The device has been successfully hacked is a new ‘sextortion’ email scam. This email scam, like most sextortion scams, relies on “social engineering”, a process through which the scammers induce shame, panic or guilt. The scammers (the authors of the email) claim that they obtained material compromising the user (as a result of a computer hack, email account hack, router hack, etc) and threaten to publish it if the ransom is not paid. All these claims are not based on anything, they are just deception. Therefore, you can safely ignore this email, just delete it or move it to spam.
“The device has been successfully hacked” email message is a new scam
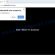
The “The device has been successfully hacked” email message says that someone successfully hacked the recipient’s device and monitored it for a long time. The hacker claims that this was made possible by a virus installed on the device when the user visited the adult site. Using this virus, the hacker was able to record a video that compromises the user, and also gained access to the user’s personal contacts, instant messengers and social networks. If the recipient pays $1200 in Bitcoin, the hacker promises to delete all the data. Next, the scam email contains the bitcoin address to which the ransom should be transferred. This email is just a sextortion scam, all statements are fake. Just ignore this email and other similar emails and emails containing similar content.
Text presented in the “The device has been successfully hacked” message:
Greetings.
I monitored your device on the net for a long time and successfully managed to hack it. It was not difficult for me, as I have been in this business for a long time.
When you visited a pornography site, I was able to put a virus on your computer that gave me full access to your device, namely your camera, microphone, phone calls, messengers, what happens on your screen, phone book, passwords to all social networks, etc. To hide my virus, I have written a special driver which is updated every 4 hours and makes it impossible to detect it.
I captured video of your screen and camera device and edited a video of you masturbating in one part of the screen and a pornographic video that you opened at that moment in the other part of the screen. I can safely send any data from your device to the Internet, as well as anyone who is recorded in your contacts, messengers and social networks. I can also give anyone access to your social networks, emails and messengers.
If you don’t want me to do it, then: Transfer $1200 (US dollars) to my Bitcoin wallet. My Bitcoin wallet address: bc1qnkxjyxtdjmr8tkwzfz2t3rc4scdmnr4ll99kg9
I give you 48 hours to transfer the money. Otherwise, I will perform the above. The timer started automatically as soon as you opened the email. I am also automatically notified when this email is opened.
If you do not know how to transfer money and what Bitcoin is. Then type “Buy Bitcoin” into Google As soon as I receive a transfer of the required amount, the system will automatically inform me about the received payment and offer to delete from my servers all the data I received from you. And therefore, I will confirm the deletion.
Do not try to complain anywhere, as a purse does not track, mail from where the letter came, and is not tracked and created automatically, so there is no point in writing to me. If you try to share this email with anyone, the system will automatically send a request to the servers and they will proceed to upload all the data to social networks.
QUICK LINKS
- What is The device has been successfully hacked EMAIL?
- What is Sextortion email scam?
- Should you pay?
- What to do when you receive the email scam?
- How to scan your PC for malware
- Updates
What is Sextortion email scam
Sextortion is the practice of extorting money from victims by blackmailing them; threatening to reveal evidence of their sexual activity. It is an old scam scheme – which try to guilt people into paying off someone claiming to have secretly recorded video or compromising information. Scammers use a database of stolen email to send out scam emails to to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user database (email address and/or password) was indexed online.
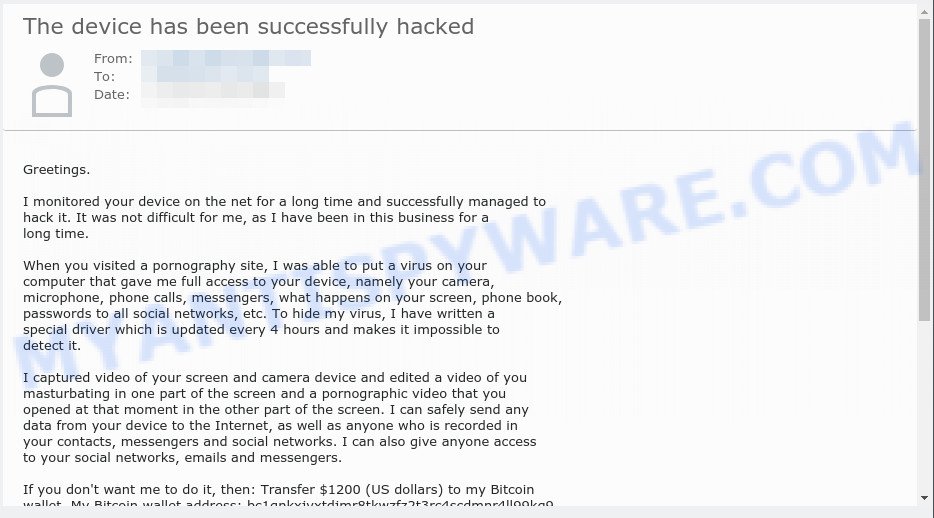
“Ich habe beobachtet Ihr Gerät im Netz seit langer Zeit” is a German version of the scam
Should you pay?
The best advice is: Don’t pay the ransom! If you receive the blackmail scam, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
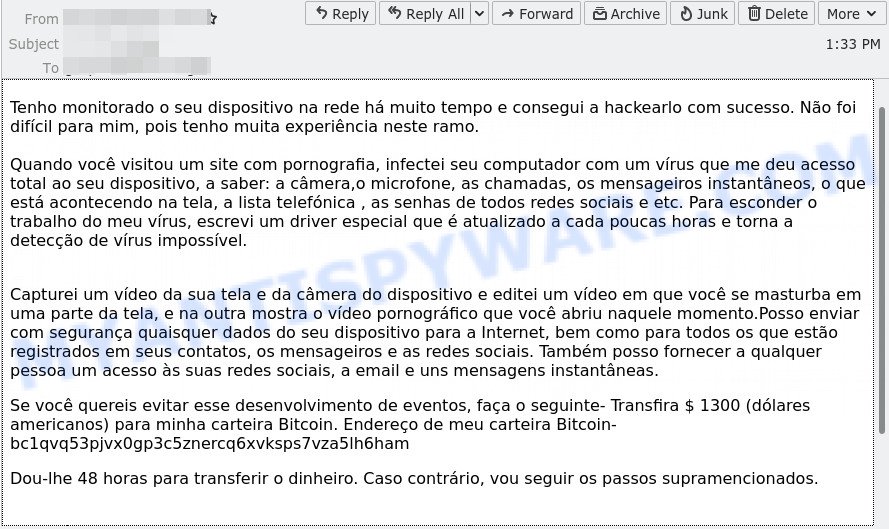
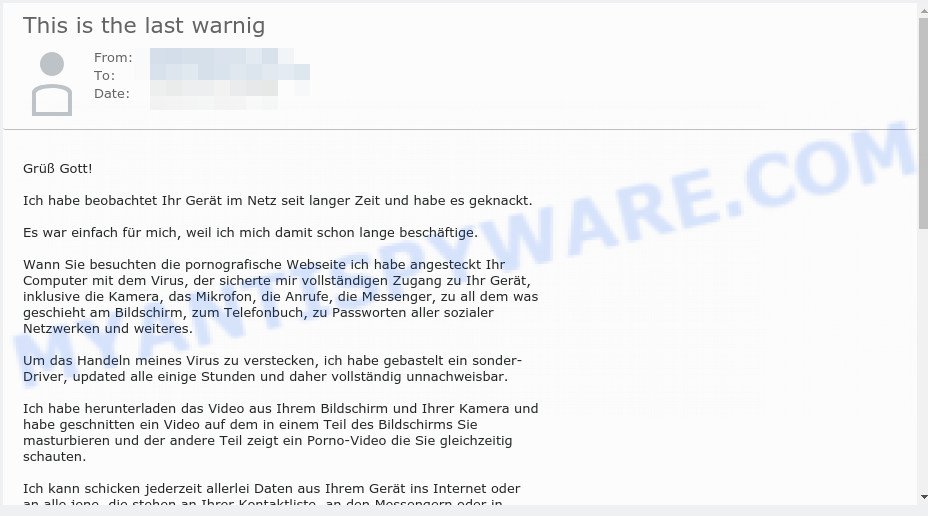
“Tenho monitorado o seu dispositivo na rede há muito tempo” is a Portuguese version of the scam
Threat Summary
| Name | The device has been successfully hacked SCAM |
| Type | Phishing, Bitcoin Email Scam, Fraud, Scam |
| Ransom amount | $1000, 160000 yen, $1200, $1300, $1400, $700 |
| Bitcoin Address | bc1q03ju8ke5snwx40rzndtns8nmpav7zejzqm8xl0, 12XpVk5cgxasf6eVtCMQ9AoMWPKUyvbLas, bc1qeuzke0t6cme84tzmrdepv00cafkznazwwxwx7j, bc1qq6u8zam54yzgc70nkm24d59vmgzjq579huy4dt, bc1q05pnnyz9gpy86nkdj8rnjuvv5dns9cy8e64a35, bc1qvq53pjvx0gp3c5znercq6xvksps7vza5lh6ham, bc1q5wjnyc239y5gnmlpj7sx9zys5ynhw5qz7a8kud, bc1q3dwsh4ryljth0yemny3wp6pe87dkheaxyg9q32, 1MuMwer8LsRzfbNUbTvQQjZRPFtLySkDyb, bc1qq5raukhfclywty4crngu0wqvdglfpfdmvxlse2, bc1qzg3ll6zfy8k9pxs20d35cffnzm8j8qdtygl9mp, bc1qpae26vlj5dnlxgwt2xjyw69sz3e596xs9xtwkn, bc1qnkxjyxtdjmr8tkwzfz2t3rc4scdmnr4ll99kg9 |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like The device has been successfully hacked, our computer security experts recommend follow some easy steps below |
What to do when you receive the The device has been successfully hacked SCAM
We advice to someone who gets this fraudulence message:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your PC for malware
Zemana is a malware removal utility designed for MS Windows. This utility will help you detect and remove various types of malicious software (including spyware, trojans, adware and potentially unwanted applications) from your PC system. It has simple and user friendly interface. While the Zemana Anti Malware does its job, your computer will run smoothly.
Zemana AntiMalware (ZAM) can be downloaded from the following link. Save it on your Windows desktop or in any other place.
165499 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
After the download is done, close all windows on your device. Further, start the setup file named Zemana.AntiMalware.Setup. If the “User Account Control” prompt pops up as displayed in the figure below, press the “Yes” button.
It will open the “Setup wizard” that will allow you install Zemana Free on the PC. Follow the prompts and do not make any changes to default settings.
Once setup is complete successfully, Zemana AntiMalware will automatically start and you may see its main window as shown below.

Next, click the “Scan” button for checking your computer for spyware, trojans, worms and other malicious software. This process can take some time, so please be patient. During the scan Zemana Anti Malware (ZAM) will scan for threats exist on your computer.

When Zemana completes the scan, Zemana Anti Malware (ZAM) will open a list of all items found by the scan. You may remove items (move to Quarantine) by simply press “Next” button.
The Zemana Free will delete malware and move the selected items to the program’s quarantine. After disinfection is finished, you can be prompted to reboot your PC system.
If you are having issues with malware removal, then check out MalwareBytes. We recommend this free malware removal utility because it may easily delete trojans, spyware, browser hijackers, adware, potentially unwanted software and toolbars with all their components such as files, folders and registry entries.
Visit the page linked below to download the latest version of MalwareBytes Anti-Malware for Windows. Save it on your Windows desktop or in any other place.
327717 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
Once the downloading process is complete, close all windows on your personal computer. Further, start the file called MBSetup. If the “User Account Control” prompt pops up as displayed on the image below, click the “Yes” button.
It will display the Setup wizard that will assist you install MalwareBytes Free on the computer. Follow the prompts and do not make any changes to default settings.
Once installation is done successfully, press “Get Started” button. Then MalwareBytes Anti-Malware (MBAM) will automatically start and you can see its main window as displayed in the figure below.
Next, click the “Scan” button to perform a system scan with this tool for malicious software. While the MalwareBytes Free utility is checking, you may see number of objects it has identified as being infected by malware.
When finished, MalwareBytes Anti Malware will open a screen which contains a list of malware that has been found. All detected threats will be marked. You can remove them all by simply press “Quarantine” button.
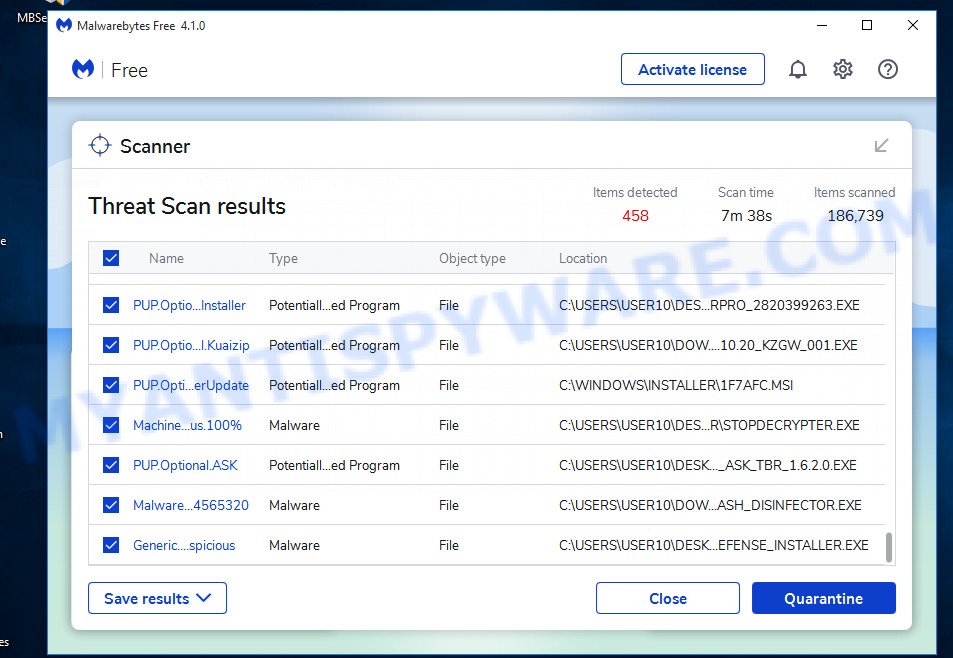
The MalwareBytes will remove malicious software. Once the process is finished, you can be prompted to restart your computer. We recommend you look at the following video, which completely explains the procedure of using the MalwareBytes to get rid of hijackers, adware and other malware.
We suggest you look at the following video, which completely explains the process of using the MalwareBytes Anti Malware to remove adware, browser hijacker and other malicious software.
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing websites, then install an ad blocker program such as AdGuard. It can block malicious and misleading web sites, stop unwanted advertisements and popups when using the Internet Explorer, Google Chrome, Firefox and Edge. So, if you like surf the Internet, and want to protect your computer from malicious web pages, then the AdGuard is your best choice.
Installing the AdGuard is simple. First you’ll need to download AdGuard by clicking on the link below.
27035 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Updates
Update, 30 March 2021. Discovered a new version of this scam aimed at Japanese users. Ransom amount: 160000 yen, Bitcoin wallet: 12XpVk5cgxasf6eVtCMQ9AoMWPKUyvbLas, 1LtJ7Ve3WaSBgQP1g6iponczo5QbRoeSGo.
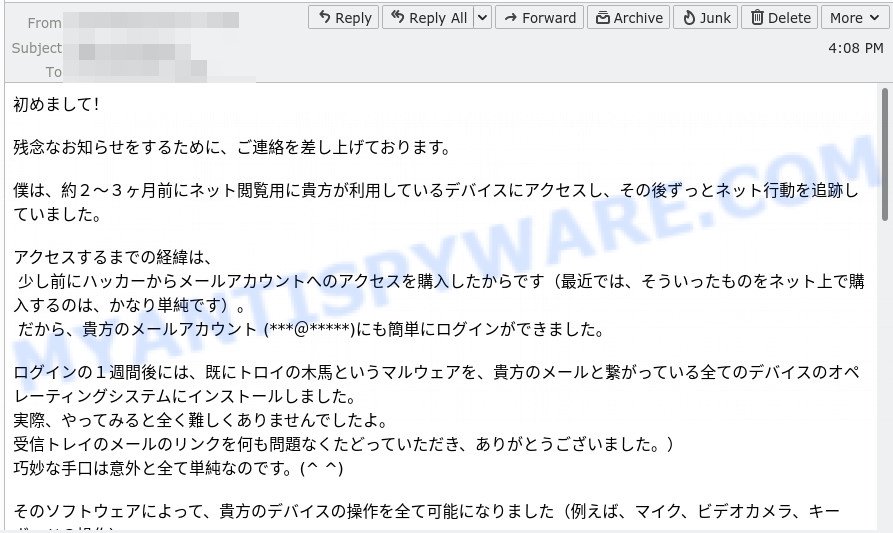
The device has been successfully hacked – Japanese version
Text presented in this scam email:
初めまして!
残念なお知らせをするために、ご連絡を差し上げております。
僕は、約2〜3ヶ月前にネット閲覧用に貴方が利用しているデバイスにアクセスし、その後ずっとネット行動を追跡していました。
アクセスするまでの経緯は、
少し前にハッカーからメールアカウントへのアクセスを購入したからです(最近では、そういったものをネット上で購入するのは、かなり単純です)。
だから、貴方のメールアカウント (***@*****)にも簡単にログインができました。ログインの1週間後には、既にトロイの木馬というマルウェアを、貴方のメールと繋がっている全てのデバイスのオペレーティングシステムにインストールしました。
実際、やってみると全く難しくありませんでしたよ。
受信トレイのメールのリンクを何も問題なくたどっていただき、ありがとうございました。)
巧妙な手口は意外と全て単純なのです。(^ ^)そのソフトウェアによって、貴方のデバイスの操作を全て可能になりました(例えば、マイク、ビデオカメラ、キーボードの操作)。
[…]
Update, 16 March 2021. Discovered a new version of this scam aimed at French users. Ransom amount: $1300, Bitcoin wallet: bc1qeuzke0t6cme84tzmrdepv00cafkznazwwxwx7j, bc1qq6u8zam54yzgc70nkm24d59vmgzjq579huy4dt.
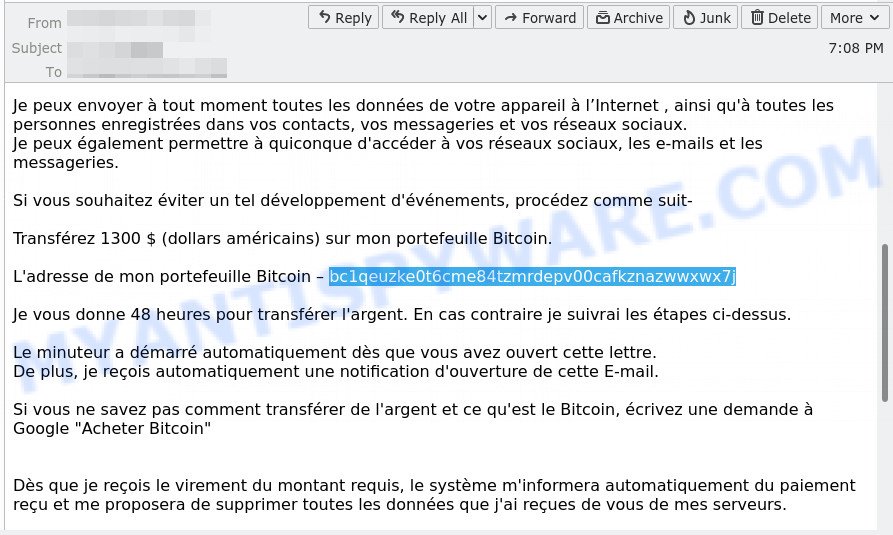
The device has been successfully hacked – French verison
Text presented in this scam email:
Bonjour.
J’ai surveillé votre appareil sur le réseau depuis longtemps et j’ai réussi à le pirater.
Cela n’a pas été difficile pour moi, puisque j’ai beaucoup d’expérience dans ce métier.Lorsque vous avez visité un site avec pornographie, j’ai pu infecter votre ordinateur avec un virus qui m’a donné un accès complet à votre appareil, à savoir: au camera,au microphone, aux appels, à la messagerie instantanée, à ce qui se passe sur l’écran, à l’annuaire, au mots de passe de tous réseaux sociaux etc.
…
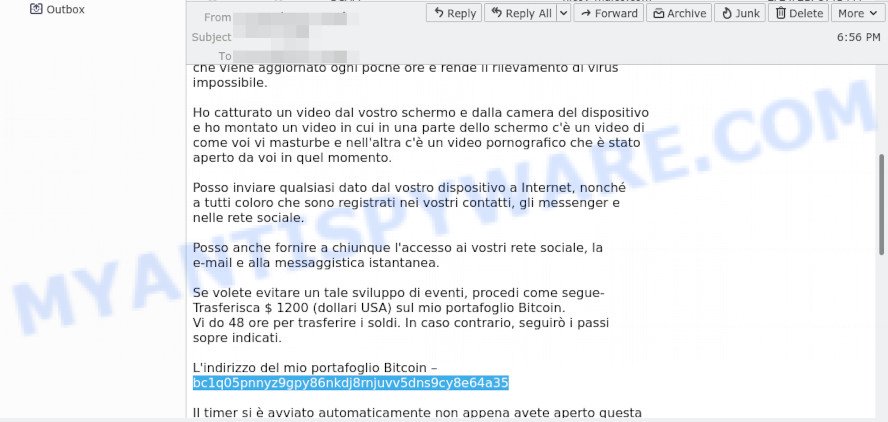
Update, 9 March 2021. Discovered a new version of this scam aimed at Italian users. Ransom amount: $1200, Bitcoin wallet: bc1q05pnnyz9gpy86nkdj8rnjuvv5dns9cy8e64a35.
Finish words
We hope that this article helped you understand what the “The device has been successfully hacked” SCAM is and not succumb to the threats of scammers. If you receive an email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. It will help our team monitor the latest scams.