What is Chromnius?
Chromnius is a potentially unwanted program that installs Chromium build browser to replace the user’s own browser. The goal of this PUP is to increase the amount of advertisement impressions shown to the user. PUPs that displays intrusive ads or injects its own advertising content called adware. Adware is a form of software designed to display unwanted advertisements to computer users. Some examples include pop-up ads, push notifications or unclosable windows. Clicks on the advertisements produce a monetary payoff for the adware creators. Some adware can be used for spying, data collection and monitoring that can be extremely harmful to victims.
Typically, adware can infect a personal computer in many ways, the most common of which involves downloading infected files as well as hacked software, freeware, Windows/Office key generators and other similar software.
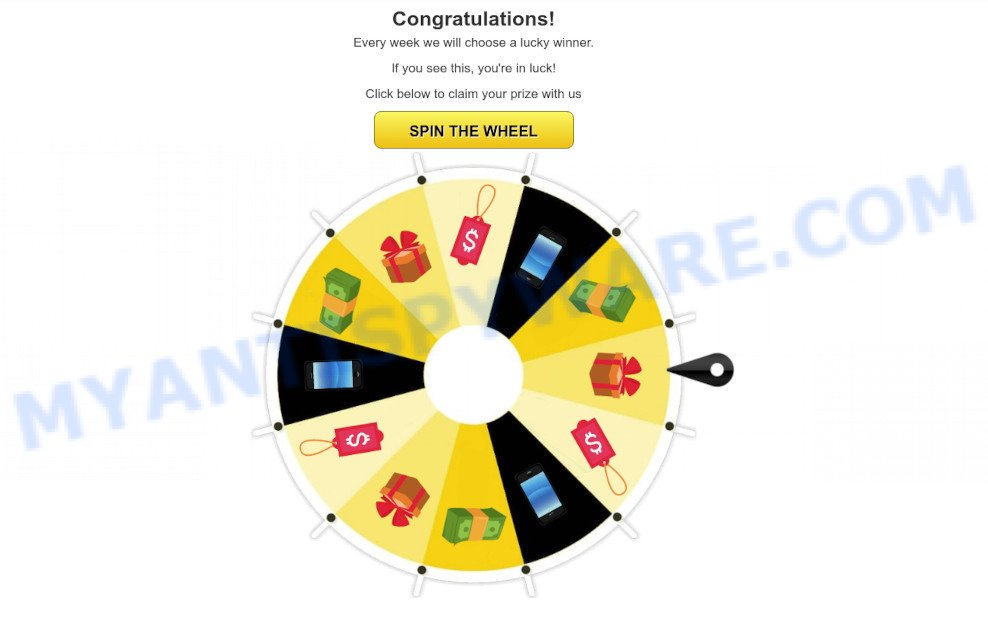
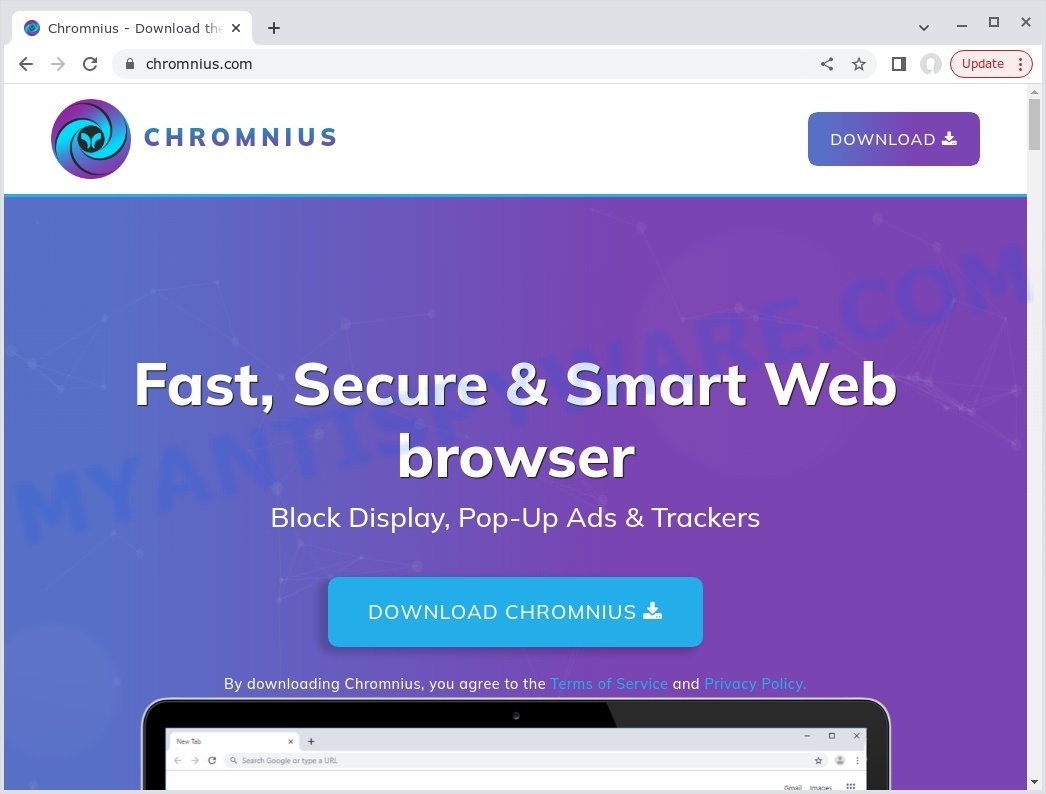
Chromnius install pop-up:
QUICK LINKS
Chromnius.exe adware in detail
Chromnius adware is based on the Chromium technology platform. It can display banner ads, full-screen advertisements, pop ups, videos, or other varieties of online advertising. Maybe you approve the idea that the ads or pop-ups are just a small problem. But these unwanted advertisements eat computer resources and slow down your web-browser performance.
Chromnius uses its own website as search engine. This means that users who use it as a web browser are forced to visit this website each time they search in the Internet, open a new window or tab. And since this website is not a real search provider and does not have the ability to find the information users need, it redirects the user’s web browser to Google, Bing or Yahoo search engine. The devs behind Chromnius are most probably doing this to generate advertisement money from the ads shown in the search results.
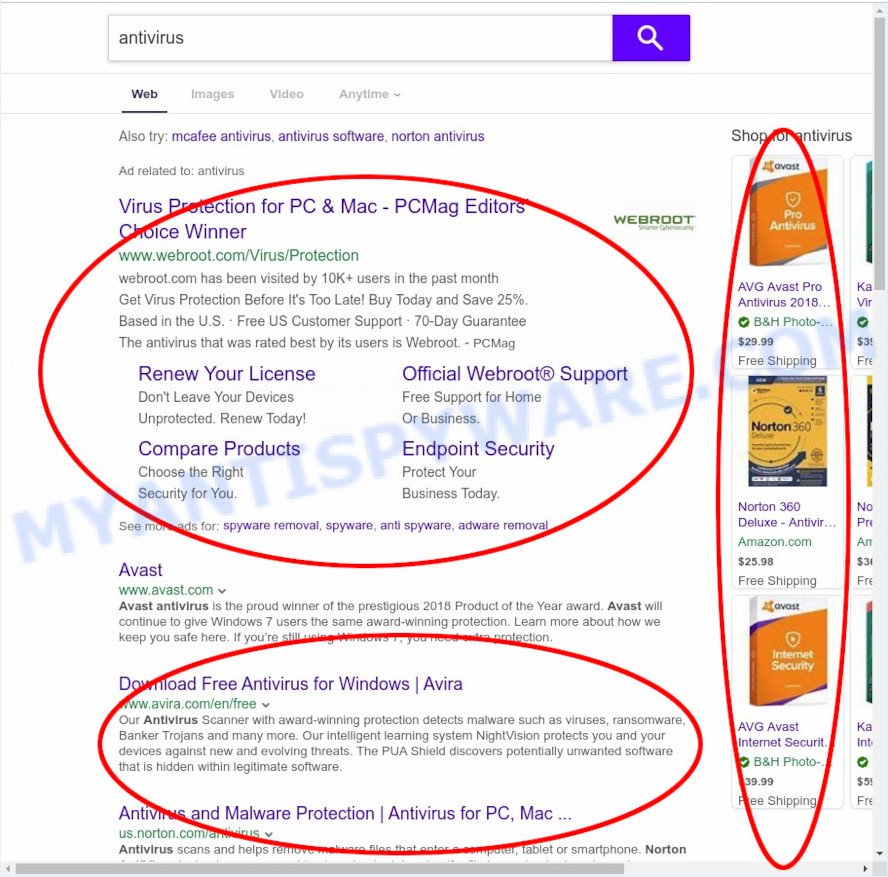
Unwanted search ads
Is Chromnius safe?
Like other adware of that kind, Chromnius is able to monitor and report on your activity and provide information to a third party. Adware can install a component (spyware) that enables its creators to track which web pages you visit, what products you look at upon those pages. They are then choose the type of ads they show you. So, if you have adware installed on your personal computer, there is a good chance that you have another that collects and shares your sensitive information with third parties without your consent.
Attackers often use adware to redirect users to malicious and scam websites. Below are some examples of such sites:
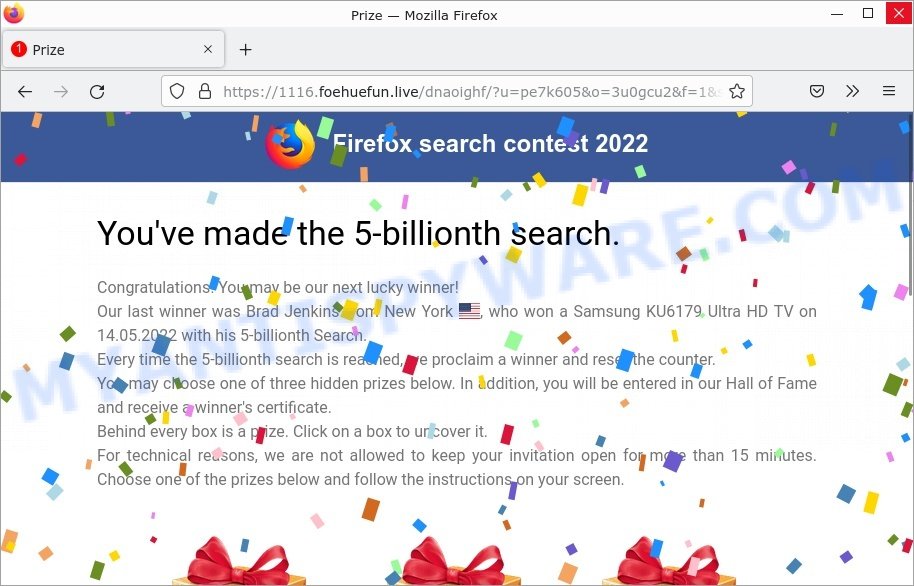
- Mostwinhere.life Search Contest Scam
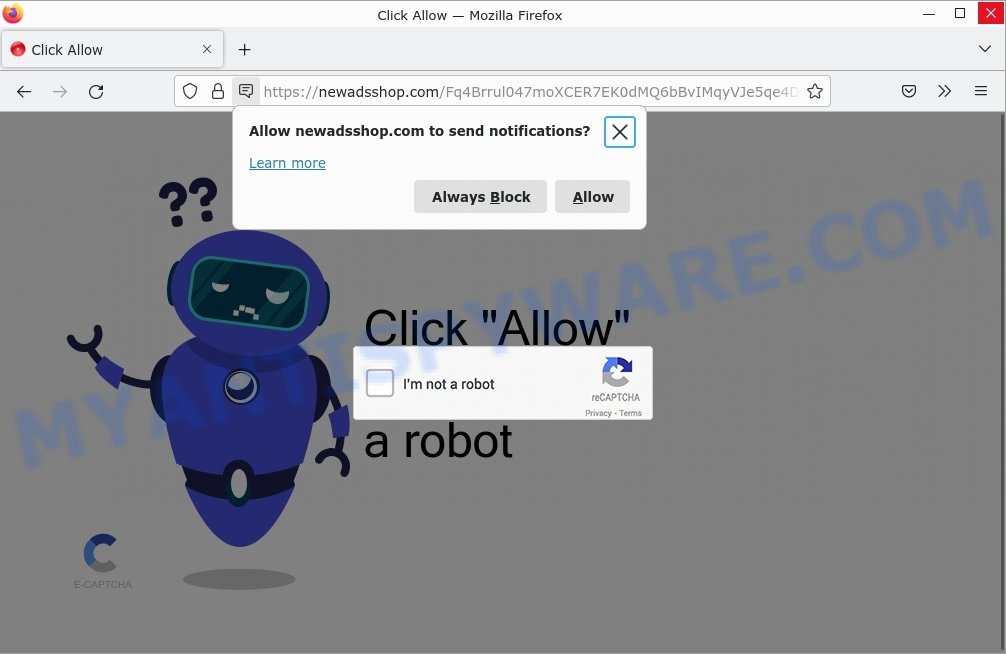
- Newadsshop.com Click Allow Scam
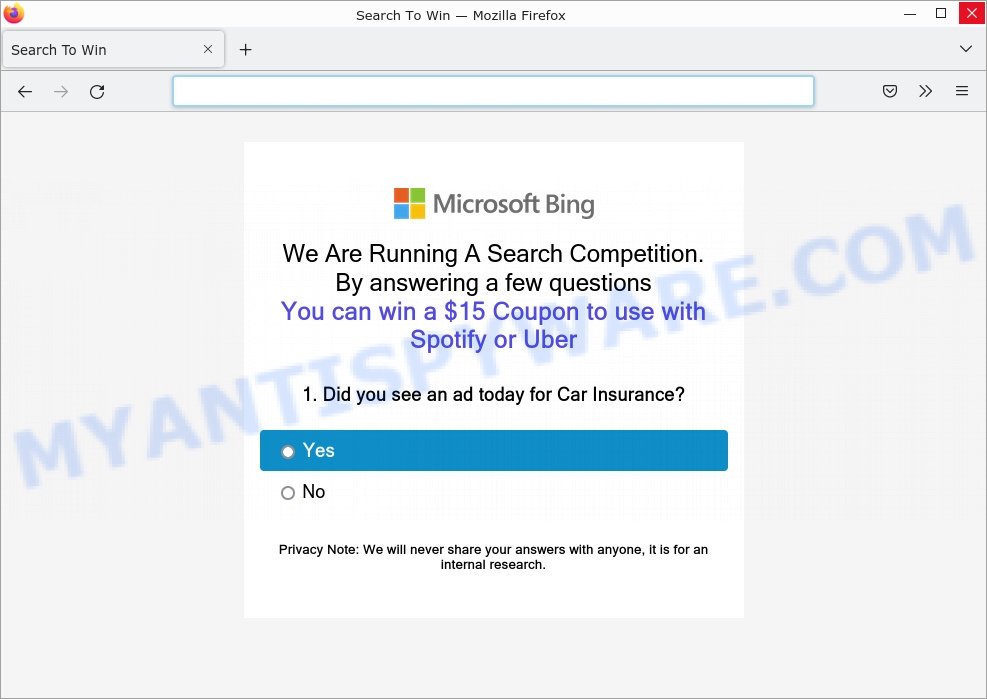
- “Microsoft Bing: We Are Running A Search Competition” is a SCAM
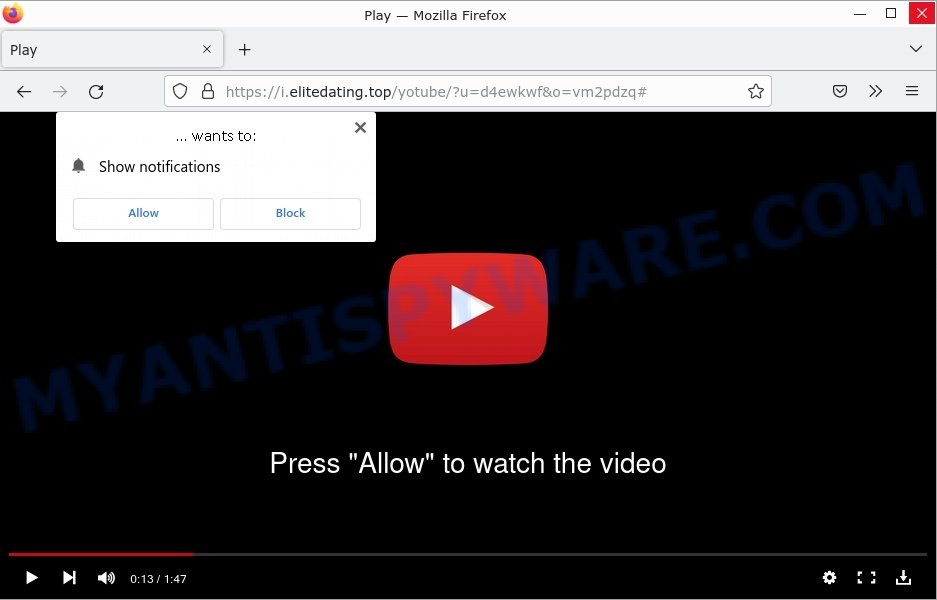
- Elitedating.top Click Allow to Play Scam
- Findshortsmall.com Scam
To summarize, the adware can lead to malware infection and financial losses. It can seriously affect your privacy, your computer’s performance and security.
How does Chromnius get on your computer
Most adware gets installed when users visit an infected website, download a malicious app, or click on a link or an attachment, install freeware that includes a bundled program. Sometimes it is possible to avoid the setup of any adware: run only reputable software which download from reputable sources, never install any unknown and suspicious apps, keep internet browser updated (turn on automatic updates), use good antivirus software, double check freeware before install it (do a google search, scan a downloaded file with VirusTotal), avoid malicious and unknown web pages.
Examples of scam pages that are designed to trick users into installing adware and browser hijackers:
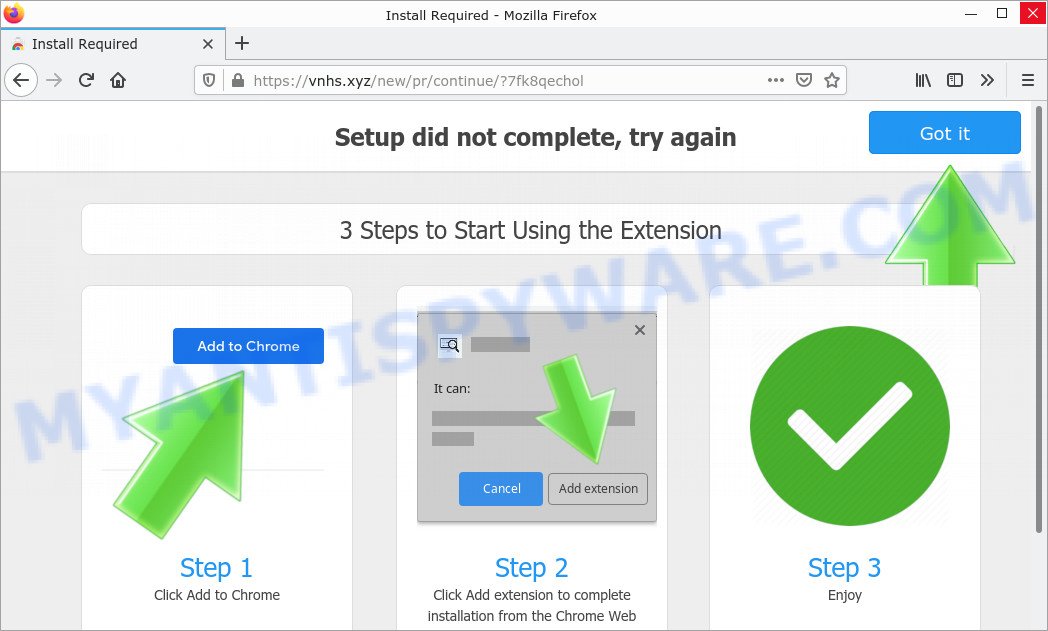
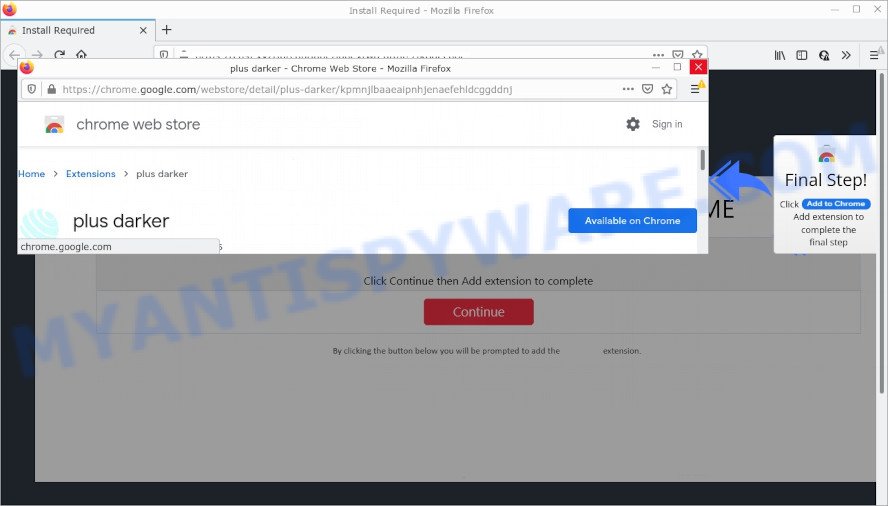
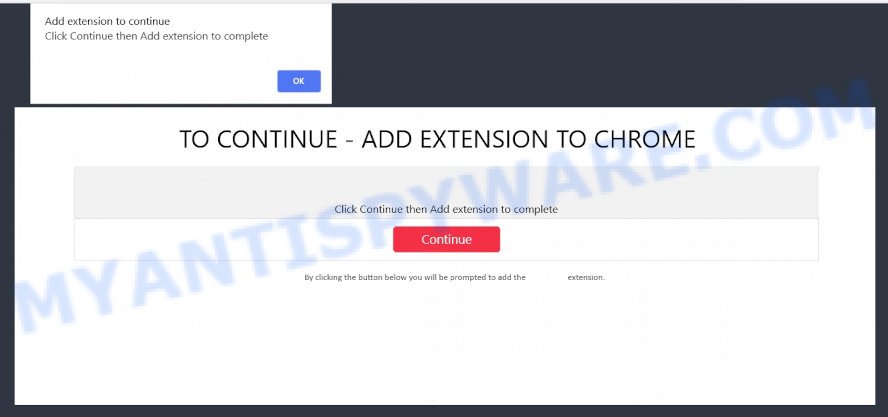
- TO CONTINUE – ADD EXTENSION TO CHROME pop-ups promote a browser hijacker
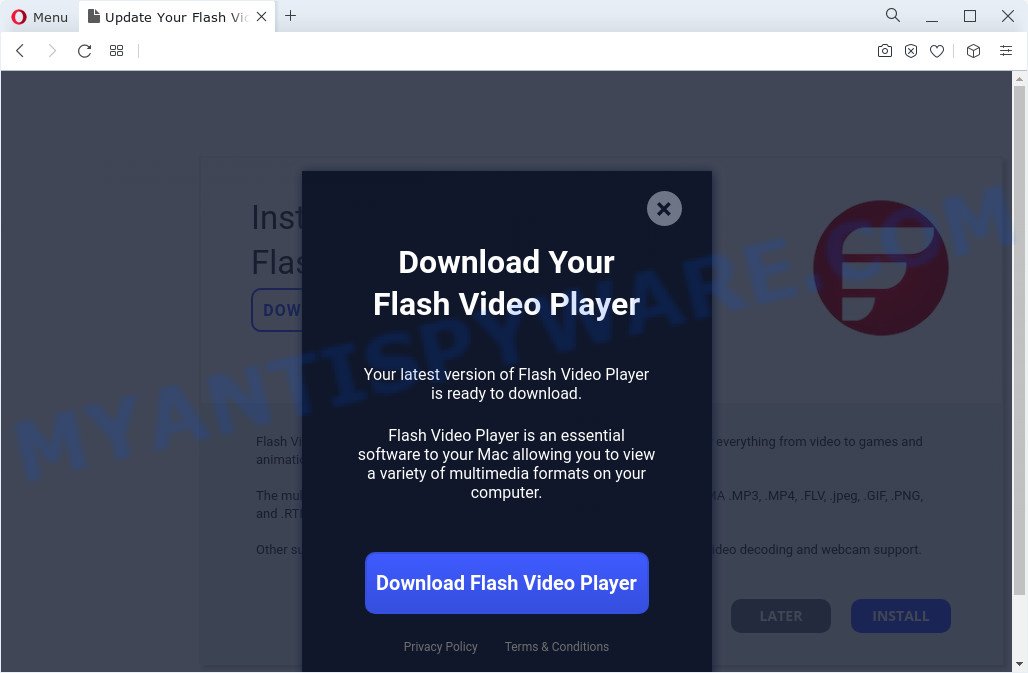
- Fake “Flash Video Player” updates Adware
- “TO CONTINUE – ADD EXTENSION TO CHROME” POP-UP is a SCAM
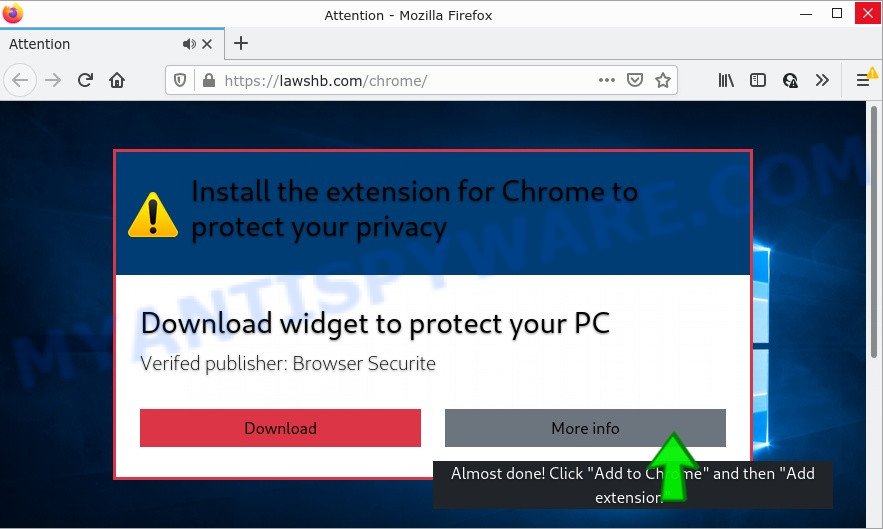
- Install the extension for Chrome to protect your privacy POP-UPS are a SCAM
Threat Summary
| Name | Chromnius, “Chromnius.exe”, “Chromnius” |
| Type | adware, potentially unwanted program (PUP), pop-up advertisements, pop-up virus |
| Distribution | dubious popup ads, adware bundles, freeware installers, fake update tools |
| Related web-sites | Chromnius.download |
| Symptoms |
|
| Removal | Chromnius removal guide |
Adware examples
Adware can be used to distribute other malware. They install PUPs, trojans, browser hijackers, keyloggers, ransomware, spyware and more. Some of the malware designed to collect user data, others install ransomware and trojans on computers, and still others add infected computers to botnets, and so on. In any case, each malicious program is a huge threat to both user privacy and computer security. Therefore, malicious programs must be removed immediately after detection; using an infected computer is very dangerous.
More examples of adware are below:
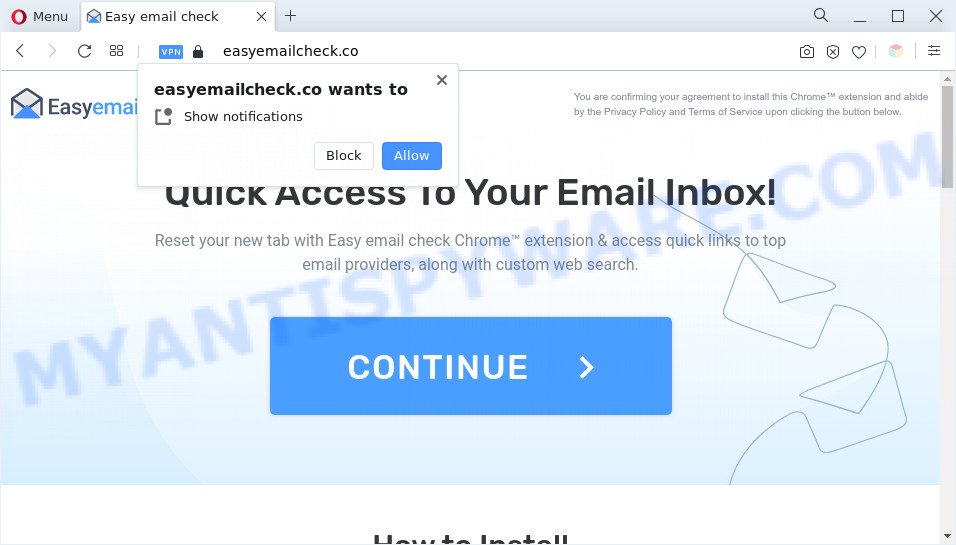
- The Easyemailcheck.co redirect is a sign of adware
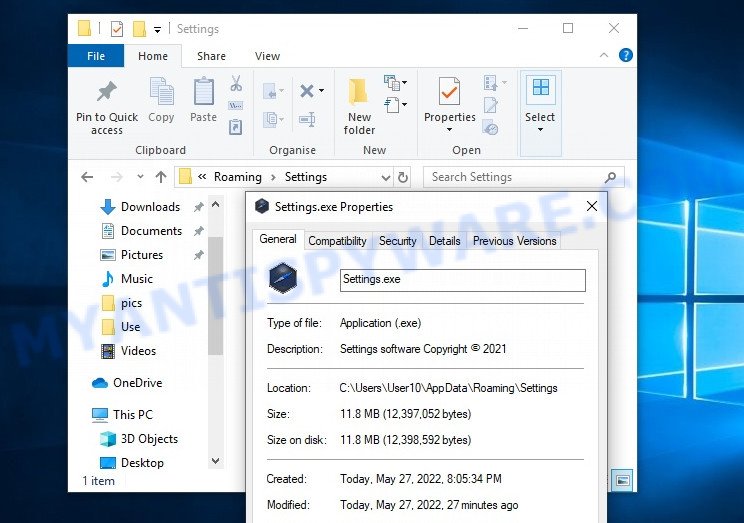
- Settings.exe Adware
- The greenadblocker.com scam promotes Green Blocker adware
- Helper_update adware changes system settings
- Shopping Lovers “adware” browser extension
How can you protect against adware?
There are a number of methods that you can use to protect against malicious adware. It is better to use them together, this will provide stronger protection.
- Use an ad blocker. Ad blockers allow you to browse sites without ads, thus eliminating the possibility of clicking on something malicious and preventing it from being downloaded to the machine.
- Pay for premium versions of popular services. The easiest way to avoid adware is to pay for the service you use. Many Internet services make it possible to use them without ads if you purchase a premium subscription. This helps ensure that malicious adware cannot reach you.
- Buy devices from trusted companies with built-in security. There have already been many cases where people who bought inexpensive Android devices found that adware was already installed on their devices. Cheap Android devices do not receive security updates and are therefore particularly susceptible to infection and should be avoided.
- Use an antivirus. Most antivirus programs can block malicious adware. Some malicious adware can block antiviruses, in which case a more aggressive method should be used, which is to use adware removal software. This software can detect and remove adware that has a negative impact on the device.
How to remove Chromnius from computer (Adware removal guide)
We can help you remove Chromnius and Chromnius from your computer without the help of a professional. Just follow the removal guide below if you currently have adware installed on your PC and you want to remove it. If you are having difficulty trying to get rid of the adware, feel free to contact us for help in the comments section below. Read it once and then bookmark this page (or open it on your smartphone) as you may need to exit your web browser or restart your computer.
To remove Chromnius, use the following steps:
- Kill Chromnius adware
- Disable Chromnius start-up
- Uninstall Chromnius related software
- Scan computer for malware
- Reset Google Chrome
- Reset Internet Explorer
- Reset Firefox
Kill Chromnius adware
Press CTRL, ALT, DEL keys together.
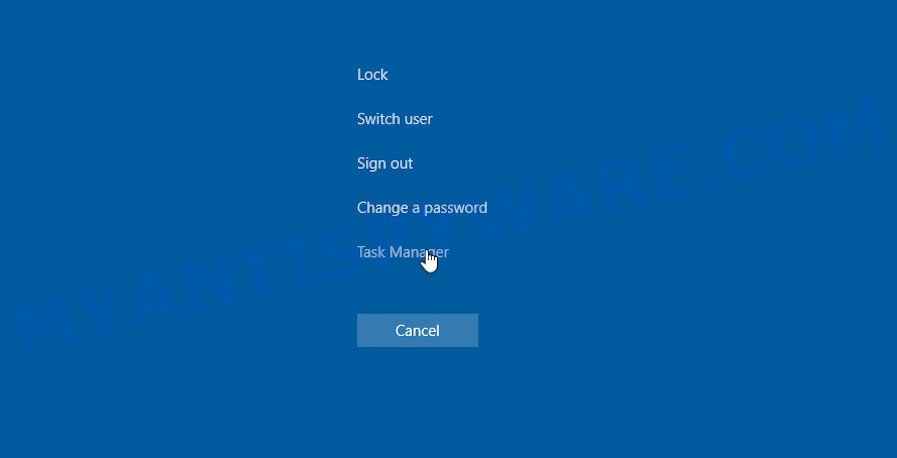
Click Task Manager. Select the “Processes” tab, look for “Chromnius Application”, “Chromnius.exe” or “Chromnius” then right-click it and select “End Task” or “End Process” option. If your Task Manager does not open or the Windows reports “Task manager has been disabled by your administrator”, then follow the guide: How to Fix Task manager has been disabled by your administrator.
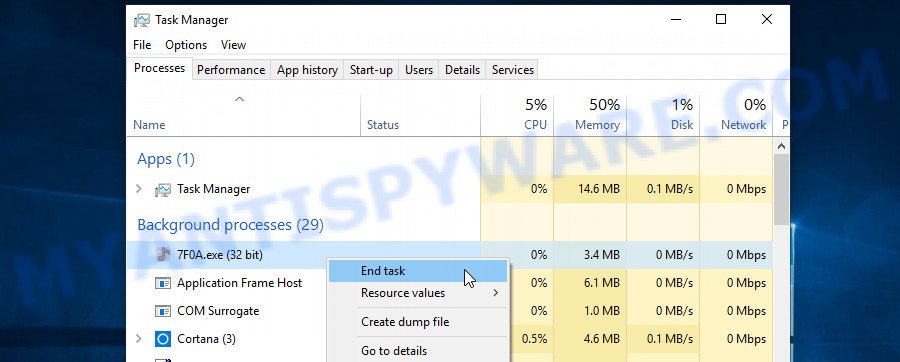
Adware can mask itself to avoid detection by imitating legitimate Microsoft Windows processes. A process is particularly suspicious: it’s taking up a lot of memory (despite the fact that you closed all of your applications), its name is not familiar to you (if you’re in doubt, you can always check the program by doing a search for its name in Google, Yahoo or Bing).
Disable Chromnius start-up
Select the “Start-Up” tab, look for something suspicious that is the Chromnius app, right click to it and select Disable.
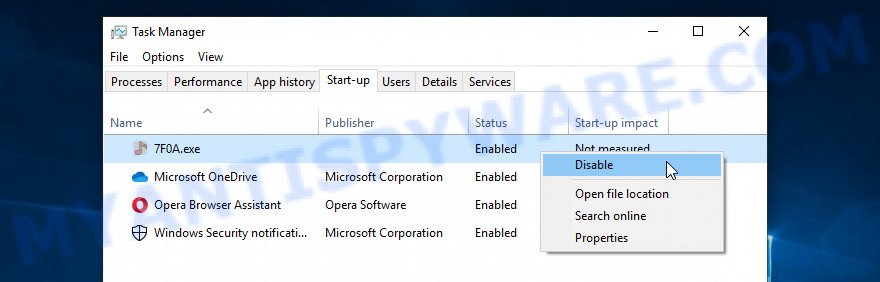
Close Task Manager.
Uninstall Chromnius related software
Check the list of installed apps on your computer and uninstall Chromnius and Chromnius, other suspicious and recently installed apps. If you see an unknown program with incorrect spelling or varying capital letters, it have most likely been installed by malware and you should clean it off first with malware removal utility such as MalwareBytes Anti-Malware.
|
|
|
|
Scan computer for adware
The easiest method to remove adware is to use an antimalware program capable of detecting adware. We suggest MalwareBytes Anti-Malware or other free malware removal tools. It has excellent detection rate when it comes to adware, browser hijackers and other PUPs.
You can remove adware automatically with a help of MalwareBytes AntiMalware. We recommend this free malware removal utility because it can easily remove browser hijackers, adware, PUPs and toolbars with all their components such as files, folders and registry entries.
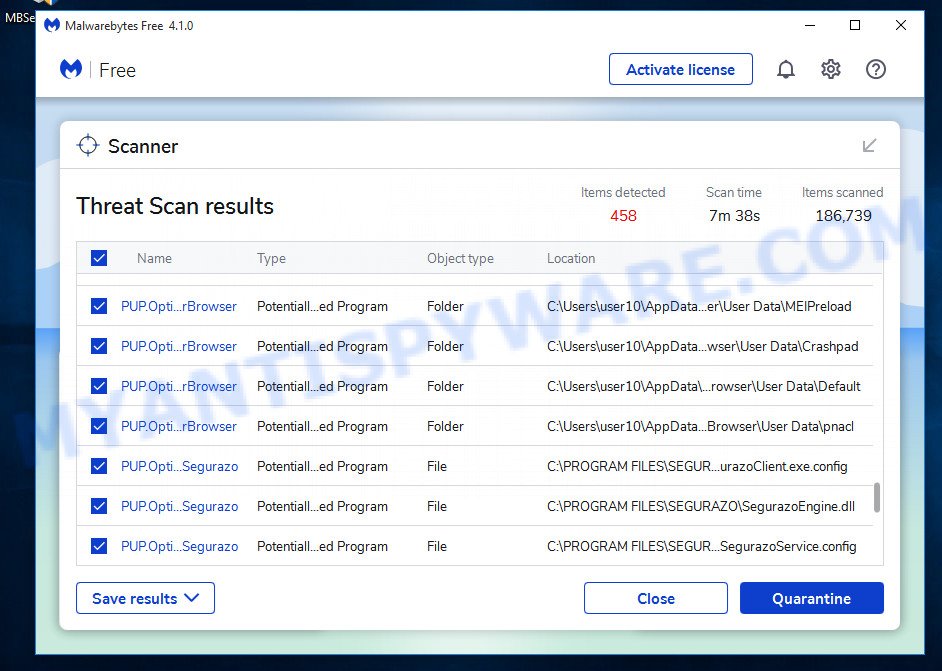
First, visit the page linked below, then click the ‘Download’ button in order to download the latest version of MalwareBytes.
327717 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
Once the downloading process is complete, run it and follow the prompts. Once installed, MalwareBytes will try to update itself and when this procedure is done, click the “Scan” button to perform a system scan with this utility for the adware. A scan can take anywhere from 10 to 30 minutes, depending on the count of files on your computer and the speed of your personal computer. During the scan MalwareBytes AntiMalware will locate threats exist on your computer. Make sure all threats have ‘checkmark’ and click “Quarantine” button.
MalwareBytes AntiMalware is a free malware removal tool that you can use to remove all detected folders, files, services, registry entries and so on. To learn more about this software, we advise you to read the guide or follow the video guide below.
Reset Google Chrome
In this step we are going to show you how to reset Google Chrome settings. Adware can make changes to your web-browser settings, add toolbars and unwanted extensions. By resetting Chrome settings you will reset unwanted changes caused by adware. However, your saved passwords and bookmarks will not be changed, deleted or cleared.
First launch the Chrome. Next, click the button in the form of three horizontal dots (![]() ).
).
It will open the Google Chrome menu. Select More Tools, then press Extensions. Carefully browse through the list of installed addons. If the list has the extension signed with “Installed by enterprise policy” or “Installed by your administrator”, then complete the following steps: Remove Google Chrome extensions installed by enterprise policy.
Open the Chrome menu once again. Further, press the option named “Settings”.
The web browser will display the settings screen. Another method to display the Chrome’s settings – type chrome://settings in the internet browser adress bar and press Enter
Scroll down to the bottom of the page and click the “Advanced” link. Now scroll down until the “Reset” section is visible, as shown in the following example and click the “Reset settings to their original defaults” button.
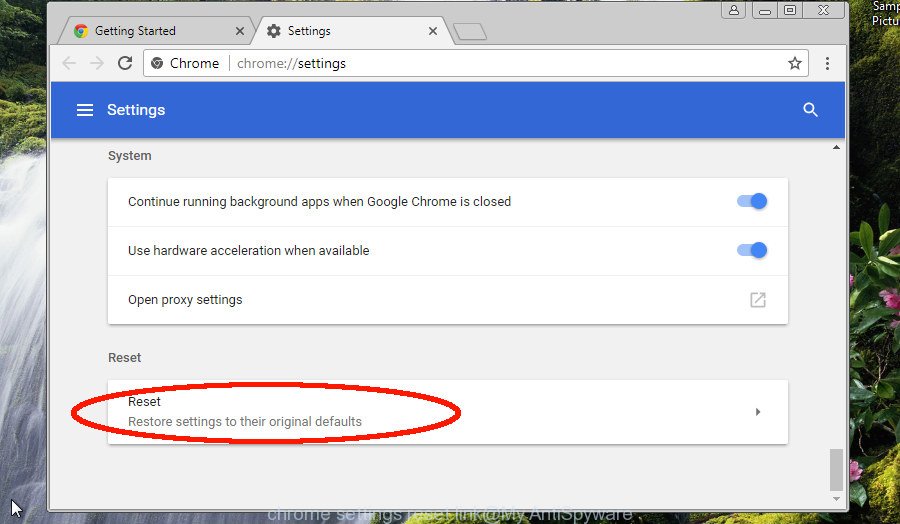
The Google Chrome will display the confirmation dialog box as displayed on the image below.

You need to confirm your action, click the “Reset” button. The web browser will run the task of cleaning. Once it is finished, the internet browser’s settings including search provider by default, home page and newtab back to the values which have been when Google Chrome was first installed on your personal computer.
Reset Firefox
If your Firefox web browser is hijacked by adware, then it may be time to perform the browser reset. Keep in mind that resetting your web-browser will not remove your history, bookmarks, passwords, and other saved data.
Start the Firefox and click the menu button (it looks like three stacked lines) at the top right of the internet browser screen. Next, click the question-mark icon at the bottom of the drop-down menu. It will open the slide-out menu.
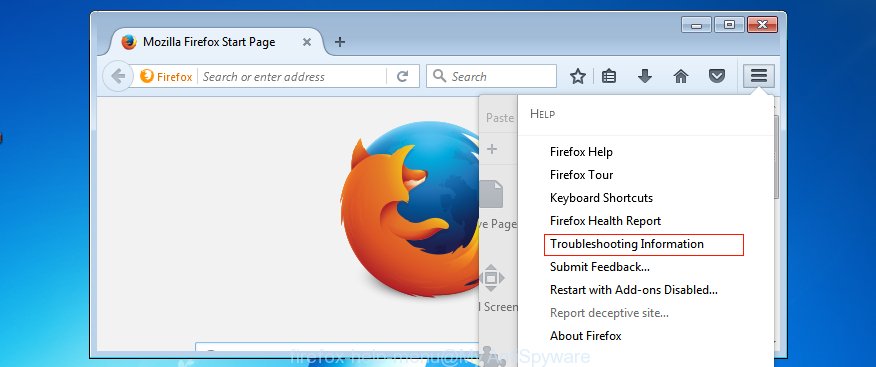
Select the “Troubleshooting information”. If you are unable to access the Help menu, then type “about:support” in your address bar and press Enter. It bring up the “Troubleshooting Information” page as displayed in the following example.
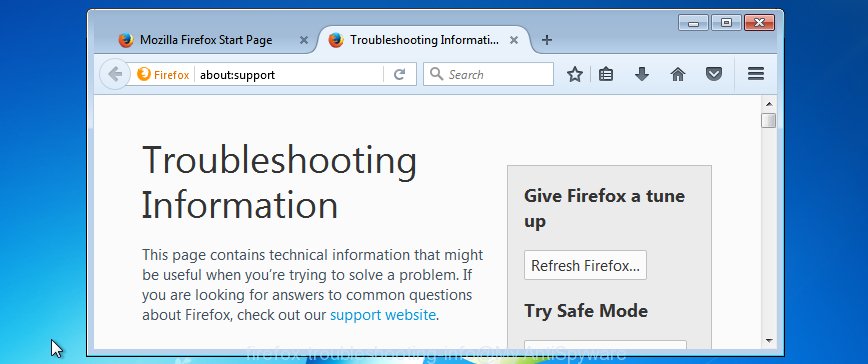
Click the “Refresh Firefox” button at the top right of the Troubleshooting Information page. Select “Refresh Firefox” in the confirmation prompt. The Firefox will start a process to fix your problems that caused by the adware. Once, it is finished, click the “Finish” button.
How to stay safe online
If you browse the Web, you can’t avoid malicious ads and scam sites. But you can protect your internet browser against it. Download and use an ad blocking program. AdGuard is an ad-blocker which can filter out a huge number of of the malicious advertising, blocking dynamic scripts from loading harmful content.
- First, visit the following page, then click the ‘Download’ button in order to download the latest version of AdGuard.
Adguard download
27035 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
- When the downloading process is complete, start the downloaded file. You will see the “Setup Wizard” program window. Follow the prompts.
- After the installation is complete, press “Skip” to close the installation program and use the default settings, or press “Get Started” to see an quick tutorial which will help you get to know AdGuard better.
- In most cases, the default settings are enough and you don’t need to change anything. Each time, when you run your computer, AdGuard will launch automatically and stop unwanted advertisements, block harmful and misleading webpages. For an overview of all the features of the program, or to change its settings you can simply double-click on the icon called AdGuard, which can be found on your desktop.
Finish words
We suggest that you keep Malwarebytes Anti-Malware (to periodically scan your device for new adware and other malware) and AdGuard (to help you stop malicious pop-ups and scam sites). Moreover, to prevent any adware, please stay clear of unknown and third party programs, make sure that your antivirus software, turn on the option to search for potentially unwanted programs.
If you need more help with Chromnius related issues, go to here.