What is Arrow file
.Arrow is a file extension that is used by the Arrow ransomware belonging to the Crysis/Dharma family to mark files that have been encrypted. Arrow ransomware is a malicious program that encrypts user files and demands a ransom for a key-decryptor pair that is necessary to decrypt the affected files. It uses a strong encryption system and a long key, which virtually eliminates the possibility of decrypting files without a key. Files encrypted with .Arrow extension become useless, their contents cannot be read without the key that the criminals have.
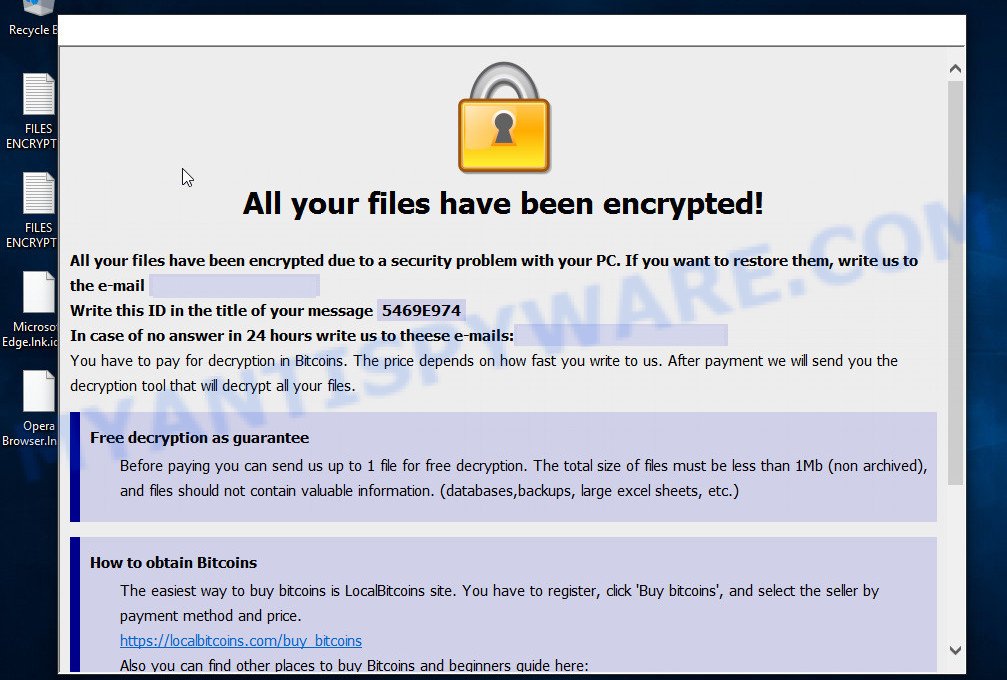
Text presented in the Arrow ransomware pop-up:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail biashabtc@redchan.it
Write this ID in the title of your message XXXXXXX
In case of no answer in 24 hours write us to theese e-mails:biashabtc@redchan.itYou have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
What is Arrow ransomware
Arrow ransomware is one of the variants of Dharma/Crysis ransomware. The most common source of infection is cracked apps and games, torrents files, freeware, Windows and Microsoft Office activators, and other similar software. Upon execution, it encrypts files using a key that is individual for each computer. Arrow uses a very strong encryption system, which eliminates the possibility of determining the key, even using a super computer. The encryption process is very fast, regardless of what is in the file, the virus can easily encrypt it. Arrow ransomware can encrypt almost all files that are on the computer, including those located on network drives. The only thing that the virus does not encrypt is the files that are necessary for the Windows OS to function normally. Below we list some types of files that can be encrypted by the ransomware:
.wire, .bc7, .wps, .zip, .fos, .dwg, .xmmap, .xbplate, .xx, .raw, .bay, .zw, .wpt, .rim, .sr2, .esm, .rofl, .xlsm, .rb, .bc6, .cfr, .mp4, .pfx, .zdc, .xlsb, .wot, .t12, .qdf, .bkf, .ncf, .wbz, .itm, .eps, .wmd, .bik, .zif, .xld, .wsc, .kf, .dba, .r3d, .hvpl, .itdb, .hplg, .desc, .wcf, .mdf, .ybk, .pptm, .nrw, .dmp, .bar, .1st, .sid, .png, .xxx, .vtf, .x, .xml, .wmv, .m3u, .ysp, .3fr, .pptx, .rwl, .pem, .dng, .rw2, .xyw, .wdp, .wb2, .jpeg, .xwp, .pef, .tor, .lrf, .y, .xdb, .xy3, .7z, .zabw, .xf, .vdf, .wp5, .raf, .wpd, .srf, .xlsx, .asset, .js, .docm, .ff, .wma, .sum, .x3f, .ibank, .wm, .iwd, .wdb, .x3d, .jpe, .wsh, .wp7, .3dm, .pst, .xls, .xls, .csv, .crw, .dazip, .dbf, .flv, .yal, .cdr, .cer, .wsd, .qic, .odb, .xlsm, .xdl, .z3d, .db0, .2bp, .ptx, .psd, .xmind, .xbdoc, .z, .odm, .wps, .wbm, .lbf, .xlk, .odt, .wpb, .docx, .indd, .wpl, .wav, .0, .wpg, .arw, .wpe, .wri, .dxg, .t13, .1, .tax, .doc, .yml, .avi, .xyp, .iwi, .map, .py, .wp4, .hkdb, .xlgc, .icxs, .erf, .syncdb, .wgz, .sie, .mdbackup, .wma, .forge, .itl, .gdb, .fpk, .ods, .fsh, .odp, .pkpass, .big, .bsa, .svg, .css, .p7c, .mddata, .bkp, .rtf, .mov, .kdc, .ztmp, .webp, .vfs0, .xar, .menu, .wbd, .orf, .zi, .accdb, .wotreplay, .x3f, .ntl, .wpd, .p12, .blob, .epk, .cas, .lvl, .wp6, .wmf, .psk, .3ds, .slm, .litemod, .vpp_pc, .der, .srw, .vpk, .sb, .jpg, .gho, .ai, .arch00, .ppt, .ltx
When a file is encrypted, ‘.id-USERID.[EMAIL-ADDRESS].Arrow’ is appended at the end of its name, that is, if you had a file of ‘document.docx’, then a file with the name ‘document.docx.id-USERID.[biashabtc@redchan.it].arrow’ will appear in its place. If you change the file name, just delete the added extension, then nothing will change. The file will remain encrypted, and as before, this file will not be possible to open in the program with which it is associated.
Perhaps you found on your computer or its desktop a new file called ‘FILES ENCRYPTED.txt’, which for some reason is not encrypted. An example of such a file is given below.
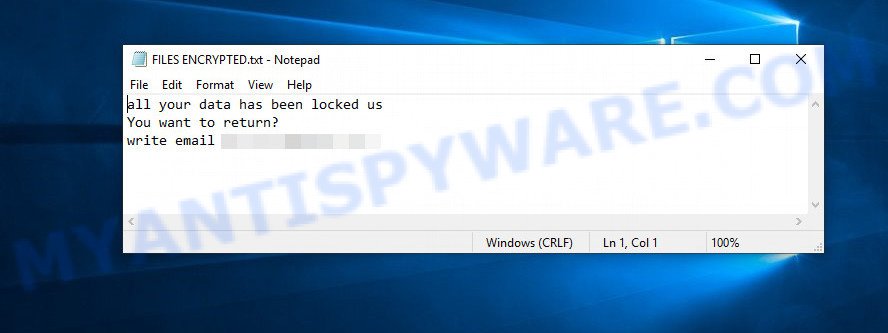
Text presented in the FILES ENCRYPTED.txt file:
all your data has been locked us
You want to return?
write email biashabtc@redchan.it
This file is very important, in addition to containing a ransom demand, it also contains information that allows you to contact intruders. According to the message, the victim is invited to contact the attackers using the given email address. In response, the authors of the virus will give a Bitcoin address to which the ransom must be transferred. Of course, you should understand that there is no guarantee that the attackers, after receiving the ransom, will provide you with the key necessary to decrypt your files. In addition, by paying the ransom, you will push attackers to create a new ransomware.
Threat Summary
| Name | Arrow ransomware |
| Type | Filecoder, File locker, Crypto virus, Ransomware, Crypto malware |
| Encrypted files extension | .arrow |
| Ransom note | FILES ENCRYPTED.txt |
| Contact | biashabtc@redchan.it |
| Ransom amount | $300-$1500 in Bitcoins |
| Detection Names | Trojan.Ransom.Crysis, Trojan/Win32.AGeneric, Trojan.Ransom.Crysis.E, Malicious.220e58, Trojan.Encoder.3953, A Variant Of Win32/Filecoder.Crysis.P, Ransom:Win32/Wadhrama!hoa, Ransom.Win32.CRYSIS.SM, Trojan-Ransom.Win32.Crusis.to |
| Symptoms | Encrypted personal files. Your personal files have odd extension appended at the end of the file name. Files called such as ‘FILES ENCRYPTED.txt’, ‘#_README_#’, ‘_DECRYPT_’ or ‘recover’ in each folder with at least one encrypted file.. ‘All files on your computer have been encrypted’ message on your desktop. |
| Distribution ways | Phishing Emails that is carefully created to trick a victim into opening an attachment or clicking on a link that contains a malicious file. Drive-by downloading (when a user unknowingly visits an infected website and then malicious software is installed without the user’s knowledge). Social media posts (they can be used to entice users to download malicious software with a built-in ransomware downloader or click a misleading link). Remote desktop protocol (RDP) hacking. |
| Removal | Arrow ransomware removal guide |
| Recovery | Arrow File Recovery |
As we have already said, Arrow is not the first ransomware belonging to the Crysis/Dharma family. The fact that to date, antivirus companies have not created a way to decrypt files, and just have not found a 100% way to protect the user’s computers, indicates the complexity of the ransomware and the method that it uses to encrypt files. Nevertheless, you do not need to despair. There are several ways to detect and remove Arrow ransomware, and there is also a chance to restore part or even all encrypted files to their original state. Below we will describe in detail how to do this.
How to remove Arrow ransomware, Restore .Arrow files
If your files have been encrypted with ‘.Arrow’ extension, then first of all you need to remove Arrow ransomware and be 100% sure that there is no active ransomware on your computer, and then proceed to restore the files. Both the ransomware removal process and the file recovery process will take a lot of time, so do not believe the magical instructions that say that this can be done very quickly. We definitely recommend, even if for some reason one of the methods proposed below did not suit you, try another one and try all of them. Perhaps one of them will help you. Feel free to ask questions in the special section on our website or in the comments below. And the last, before proceeding with the instructions, we advise you to read it thoroughly carefully, and then print or open it on a tablet or smartphone to have it always at hand.
- How to remove Arrow ransomware
- How to decrypt .arrow files
- How to restore .arrow files
- How to protect your computer from Arrow ransomware
How to remove Arrow ransomware
First you need to remove the Arrow ransomware autostart entries before decrypting and recovering encrypted files. Another option is to perform a full scan of the computer using antivirus software capable of detecting and removing ransomware infection.
It is very important to scan the computer for malware, as security researchers found that spyware could be installed on the infected computer along with the Arrow ransomware. Spyware is a very dangerous security threat as it is designed to steal the user’s personal information such as passwords, logins, contact details, etc. If you have any difficulty removing Arrow ransomware, then let us know in the comments, we will try to help you.
To remove Arrow ransomware, use the steps listed below:
Kill Arrow ransomware
Press CTRL, ALT, DEL keys together.
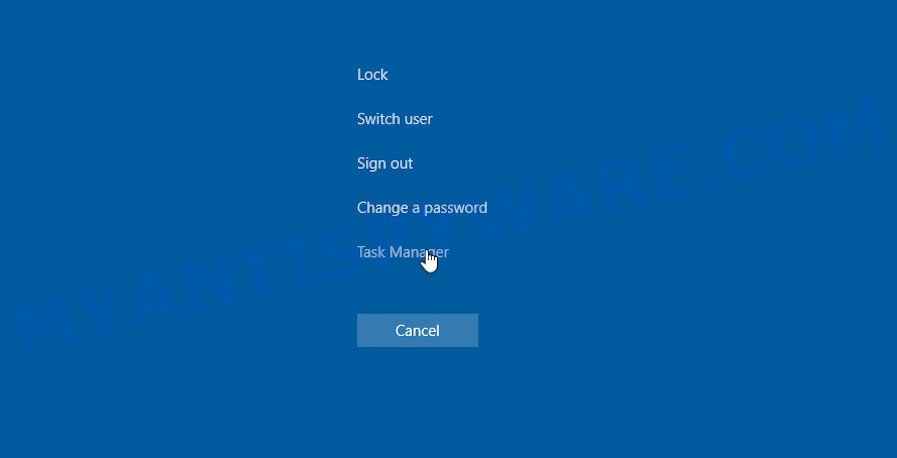
Click Task Manager. Select the “Processes” tab, look for something suspicious that is the Arrow ransomware then right-click it and select “End Task” or “End Process” option.
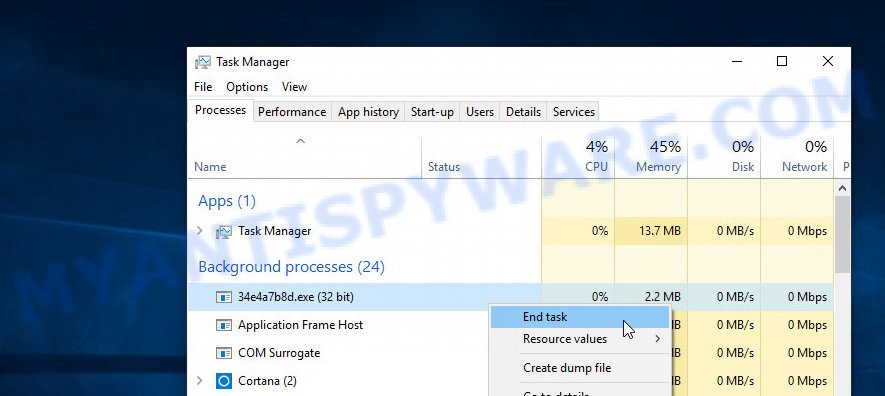
A process is particularly suspicious: it is taking up a lot of memory (despite the fact that you closed all of your programs, its name is not familiar to you (if you are in doubt, you can always check the program by doing a search for its name in Google, Yahoo or Bing).
Disable Arrow ransomware Start-Up
Select the “Start-Up” tab, look for something similar to the one shown in the example below, right click to it and select Disable.
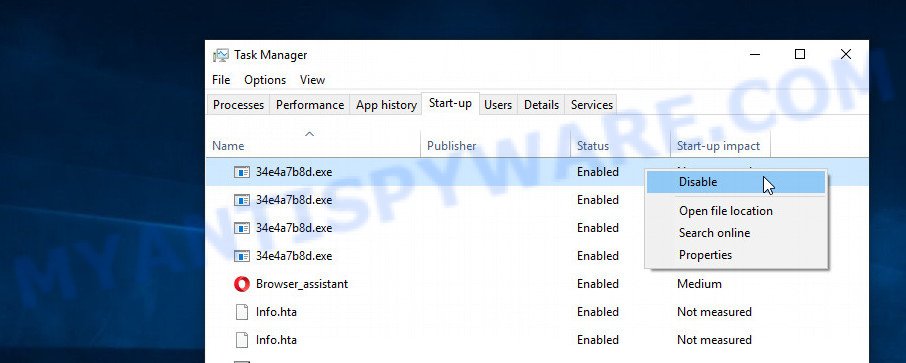
Close Task Manager.
Scan computer for malware
Zemana Anti Malware (ZAM) is a complete package of anti malware utilities that can help you delete Arrow ransomware. Despite so many features, it does not reduce the performance of your PC system. Zemana is able to remove almost all the types of ransomware including ransomware, trojans, worms, adware, browser hijackers, PUPs and other malicious software. ZAM has real-time protection that can defeat most malware and ransomware. You can run Zemana Free with any other antivirus without any conflicts.
Please go to the following link to download Zemana Anti Malware setup package named Zemana.AntiMalware.Setup on your computer. Save it on your MS Windows desktop.
164809 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
Start the installer after it has been downloaded successfully and then follow the prompts to setup this tool on your computer.
During setup you can change some settings, but we advise you do not make any changes to default settings.
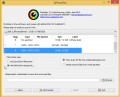
When installation is complete, this malicious software removal utility will automatically start and update itself. You will see its main window as on the image below.

Now click the “Scan” button . Zemana AntiMalware utility will begin scanning the whole machine to find out the Arrow ransomware related folders,files and registry keys. A scan can take anywhere from 10 to 30 minutes, depending on the number of files on your machine and the speed of your computer. While the Zemana AntiMalware is scanning, you can see number of objects it has identified either as being malicious software.

Once Zemana Anti-Malware (ZAM) completes the scan, a list of all threats detected is created. You may delete items (move to Quarantine) by simply click “Next” button.
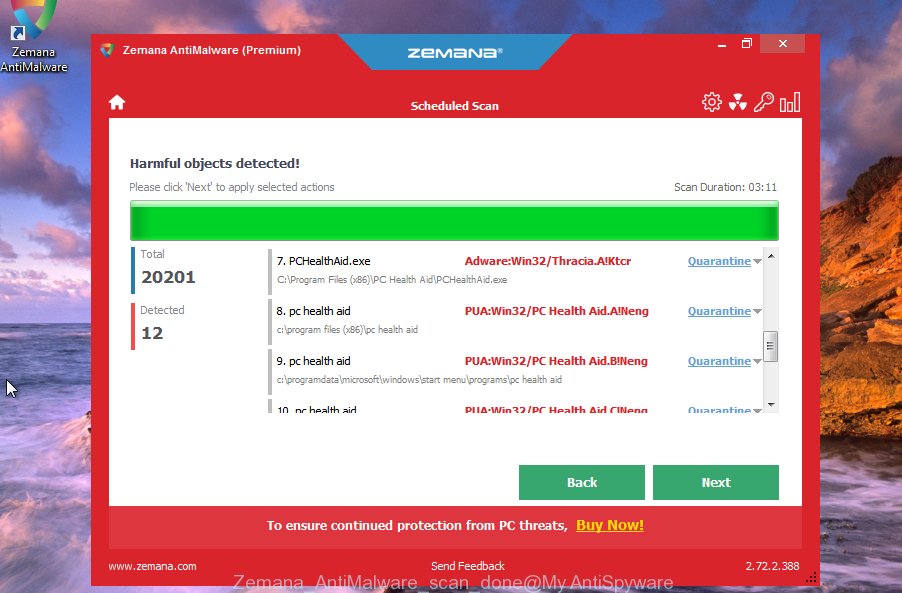
The Zemana AntiMalware (ZAM) will remove Arrow ransomware related folders,files and registry keys and move the selected threats to the Quarantine. After that process is complete, you can be prompted to reboot your PC to make the change take effect.
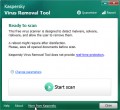
In order to be 100% sure that the computer no longer has the Arrow ransomware, we recommend using the Kaspersky virus removal tool (KVRT). It is a free portable program that scans your computer for spyware, ransomware, adware, potentially unwanted apps, trojans, worms, malicious software and helps remove them easily. Moreover, it will also help you delete any other security threats for free.
Download Kaspersky virus removal tool (KVRT) on your Microsoft Windows Desktop from the link below.
129232 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
Once downloading is finished, double-click on the KVRT icon. Once initialization process is finished, you’ll see the KVRT screen as shown in the following example.
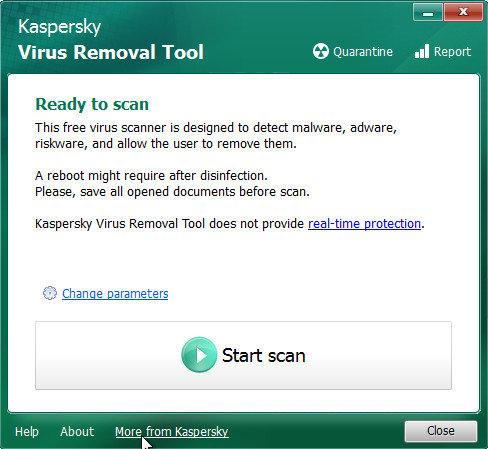
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next click Start scan button to start scanning your PC system for the Arrow crypto malware .
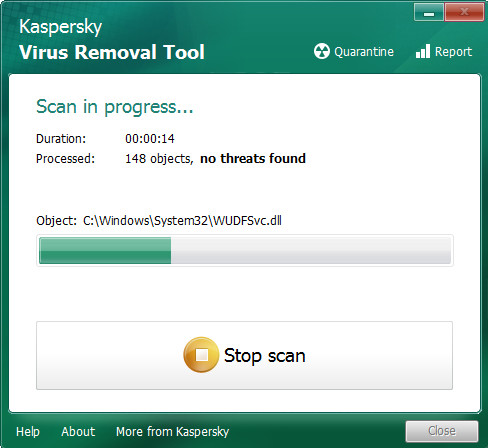
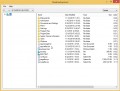
When KVRT completes the scan, KVRT will produce a list of unwanted software and ransomware virus like below.
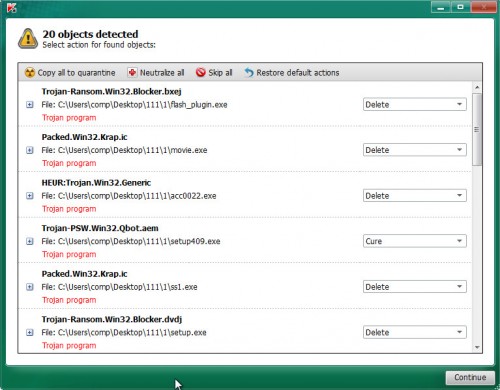
Review the results once the utility has finished the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply press on Continue to start a cleaning process.
How to decrypt .arrow files
All files with the ‘.arrow’ extension are encrypted. Their contents cannot be unlocked simply by removing this extension or completely changing the filename. Unfortunately, as we already reported in this article, there is currently no way to decrypt files. The reason for this is the complexity of the encryption algorithm that the authors of Arrow virus use. In principle, this is what the attackers sought. But this does not mean that you have no choice and you need to pay a ransom for your files.

Never pay the ransom! Every security expert will tell you this over and over. Of course, there is a chance that by paying a ransom, the Arrow virus authors will allow you to unlock your files, but there is no guarantee. Moreover, you should understand that when you pay a ransom, you unknowingly push the attackers to create new, even more destructive viruses.
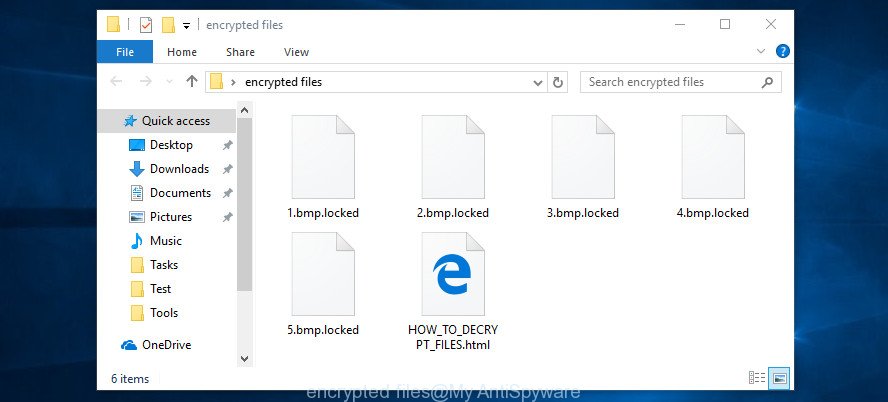
Do not forget that besides you, thousands more people around the world have lost their files, that is, you are not alone. Antivirus companies, security experts are working on something that will allow you to decrypt .Arrow files. Perhaps in the future an universal method will be developed that will allow all victims to unlock all their data.
Of course, as soon as a way to decrypt the files appears, we will post a message about this to this article or to our facebook account. Therefore, we recommend that you follow the updates.
How to restore .arrow files
As we wrote above, you cannot decrypt files encrypted with Arrow ransomware. But you can use a different way, there is a small chance to restore .Arrow files without decrypting them. Programs created for searching and recovering lost and deleted data can help you with this. We recommend you to use the following free programs: PhotoRec and ShadowExplorer. Two more things we want to say about. First, before restoring files, you must be 100% sure that there is no ransomware on the computer. We recommend using free malware removal tools that we examined in this article. Second, and what is very important! The less you use your computer after ransomware infection, the higher the chance that you will be able to recover encrypted files.
Recover .arrow files with ShadowExplorer
First of all, try to recover your files using a free tool called ShadowExplorer. This program will allow you to recover your files from Shadow Volume Copies. These copies are created automatically by the Windows OS when you work with your files. Unfortunately, very often, the virus automatically deletes all these copies and thus prevents the user from recovering encrypted files. Nevertheless, in some cases, the ransomware cannot delete all copies, and the user gets the opportunity to quickly restore all files. Therefore, our opinion, you should definitely try this method!
Visit the page linked below to download ShadowExplorer. Save it directly to your Windows Desktop.
439454 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
When the downloading process is finished, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as on the image below.
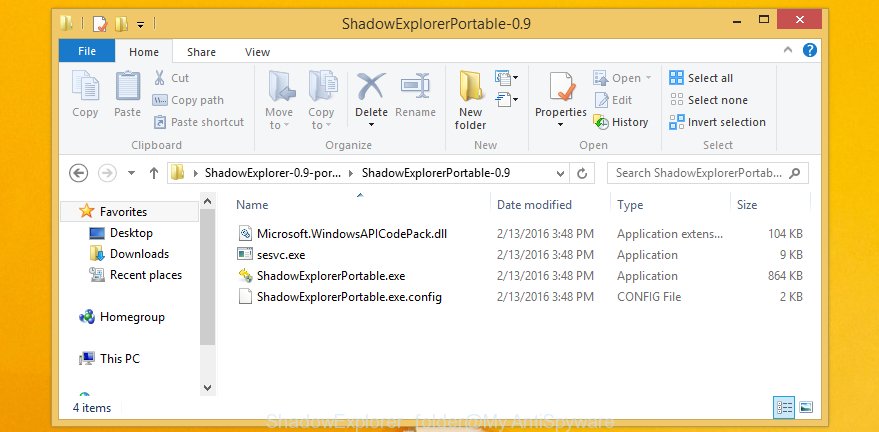
Double click ShadowExplorerPortable to launch it. You will see the a window as shown in the following example.
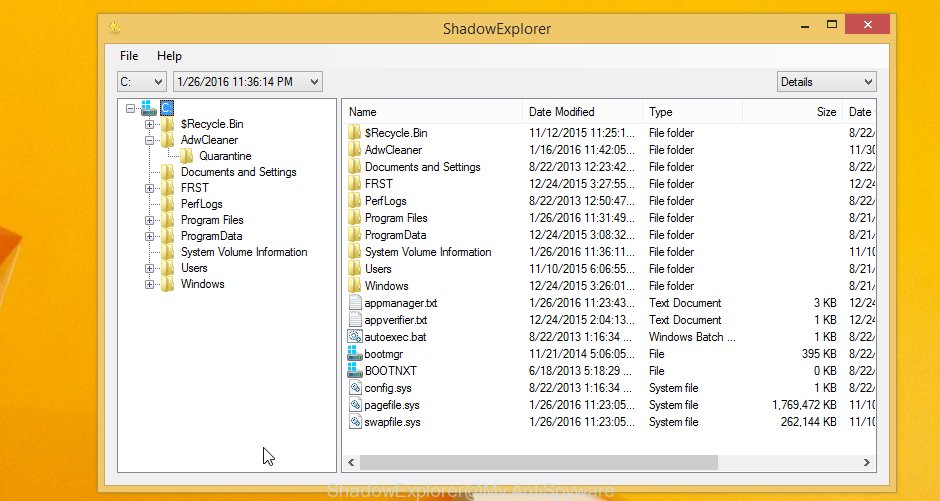
In top left corner, select a Drive where encrypted files are stored and a latest restore point similar to the one below (1 – drive, 2 – restore point).
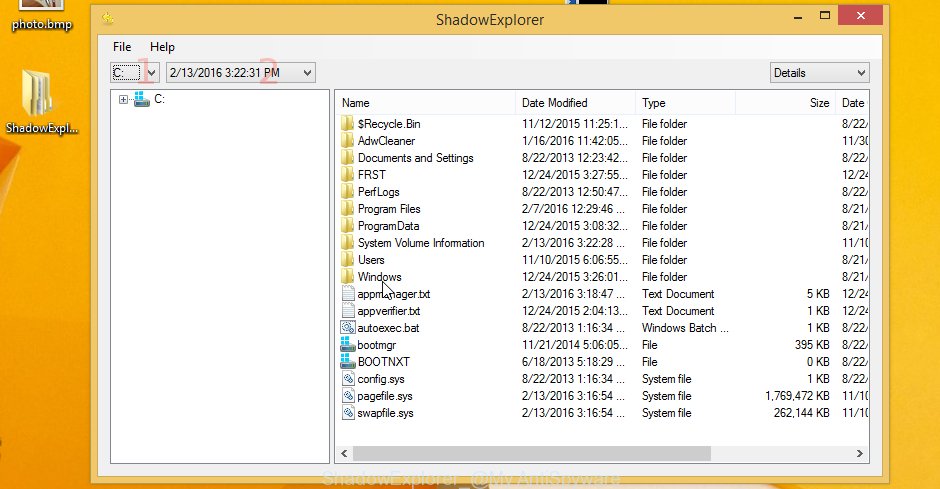
On right panel look for a file that you want to recover, right click to it and select Export similar to the one below.

This video step-by-step guide will demonstrate How to recover encrypted files using Shadow Explorer.
Use PhotoRec to restore .arrow files
Another really working way to recover your encrypted files is to use a program named PhotoRec. It is created to recover deleted or lost files. Does the Arrow ransomware block this method? Fortunately, the ransomware cannot block this method of recovering the contents of encrypted files. The more you used (moved, deleted, modified) files before infection, the greater the chance that you will be able to recover them.
Download PhotoRec by clicking on the link below.
Once the downloading process is done, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as displayed in the following example.

Double click on qphotorec_win to run PhotoRec for Microsoft Windows. It will display a screen as displayed on the image below.
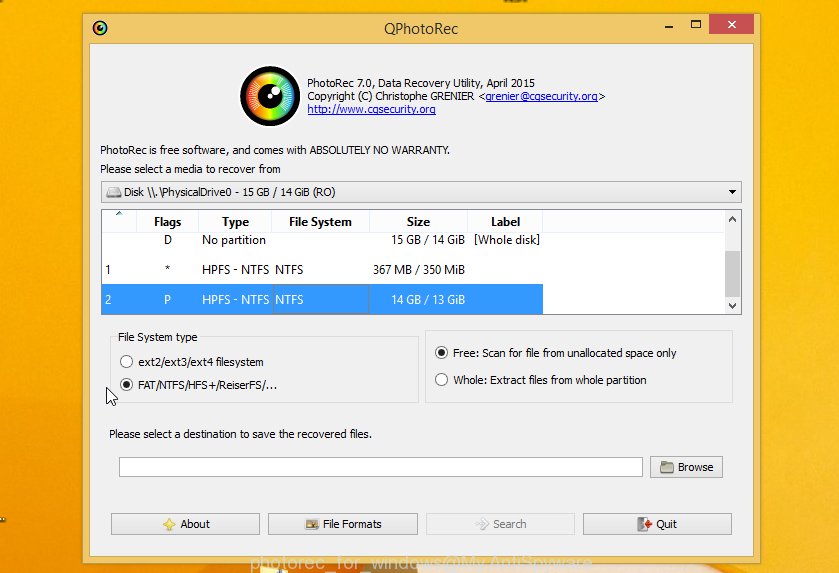
Select a drive to recover such as the one below.
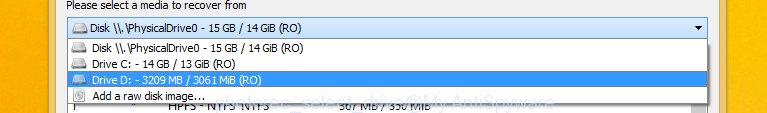
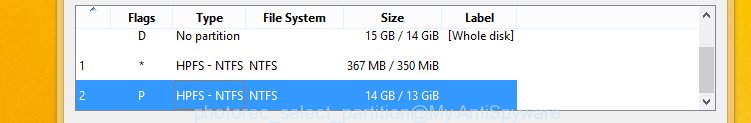
You will see a list of available partitions. Choose a partition that holds encrypted personal files as shown in the figure below.
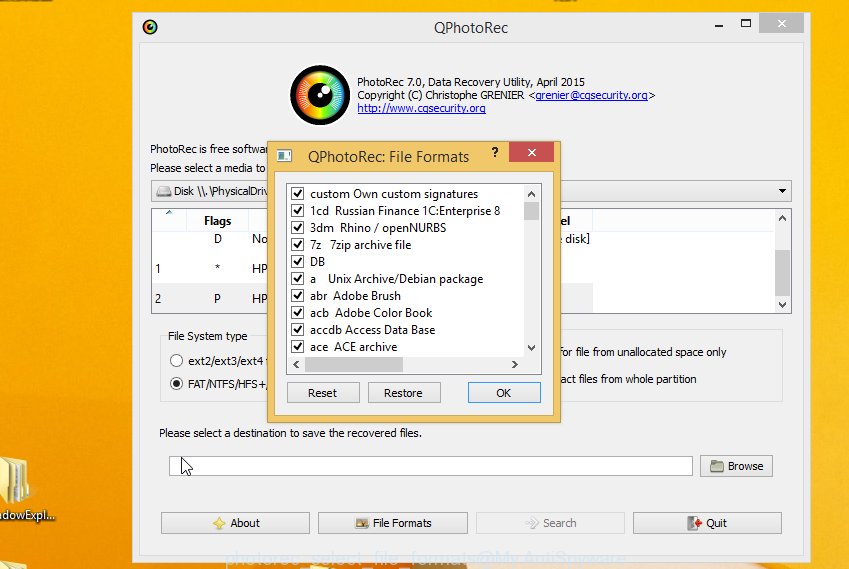
Click File Formats button and choose file types to recover. You can to enable or disable the restore of certain file types. When this is done, press OK button.
Next, press Browse button to choose where recovered files should be written, then click Search. We strongly recommend that you save the recovered files to an external drive.
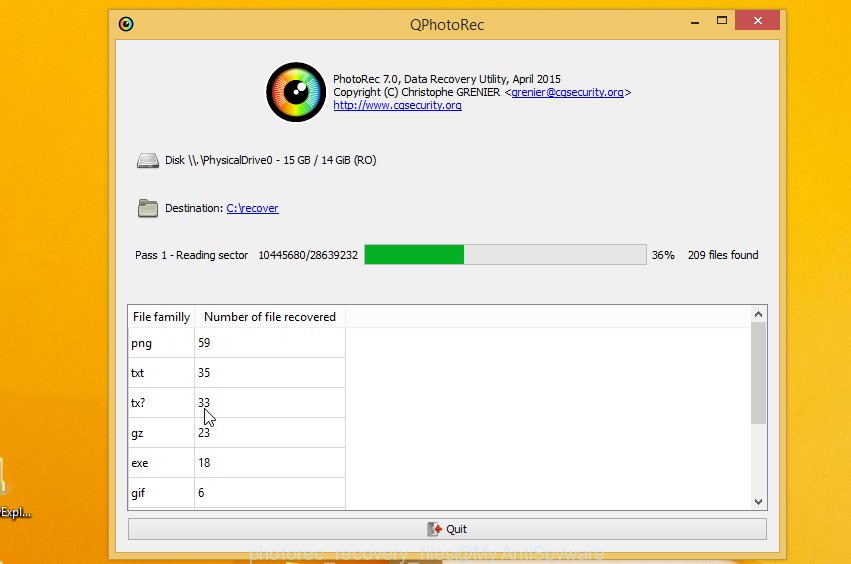
Count of recovered files is updated in real time. All recovered photos, documents and music are written in a folder that you have selected on the previous step. You can to access the files even if the restore process is not finished.
When the recovery is complete, press on Quit button. Next, open the directory where restored personal files are stored. You will see a contents as shown below.
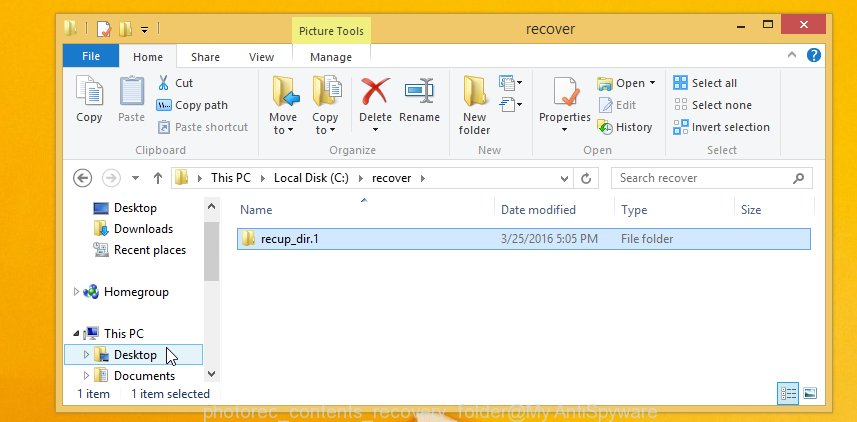
All restored documents, photos and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you are looking for a specific file, then you can to sort your recovered files by extension and/or date/time.
This video step-by-step guide will demonstrate How to recover encrypted files using PhotoRec.
How to protect your computer from Arrow ransomware
Most antivirus apps already have built-in protection system against the crypto virus. Therefore, if your computer does not have an antivirus program, make sure you install it. As an extra protection, run the HitmanPro.Alert. All-in-all, HitmanPro.Alert is a fantastic tool to protect your PC from any ransomware. If ransomware is detected, then HitmanPro.Alert automatically neutralizes malware and restores the encrypted files. HitmanPro.Alert is compatible with all versions of Microsoft Windows OS from Microsoft Windows XP to Windows 10.
Installing the HitmanPro.Alert is simple. First you will need to download HitmanPro.Alert from the following link. Save it to your Desktop.
Once the download is finished, open the file location. You will see an icon like below.

Double click the HitmanPro Alert desktop icon. After the tool is started, you’ll be displayed a window where you can select a level of protection, as displayed in the following example.

Now click the Install button to activate the protection.
To sum up
This guide was created to help all victims of the Arrow ransomware virus. We tried to give answers to the following questions: how to remove ransomware; how to recover .arrow files. We hope that the information presented in this manual has helped you.
If you have questions, then write to us, leaving a comment below. If you need more help with Arrow related issues, go to here.