What is Mpal file extension
.Mpal file extension is an extension that is used by the newest variant of STOP (djvu) ransomware to mark files that have been encrypted. Mpal ransomware is a malware created by criminals that restricts access to the victim’s files by encrypting them and demands a ransom for a pair of key-decryptor, necessary for decrypting files. Files encrypted with .mpal extension become useless, their contents cannot be read without the key that the criminals have. Fortunately, there is a free Mpal File Decrypt Tool called ‘STOP (Djvu) Decryptor’ that allows in some cases to decrypt encrypted files. Scroll through this article below to learn more about this decrypt tool and how to use it, as well as alternative ways to recover the contents of encrypted files.
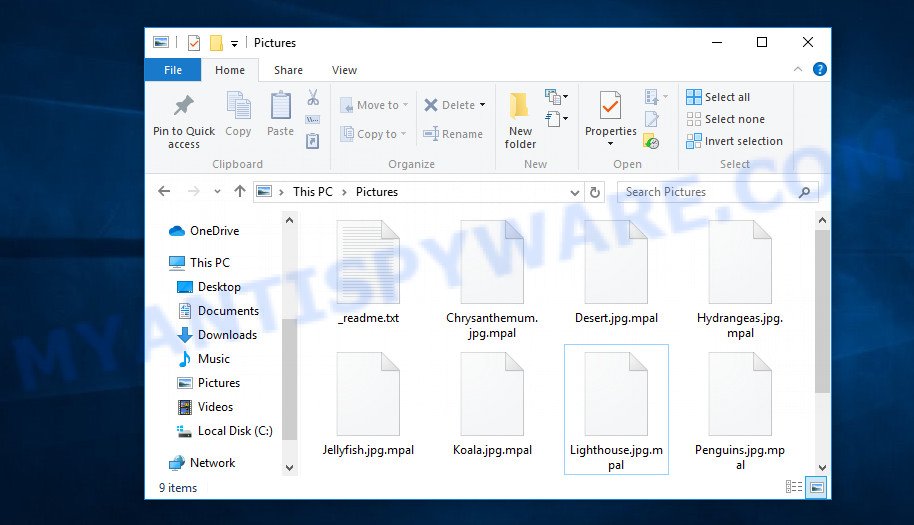
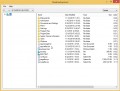
Screenshot of files encrypted by Mpal virus (‘.mpal’ file extension)
What is Mpal ransomware
First discovered recently, Mpal ransomware is the newest version of STOP ransomware. This is already the is the 223th variant (v0223) of STOP ransomware. Like other variants, it encrypts all files on the computer and then demands a ransom for decryption. This virus encrypts files using a strong encryption method, which eliminates the possibility of finding a key in any way. For each victim, Mpal uses a unique key with a small exception. If the virus cannot establish a connection with its command and control server (C&C) before starting the encryption process, then it uses an offline key. This key is the same for different victims, which makes it possible in some cases to decrypt files that were encrypted during the ransomware attack.

Mpal has the ability to encrypt files of any type, regardless of what is in them. But it skips files with the extension: .ini, .dll, .lnk, .bat, .sys and files named ‘_readme.txt’. Thus, the following common file types can be easily encrypted:
.wbz, .dazip, .y, .w3x, .sql, .wpd, .das, .wmv, .xyp, .xlgc, .ysp, .pdf, .3fr, .pptm, .raw, .ff, .xld, .r3d, .cer, .docm, .ztmp, .wbm, .ntl, .wpb, .gdb, .wma, .wdb, .x3d, .pdd, .wsh, .iwd, .xx, .wire, .p7c, .dxg, .sum, .xls, .wotreplay, .sid, .jpe, .jpeg, .hkx, .m4a, .gho, .wps, .wbc, .docx, .zi, .raf, .wma, .apk, .xlk, .vpk, .asset, .wb2, .3dm, .itm, .3ds, .xmmap, .wbk, .bik, .yml, .ws, .db0, .xpm, wallet, .wsc, .fsh, .svg, .wpt, .vdf, .indd, .cdr, .mrwref, .wav, .odb, .rgss3a, .1, .avi, .bsa, .sr2, .sb, .dwg, .mpqge, .blob, .xwp, .wmf, .wp6, .css, .zdc, .wp5, .pkpass, .icxs, .csv, .zip, .7z, .ncf, .esm, .x3f, .zw, .rar, .desc, .m2, .jpg, .zip, .wri, .mdb, .sav, .webdoc, .xf, .wp7, .der, .wpg, .ibank, .itl, .wpw, .fos, .psd, .hkdb, .litemod, .py, .wp4, .big, .xmind, .doc, .mlx, .qic, .srw, .hvpl, .d3dbsp, .itdb, .tax, .wpa, .wbmp, .zif, .wmo, .p12, .t13, .xlsm, .hplg, .bay, .pptx, .yal, .cas, .rb, .map, .z, .crt, .xml, .vtf, .wsd, .arch00, .odp, .slm, .srf, .xy3, .xlsx, .erf, .ppt, .nrw, .x3f, .rofl, .wmd, .wbd, .epk, .wpl, .odm, .t12, .lvl, .ybk, .xdl, .vcf, .pem, .dbf, .flv, .rtf, .wp, .odc, .wmv, .lrf, .x, .kdc, .tor, .orf, .mdf, .xll, .vfs0, .bc7, .dcr, .xls, .arw, .mov, .xlsx, .ptx, .1st, .sie, .snx, .ods, .ai, .mef, .rwl, .psk, .wpe, .dba
Each file that has been encrypted will be renamed. This means the following. If the file was called ‘document.docx’, then after encryption, it will be named ‘document.docx.mpal’. Mpal virus can encrypt files located on all drives connected to the computer. Therefore, files located in network attached storage and external devices can also be encrypted. It encrypts file by file, when all the files in the directory are encrypted, it drops a new file in the directory, which is called ‘_readme.txt’. Below is the contents of this file.
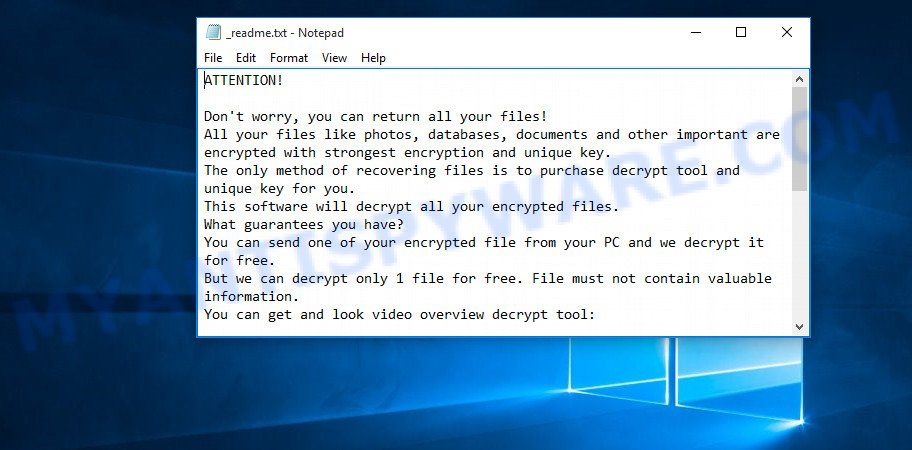
Screenshot of the contents of ‘_readme.txt’ file (Mpal ransom note)
All directories with encrypted files have this file. But the contents of this file are the same everywhere. This file contains a message from Mpal creators. In this message, the criminals report that all the files were encrypted and the only way to decrypt them is to buy a decryptor and key. Attackers demand a ransom of $490, if the victim does not pay the ransom within 72 hours, then the ransom will double to $980. Mpal authors left two email addresses that the victim must use to contact them. To confirm the possibility of decryption, criminals offer to decrypt one file that does not contain important information for free. But it’s obvious that there is no guarantee that even by paying the ransom, the victim will be able to decrypt all files that have been encrypted.
Threat Summary
| Name | Mpal |
| Type | Ransomware, Crypto malware, Crypto virus, File locker, Filecoder |
| Encrypted files extension | .mpal |
| Ransom note | _readme.txt |
| Contact | helpmanager@mail.ch, helpdatarestore@firemail.cc |
| Ransom amount | $980/$490 in Bitcoins |
| Detection Names | Gen:NN.ZexaF.34108.WqW@aebl1hL, W32.AIDetectVM.malware, Generic.mg.d215df8dcece3599, Trojan:Win32/Wacatac.D!ml, Trojan.Malware.300983.susgen, W32.Malware.gen, UDS:DangerousObject.Multi.Generic |
| Symptoms | Personal files won’t open. All of your documents, photos and music have a new file extension appended to the filenames. Files called such as ‘_readme.txt’, ‘READ-ME’, ‘_open me’, _DECRYPT YOUR FILES’ or ‘_Your files have been encrypted” in every folder with an encrypted file. New files on your desktop, with name variants of: ‘HOW_TO_DECRYPT.txt’, ‘DECRYPT.txt’ or ‘README.txt’. |
| Distribution ways | Malicious email attachments. Exploit kits (cybercriminals use crypto malware packaged in an ‘exploit kit’ that can find a vulnerability in Web-browser, PDF reader, Adobe Flash Player, Windows operating system). Social media, like web-based instant messaging programs. Cybercriminals use suspicious advertisements to distribute malware with no user interaction required. |
| Removal | Mpal ransomware removal guide |
| Decryption | Mpal File Decrypt Tool |
Mpal authors scare victims by saying that encrypted files cannot be decrypted without paying a ransom. And unfortunately this is true, the contents of the files cannot be read while the files are encrypted, and a key and decryptor are needed to decrypt them.
Fortunately, Emsisoft created a decryptor (Mpal File Decrypt Tool). This decryptor can help each victim to decrypt .mpal files for free. But in addition to the decryptor, the key is still necessary. As we reported above, the ransomware can use two types of keys. An offline key can be determined by researchers, but only criminals have an online key. Thus, files encrypted with so called ‘offline key’ can be decrypted. And all files that have been encrypted with so called ‘online key’ cannot yet be decrypted. In this case, the alternative methods listed below in this article can be used to recover the contents of these files.
How to remove Mpal ransomware virus & Decrypt .mpal files
If your documents, the files of your friends or colleagues, were encrypted with Mpal ransomware virus, then you need to follow a few steps listed below that will allow you to find and remove Mpal, as well as decrypt or restore the encrypted files. It is very important to read the entire instruction manual carefully and make sure to understand it all. We advise you not to skip any steps, each of the steps is very important and must be completed by you. In order not to get confused and not miss an important point in the instructions, we recommend that you print this article or open it on your smartphone.
- How to remove Mpal ransomware
- How to decrypt .mpal files
- How to restore .mpal files
- How to protect your system from Mpal ransomware
How to remove Mpal ransomware
The presence of encrypted files on the computer means one thing – the computer has become the victim of ransomware attack. Therefore, regardless of the fact that it seems to you that Mpal ransomware virus is no longer on the computer, you should check the computer with malware removal utilities. Do not try to skip this step and immediately begin to decrypt your files. By doing so, you can kill the ability to decrypt files or block alternative methods of data recovery.
In order to scan the system for ransomware and other malware, we recommend using free malware removal tools. These utilities have all the necessary functions, they can find ransomware and its components, remove Mpal ransomware virus from your computer for free. Below we provide a list of the best malware removal utilities, with brief instructions describing the process of identifying and removing the ransomware.
Use Zemana AntiMalware (ZAM) to remove Mpal ransomware
Zemana AntiMalware is a malware removal utility. Currently, there are two versions of the tool, one of them is free and second is paid (premium). The principle difference between the free and paid version of the tool is real-time protection module. If you just need to check your system for malware and remove Mpal ransomware related folders,files and registry keys, then the free version will be enough for you.
- Zemana AntiMalware can be downloaded from the following link. Save it on your MS Windows desktop.
Zemana AntiMalware
164721 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
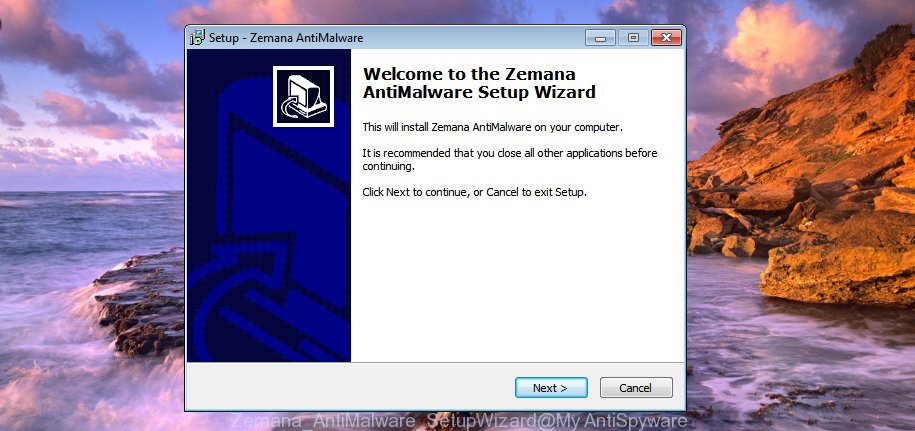
- Once you have downloaded the setup file, make sure to double click on the Zemana.AntiMalware.Setup. This would start the Zemana installation on your computer.
- Select setup language and press ‘OK’ button.
- On the next screen ‘Setup Wizard’ simply click the ‘Next’ button and follow the prompts.

- Finally, once the installation is finished, Zemana will open automatically. Else, if doesn’t then double-click on the Zemana AntiMalware (ZAM) icon on your desktop.
- Now that you have successfully install Zemana Anti Malware, let’s see How to use Zemana Free to remove Mpal ransomware from your computer.
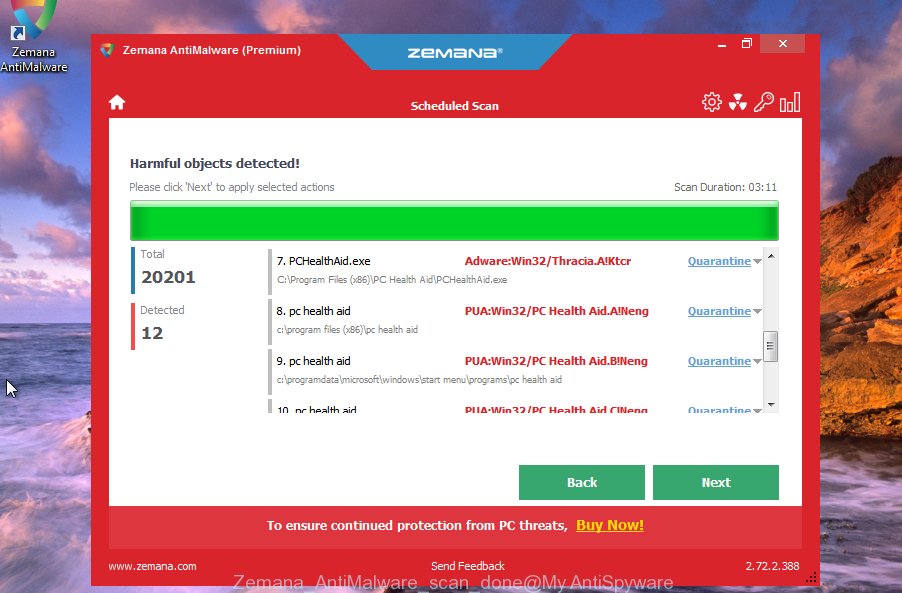
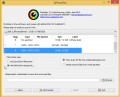
- After you have launched the Zemana Free, you will see a window similar to the one below, just press ‘Scan’ button to begin scanning your system for the Mpal ransomware.

- Now pay attention to the screen while Zemana Anti-Malware (ZAM) scans your personal computer.

- After that process is complete, Zemana Anti Malware (ZAM) will show you the results. Review the scan results and then press ‘Next’ button.

- Zemana may require a reboot PC in order to complete the Mpal ransomware removal procedure.
- If you want to permanently delete ransomware virus from your PC system, then click ‘Quarantine’ icon, select all malicious software, adware, potentially unwanted software and other items and click Delete.
- Restart your computer to complete the ransomware removal procedure.
Remove Mpal virus with MalwareBytes
We advise using the MalwareBytes Anti-Malware. You may download and install MalwareBytes AntiMalware (MBAM) to detect and remove Mpal from your PC. When installed and updated, this free malicious software remover automatically identifies and deletes all threats exist on the system.
Installing the MalwareBytes is simple. First you will need to download MalwareBytes on your PC from the link below.
326997 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
Once the downloading process is complete, run it and follow the prompts. Once installed, the MalwareBytes Anti Malware (MBAM) will try to update itself and when this task is finished, click the “Scan Now” button to detect the Mpal ransomware virus, other kinds of potential threats like malware and trojans. Depending on your personal computer, the scan can take anywhere from a few minutes to close to an hour. When a threat is found, the number of the security threats will change accordingly. Wait until the the checking is complete. When you are ready, click “Quarantine Selected” button.
The MalwareBytes Free is a free program that you can use to remove all detected folders, files, services, registry entries and so on. To learn more about this malicious software removal utility, we recommend you to read and follow the instructions or the video guide below.
Remove Mpal with KVRT
If MalwareBytes and Zemana anti-malware cannot remove the Mpal virus, then we advises to use Kaspersky virus removal tool (KVRT). KVRT is a free removal tool for ransomware, worms, spyware, trojans, adware software, PUPs and other malicious software.
Download Kaspersky virus removal tool (KVRT) from the following link. Save it to your Desktop so that you can access the file easily.
129215 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
When the downloading process is done, double-click on the Kaspersky virus removal tool icon. Once initialization procedure is finished, you will see the Kaspersky virus removal tool screen as shown on the image below.
Click Change Parameters and set a check near all your drives. Press OK to close the Parameters window. Next click Start scan button to perform a system scan for the Mpal ransomware virus and other known infections. A system scan can take anywhere from 5 to 30 minutes, depending on your system. While the Kaspersky virus removal tool tool is scanning, you can see how many objects it has identified as being infected by malware.
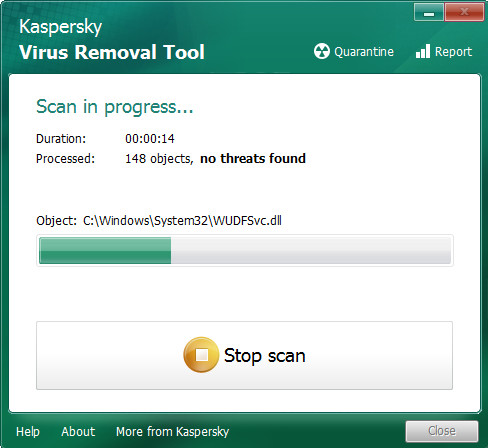
After the checking is complete, you’ll be shown the list of all detected items on your PC similar to the one below.
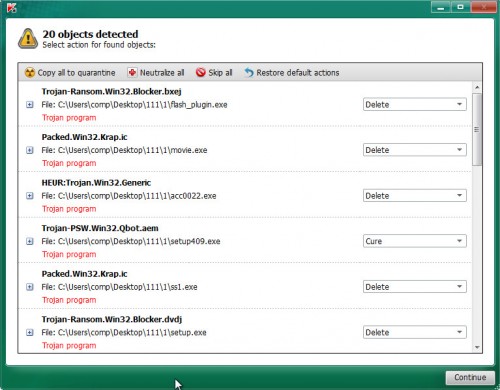
Make sure all threats have ‘checkmark’ and click on Continue to start a cleaning process.
How to decrypt .mpal files
All files with the ‘.mpal’ extension are encrypted. Their contents cannot be unlocked simply by removing this extension or completely changing the filename. To decrypt .mpal files, you need a decryptor. Fortunately, there is a free Mpal File Decrypt Tool that can decrypt .mpal files. Below we provide instructions on where to download and how to use Mpal File Decrypt Tool.
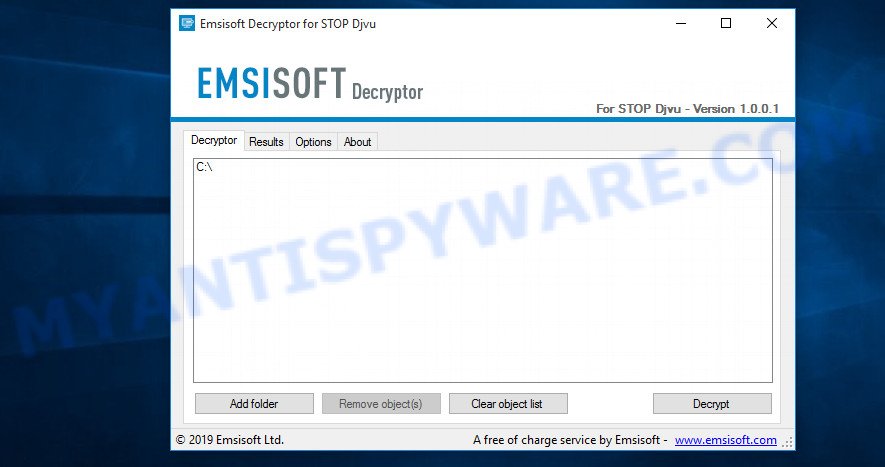
Mpal File Decrypt Tool (STOP Djvu decryptor)
To decrypt .mpal files, use Mpal File Decrypt Tool
- Download Mpal File Decrypt Tool from the following link.
STOP Djvu decryptor - Scroll down to ‘New Djvu ransomware’ section.
- Click the download link and save the ‘decrypt_STOPDjvu.exe’ file to your desktop.
- Run decrypt_STOPDjvu.exe, read the license terms and instructions.
- On the ‘Decryptor’ tab, using the ‘Add a folder’ button, add the directory or disk where the encrypted files are located.
- Click the ‘Decrypt’ button.
Mpal File Decrypt Tool is a free tool that allows everyone to decrypt .mpal files for free. At the moment, the decryptor can only decrypt files that have been encrypted with an offline key. Unfortunately, if the files were encrypted with an online key, then the free decryptor is completely useless. In this case, there is a chance to restore the encrypted files using alternative methods, which are described below.
How to find out which key was used to encrypt files
Since Mpal File Decrypt Tool only decrypts files encrypted with the offline key, each Mpal’s victim needs to find out which key was used to encrypt the files. Determining the type of key used is not difficult. Below we give two ways. Use any of them. We recommend using the second method, as it is more accurate.
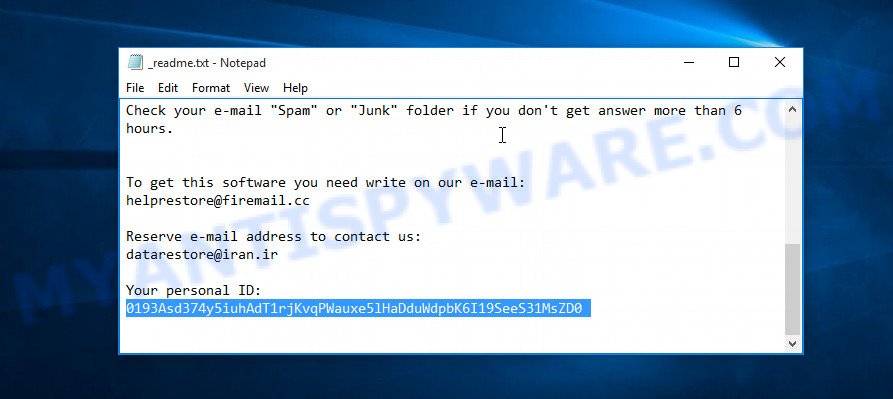
Personal ID is highlighted here
Find out the type of key using ‘_readme.txt’ file
- Open the ransom demand message (‘_readme.txt’ file).
- Scroll down to the end of the file.
- There you will see a line with the text ‘Your personal ID’.
- Below is a line of characters that starts with ‘0223’ – this is your personal id.
Find out the type of key using ‘PersonalID.txt’ file
- Open disk C.
- Open directory ‘SystemID’.
- Open file named ‘PersonalID.txt’. This file lists ‘Personal ID’s that match the keys that the virus used to encrypt files.
The ‘Personal ID’ is not a key, it is an identifier related to a key that was used to encrypt files. If the ID ends with ‘t1’, then the files are encrypted with an offline key. If the ID does not end with ‘t1’, Mpal virus used an online key. If you could not figure out how to determine which key was used to encrypt files, then we can help. Just write a request here or in the comments below.
Mpal File Decypt Tool : No key for New Variant offline ID
If during decryption of .mpal files the Mpal File Decypt Tool reports No key for New Variant offline ID, then this means the following: your files are encrypted with an ‘offline key’, but the key itself has not yet been found by security researchers, in this case, you need to be patient and wait a while, in addition, you can also use alternative ways for recovering encrypted data. It is impossible to say exactly when the ‘offline key’ will be determined. Sometimes it takes several days, sometimes more. We recommend that you try to decrypt .mpal files from time to time. You can also use alternative ways listed below for recovering encrypted data.
Mpal File Decypt Tool : No key for New Variant online ID
If, when you try to decrypt .mpal files, the Mpal File Decypt Tool reports No key for New Variant online ID, then this means that your files are encrypted with an ‘online key’ and their decryption is impossible, since only the Mpal authors have the key necessary for decryption. In this case, you need to use alternative methods listed below to restore the contents of encrypted files.
How to restore .mpal files
As we already said, the Mpal File Decrypt Tool can only decrypt files encrypted using the so called ‘offline key’. What to do when files were encrypted with an online key? Even in this case, everyone has a chance to recover the contents of encrypted files. This is possible due to the existence of several alternative ways to restore files. Each of these methods does not require a decryptor and a unique key, which is in the hands of criminals. The only thing we strongly recommend that you perform (if you have not already done so) is to perform a full scan of the computer. You must be 100% sure that Mpal ransomware has been removed. To find and remove ransomware, use the free malware removal tools.
Use ShadowExplorer to recover .mpal files
The Windows OS (10, 8, 7 , Vista) has one very useful feature, it makes copies of all files that have been modified or deleted. This is done so that the user can recover, if necessary, the previous version of accidentally deleted or damaged files. These copies of the files are called ‘Shadow copies’. One tool that can help you recover files from the Shadow copies is ShadowExplorer. It is very small tool and easy to use. Unfortunately, ransomware often delete Shadow copies, thus blocking this method of recovering encrypted files. Nevertheless, be sure to try this method.
Download ShadowExplorer on your personal computer by clicking on the link below.
439350 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
When the downloading process is complete, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as displayed on the image below.
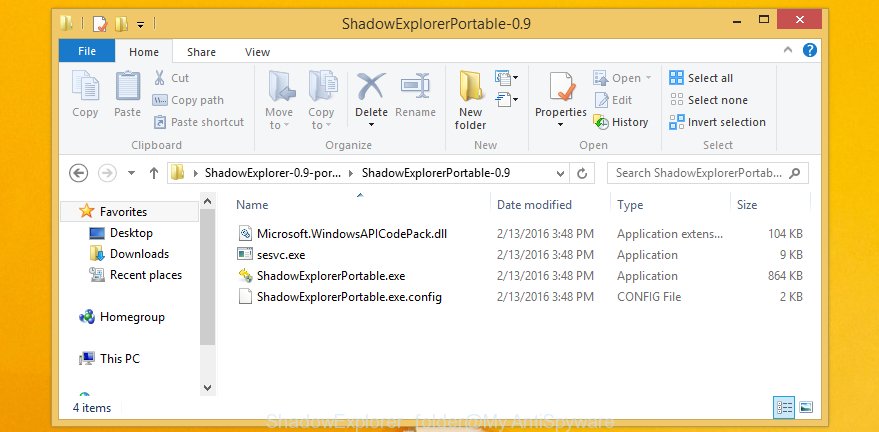
Run the ShadowExplorer utility and then select the disk (1) and the date (2) that you wish to restore the shadow copy of file(s) encrypted by the Mpal ransomware virus as on the image below.
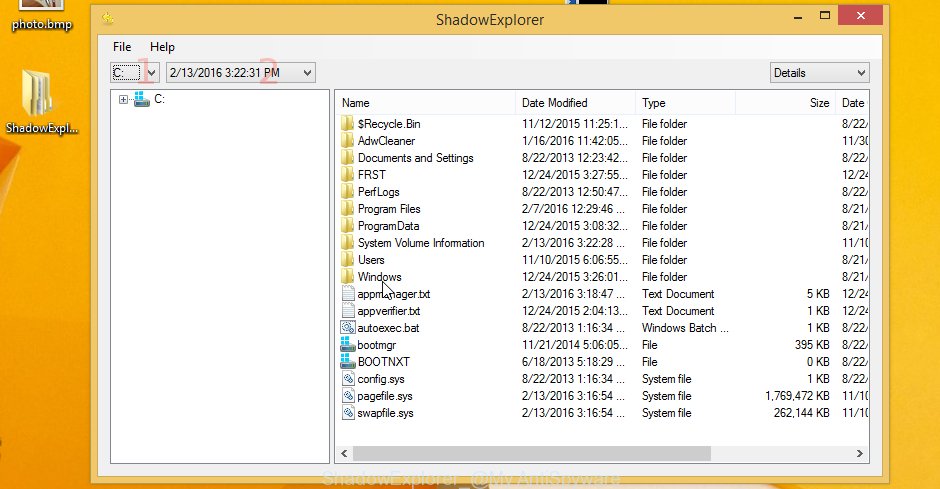
Now navigate to the file or folder that you want to restore. When ready right-click on it and click ‘Export’ button as shown below.

This video step-by-step guide will demonstrate How to recover encrypted files using Shadow Explorer.
Run PhotoRec to recover .mpal files
Another alternative way to recover encrypted files is to use data recovery tools. We recommend using a program called PhotoRec. This tool is free and does not require installation. Below we will show in detail how to use it to restore encrypted files.
Download PhotoRec on your Microsoft Windows Desktop by clicking on the following link.
After the download is finished, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as shown below.

Double click on qphotorec_win to run PhotoRec for MS Windows. It’ll display a screen as shown in the figure below.
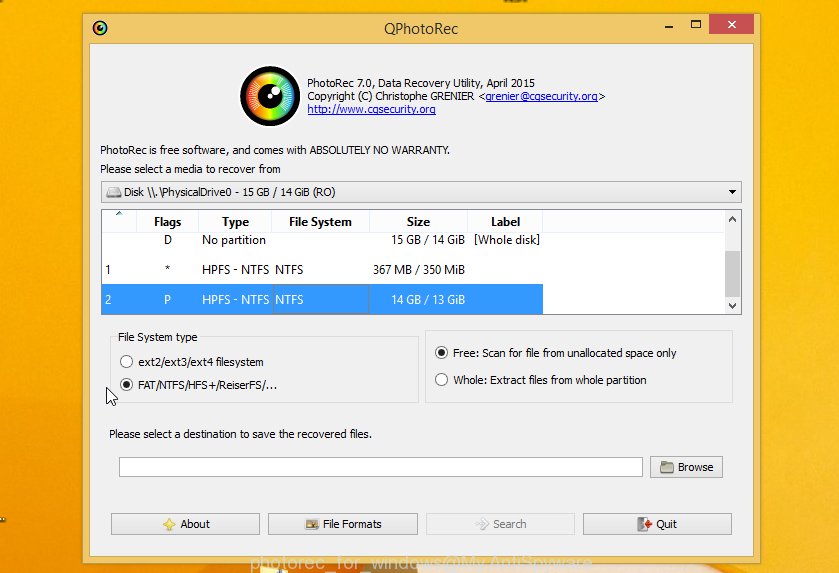
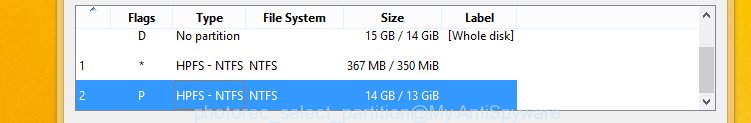
Select a drive to recover as displayed on the screen below.
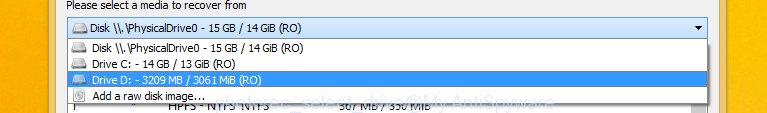
You will see a list of available partitions. Select a partition that holds encrypted photos, documents and music like the one below. Added: The Windows OS (10, 8, 7 , Vista) has one very useful feature, it makes copies of all f
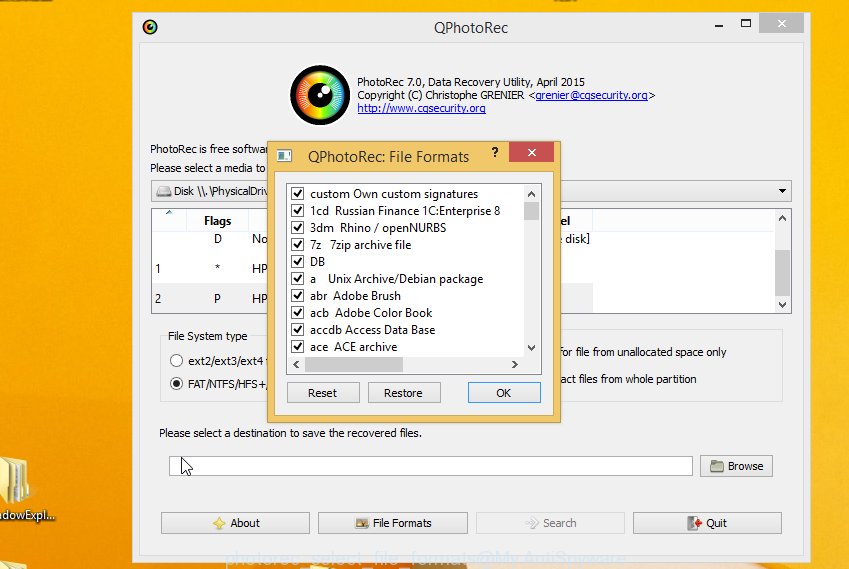
Press File Formats button and choose file types to restore. You can to enable or disable the restore of certain file types. When this is finished, click OK button.
Next, click Browse button to choose where restored personal files should be written, then click Search.
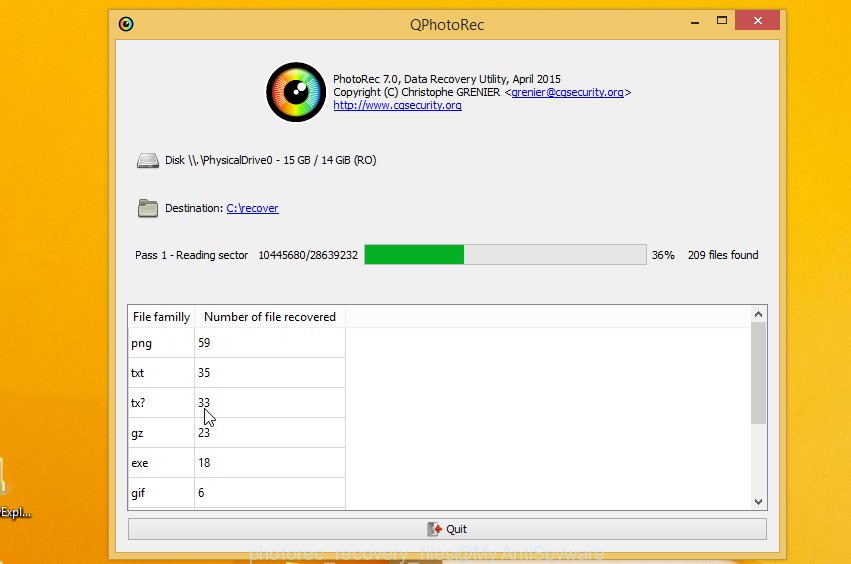
Count of recovered files is updated in real time. All restored files are written in a folder that you have selected on the previous step. You can to access the files even if the recovery process is not finished.
When the restore is complete, click on Quit button. Next, open the directory where restored files are stored. You will see a contents as on the image below.
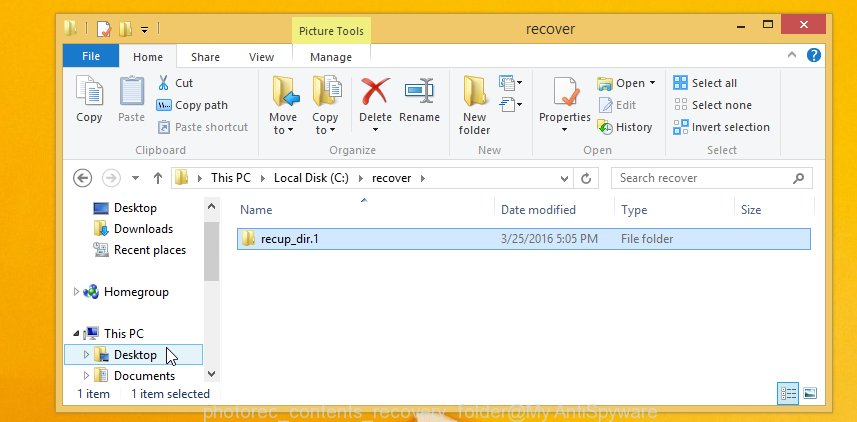
All recovered documents, photos and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you are searching for a specific file, then you can to sort your restored files by extension and/or date/time.
This video step-by-step guide will demonstrate How to recover encrypted files using PhotoRec.
How to protect your system from Mpal ransomware
Most antivirus programs already have built-in protection system against the ransomware virus. Therefore, if your PC system does not have an antivirus application, make sure you install it. As an extra protection, use the HitmanPro.Alert. All-in-all, HitmanPro.Alert is a fantastic utility to protect your PC system from any ransomware. If ransomware is detected, then HitmanPro.Alert automatically neutralizes malware and restores the encrypted files. HitmanPro.Alert is compatible with all versions of Windows operating system from Microsoft Windows XP to Windows 10.
Visit the page linked below to download the latest version of HitmanPro.Alert for Microsoft Windows. Save it on your Microsoft Windows desktop.
Once the download is complete, open the file location. You will see an icon like below.

Double click the HitmanPro.Alert desktop icon. Once the tool is started, you will be shown a window where you can choose a level of protection, as shown in the figure below.
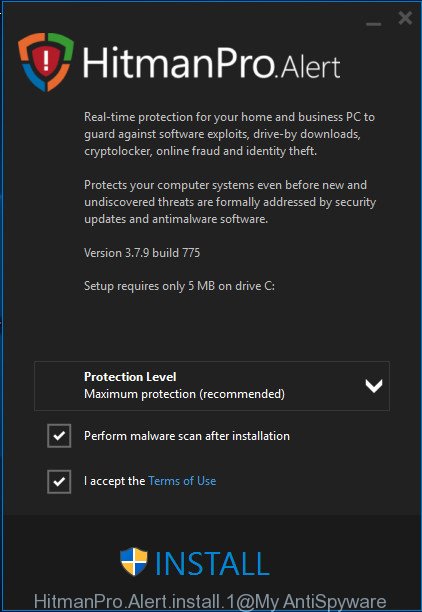
Now click the Install button to activate the protection.
To sum up
This guide was created to help all victims of Mpal ransomware virus. We tried to give answers to the following questions: how to remove ransomware; how to decrypt .mpal files; how to recover files, if Mpal File Decrypt Tool does not help; what is an online key and what is an offline key. We hope that the information presented in this manual has helped you.
If you have questions, then write to us, leaving a comment below. If you need more help with Mpal ransomware related issues, go to here.

















If you say that decrypt tool does not repair the files with online keys, who can find the systemID? In which program or application would we use it?
You can determine the type of key, just follow the instructions above. If the files are encrypted with an online key, then they cannot be decrypted. If the files are encrypted with an offline key, they can be decrypted. But the offline key has not yet been determined by security researchers, so you need to wait.
hey my system is infected with MPAL files but even using emsisoft decryption the files arent getting decrypted.
can you help with that?
what to do n how to recover the encrypted file.