Hey, some time ago your computer was infected with my private software is a new Bitcoin Email Scam that has been spreading on the Internet recently. Many people from all over the world have received such emails and reported about it on the Internet.
Hey, some time ago your computer was infected EMAIL SCAM
Scammers use threats to get a ransom from the recipients of such emails. Despite the fact that these email messages are very suspicious, and most people simply delete them, scammers hope that at least a few recipients will be naive enough and pay a ransom.
There are variations in the wording of the email body, but all of these messages are basically the same. Below is the most common variant of this scam.
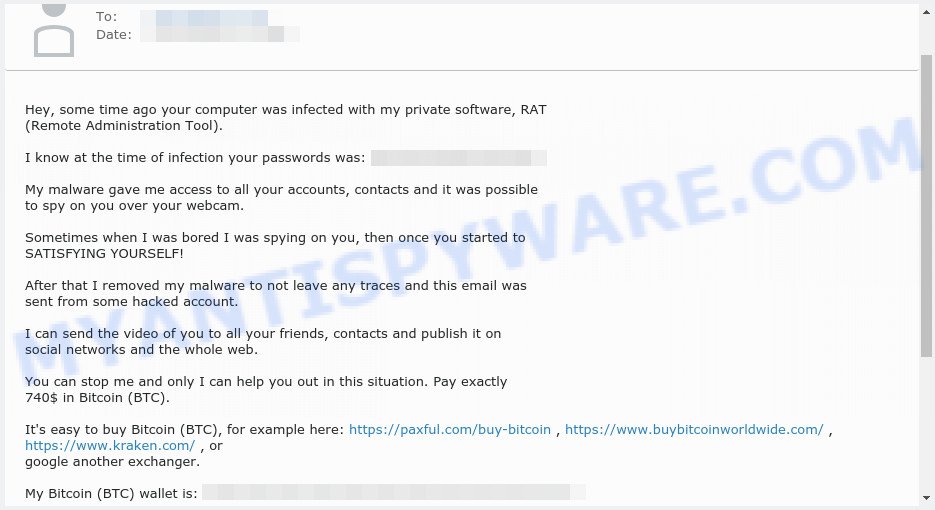
Hey, some time ago your computer was infected with my private software, RAT (Remote Administration Tool).
I know at the time of infection your passwords was: XXXXXXXXXXXXXXXXXXX
My malware gave me access to all your accounts, contacts and it was possible to spy on you over your webcam.
Sometimes when I was bored I was spying on you, then once you started to SATISFYING YOURSELF!
After that I removed my malware to not leave any traces and this email was sent from some hacked account.
I can send the video of you to all your friends, contacts and publish it on social networks and the whole web.
You can stop me and only I can help you out in this situation. Pay exactly 740$ in Bitcoin (BTC).
It’s easy to buy Bitcoin (BTC), for example here: https://paxful.com/buy-bitcoin , https://www.buybitcoinworldwide.com/ , https://www.kraken.com/ , or google another exchanger.
My Bitcoin (BTC) wallet is: ###################################
Yes that’s how the wallet looks like, copy and paste it, it’s (cAsE-sEnSEtiVE)
I give you 3 days time to pay.
As I got access to this email account, I will know if this email has already been read, so the time is running.
After receiving the payment, I will remove the video and you can life your live in peace like before.
Learn from the mistake and update your browser before browsing the web next time!
What is Bitcoin email scam
Bitcoin email scam is old extortion scheme – which try to guilt people into paying off someone claiming to have secretly recorded video or compromising information. Scammers uses the database of emails to sent this email scam out to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user database (email address and/or password) was indexed online.
Should you pay?
The best advice is: Don’t pay the ransom! If you receive the blackmail scam, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Name | Hey, some time ago your computer was infected with my private software SCAM |
| Type | Phishing, Bitcoin Email Scam, Fraud, Scam |
| Sender | Frank Black, Frank**@****.com |
| Ransom amount | $740 |
| Bitcoin Address | 12qyWVJL65VaKiUx1DFbCYckQcowXHGWs4 |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like Hey, some time ago your computer was infected with my private software, our computer security experts recommend follow some easy steps below |
What to do when you receive the Hey, some time ago your computer was infected with my private software SCAM
We advice to someone who gets this fraudulence message:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your PC for malware
Zemana is a malware removal utility designed for Microsoft Windows. This tool will help you various types of malicious software (including spyware, trojans, worms, hijackers and PUPs) from your computer. It has simple and user friendly interface. While the Zemana does its job, your computer will run smoothly.
First, please go to the following link, then click the ‘Download’ button in order to download the latest version of Zemana AntiMalware (ZAM).
164813 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
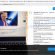
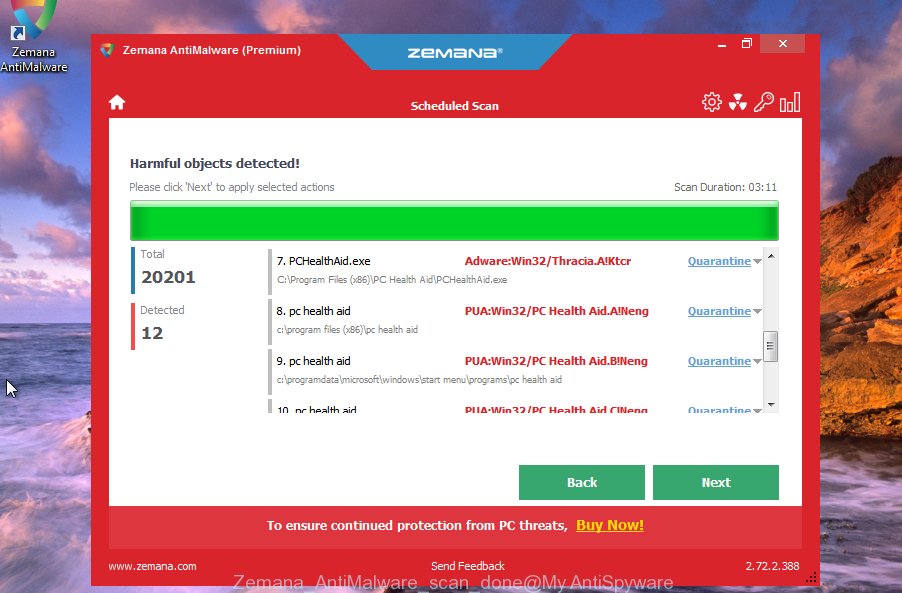
When the downloading process is done, launch it and follow the prompts. Once installed, the Zemana Anti-Malware will try to update itself and when this process is finished, click the “Scan” button to scan for malware.

When a threat is found, the count of the security threats will change accordingly. Wait until the the scanning is complete. Review the report and then click “Next” button.
If you are having issues with malware removal, then check out MalwareBytes. This tool is an advanced malware removal program developed by (c) Malwarebytes lab. This program uses the world’s most popular antimalware technology. It’s able to help you remove spyware, trojans, potentially unwanted apps, browser hijackers, toolbars, ransomware and other security threats from your PC for free.
Installing MalwareBytes is simple. First you’ll need to download MalwareBytes from the link below.
327070 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
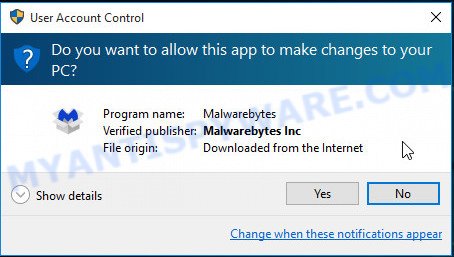
Once the download is complete, close all apps and windows on your computer. Double-click the install file named MBSetup. If the “User Account Control” prompt pops up as shown in the following example, click the “Yes” button.
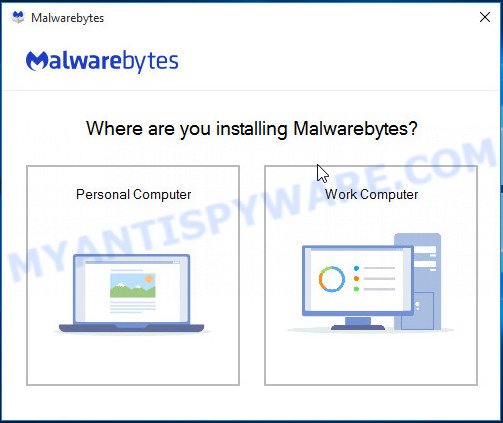
It will open the Setup wizard that will help you set up MalwareBytes Anti Malware on your PC. Follow the prompts and do not make any changes to default settings.
Once installation is complete successfully, click “Get Started” button. MalwareBytes Anti-Malware will automatically start and you can see its main screen as displayed on the screen below.
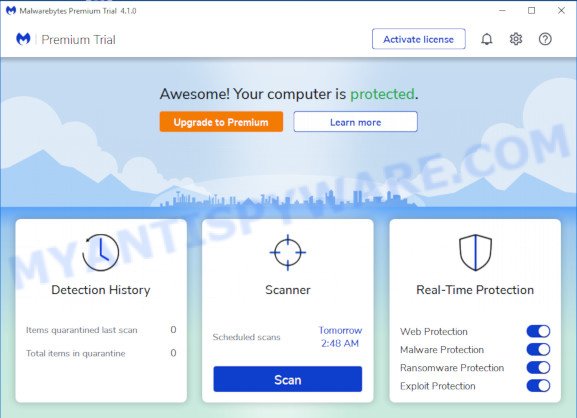
Now click the “Scan” button to search for malicious software. A system scan can take anywhere from 5 to 30 minutes, depending on your device. While MalwareBytes is scanning, you may see how many objects it has identified either as being malicious software.
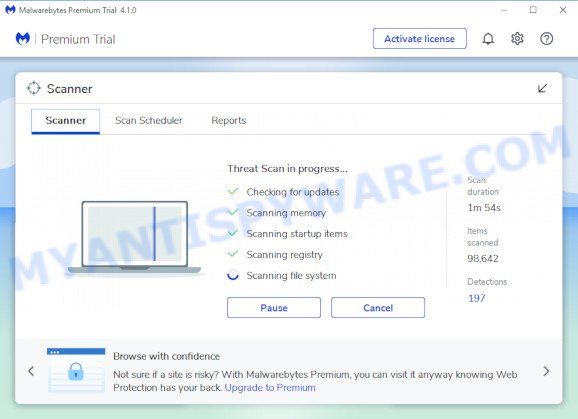
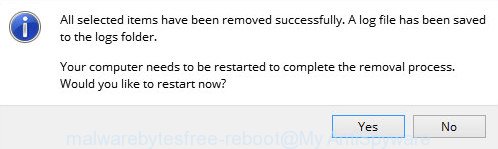
When the scan is complete, MalwareBytes Anti Malware will display you the results. When you’re ready, press “Quarantine” button. It will remove the found malware and move the selected threats to the Quarantine. Once the clean-up is finished, you may be prompted to reboot the personal computer.
We advise you look at the following video, which completely explains the process of using the MalwareBytes to remove adware, hijacker and other malware.
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing websites, then install an ad blocker program such as AdGuard. It can block malicious and misleading web sites, stop unwanted advertisements and popups when using the Internet Explorer, Google Chrome, Firefox and Edge. So, if you like surf the Internet, and want to protect your computer from malicious web pages, then the AdGuard is your best choice.
Installing the AdGuard is simple. First you’ll need to download AdGuard by clicking on the link below.
26842 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Finish words
We hope that this article helped you understand what the “Hey, some time ago your computer was infected with my private software” SCAM is and not succumb to the threats of scammers. If you receive an email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. It will help our team monitor the latest scams.