Recover Encrypted Files is a question, the answer to which is important for all victims of ransomware attack. Ransomware is malicious software that encrypts files and demands a ransom for their release. Encrypted files cannot be opened, that is, all encrypted files are locked and cannot be used. This may result in loss of data or important information. Since ransomware uses a complex encryption algorithm, in most cases it is impossible to decrypt encrypted files manually or create a decryptor. But not everything is so bad, everyone who has become a victim of ransomware has a chance to recover encrypted files. In this article, we will show alternative ways to recover ransomware encrypted files. Each of the methods does not require the use of paid software, is easy to repeat, contains explanatory illustrations.
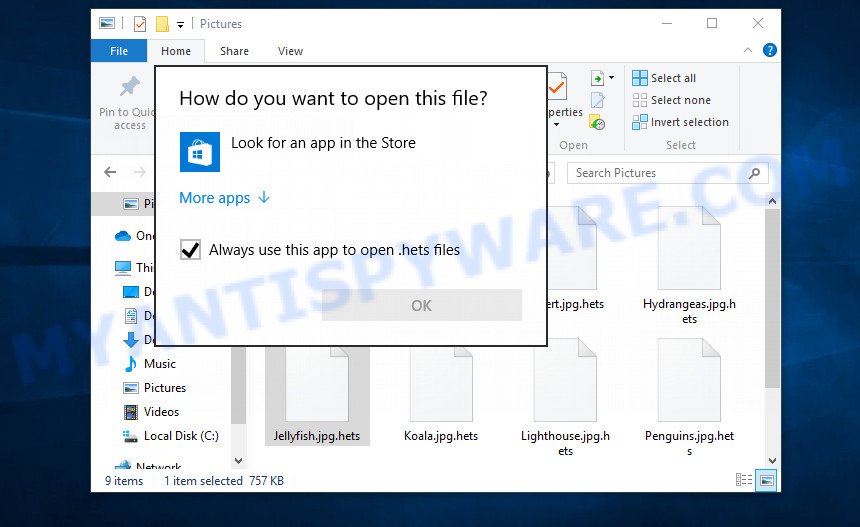
Encrypted files cannot be opened
Files encrypted by ransomware become useless, they cannot be used, their contents cannot be read. Even if you change the filename of the encrypted file, try to open this file in the editor, this will not help. In any case, Windows OS will report that the file was damaged or it is of an unknown type. To return files back, that is, to access their contents, encrypted files must be decrypted. Decryption requires a decryptor and a key. Ransomware authors offer victims to buy a key and a decryptor from them. Usually the size of the ransom is from 300 to 1000 dollars. All security experts agree that the ransom should not be paid. There is no guarantee that paying a ransom will provide a key to decrypt the encrypted files.

Although decrypting files requires a decryptor and a key, which are in the hands of criminals, this does not mean that ransomware victims have no hope of recovering encrypted files. This is not true! There is a chance that allows everyone to recover the contents of encrypted files. Depending on the type of ransomware, this chance may be greater or lesser. Unfortunately, there are very few methods to recover encrypted files without the help of the decryptor. Each of these methods requires neither a decryptor nor a key, therefore these methods are suitable for any victim and can help restore files after any type of ransomware.

Regardless of which method you choose, before you begin the process of recovering encrypted files, you need to check your computer for malware. You need to be sure that ransomware is no longer on the computer. Even if there are no signs of ransomware activity, this does not mean that it disappeared or deleted itself after all the files were encrypted. Ransomware probably just hides itself, and after the appearance of new unencrypted files on the computer, it activates again and encrypts these files. In addition, an active ransomware can be a source of infection for other devices, as well as work as a spyware, that is, collect various information about the victim, which will then be sold or transmitted to attackers.

We highly recommend that before you start recovering encrypted files, first check your computer for malware. It is very important to find the ransomware and completely remove it. In order to quickly find all parts of the ransomware and easily remove them, we recommend that you use free malware removal tools. Each of them tested by security experts, has a powerful malware detector, and will allow you to remove various types of malware, including ransomware, spyware, worms and trojans.
How to recover ransomware encrypted files
Recover encrypted files from Volume shadow copies
Volume shadow copy is a feature on modern versions of Microsoft Windows (Vista,7,8,10). It is turned on by default and creates copies of all user files. These copies can be created automatically from time to time or when creating a restore point. This allows you to retrieve copies of files that have been encrypted by ransomware. To access these shadow copies, we recommend using a program called ShadowExplorer. It is a free program that does not require installation, has a simple interface and is easy to use.
Download ShadowExplorer on your computer by clicking on the link below.
440045 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
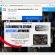
When the file download is complete, open the directory in which you saved the file. Right click to ‘ShadowExplorer-0.9-portable’ and select ‘Extract all’. You will see a window, as in the following figure.
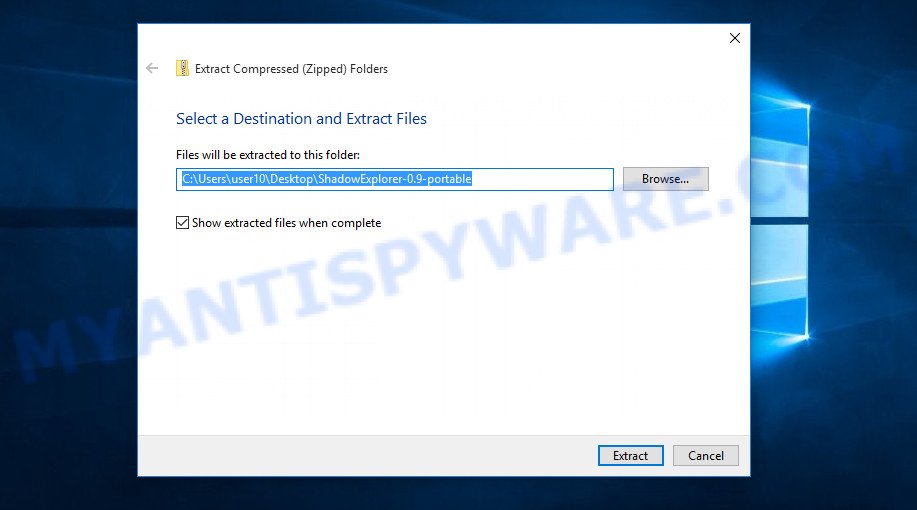
Here you can change the place where the archive will be unpacked. If you do not make any changes, then in the directory where the file is located, a directory with the name ‘ShadowExplorer-0.9-portable’ will be created in which all the unzipped files will be placed. Then the contents of this directory will open. Now open directory ‘ShadowExplorerPortable-0.9’. The following is an example of the contents of this directory.
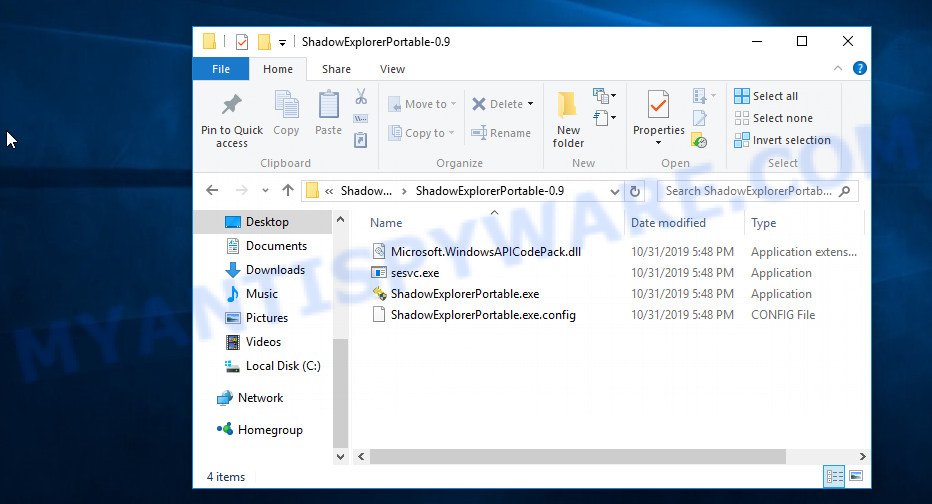
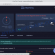
Find the ShadowExplorerPortable file and run it. You will see the main window of ShadowExplorer similar to what is shown in the picture below.
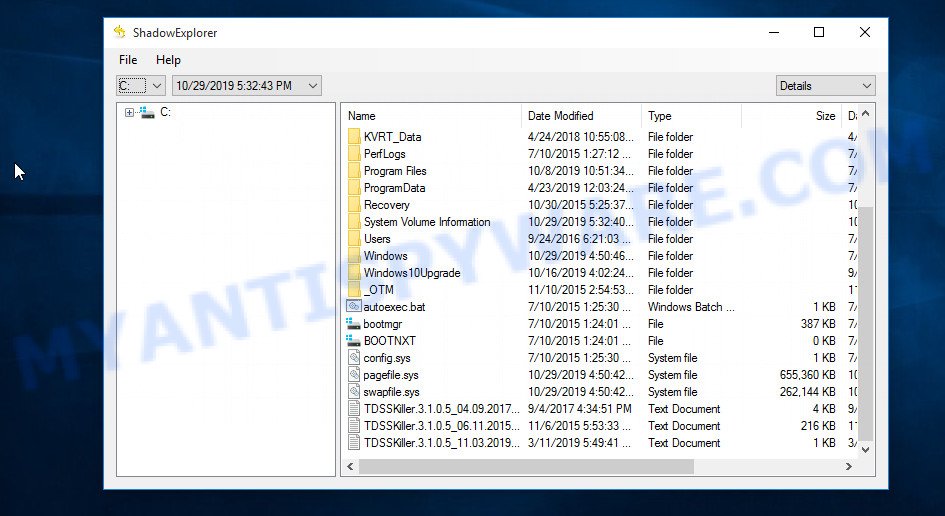
In the upper left corner of the window, select the drive on which encrypted files are located that you want to recover. Then, slightly to the right of the drive name, select the recovery point that is before the moment the files were encrypted.
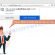
On right panel look for a file that you wish to recover, right click to it and select Export as shown on the image below.
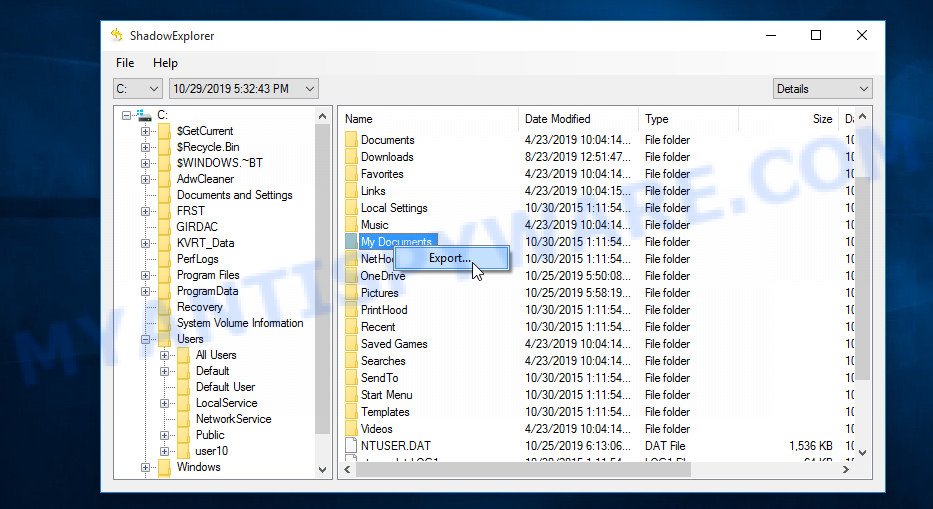
Now select the directory where the recovered files will be saved, then click OK button.
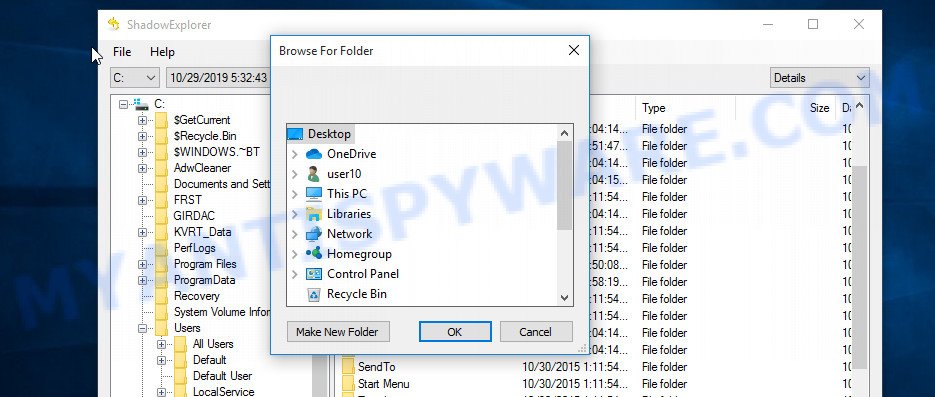
Unfortunately, ransomware often deletes all Shadow copies, and this blocks the ability to use the method described above to recover encrypted files. Therefore, if ShadowExplorer did not find Shadow copies (the field in which the recovery points are listed is empty), then all Shadow copies have been deleted. In this case, you have only one option left, to use data recovery tools. This method of recovering encrypted files is described below.
This video tutorial will demonstrate how to Recover encrypted files from Volume shadow copies using Shadow Explorer.
Recover encrypted files using Photo Rec
Data Recovery Utilities is your last chance to recover encrypted files. Why data recovery tools can help recover encrypted files? Before encrypting the file, some types of ransomware copies its contents to the computer’s RAM, encrypts it, then deletes the non-encrypted file, and writes the encrypted file to the hard disk. In reality, not-encrypted files are not physically deleted; they are simply marked by Windows OS as deleted. Data recovery software scan the computer’s hard drive for such files, and then restore them.
PhotoRec is a free data recovery tool that can help you recover encrypted files. This program has all the necessary functions and is absolutely free. In addition, PhotoRec has repeatedly proven its effectiveness. With its help, many users were able to recover the contents of encrypted files.
Download PhotoRec on your machine by clicking on the link below.
After the file download is completed, open the directory where you saved the file. Although PhotoRec does not require installation, but since it is delivered in the archive, you must unpack the archive before using it. Right click to testdisk-7.x.win and select Extract all. Follow the prompts. By default, the program will be unpacked into a new directory, which will be created in the directory where the downloaded file is located. When unpacking is completed, you will see a new directory with the name testdisk-7.x, open it.
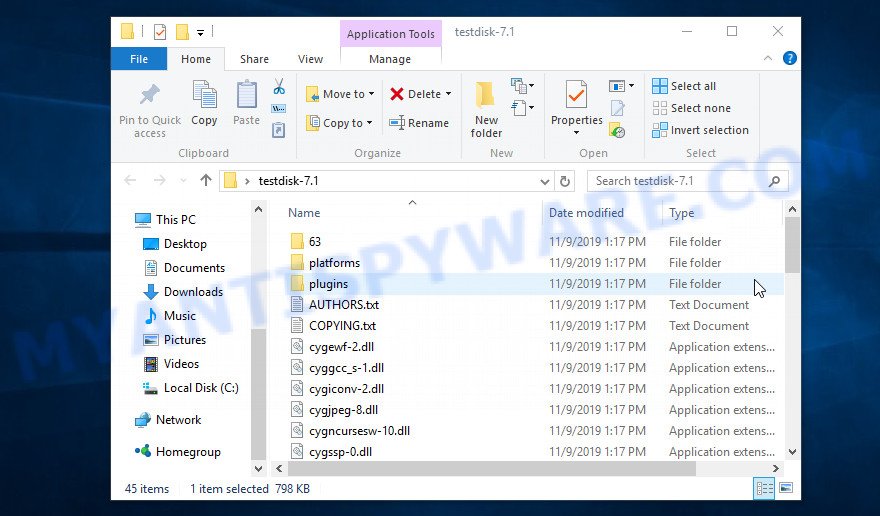
Scroll down the directory until you find a file named qphotorec_win. Run it. You will be shown the main program window as on the image below.
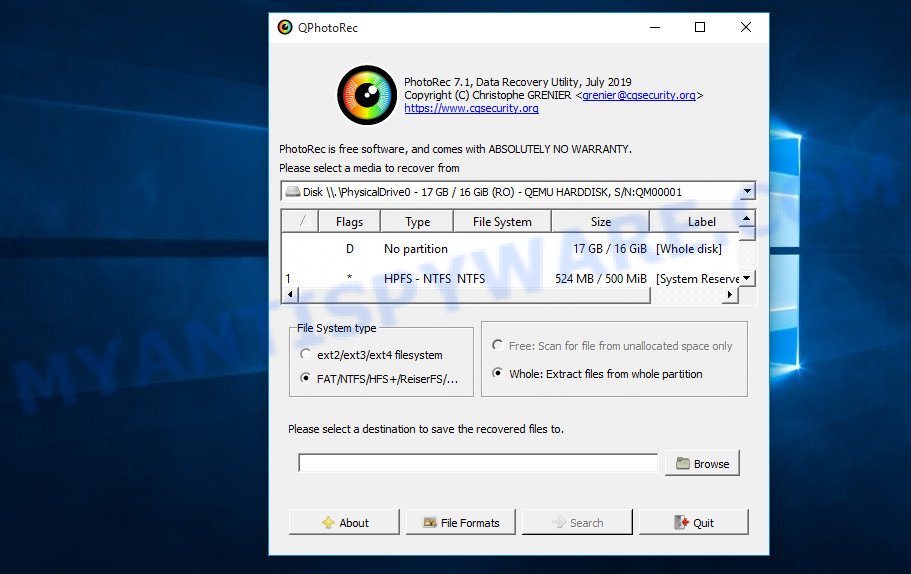
Find the box that is signed by “Please select a media to recover from”, right-click on it and select the device on which the encrypted files are located.
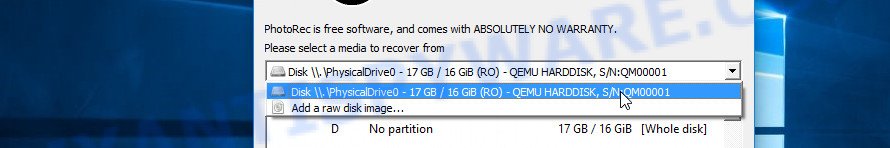
PhotoRec will scan the partition table of the selected device and show a list of partitions in the list. Select the partition from which you want to start the recovery of encrypted files. Be careful, pay attention to the type of partition (usually NTFS) and its size. Skip sections marked ‘System Reserved’.
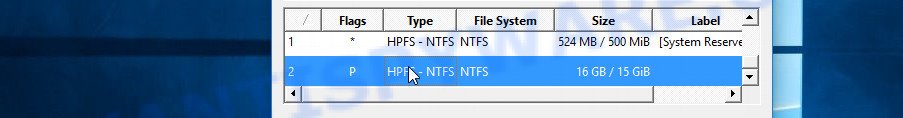
Having decided where PhotoRec will look for unencrypted files, now you need to select the types of files you want to restore. Click File Formats button, a small window opens with a list of file types that PhotoRec has the ability to find and restore. We advise you to leave only those types that you really need, so you will significantly speed up the process of searching and restoring files. After you make your choice, click the OK button.
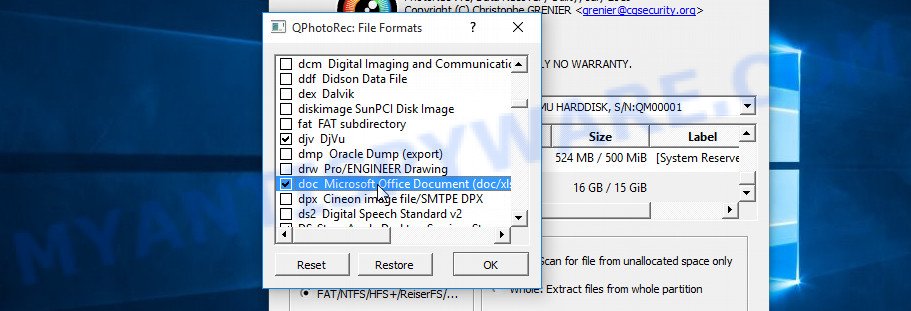
And lastly, click on the Browse button and select where the recovered files will be written. We highly recommend that you select an external drive, flash drive, or a separate section of the internal drive. If you restore files to the same disk on which you are looking for them, then the restored files will overwrite files that have not yet been found, which will block the ability to restore their contents.
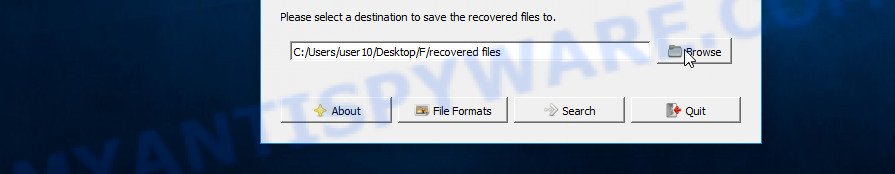
Now you can start file recovery. Just click the Search button. The program will start searching and restoring files. PhotoRec will open a window in which information on the count of recovered files will be updated in real time.
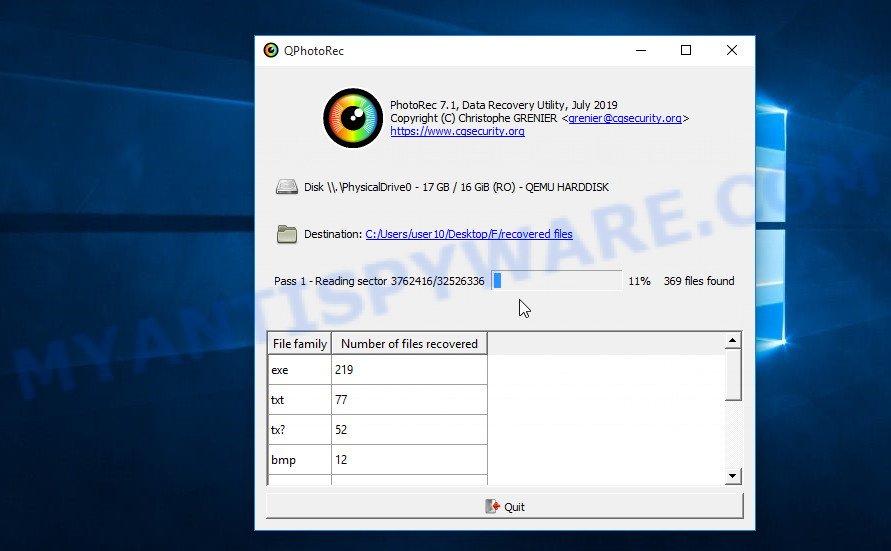
All files that were restored are written to the directory that you specified above. When the file recovery process is completed, press the Quit button. Open the directory where the recovered files were written. You will see something like the following.
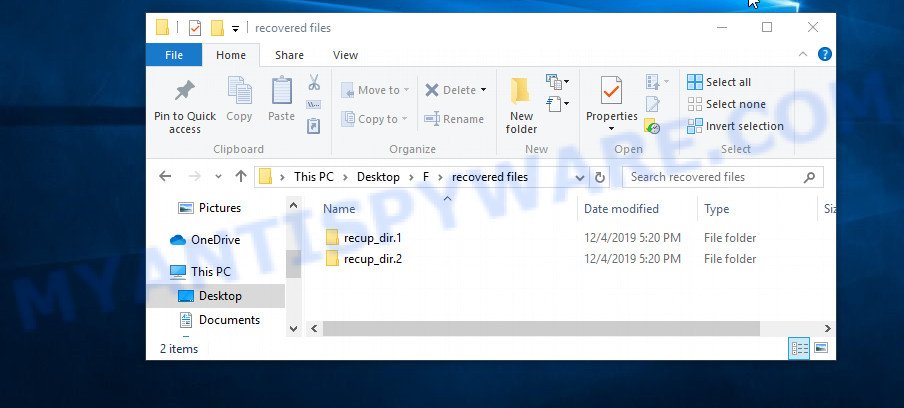
All recovered files are written in recup_dir.1, recup_dir.2 … sub-directories. If you are searching for a specific file, then you can to sort your restored files by filename, extension and/or date/time.
This video tutorial will demonstrate how to Recover encrypted files using PhotoRec.
Finish words
This manual is designed to help ransomware victims recover encrypted files for free. If you have any questions or comments, then write to us. If you need help, please ask your question here.











After cleaning the ransomware, u must be frustrated to recover the encrypted file. try manually recover your files with shadowexplorer app. really works. just need to do it manually. better than nothing.
Mi PC Fue Infectada con el Ransomware ggwq. Con la Herramienta Malwarebyts pude eliminar el Rasomware pero los archivos ( Fotos, Videos, Doc, Musica) seguian encriptados, ya que el virus trabajó en mi equipo de forma OFF LINE como se muestra en el siguiente ID de la nota que se deja en la carpeta encriptada (Your personal ID:0525JhyjdvRqEVDBJg9FN0nWnafBGjHDpRiWWaNDz6FCNjtMa) Utilizando y siguiendo pasa a paso la descripcion de uso brindada por el equipo de Mi Antispyware, pude restaurar varios de mis archivos encriptados, solo no puedo todavia recuperar archivos de video AVCHD/MTS, de camara Sony, por lo demas se pudo recuperar muchos de mis archivos ya que temia haberlo perdido todo . recomiendo el uso y leer las isntrucciones detalladas de las herramientas brindadas por este equipo para lograr recuoerar lo encriptado.
Al equipo de Mi Antyspyreware, MUCHAS GRACIAS!!!
Hello
Sir
Can you please help me decrypt and recover an encrypted file with the .mkp extension?
Cdcc file
It works with PhotoRec. Thanks a lot.
Good evening ! Please if you can help me I have the computer infected with Ransomware and changed all the harddisk extension OFLG.Am tried to decrypt files with decrypt_STOPDjvu File: E:101CANONIMG_5950.JPG.oflg
Error: No key for New Variant online ID: Ay2Ju0ggnBD53kIgdKn8Y7GerqSQnPNMQmgMMjNE
Notice: this ID appears to be an online ID, decryption is impossible .
Thank you !
A beautiful evening !
The “Ay2Ju0ggnBD53kIgdKn8Y7GerqSQnPNMQmgMMjNE ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Error: No key for New Variant online ID: 0604JhyjdzWOtRoqBrGM0CbbuDJbIX5r4iFjsg5xuuDP3nRVx
Notice: this ID appears to be an online ID, decryption is impossible .
Thank you !
Muchas Gracias por su aporte, realmente he podido recuperar información personal muy valiosa con su explicación y herramientas…
Hi, my computer was infected by the udla virus, when I saw that I was infected I quickly Reset My Windows but in my F: Disk were all my Data (400GB+) is located all the archive / Files were like this .ai.udla or .jpg.udla, at that point what I did was to change all the names / extension of every file by using a Software that can remove extension, what happen next is that 90% of my files are somehow corrupted or encrypted Windows cannot open them even .exe (Software Setups) were affected, I am seeing that all the files have their own Size (Which is good) but my Illustrator, Music, RAR documents will not open, and I would like to know if there is an easy way to fix them.
IMPORTANT NOTE: I haven’t being able to recover my files with the REC software, is there any other way?
Note: I installed a Decrypt Sofware and it give the following error:
Error: No key for New Variant online ID: AkCXBEVWmQnoILjNkrieJ7ziDca45YdoENqUyfZO
Notice: this ID appears to be an online ID, decryption is impossible
Oscar Curiel
Graphic Designer
If your files are encrypted with “online key”, they cannot be decrypted. There are no other recovery methods other than those described in the article (https://www.myantispyware.com/2019/12/04/how-to-recover-encrypted-files-ransomware-file-recovery/). If the methods described in this article did not help you, then I advise you to back up your important files and wait until decryption becomes possible. This can happen in a year, two years, or even never. Follow the news on our website or in our Facebook/YouTube account.
i need to decrypted my file please sent me code and tell me how i recover my account
my personal id is
0594Jhyjdoh25esBomB2tR8HM8ZfwaBeMaLH14b27oRfsAOrB
The “0594Jhyjdoh25esBomB2tR8HM8ZfwaBeMaLH14b27oRfsAOrB ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Hello. If this message appears to me, why do I have to wait for an update of the Decrypt STOP Djvu Software?
Error: No key for New Variant online ID: mu76TBLftpm6Kd66REku6tXZlaYfQ40NmpHoV65j
Notice: this ID appears to be an online ID, decryption is impossible
The “mu76TBLftpm6Kd66REku6tXZlaYfQ40NmpHoV65j ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
File: F:\TVCP\MOV05495.THM.tcvp
Error: No key for New Variant online ID: 6oIzB5z2xBbsLiD4LRxmLZdHPCJdiLiLOBQ9sBxS
Notice: this ID appears to be an online ID, decryption is impossible
The “6oIzB5z2xBbsLiD4LRxmLZdHPCJdiLiLOBQ9sBxS ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using ShadowExplorer and PhotoRec as shown above.
I was affected by ISWR ransomware online key, I tried both methods. ShadowExplorer and PhotoRec, unfortunately, are not working with me:
1- ShadowExplorer gives me the option only to go back only for one day before not giving me more options for 3 or 4 days.
2- PhotoRec did not recognize even the selected files.
I have Mallox, so can you help me decrypt about this ransomeware.
My key private :063066422F896227B66ADB6B
So Thank you very much.
Do these softwars recover vvoo
got this message:
No key for New Variant online ID: uWyoWLBUyNRdqHLiMmCasWurmRynt069T22jba53
plz help
Hi , is my personal id an offline or online key? Your personal ID:0724JOsie0vTA6MA1m5nzrdffOCJC7YmAa4Lp6YNN8lOJ4mt1
Your ID is an “offline ID”.
Dear, thank you for reply. how can i find the key//?
please help
Error: No key for New Variant offline ID: 0vTA6MA1m5nzrdffOCJC7YmAa4Lp6YNN8lOJ4mt1
Notice: this ID appears be an offline ID, decryption MAY be possible in the future
is it hard coded in virus source?
is it possible to find it with reverse engineering?
how it will be possible to decrypt in the future?
in my ransomware its showing an offline key…Can i decrypt my files which extension is .WAYN?
Your personal ID:
0740ISdikV5TMuF1BBuDZFeJXDU5xmjrzp6rwS1IuZWNpDCt1
Use the following guide: https://www.myantispyware.com/2023/07/06/how-to-remove-wayn-ransomware-decrypt-wayn-files/
i need to decrypt my file please tell me how i recover my data
my personal id is 0795JOsiekf2Li3RNdltbF3sUaUVoKaZs9NHHGEMhVm0Q2DXM
The “0795JOsiekf2Li3RNdltbF3sUaUVoKaZs9NHHGEMhVm0Q2DXM ” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Preciso descriptografar meus arquivos com seguinte id ( Your personal ID:
0813JOsieT6och5XI54fZgJkg18HEZXo1BEwYdHW7DFe8MFc4 ) extensão .zpww, é possível?
Your personal ID:
0822ASdwDDYRUWmbQqFdrmvdg1oujdEmEJ9gxfRFBCUbMnJZ
Additional extention .jzie
Can I recover it?
Can photorec work for videos ?
yes
is there anyway to get my files back?
File: 644519.jpg
Error: No key for New Variant online ID: kjtTPx2VwavIJ4I8Jya4ZeCTacZQFGQvYpc7QFND
Notice: this ID appears to be an online ID, decryption is impossible
do you know of anyway?
The “kjtTPx2VwavIJ4I8Jya4ZeCTacZQFGQvYpc7QFND” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
gracias!!!!!!
Hola. le hago una pregunta. En algun caso ya se pudo desencriptar una clave en linea sea cual sea la variante?. Tengo la extension cdcc. le pregunto esto para saber si existe alguna esperanza en un futuro. Desde ya muchas gracias
In some cases, security researchers have been able to decrypt certain variants when encryption keys were obtained from the attackers’ command and control servers or through other means. However, for variants that use unique online encryption keys, like it might be in your case with the “.cdcc” extension, decrypting the files without the specific key is very challenging.
Although the situation might seem discouraging, there is a glimmer of hope. Security experts are constantly working to find solutions to these problems. It’s possible that vulnerabilities in the ransomware variant affecting your files might be discovered in the future, which could lead to the development of decryption tools.
I recommend keeping up with updates from our team, cybersecurity organizations and specialized forums for information on new decryption tools. It’s also important to have backups of your important files in the future to prevent data loss in these kinds of attacks.
sUnDmgo5a0akeSH4soLpnFN8csfmJXgUrgny2HHN
Good evening ! Please if you can help me I have the computer infected with Ransomware and tried to decrypt files with decrypt_STOPDjvu
Error: No key for New Variant online ID: sUnDmgo5a0akeSH4soLpnFN8csfmJXgUrgny2HHN
Notice: this ID appears to be an online ID, decryption is impossible .
Thank you !
A beautiful evening !
my encrypted file -wiaw.no program has a key to it, please help if you can…thank you
If your files are encrypted with “online key”, they cannot be decrypted. There are no other recovery methods other than those described in the article (https://www.myantispyware.com/2019/12/04/how-to-recover-encrypted-files-ransomware-file-recovery/). If the methods described in this article did not help you, then I advise you to back up your important files and wait until decryption becomes possible. This can happen in a year, two years, or even never. Follow the news on our website or in our Facebook/YouTube account.
I never got a reply
Good evening ! Please if you can help me I have the computer infected with Ransomware and tried to decrypt files with decrypt_STOPDjvu
Error: No key for New Variant online ID: sUnDmgo5a0akeSH4soLpnFN8csfmJXgUrgny2HHN
Notice: this ID appears to be an online ID, decryption is impossible .
Thank you !
A beautiful evening !
The “sUnDmgo5a0akeSH4soLpnFN8csfmJXgUrgny2HHN” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the steps linked below: How to recover encrypted files.
Your personal ID:
0878qualbBCHNvLHvhDeTZVIG7UI7EGEFxtU9waQnUzKCVZA
Additional extention .hlas
help me..
Use the following guide: https://www.myantispyware.com/2024/09/10/how-to-remove-hlas-ransomware-decrypt-hlas-files/