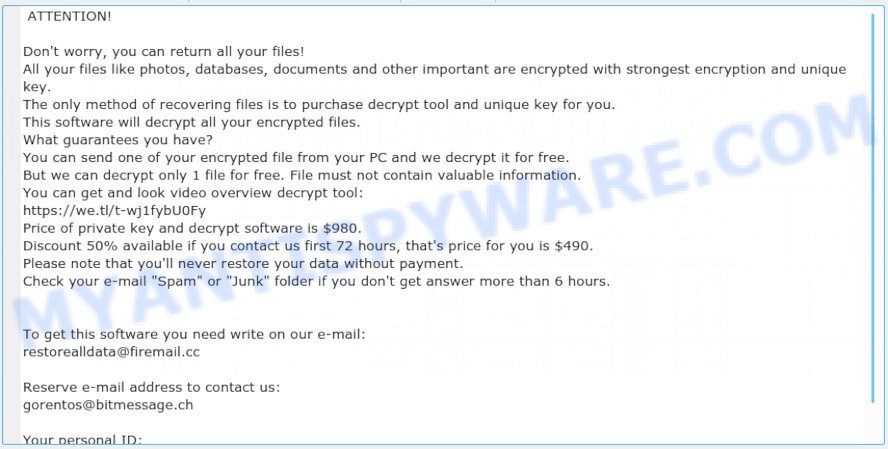
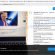
Screenshot of the contents of the ‘_readme.txt’ file (ransom demand message)
Restorealldata@firemail.cc virus locks up the files using AES-RSA technology, that makes it impossible to unlock the encrypted data by the victim without obtaining a key and a decryptor, which is the only way to decrypt affected files. It can be obtained only in the case of payment of the required ransom through cryptocurrency wallet. The ransomware virus encrypts almost of images, databases, videos, documents, music, web application-related files, and archives including common as:
.wp4, .ws, .xxx, .wbmp, .rw2, .raf, .psk, .bc7, .wm, .pptx, .srw, .zip, .mdb, .m2, .itdb, .odp, .cr2, .m3u, .bay, .m4a, .ptx, .iwd, .dng, .bkf, .p12, .xbdoc, .y, .fos, .wri, .srf, .psd, .db0, .dmp, .ysp, .t12, .blob, .x3d, .z, .crt, .wpe, .sum, .1st, .wot, .doc, .ltx, .xld, .qic, .re4, .zip, .itl, .x3f, .menu, .xpm, .xlsx, .wsc, .lrf, .pef, .py, .xy3, .wma, .cfr, .css, .layout, .lbf, .vpp_pc, .das, .nrw, .crw, .ybk, .epk, .mp4, .wdp, .r3d, .xls, .flv, .xlk, .ppt, .jpg, .pfx, .rtf, .map, .wpg, .slm, .xls, .vdf, .wpt, .xmind, .ibank, .dxg, .rar, .zdc, .wp7, .litemod, .1, .rim, .sql, .csv, .hvpl, .dba, .kdc, .cas, .zif, .wma, .webp, .wotreplay, .mov, .wb2, .sb, .3ds, .wbc, .arw, .z3d, .ntl, .xdb, .bc6, .pptm, .rb, .ai, .xwp, .rofl, .wcf, .forge, .mpqge, .xmmap, .pkpass, .xyw, .pst, .wav, .itm, .xx, .orf, .mcmeta, .ncf, .wpb, .desc, .xlsb, .w3x, .gdb, .lvl, .vpk, .esm, .kdb, .qdf, .jpeg, .wmo, .xml, .big, .arch00, .sid, .txt, .apk, .hplg, .sie, .wn, .sis, .accdb, .gho, .wmv, .yal, .bsa, .wsd, .xlgc, .pak, .xll, .syncdb, .vfs0, .eps, .wp6, .kf, .x3f, .pem, .cer, .wmf, .asset, .xdl, .wpw, .zw, .2bp, .wmd, wallet, .zi, .mdbackup, .webdoc, .wp, .pdd, .sav, .sidn, .wmv, .3fr, .sr2, .erf, .snx, .bar, .docm, .zdb, .wps, .tax, .pdf, .bik, .zabw, .icxs, .mlx, .wbm, .p7b, .xf, .cdr, .wpd, .upk, .odm, .odc, .dcr, .xlsx, .der, .raw, .odt, .wsh, .mddata, .wpl, .jpe, .yml, .xlsm, .ods, .sidd, .wbk, .avi, .dazip, .hkx, .wp5, .vcf, .wps, .xbplate, .wbz, .wire, .wgz, .wbd, .rgss3a, .d3dbsp
With the encryption process is finished, all encrypted files will now have a new extension appended to them. In every directory where there are encrypted files, Restorealldata@firemail.cc virus drops a file called ‘_readme.txt’. This file contains a ransom note that is written in the English. The ransom message directs victims to make payment in exchange for a key needed to unlock personal files.
Summary
| Email address | restorealldata@firemail.cc |
| Related ransomware | STOP (DJVU) family |
| Variants of STOP (Djvu) that use this address | Kodg |
| Ransom note | _readme.txt |
| Ransom amount | $980/$490 |
| Removal | Free Malware Removal Tools |
| Decryption | Free STOP Djvu Decryptor |
Text presented in “_readme.txt”:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-wj1fybU0Fy
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
restorealldata@firemail.ccReserve e-mail address to contact us:
gorentos@bitmessage.chYour personal ID:
If you find files called ‘_readme.txt’, then your computer is the victim of ransomware attack. First you need to find and remove Restorealldata@firemail.cc virus. We recommend using free malware removal tools. Only after you are completely sure that the virus has been removed, start decrypting the files.
How to decrypt files encrypted by Restorealldata@firemail.cc virus
Using the STOP decryptor is not difficult, just follow the few steps described below.
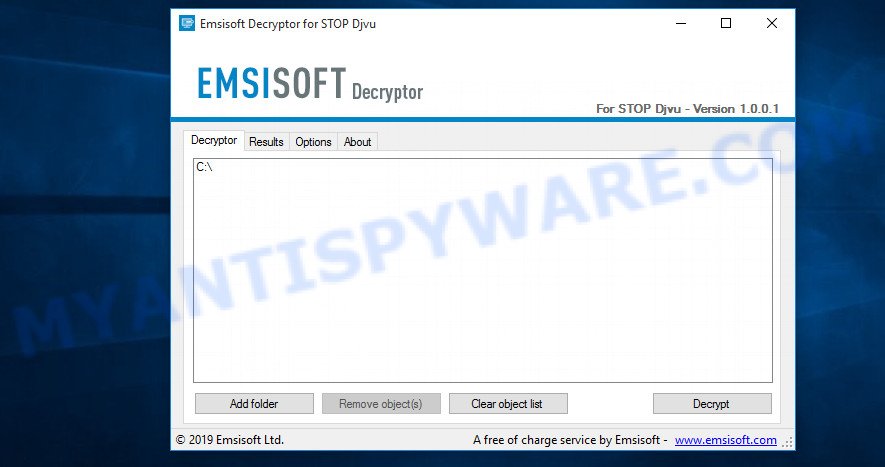
STOP Djvu decryptor
- Download STOP Djvu decryptor from here (scroll down to ‘New Djvu ransomware’ section).
- Run decrypt_STOPDjvu.exe.
- Add the directory or disk where the encrypted files are located.
- Click the ‘Decrypt’ button.