PLEASE FORWARD THIS EMAIL TO SOMEONE IN YOUR COMPANY WHO IS ALLOWED TO MAKE IMPORTANT DECISIONS! is an extortion email scam that relies on psychological manipulation tactics. Scammers claim to have obtained information that could damage the victims reputation. It should be emphasized that any claims and threats contained in such emails are false and should be ignored.
Scammers use a database of stolen email credentials to send out scam emails to millions of people around the World. The emails are sent to addresses exposed in previous known data breaches in which the user email address and password has been compromised.
We have hacked your website – “PLEASE FORWARD THIS EMAIL TO SOMEONE IN YOUR COMPANY WHO IS ALLOWED TO MAKE IMPORTANT DECISIONS!” – is an extortion email scam
QUICK LINKS
- What is “We have hacked your website” email?
- Should you pay?
- What to do when you receive the scam email?
- Report a Scam
The extortion scam in details
“We have hacked your website” is an extortion scam that is not the only one of its kind, there are many similar ones. They all have similar features: spelling and grammatical errors, statement that the victim’s computer, webcam, network, or website were hacked, threats that the attackers recorded a compromising video or stole compromising materials and a ransom demand.
Depending on the scam, victims are given 24 to 48 hours to pay a ransom in Bitcoin. The extortion scams also contain claims that the victim’s contact information was stolen, allegedly the hacker copied the victim’s contact list and social media credentials. And finally, extortion scams contain threats, the victims must pay a ransom, or compromising materials will be sent to their contacts.
Full text of the scam email:
Your Site Has Been Hacked
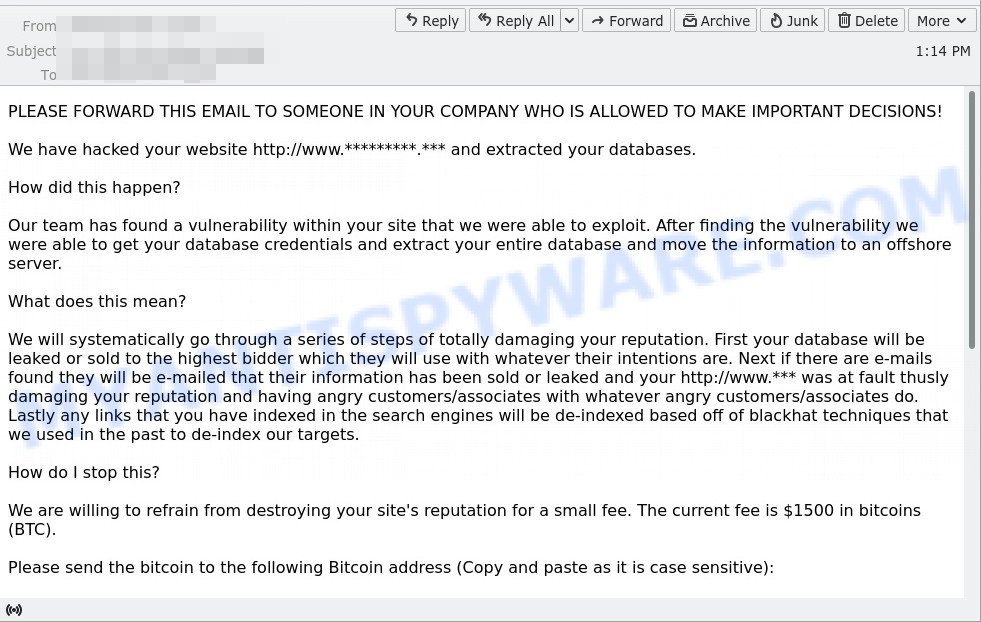
PLEASE FORWARD THIS EMAIL TO SOMEONE IN YOUR COMPANY WHO IS ALLOWED TO MAKE IMPORTANT DECISIONS!
We have hacked your website http://www.*** and extracted your databases.
How did this happen?
Our team has found a vulnerability within your site that we were able to exploit. After finding the vulnerability we were able to get your database credentials and extract your entire database and move the information to an offshore server.
What does this mean?
We will systematically go through a series of steps of totally damaging your reputation. First your database will be leaked or sold to the highest bidder which they will use with whatever their intentions are. Next if there are e-mails found they will be e-mailed that their information has been sold or leaked and your http://www.*** was at fault thusly damaging your reputation and having angry customers/associates with whatever angry customers/associates do. Lastly any links that you have indexed in the search engines will be de-indexed based off of blackhat techniques that we used in the past to de-index our targets.
How do I stop this?
We are willing to refrain from destroying your site’s reputation for a small fee. The current fee is $1500 in bitcoins (BTC).
Please send the bitcoin to the following Bitcoin address (Copy and paste as it is case sensitive):
36nmXWJ2JBTUib5UeGeds5yDT5WYm6n6Cs
Once you have paid we will automatically get informed that it was your payment. Please note that you have to make payment within 5 days after receiving this e-mail or the database leak, e-mails dispatched, and de-index of your site WILL start!
How do I get Bitcoins?
You can easily buy bitcoins via several websites or even offline from a Bitcoin-ATM. We suggest you to start with localbitcoins.com, paxful.com or do a google search.
What if I don’t pay?
If you decide not to pay, we will start the attack at the indicated date and uphold it until you do, there’s no counter measure to this, you will only end up wasting more money trying to find a solution. We will completely destroy your reputation amongst google and your customers.
This is not a hoax, do not reply to this email, don’t try to reason or negotiate, we will not read any replies. Once you have paid we will stop what we were doing and you will never hear from us again!
Please note that Bitcoin is anonymous and no one will find out that you have complied.
Typically, extortion scams are sent via email, thousands at a time, and are part of larger spam campaigns. As with many other types of scams, scammers are evolving their methods to deliver their messages to potential victims. Such attacks can be personalized and sent out in smaller numbers to avoid detection. Scammers can use reputable services, change and personalize the content of each message, and avoid including links or attachments – all in an attempt to bypass security.
There’s a new version of the scam making the rounds:
Text presented in the scam email:
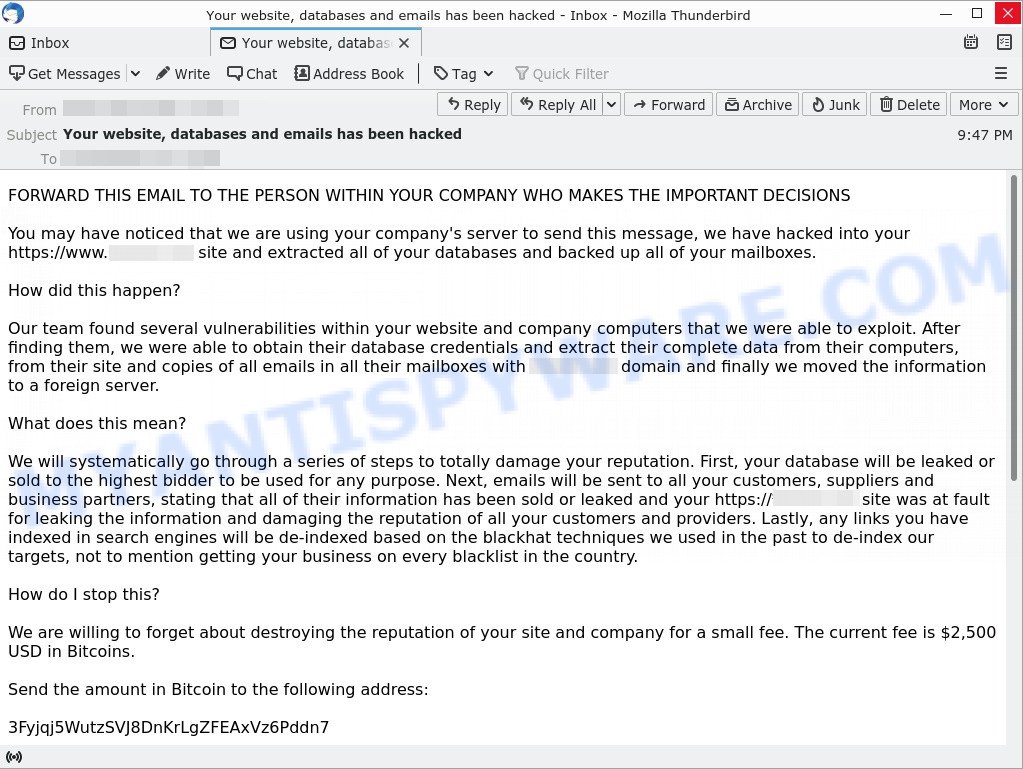
FORWARD THIS EMAIL TO THE PERSON WITHIN YOUR COMPANY WHO MAKES THE IMPORTANT DECISIONS
You may have noticed that we are using your company’s server to send this message, we have hacked into your https://www.*******.*** site and extracted all of your databases and backed up all of your mailboxes.
How did this happen?
Our team found several vulnerabilities within your website and company computers that we were able to exploit. After finding them, we were able to obtain their database credentials and extract their complete data from their computers, from their site and copies of all emails in all their mailboxes with *******.*** domain and finally we moved the information to a foreign server.
What does this mean?
We will systematically go through a series of steps to totally damage your reputation. First, your database will be leaked or sold to the highest bidder to be used for any purpose. Next, emails will be sent to all your customers, suppliers and business partners, stating that all of their information has been sold or leaked and your https://*******.*** site was at fault for leaking the information and damaging the reputation of all your customers and providers. Lastly, any links you have indexed in search engines will be de-indexed based on the blackhat techniques we used in the past to de-index our targets, not to mention getting your business on every blacklist in the country.
How do I stop this?
We are willing to forget about destroying the reputation of your site and company for a small fee. The current fee is $2,500 USD in Bitcoins.
Send the amount in Bitcoin to the following address:
3Fyjqj5WutzSVJ8DnKrLgZFEAxVz6Pddn7
Once you have made your payment, we will automatically be informed of it. At the precise moment that you have read this message, you have a period of 72 hours to make the payment, or I guarantee that the reputation of your company will be completely destroyed. The proof that we have access and all your data is that this message has been sent using your company’s servers.
How do I get Bitcoins?
You can easily buy bitcoins through various websites.
What happens if I don’t pay?
If you decide not to pay, we will launch the attack after 72 hours and keep it until you do, there is no countermeasure to this, you will just end up wasting more money trying to find a solution. We will completely destroy your reputation with your customers, your suppliers, your partners, on google and the entire country.
This is not a hoax, do not try to reason or negotiate, we will not read any answers. Once you’ve paid, we’ll stop what we were doing, we’ll destroy all data taken from your site, your databases, your mailboxes, and you’ll never hear from us again.
Keep in mind that the payment with Bitcoin is anonymous and no one will know that you have complied. The time is running.
Should you pay?

The best advice is: Don’t pay the ransom! If you receive an extortion email, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Name | “PLEASE FORWARD THIS EMAIL TO SOMEONE IN YOUR COMPANY WHO IS ALLOWED TO MAKE IMPORTANT DECISIONS!” EMAIL SCAM |
| Type | Phishing, Bitcoin Email Scam, Fraud, Scam |
| Subject line | Your Site Has Been Hacked, “Your website, databases and emails has been hacked” |
| Sender | hacker@*** |
| Scammers Cryptowallet Addresses | bc1qvmg0x7v4c6f0hajs3uru09uqhkuepl4d5vqhev, 3Fyjqj5WutzSVJ8DnKrLgZFEAxVz6Pddn7, 3PmYSqtG5x5bGNrsYUy5DGtu93qNtsaPRH, 1JToMSCtc4nW3fNDUL4xV9QYqmyKJEYMdj, 3GGQxApV9d6U6CVPeXPSCMYraJdCnmz5u1, 36nmXWJ2JBTUib5UeGeds5yDT5WYm6n6Cs |
| Ransom amount | $2500, $1500 |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like the PLEASE FORWARD THIS EMAIL TO SOMEONE IN YOUR COMPANY WHO IS ALLOWED TO MAKE IMPORTANT DECISIONS! SCAM, our computer security experts recommend follow some easy steps below |
Examples of scam emails
There are many extortion scams circulating via email. Scammers often change the content of emails in order to deceive victims and bypass the security system. Payment from your account, FINAL WARNING Email, I have to share bad news with you are other examples of extortion scams. Such emails are also often used to distribute ransomware, trojans, worms and other malware.
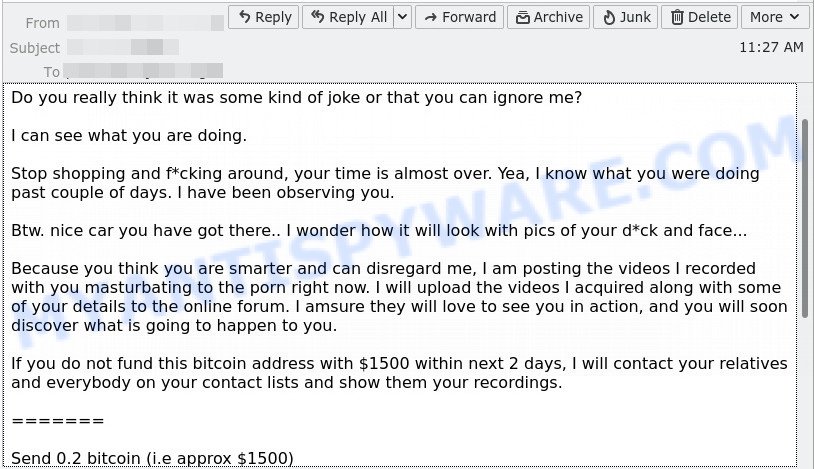
- FINAL WARNING email is a sextortion scam
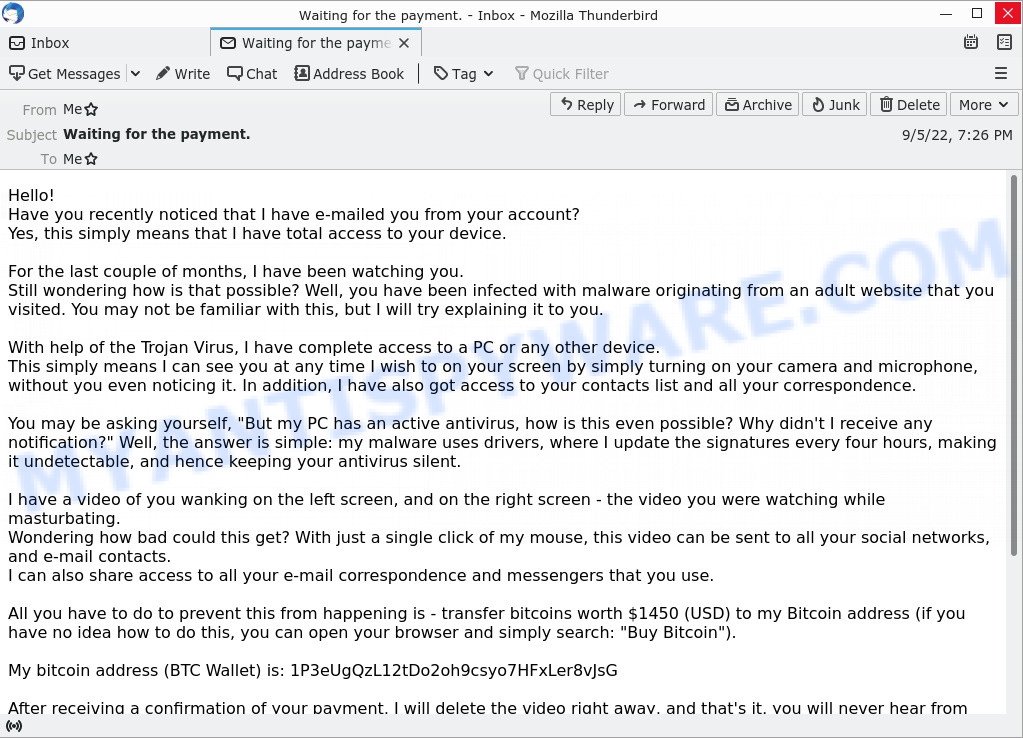
- Waiting for the payment. Email Scam
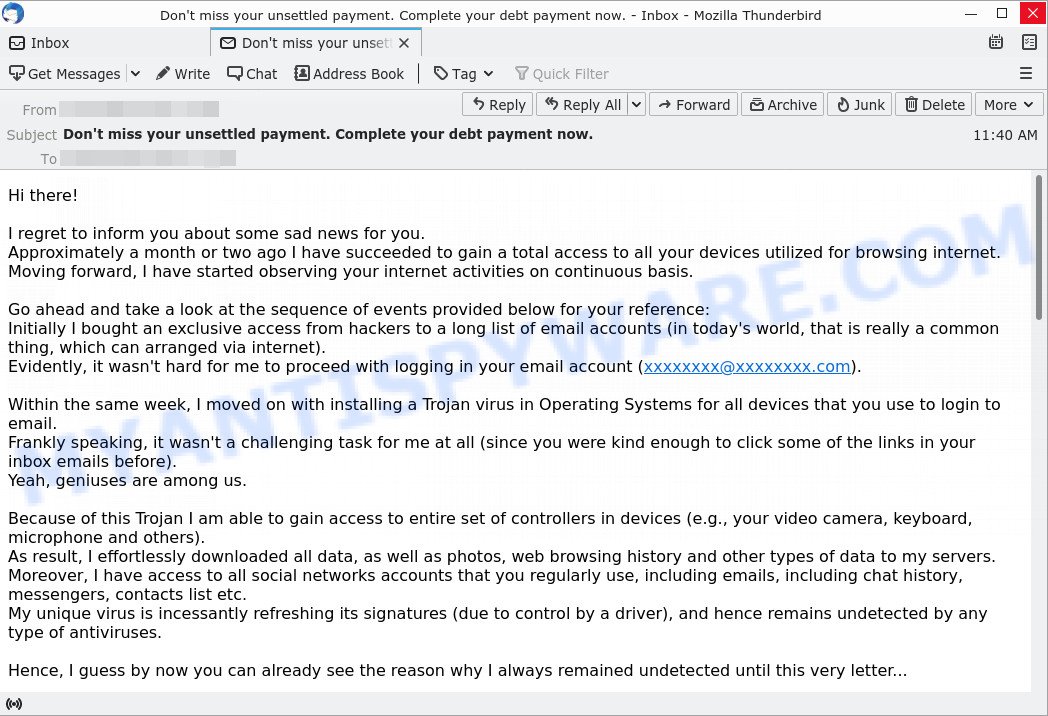
- “Don’t miss your unsettled payment. Complete your debt payment now.” email is a SCAM
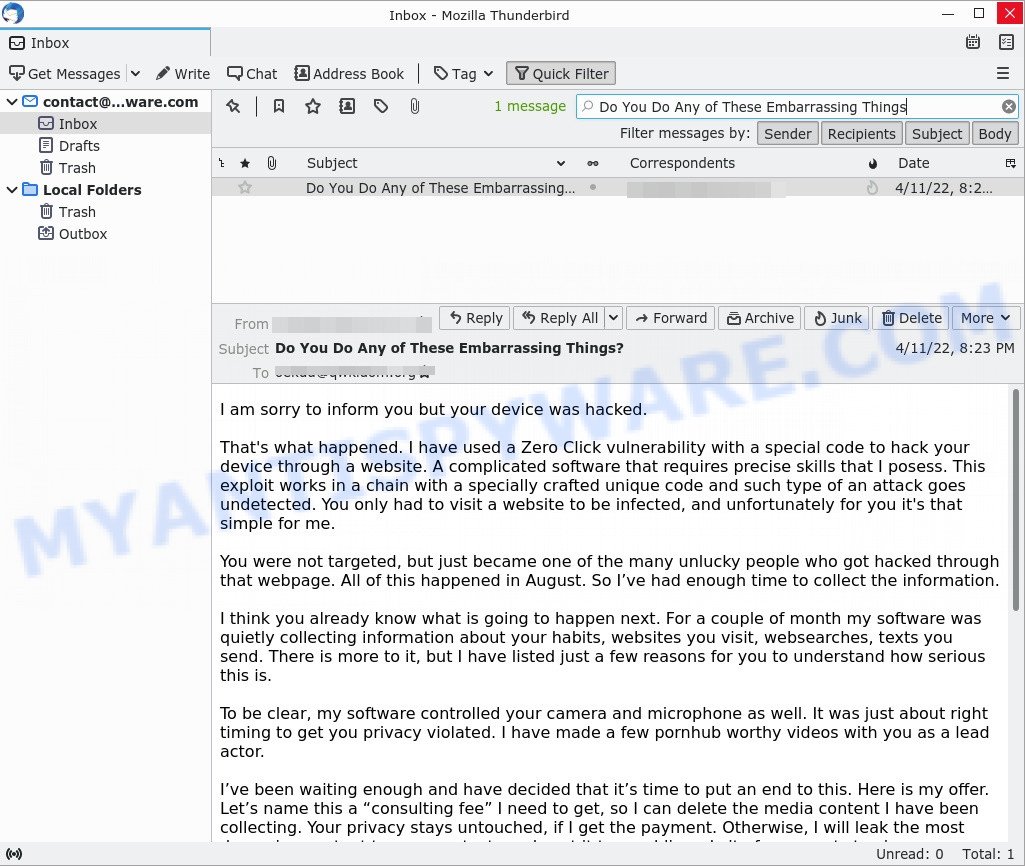
- “Do You Do Any of These Embarrassing Things” email message is a sextortion SCAM
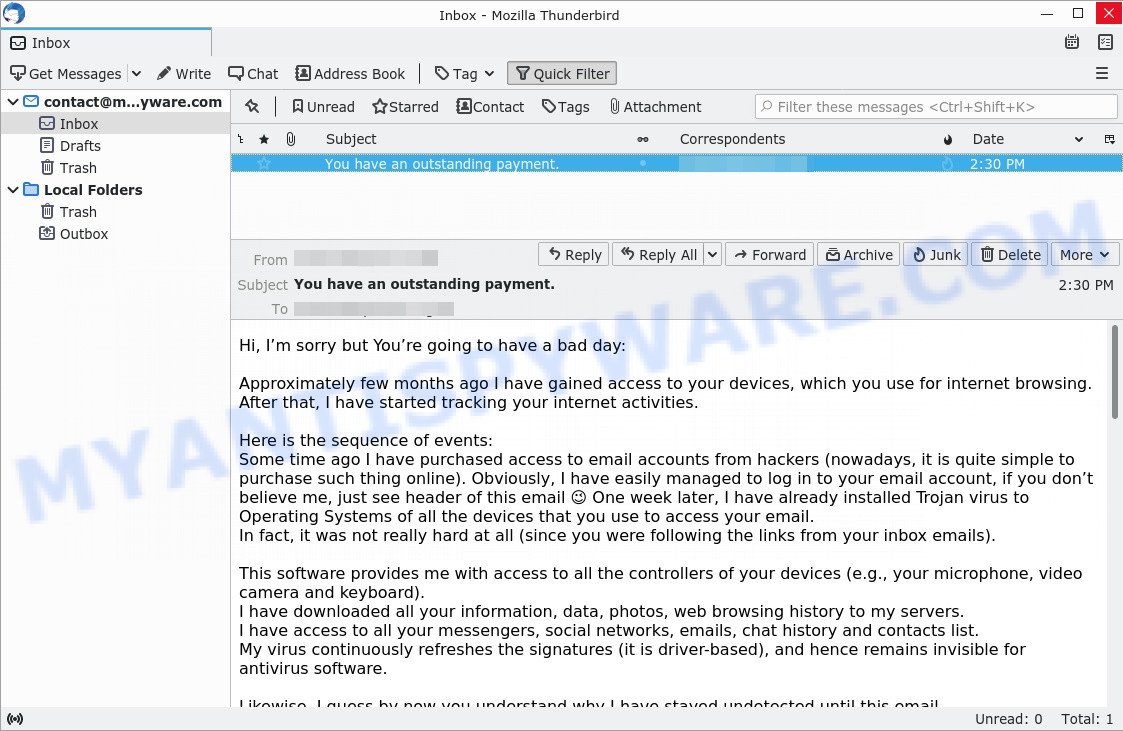
- The “Hi, I’m sorry but You’re going to have a bad day” email message is a new SCAM
What to do when you receive the “PLEASE FORWARD THIS EMAIL TO SOMEONE IN YOUR COMPANY WHO IS ALLOWED TO MAKE IMPORTANT DECISIONS!” EMAIL SCAM
We advice to someone who gets this fraudulence message:
- Do not panic.
- Scammers will try to rush you, put pressure on you to make a decision to pay them. We recommend that you do not pay the ransom because your payment will only increase the attacks against you.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your PC for malware
If you suspect that your computer is infected with malware, you accidentally clicked on a link in the scam email, or just want to scan your computer, then use one of the best free malware removal tools. MalwareBytes is an antivirus that can be used to perform a virus scan, detect and remove almost all the forms of malicious programs including ransomware, trojans, worms, adware, browser hijackers, potentially unwanted software and spyware. MalwareBytes has real-time protection that can defeat most malicious software and ransomware. Despite so many features, it does not reduce the performance of your computer. You can use MalwareBytes with any other antivirus without any conflicts.
First, please go to the link below, then click the ‘Download’ button in order to download the latest version of MalwareBytes.
327721 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When the downloading process is done, close all windows on your computer. Further, launch the file named MBSetup. If the “User Account Control” dialog box pops up like below, click the “Yes” button.
It will show the Setup wizard which will assist you install MalwareBytes on the computer. Follow the prompts and do not make any changes to default settings.
After the setup is complete successfully, press “Get Started” button. Then MalwareBytes AntiMalware will automatically run and you can see its main window such as the one below.
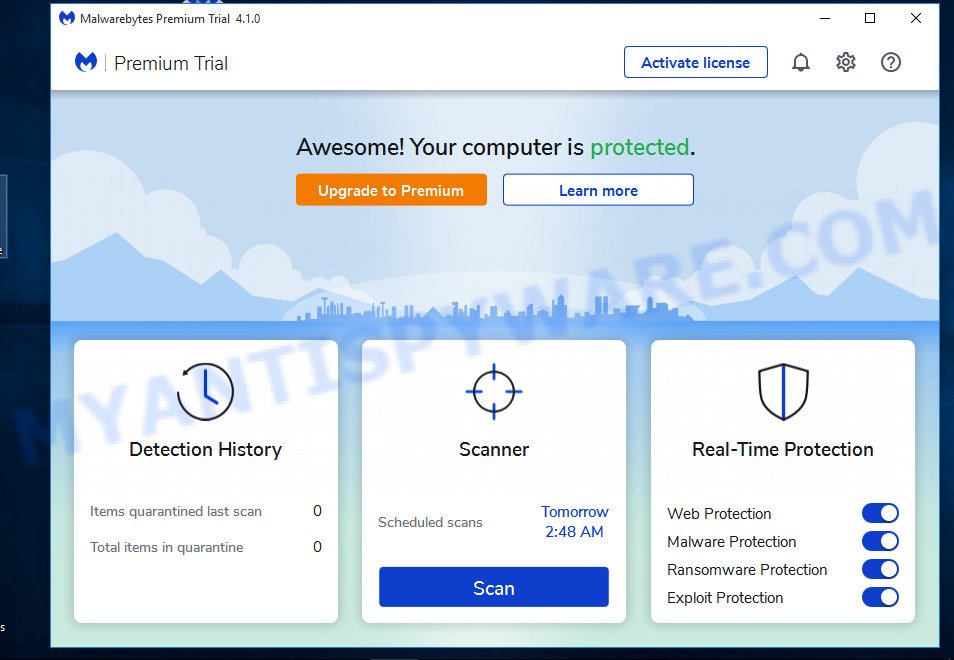
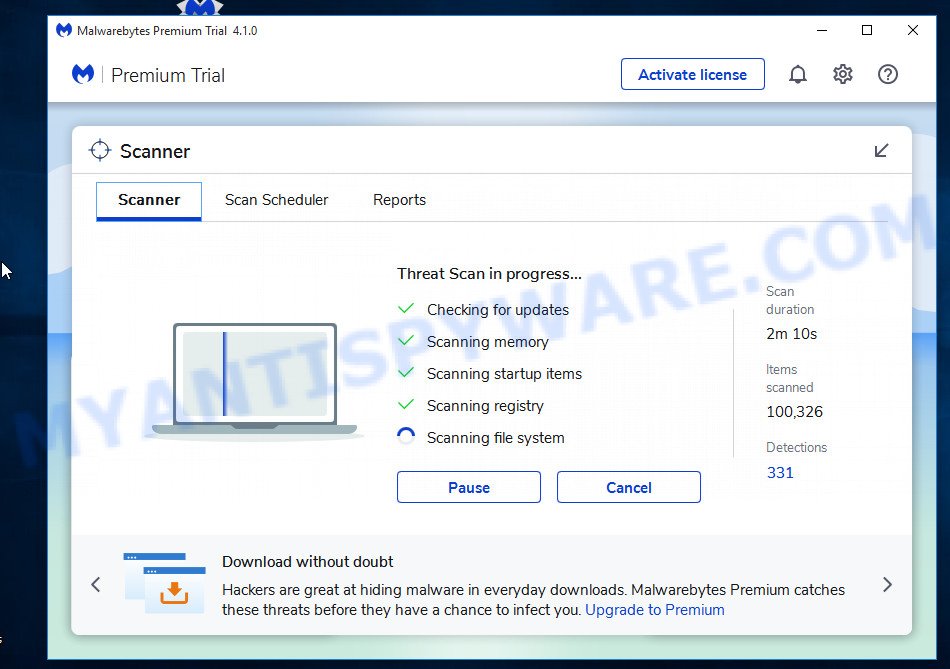
Next, click the “Scan” button for scanning your computer for malicious software and other security threats. A system scan can take anywhere from 5 to 30 minutes, depending on your computer. While MalwareBytes is scanning, you can see how many objects it has identified as threat.
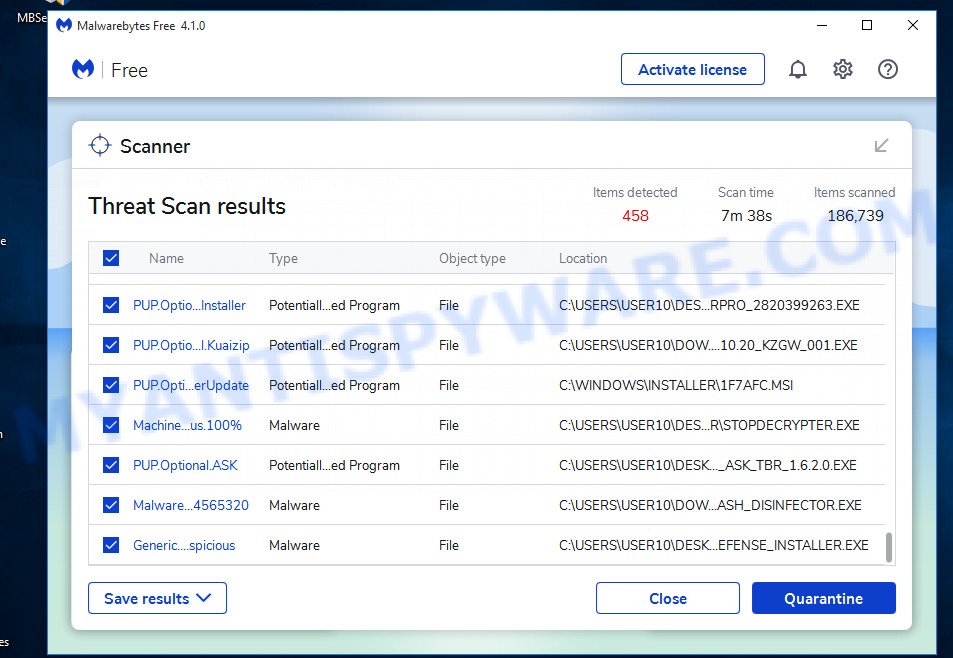
When the scanning is done, the results are displayed in the scan report. In order to remove all threats, simply press “Quarantine” button.
We suggest you look at the following video, which completely explains the process of using MalwareBytes to remove malicious software.
If you are having issues with malware removal, then check out Kaspersky virus removal tool. It can easily remove trojans, spyware, browser hijackers, adware, worms and ransomware with all their components such as files, folders and registry entries. Visit the page linked below to download the latest version of Kaspersky virus removal tool for Windows.
129493 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing sites, install an ad blocking program like AdGuard. It can block malicious and misleading websites, stop unwanted ads and pop-ups while using Internet Explorer, Google Chrome, Firefox and Edge. So, if you like to surf the Internet and want to protect your computer from phishing scams, then AdGuard is your best choice.
Installing AdGuard is very easy. First you’ll need to download AdGuard by clicking on the link below.
27036 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
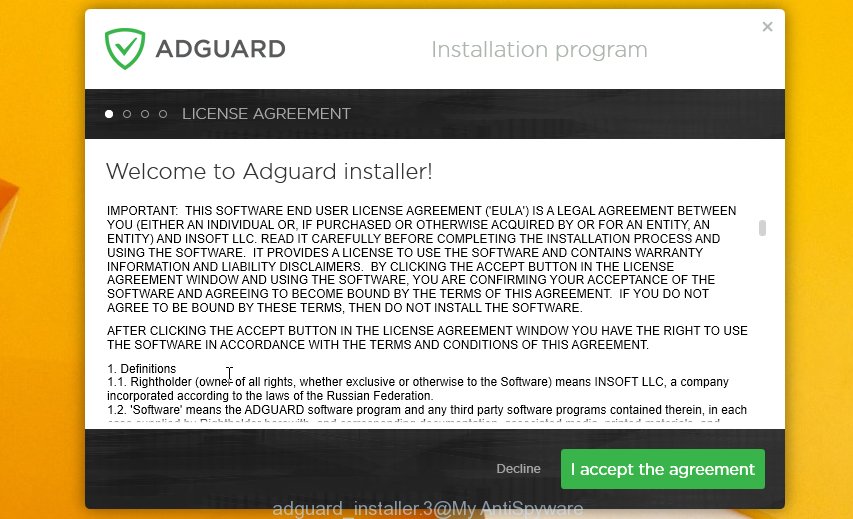
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Report a Scam
If you receive a scam email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.