What is “On this day, I hacked your device’s operating system” EMAIL?
On this day, I hacked your device’s operating system email is a ‘sextortion’ scam that relies on psychological manipulation tactics. Scammers claim to have obtained information that could damage the victims reputation. It should be emphasized that any statements, claims and threats contained in such emails are false and should be ignored. Criminals usually contact potential victims through email, but in some cases, criminals can use online web forms, whatsapp and sms messages.
“On this day, I hacked your device’s operating system” email is a ‘sextortion’ scam
QUICK LINKS
- What is “On this day, I hacked your device’s operating system” email?
- Should you pay?
- What to do when you receive the scam email?
On this day, I hacked your device’s operating system Email Scam in detail
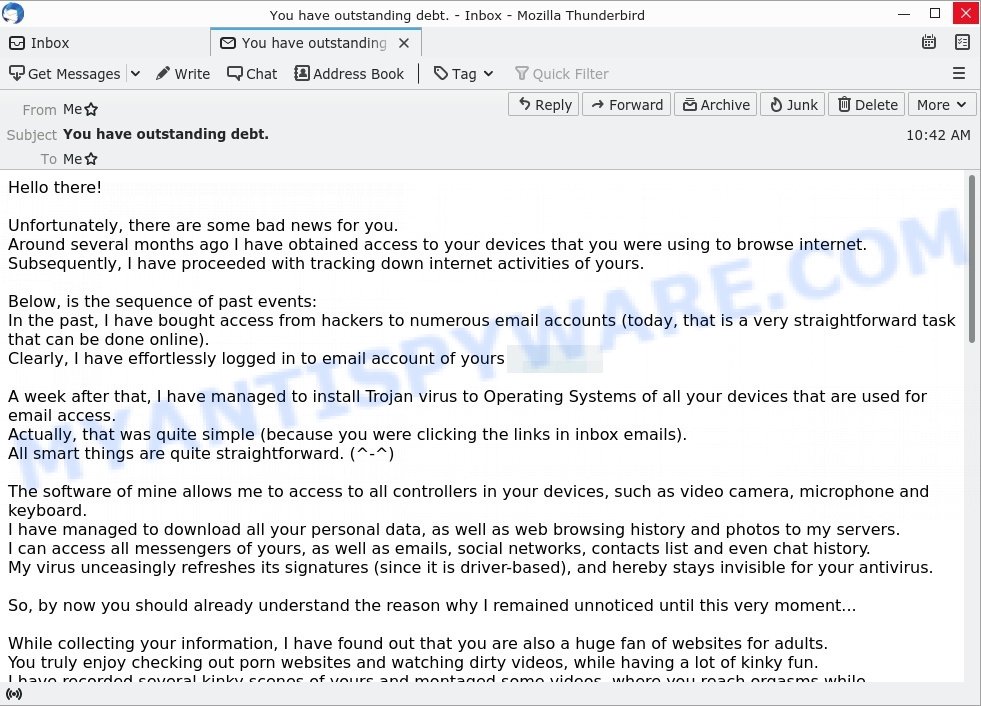
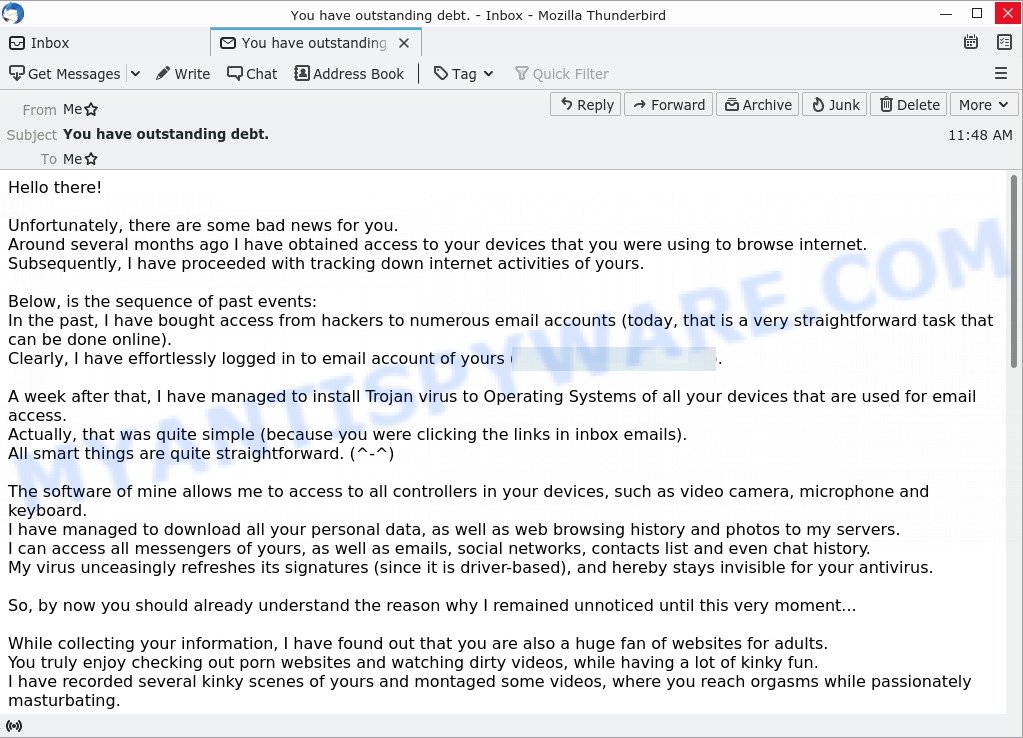
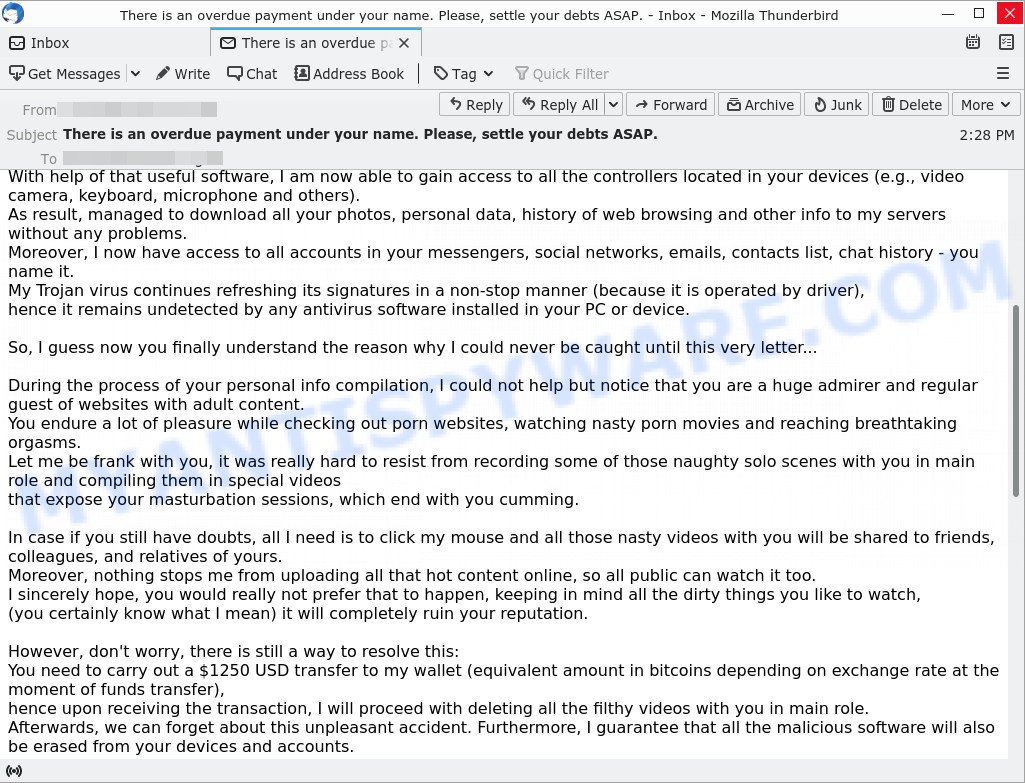
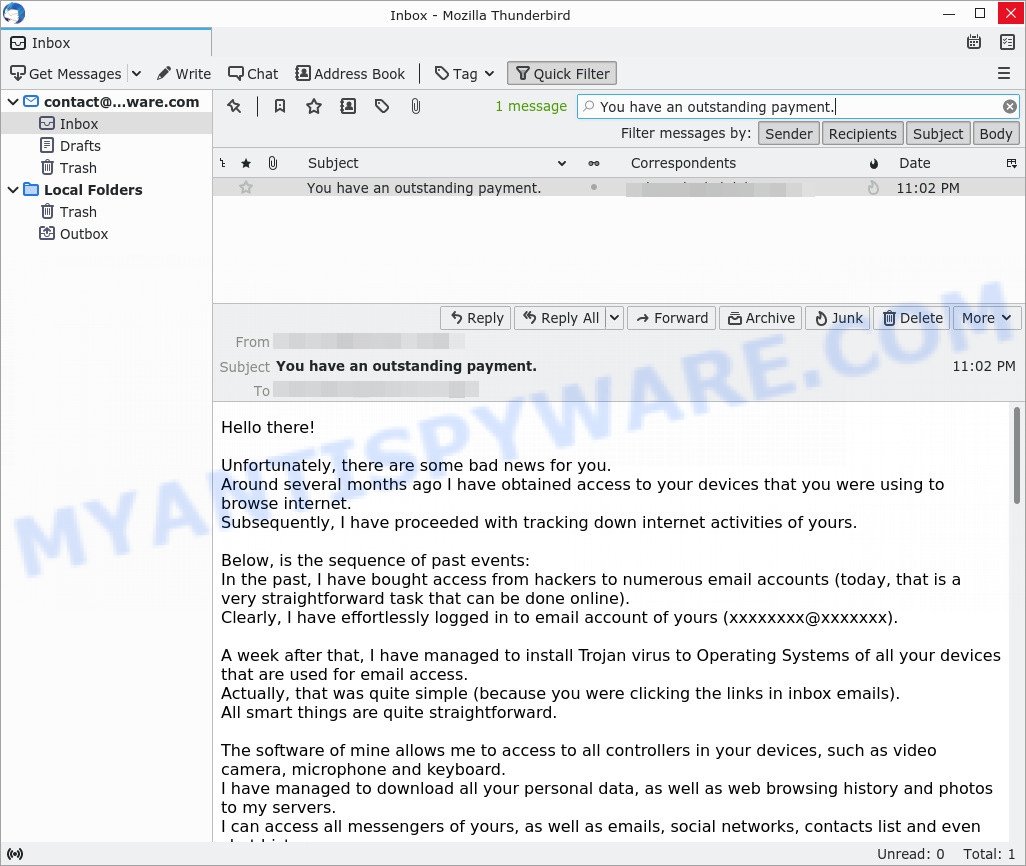
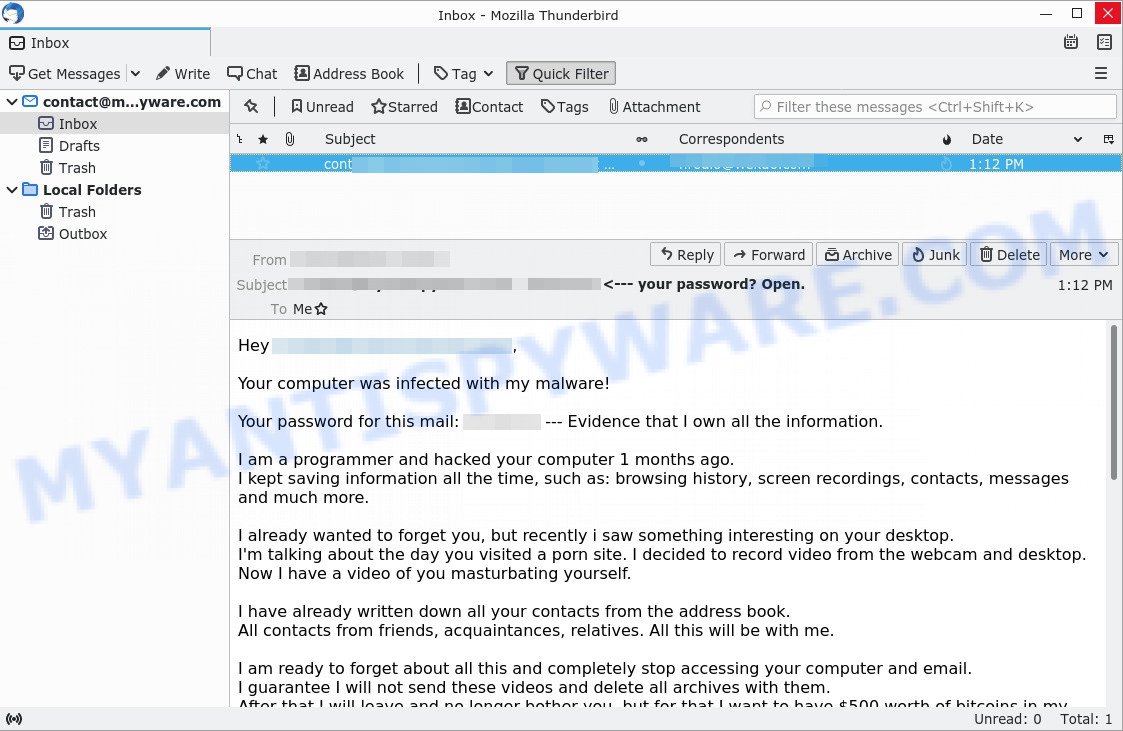
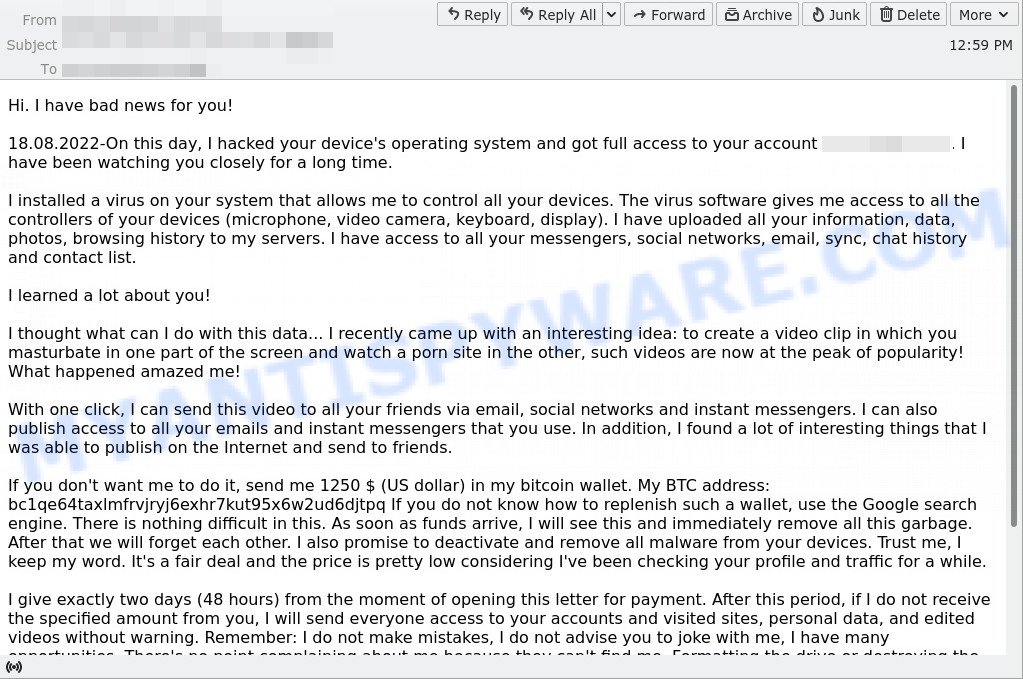
In this particular case, the scam says that someone has been watching the victim for several months now, because the victim’s computer has a virus, which is a Trojan that allows the attacker to completely control the computer and even record video from the computer’s camera. The scam claims that a video was recorded showing the victim masturbating while browsing porn sites. This video will be sent to the victim’s friends, family and even colleagues unless the victim pays the attacker a ransom to the bitcoin address provided in the email.
Full text of the scam email:
Hi. I have bad news for you!
18.08.2022-On this day, I hacked your device’s operating system and got full access to your account xxxxxxx. I have been watching you closely for a long time.
I installed a virus on your system that allows me to control all your devices. The virus software gives me access to all the controllers of your devices (microphone, video camera, keyboard, display). I have uploaded all your information, data, photos, browsing history to my servers. I have access to all your messengers, social networks, email, sync, chat history and contact list.
I learned a lot about you!
I thought what can I do with this data… I recently came up with an interesting idea: to create a video clip in which you masturbate in one part of the screen and watch a porn site in the other, such videos are now at the peak of popularity! What happened amazed me!
With one click, I can send this video to all your friends via email, social networks and instant messengers. I can also publish access to all your emails and instant messengers that you use. In addition, I found a lot of interesting things that I was able to publish on the Internet and send to friends.
If you don’t want me to do it, send me 1250 $ (US dollar) in my bitcoin wallet. My BTC address: bc1qe64taxlmfrvjryj6exhr7kut95x6w2ud6djtpq If you do not know how to replenish such a wallet, use the Google search engine. There is nothing difficult in this. As soon as funds arrive, I will see this and immediately remove all this garbage. After that we will forget each other. I also promise to deactivate and remove all malware from your devices. Trust me, I keep my word. It’s a fair deal and the price is pretty low considering I’ve been checking your profile and traffic for a while.
I give exactly two days (48 hours) from the moment of opening this letter for payment. After this period, if I do not receive the specified amount from you, I will send everyone access to your accounts and visited sites, personal data, and edited videos without warning. Remember: I do not make mistakes, I do not advise you to joke with me, I have many opportunities. There’s no point complaining about me because they can’t find me. Formatting the drive or destroying the device won’t help because I already have your data. It makes no sense to write back to me – I do not write from personal mail and do not look at the answers.
Good luck and don’t get angry! Everyone has their own job, you just got unlucky today.
P.S. In the future, I recommend that you follow the safety rules on the Internet and do not visit dubious sites
As stated above, the “On this day, I hacked your device’s operating system” email is just a sextortion scam. All claims and threats made in this email are false. Therefore, the email can be safely ignored and deleted.
Typically, sextortion scams are sent via email, thousands at a time, and are part of larger spam campaigns. As with many other types of scams, scammers are evolving their methods to deliver their messages to potential victims. Such attacks can be personalized and sent out in smaller numbers to avoid detection. Scammers can use reputable services, change and personalize the content of each message, and avoid including links or attachments – all in an attempt to bypass security.
Should you pay?

The best advice is: Don’t pay the ransom! If you receive the sextortion scam email, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Name | On this day, I hacked your device’s operating system SCAM |
| Type | Phishing, Bitcoin Email Scam, Fraud, Scam |
| Ransom amount | $850, $950, $1900, $1750, $1250 |
| Bitcoin Address | 1Jo66YRYVogrb9htwauuzqTM1Fqpd7EtHb, 1Q5tNZM6pRQa1RejyKYHgJDkw23riFx9zw, bc1qe9h0drc5aq3xl7zyaq6l0al6nwf92uweruw24j, bc1qa9nn0xzdlqey58hd7kqgutlry9c04e5pf6sql2, bc1qe64taxlmfrvjryj6exhr7kut95x6w2ud6djtpq |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like On this day, I hacked your device’s operating system, our computer security experts recommend follow some easy steps below |
Examples of scam emails
There are many sextortion scams circulating via email. Scammers often change the content of emails in order to deceive victims and bypass the security system. I have to share bad news with you, Hi, I’m sorry but You’re going to have a bad day, FINAL WARNING Email are other examples of sextortion scams. Such emails are also often used to distribute ransomware, trojans, worms and other malware.
- “You have outstanding debt.” email is a sextortion scam
- Unfortunately there are some bad news for you email is a sextortion SCAM
- “There is an overdue payment under your name. Please, settle your debts ASAP.” email is a SCAM
- The “You have an outstanding payment.” email is a SCAM
- Your computer was infected with my malware Email Message is a SCAM
What to do when you receive the “Payment from your account” email?
We advice to someone who gets this fraudulence message:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/.
- Mark the “On this day, I hacked your device’s operating system” email as SPAM/JUNK and delete it.
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your computer for malware
If you suspect that your computer is infected with malware, you accidentally clicked on a link in the scam email, or just want to scan your computer, then use one of the best free malware removal tools. MalwareBytes is an antivirus that can be used to perform a virus scan, detect and remove almost all the forms of malicious programs including ransomware, trojans, worms, adware, browser hijackers, potentially unwanted software and spyware. MalwareBytes has real-time protection that can defeat most malicious software and ransomware. Despite so many features, it does not reduce the performance of your computer. You can use MalwareBytes with any other antivirus without any conflicts.
First, please go to the link below, then click the ‘Download’ button in order to download the latest version of MalwareBytes.
327035 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When the downloading process is done, close all windows on your computer. Further, launch the file named MBSetup. If the “User Account Control” dialog box pops up like below, click the “Yes” button.
It will show the Setup wizard which will assist you install MalwareBytes on the computer. Follow the prompts and do not make any changes to default settings.
After the setup is complete successfully, press “Get Started” button. Then MalwareBytes AntiMalware will automatically run and you can see its main window such as the one below.
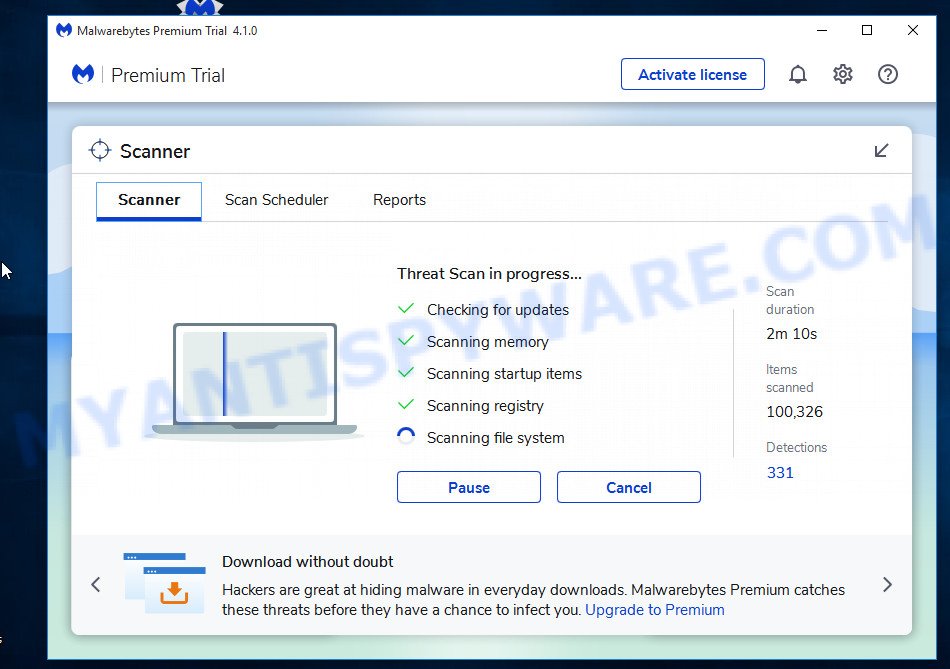
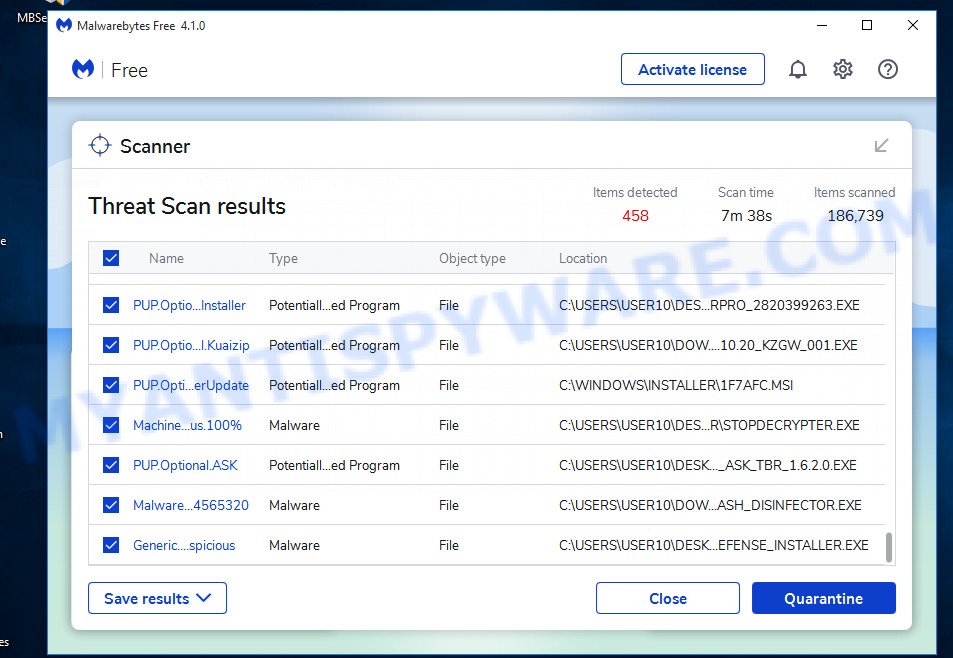
Next, click the “Scan” button for scanning your computer for malicious software and other security threats. A system scan can take anywhere from 5 to 30 minutes, depending on your computer. While MalwareBytes is scanning, you can see how many objects it has identified as threat.
When the scanning is done, the results are displayed in the scan report. In order to remove all threats, simply press “Quarantine” button.
We suggest you look at the following video, which completely explains the process of using MalwareBytes to remove malicious software.
If you are having issues with malware removal, then check out Kaspersky virus removal tool. It can easily remove trojans, spyware, browser hijackers, adware, worms and ransomware with all their components such as files, folders and registry entries. Visit the page linked below to download the latest version of Kaspersky virus removal tool for Windows.
129227 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing sites, install an ad blocking program like AdGuard. It can block malicious and misleading websites, stop unwanted ads and pop-ups while using Internet Explorer, Google Chrome, Firefox and Edge. So, if you like to surf the Internet and want to protect your computer from phishing scams, then AdGuard is your best choice.
Installing AdGuard is very easy. First you’ll need to download AdGuard by clicking on the link below.
26838 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Finish words
If you receive a scam email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.