What is You have an outstanding payment EMAIL?
You have an outstanding payment is a ‘sextortion’ scam that relies on psychological manipulation tactics. The scammers claim that they obtained material compromising victims’ reputations. It should be emphasized that any statements, claims and threats contained in the ‘sextortion’ scams are false and should be ignored. Criminals usually contact potential victims through email, but in some cases, criminals can use online web forms, whatsapp and sms messages.
The “You have an outstanding payment.” email is a SCAM
QUICK LINKS
- What is You have an outstanding payment SCAM?
- Should you pay?
- What to do when you receive the scam message?
The “You have an outstanding payment” email says that someone has been watching the recipient for the past couple of months. The sender claims that he was able to install a Trojan virus on the victim’s computer, which allowed him to take complete control of the computer and record a video in which the victim masturbates while browsing porn websites and watching dirty videos. The attacker threatens to send this video to the victim’s friends, relatives and even colleagues unless the victim pays the ransom to the bitcoin address provided in the message. As stated above, the email message is just a sextortion scam. All claims and threats made in this message are false. Therefore, recipients are not in danger, the message and similar messages can be safely ignored.
Typically, sextortion scams are sent via email, thousands at a time, and are part of larger spam campaigns. As with many other types of scams, scammers are evolving their methods to deliver their messages to potential victims. Such attacks can be personalized and sent out in smaller numbers to avoid detection. Scammers can use reputable services, change and personalize the content of each message, and avoid including links or attachments – all in an attempt to bypass security.
Text presented in the “You have an outstanding payment” message:
Hello there!
Unfortunately, there are some bad news for you.
Around several months ago I have obtained access to your devices that you were using to browse internet.
Subsequently, I have proceeded with tracking down internet activities of yours.Below, is the sequence of past events:
In the past, I have bought access from hackers to numerous email accounts (today, that is a very straightforward task that can be done online).
Clearly, I have effortlessly logged in to email account of yours (xxxxxxxx@xxxxxxx).A week after that, I have managed to install Trojan virus to Operating Systems of all your devices that are used for email access.
Actually, that was quite simple (because you were clicking the links in inbox emails).
All smart things are quite straightforward.The software of mine allows me to access to all controllers in your devices, such as video camera, microphone and keyboard.
I have managed to download all your personal data, as well as web browsing history and photos to my servers.
I can access all messengers of yours, as well as emails, social networks, contacts list and even chat history.
My virus unceasingly refreshes its signatures (since it is driver-based), and hereby stays invisible for your antivirus.So, by now you should already understand the reason why I remained unnoticed until this very moment…
While collecting your information, I have found out that you are also a huge fan of websites for adults.
You truly enjoy checking out porn websites and watching dirty videos, while having a lot of kinky fun.
I have recorded several kinky scenes of yours and montaged some videos, where you reach orgasms while passionately masturbating.If you still doubt my serious intentions, it only takes couple mouse clicks to share your videos with your friends, relatives and even colleagues.
It is also not a problem for me to allow those vids for access of public as well.
I truly believe, you would not want this to occur, understanding how special are the videos you love watching, (you are clearly aware of that) all that stuff can result in a real disaster for you.Let’s resolve it like this:
All you need is $1750 USD transfer to my account (bitcoin equivalent based on exchange rate during your transfer), and after the transaction is successful, I will proceed to delete all that kinky stuff without delay.
Afterwards, we can pretend that we have never met before. In addition, I assure you that all the harmful software will be deleted from all your devices. Be sure, I keep my promises.That is quite a fair deal with a low price, bearing in mind that I have spent a lot of effort to go through your profile and traffic for a long period.
If you are unaware how to buy and send bitcoins – it can be easily fixed by searching all related information online.Below is bitcoin wallet of mine: 12vuAcRSYDWuGHEVNVtQaEjBCBevps3ZcE
You are given not more than 48 hours after you have opened this email (2 days to be precise).
Below is the list of actions that you should not attempt doing:
> Do not attempt to reply my email (the email in your inbox was created by me together with return address).
> Do not attempt to call police or any other security services. Moreover, don’t even think to share this with friends of yours. Once I find that out (make no doubt about it, I can do that effortlessly, bearing in mind that I have full control over all your systems) – the video of yours will become available to public immediately.
> Do not attempt to search for me – there is completely no point in that. All cryptocurrency transactions remain anonymous at all times.
> Do not attempt reinstalling the OS on devices of yours or get rid of them. It is meaningless too, because all your videos are already available at remote servers.Below is the list of things you don’t need to be concerned about:
> That I will not receive the money you transferred.
– Don’t you worry, I can still track it, after the transaction is successfully completed, because I still monitor all your activities (trojan virus of mine includes a remote-control option, just like TeamViewer).
> That I still will make your videos available to public after your money transfer is complete.
– Believe me, it is meaningless for me to keep on making your life complicated. If I indeed wanted to make it happen, it would happen long time ago!Everything will be carried out based on fairness!
Before I forget…moving forward try not to get involved in this kind of situations anymore!
An advice from me – regularly change all the passwords to your accounts.
Should you pay?

The best advice is: Don’t pay the ransom! If you receive the sextortion email scam, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Name | You have an outstanding payment SCAM |
| Type | Phishing, Bitcoin Email Scam, Fraud, Scam |
| Ransom amount | $950, $1300, $1450, $1750 |
| Bitcoin Address | 15mSqySLsJ8MZqNQ7RfXiq54HGyt7uh3Cn, 12gHyoR78pjHpfueWUYyMudnwNMc6NGEPY, 1KXiY1reDCotVXpYdar6zoNknqGAsi1WeG, 1C2ek9b57xdVY9rPUaUnczxN5vGjVS8EhA, 12vuAcRSYDWuGHEVNVtQaEjBCBevps3ZcE |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like You have an outstanding payment, our computer security experts recommend follow some easy steps below |
There are many variations of the scam, scammers often change the text of messages in order to deceive victims and bypass security systems. In addition, in some cases, criminals can translate the text of sextortion messages into other languages, thus targeting a specific group of Internet users. Hi, I’m sorry but You’re going to have a bad day, Hello, I’m going to share important information with you, I have to share bad news with you are other examples of sextortion scams. Such messages are also often used to distribute ransomware, trojans, worms and other malware.
What to do when you receive the You have an outstanding payment SCAM
We advice to someone who gets this fraudulence message:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your computer for malware
If you suspect that your computer is infected with malware, you accidentally clicked on a link in the scam email, or just want to scan your computer, then use one of the best free malware removal tools. Zemana is extremely fast and ultra light weight malicious software removal tool. It will help you detect and remove adware, spyware, trojans, potentially unwanted programs and other malware. This program gives real-time protection that never slow down your device. Zemana Anti Malware is developed for experienced and beginner computer users. The interface of this tool is very easy to use, simple and minimalist.

- Visit the page linked below to download the latest version of Zemana for MS Windows. Save it on your desktop.
Zemana AntiMalware
164769 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- At the download page, click on the Download button. Your browser will show the “Save as” prompt. Please save it onto your Windows desktop.
- After the downloading process is complete, please close all apps and open windows on your PC system. Next, launch a file named Zemana.AntiMalware.Setup.
- This will start the “Setup wizard” of Zemana Anti Malware onto your computer. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, the Zemana AntiMalware will start and display the main window.
- Further, click the “Scan” button . Zemana will begin scanning the whole computer to detect malicious software. Depending on your personal computer, the scan can take anywhere from a few minutes to close to an hour. While the utility is scanning, you can see how many objects and files has already scanned.
- After Zemana Anti-Malware has completed scanning your computer, you will be displayed the list of all found items on your computer.
- Make sure to check mark the threats which are unsafe and then click the “Next” button. When finished, you may be prompted to reboot the computer.
- Close the Zemana Anti-Malware and continue with the next step.
If you are having issues with malware removal, then check out MalwareBytes. We recommend this free malware removal utility because it can easily remove trojans, spyware, browser hijackers, adware, potentially unwanted software and toolbars with all their components such as files, folders and registry entries. Visit the page linked below to download the latest version of MalwareBytes Anti-Malware for Windows.
327029 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
We suggest you look at the following video, which completely explains the process of using the MalwareBytes Anti Malware to remove malicious software.
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing websites, then install an ad blocker program such as AdGuard. It can block malicious and misleading web sites, stop unwanted advertisements and popups when using the Internet Explorer, Google Chrome, Firefox and Edge. So, if you like surf the Internet, and want to protect your computer from malicious web pages, then the AdGuard is your best choice.
Installing the AdGuard is simple. First you’ll need to download AdGuard by clicking on the link below.
26838 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
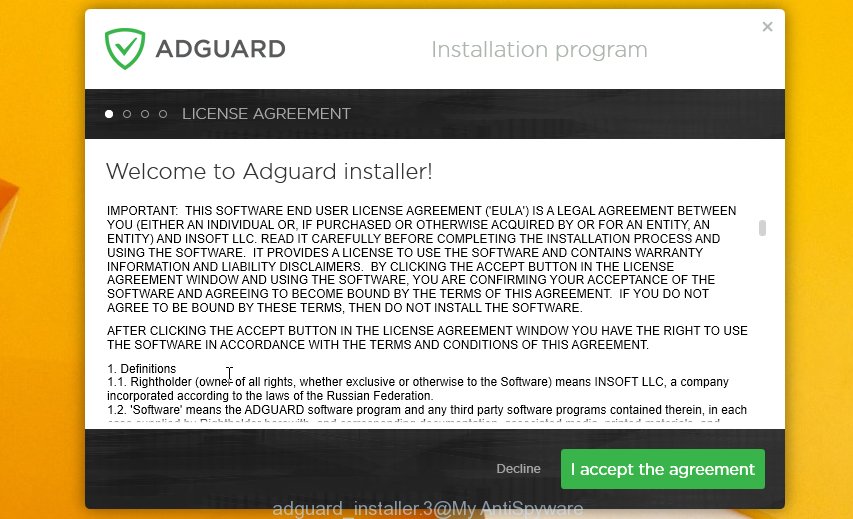
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Finish words
If you receive a scam message that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.










I’m feeling very important about receiving two of these scam emails is as many days… After deleting the first one, I decided to do a deep dive on the second, to find the source.
At first, (by reading the header information), I thought the email was sent from a domain server in South America… But, I did more digital digging and found a free online email trace route tool…
I plugged in the email header information and POOF! the program pointed the origin of the email to…
TA DA…! a sender IP Address: 212.188.16.187, on an unknown server in… (imagine this… of all places…) The Russian Federation, specifically – Moscow!
(The program returned a geo-location of, Lat. 55.752201080322 – Long. 37.615600585938…
Right in the middle of Red Square…
Dasvidaniya email scam!