Admin@sectex.net is an email address that cyber criminals use to contact victims of Crysis/Dharma ransomware. Ransomware is a type of malware that blocks access to files by encrypting them, until the victim pays a ransom.
Admin@sectex.net virus locks up the files using AES-RSA technology, that makes it impossible to unlock the encrypted data by the victim without obtaining a key and a decryptor, which is the only way to decrypt affected files. It can be obtained only in the case of payment of the required ransom through cryptocurrency wallet. The ransomware virus encrypts almost of database, videos, documents, music, web application-related files, archives and images, including common as:
.wdp, .ysp, .mp4, .psd, .odp, .zdc, .wp, .zdb, .qic, .t12, .ltx, .mef, .zip, .x3d, .wps, .ws, .jpeg, .mdb, .srf, .mddata, .odc, .xyp, .pef, .dmp, .bc6, .arw, .wsd, .wp4, .erf, .crw, .xlk, .re4, .das, .wdb, .snx, .vfs0, .iwi, .odb, .rofl, .txt, .rtf, .wn, .p7c, .sum, .wbk, .wire, .wbm, .webdoc, .dbf, .ncf, .xml, .rar, .wpd, .eps, .pkpass, .slm, .kdb, .sql, .cfr, .tax, .t13, .0, .dcr, .zw, .asset, .dba, .mpqge, .der, .xpm, .hkx, .wot, .css, .wotreplay, .r3d, .nrw, .pem, .dwg, .mdbackup, .png, .itm, .ff, .bc7, .cer, .xyw, .mcmeta, .wbc, .bay, .wma, .jpe, .wcf, .3dm, .raf, .kf, .layout, .pptx, .w3x, .vpk, .bar, .wpg, .sidd, .xdb, .fpk, .bkf, .2bp, .wbz, .sidn, .orf, .wsh, .wpa, .zi, wallet, .xbdoc, .xll, .1, .wpw, .flv, .sr2, .wmv, .cas, .big, .py, .bkp, .desc, .p7b, .csv, .vtf, .xls, .srw, .ztmp, .rwl, .itdb, .mlx, .gdb, .indd, .lrf, .tor, .xlsm, .iwd, .7z, .wmo, .xlsm, .js, .sb, .xf, .dazip, .wp6, .3ds, .sav, .wpb, .odt, .xlsx, .ppt, .docm, .forge, .jpg, .rb, .pfx, .ods, .vcf, .wmv, .hplg, .ntl, .bik, .wbd, .yml, .ptx, .xmmap, .xy3, .ai, .wbmp, .cr2, .qdf, .wmd, .pdd, .xx, .rgss3a, .bsa, .pst, .zip, .wpl, .wsc, .wpe, .xbplate, .p12, .wm, .arch00, .wpd, .xdl, .pak, .xwp, .3fr, .wb2, .webp, .wmf, .epk, .litemod, .x3f, .menu, .raw, .zif, .map, .cdr, .psk, .xmind, .db0, .rw2, .apk, .rim, .z, .sie, .pptm, .esm, .lbf, .crt, .yal, .sis, .wps, .xld, .hkdb, .z3d, .mov, .x3f, .docx, .doc, .y, .xar, .m2, .ybk, .vpp_pc, .accdb, .xlgc, .xlsb, .syncdb
With the encryption process is finished, all encrypted files will now have a new extension appended to them. In every directory where there are encrypted files, Admin@sectex.net virus drops a file called ‘RETURN FILES.txt’. This file contains a ransom note that is written in the English. The ransom message directs victims to make payment in exchange for a key needed to unlock personal files.
Summary
| Email address | Admin@sectex.net |
| Related ransomware | Dharma family |
| Variants of Dharma that use this address | .[admin@sectex.net].bot |
| Ransom note | RETURN FILES.txt |
| Ransom amount | $300 – $1000 |
| Removal | Free Malware Removal Tools |
| Recover Encrypted files | How to recover ransomware encrypted files |
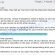
Text presented in Admin@sectex.net ransomware pop-up window:
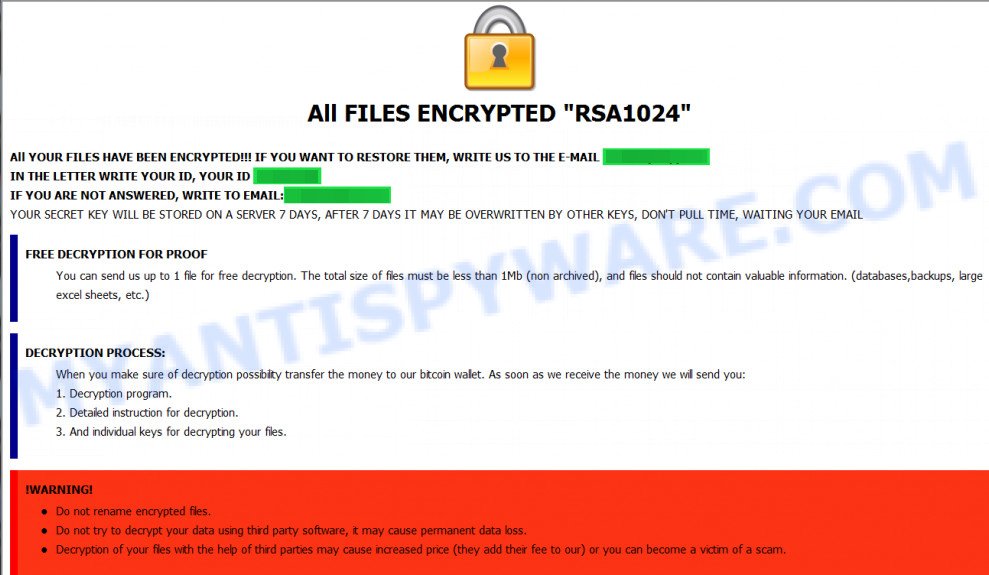
All FILES ENCRYPTED “RSA1024”
All YOUR FILES HAVE BEEN ENCRYPTED!!! IF YOU WANT TO RESTORE THEM, WRITE US TO THE E-MAIL admin@sectex.net
IN THE LETTER WRITE YOUR ID, YOUR ID ***YOUR SECRET KEY WILL BE STORED ON A SERVER 7 DAYS, AFTER 7 DAYS IT MAY BE OVERWRITTEN BY OTHER KEYS, DON’T PULL TIME, WAITING YOUR EMAIL
FREE DECRYPTION FOR PROOF
You can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
DECRYPTION PROCESS:
When you make sure of decryption possibility transfer the money to our bitcoin wallet. As soon as we receive the money we will send you:
1. Decryption program.
2. Detailed instruction for decryption.
3. And individual keys for decrypting your files.
!WARNING!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
How to recover .[admin@sectex.net].bot files
Unfortunately, at the moment it is impossible to decrypt .[admin@sectex.net].bot files, but do not despair. Fortunately, there are several alternative methods that can allow everyone to recover the contents of encrypted files. Each of these methods does not involve the use of special knowledge and paid programs and can be performed by everyone. We have prepared an instruction with illustrations, which describes in detail the process of data recovery. Before you begin data recovery, check your computer for malware using free malware removal tools. You must be 100% sure that admin@datastex.club virus is completely removed.