What is I know, it’s unpleasant to start the conversation with bad news SCAM?
I know, it’s unpleasant to start the conversation with bad news is a new ‘sextortion’ scam. Sextortion scams are designed to scare victims into handing over money without seeking any further information and assistance. Criminals usually contact potential victims through email, but in some cases, criminals can use online web forms, whatsapp and sms messages. The scammers claim that they obtained material compromising victims’ reputations. It should be emphasized that any statements, claims and threats contained in the ‘sextortion’ scams are false.
Hi. How are you? I know, it’s unpleasant to start the conversation with bad news, but I have no choice.” message is a SCAM
QUICK LINKS
- What is I know, it’s unpleasant to start the conversation with bad news SCAM?
- Should you pay?
- What to do when you receive the scam email?
- How to spot a phishing email?
- Report Scam Email
The Scam in detail
The “I know, it’s unpleasant to start the conversation with bad news” email informs that for several months now the sender has full access to the email recipient’s computer and other devices. The attacker claims to have installed a Trojan on the victim’s computer, which allowed him to take full control of the computer and record a video in which the victim masturbates while browsing adult websites. The sender threatens to send this video to the victim’s colleagues, relatives and friends if the ransom of $1370 is not paid. If the victim pays the required amount in Bitcoin, the hacker promises to remove the compromising video, as well as malware from all victim devices.
The scam email is not the only one of its kind, there are many similar ones. They all have similar features: statement that the victim’s computer and webcam were hacked, threats that the attackers recorded a compromising video, and a ransom demand. Explanations that scammers use to explain how they have access to your camera and privacy:
- They set up malware on adult (porn) website.
- They penetrated with “zero-click” vulnerability on Zoom or Pegasus.
- They got your credentials (login and password) from hackers.
Depending on the scam email, victims are given 24 to 48 hours to pay a ransom in Bitcoin. The sextortion emails also contain claims that the victim’s contact information was stolen, allegedly the hacker copied the victim’s contact list and social media credentials. And finally, Sextortion scams contain threats, the victims must pay a ransom, or compromising materials will be sent to their contacts.
Typically, sextortion scams are sent via email, thousands at a time, and are part of larger spam campaigns. As with many other types of scams, scammers are evolving their methods to deliver their messages to potential victims. Such attacks can be personalized and sent out in smaller numbers to avoid detection. Scammers can use reputable services, change and personalize the content of each message, and avoid including links or attachments – all in an attempt to bypass security.
Text presented in the “I know, it’s unpleasant to start the conversation with bad news” email:
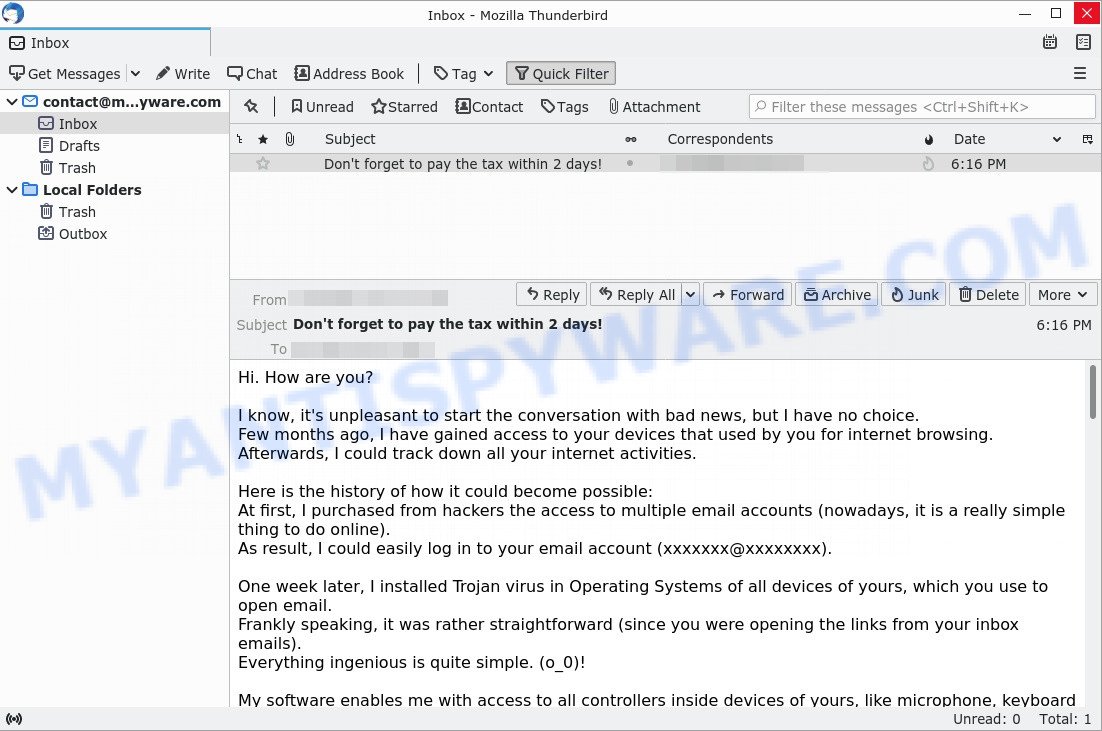
Hi. How are you?
I know, it’s unpleasant to start the conversation with bad news, but I have no choice.
Few months ago, I have gained access to your devices that used by you for internet browsing.
Afterwards, I could track down all your internet activities.Here is the history of how it could become possible:
At first, I purchased from hackers the access to multiple email accounts (nowadays, it is a really simple thing to do online).
As result, I could easily log in to your email account (xxxxxxx@xxxxxxxx).One week later, I installed Trojan virus in Operating Systems of all devices of yours, which you use to open email.
Frankly speaking, it was rather straightforward (since you were opening the links from your inbox emails).
Everything ingenious is quite simple. (o_0)!My software enables me with access to all controllers inside devices of yours, like microphone, keyboard and video camera.
I could easily download to my servers all your private info, including the history of web browsing and photos.
I can effortlessly gain access to all your messengers, social networks accounts, emails, contact list as well as chat history.
Virus of mine constantly keeps refreshing its signatures (because it is driver-based), and as result remains unnoticed by your antivirus.Hence, you can already guess why I stayed undetected all this while.
As I was gathering information about you, I couldn’t help but notice that you are also a true fan of adult-content websites.
You actually love visiting porn sites and browsing through kinky videos, while pleasuring yourself.
I could make a few dirty records with you in the main focus and montaged several videos showing the way you reach orgasm while masturbating with joy.If you are still uncertain regarding the seriousness of my intentions,
it only requires several mouse clicks for me to forward your videos to all your relatives, as well as friends and colleagues.
I can also make those vids become accessible by public.
I honestly think that you do not really want that to happen, considering the peculiarity of videos you like to watch,
(you obviously know what I mean) all that kinky content can become a reason of serious troubles for you.However, we can still resolve this situation in the following manner:
Everything you are required to do is a single transfer of $1370 USD to my account (or amount equivalent to bitcoin depending on exchange rate at the moment of transfer),
and once the transaction is complete, I will straight away remove all the dirty content exposing you.
After that, you can even forget that you have come across me. Moreover, I swear that all the harmful software will be removed from all devices of yours as well.
Make no doubt that I will fulfill my part.This is really a great deal that comes at a reasonable price, given that I have used quite a lot of energy to check your profile as well as traffic over an extended period of time.
If you have no idea about bitcoin purchase process – it can be straightforwardly done by getting all the necessary information online.Here is my bitcoin wallet provided below: 1NYCdN9eBXhT4tPSpu4EhpjC9gHXLzipLL
You should complete the abovementioned transfer within 48 hours (2 days) after opening this email.
The following list contains actions you should avoid attempting:
#Do not try replying my email (email in your inbox was generated by me alongside with return email address).
#Do not try calling police as well as other security forces. In addition, abstain from sharing this story with your friends.
After I find out (be sure, I can easily do that, given that I keep complete control of all your devices) – your kinky video will end up being available to public right away.
#Do not try searching for me – there is absolutely no reason to do that. Moreover, all transactions in cryptocurrency are always anonymous.
#Do not try reinstalling the OS on your devices or throwing them away. It is pointless as well, since all your videos have already been uploaded to remote servers.The following list contains things you should not be worried about:
#That your money won’t reach my account.
– Rest assured, the transactions can be tracked, hence once the transaction is complete,
I will know about it, because I continuously observe all your activities (my trojan virus allows me to control remotely your devices, same as TeamViewer).
#That I still will share your kinky videos to public after you complete money transfer.
– Trust me, it’s pointless for me to continue troubling your life. If I really wanted, I would make it happen already!Let’s make this deal in a fair manner!
Owh, one more thing…in future it is best that you don’t involve yourself in similar situations any longer!
One last advice from me – recurrently change all your passwords from all accounts.
Should you pay?
The best advice is: Don’t pay the ransom and do not reply! Sometimes scammers will escalate if you reply. If you receive the sextortion email scam, just ignore the scammers. The best way to deal with the scam email is simply to move it to trash!

Threat Summary
| Name | I know, it’s unpleasant to start the conversation with bad news SCAM |
| Type | Sextortion, Phishing, Bitcoin Email Scam, Fraud, Scam |
| Email subject line | Don’t forget to pay the tax within 2 days! |
| Ransom amount | $1370 |
| Bitcoin Address | 1LCFadwrvkDtYJFZqTPwBncKkfrvR2oWnk, 1JY9VZAF7kMofJDHZfgXgYNBQfPWVg8oF3, 1Ei4Mer3MowiR5a11VDUhsoNSxU27AnM8U, 1AJcoDsSGe9teEfzSMicXprJFae7729J5y, 1NYCdN9eBXhT4tPSpu4EhpjC9gHXLzipLL |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like I know, it’s unpleasant to start the conversation with bad news, our computer security experts recommend follow some easy steps below |
Examples of such scams
There are many sextortion scams circulating via email. Scammers often change the content of emails in order to deceive victims and bypass the security system. Unfortunately, there are some bad news for you, I have e-mailed you from your account, I am sorry to inform you that your device was hacked are other examples of sextortion scams. Such messages are also often used to distribute ransomware, trojans, worms and other malware.
What to do when you receive the I know, it’s unpleasant to start the conversation with bad news SCAM email
We advice to someone who gets this fraudulence message:
- Do not panic.
- Don’t even think this message is true.
- If you receive a message from someone threatening you and asking you to pay a ransom, do not respond. Just delete this message.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Do not respond to scam messages or emails.
- Scan your computer for malware.
- Install an anti-phishing software.
If you suspect that your computer is infected with malware, you accidentally clicked on a link in the scam email, or just want to scan your computer, then use one of the free malware removal tools.
How to spot a phishing email?
Phishing emails often share common characteristics; they are designed to trick victims into clicking on a phishing link or opening a malicious attachment. If you know these characteristics, you can detect phishing emails and prevent identity theft.
Here are some ways to recognize a phishing email
- Inconsistencies in Email Addresses. The most obvious way how to spot a scam email is finding inconsistencies in email addresses and domain names. If the email claims to be from a reputable company, like Amazon or PayPal, but the email is being sent from a public email domain, such as “gmail.com” it’s probably a scam.
- The domain name is misspelt. Look carefully for any subtle misspellings in the domain name. Like arnazon.com where the “m” has been replaced by “rn”, or paypa1.com, where the “l” has been replaced by “1”. These are common tricks of scammers.
- Generic greetings. If the email starts with a generic “Dear”, “Dear sir” or “Dear madam” that is a warning sign that it might not really be your shopping site or bank.
- Suspicious links. If you have the slightest suspicion an email may be a scam, do not click on the links you see. Instead, hover over the link, but don’t click it. This will pop up a small box that contains the actual URL. This works on image links as well as text links.
- Unexpected attachments. Email attachments should always be verified before clicking. Any attachments should be scanned for viruses – especially if they have an unfamiliar extension or one commonly associated with malware (.zip, .exe, .scr, etc.).
- The email creates a sense of urgency. Creating a false sense of urgency is a common trick of phishing emails. Be suspicious of emails that claim you must call, open an attachment or click a link immediately.
Report Scam Email
If you receive a scam email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.










Greetings from Japan,
Many thanks for the valuable information you’ve provided here. Yesterday I got my THIRD “I know, it’s unpleasant yadda yadda yadda…” email. They were all identical.: “Pay up in two days or else.” Pffft. Yeah, right. Two days pass and what happens? Nothing. Delete,delete, delete. On the one hand it makes my blood boil that these parasites exist and people fall for it, while on the other hand I have to laugh because these are such pathetically lame attempts at extortion. It’s always “I have control of all your devices and I can do this and I can do that.”, but always in generalities. There’s never anything specific, no actual proof displayed that they have anything at all from your PC or any other device. That should raise a huge red flag to anyone even slight computer literate. I’m no PC genius myself, yet it’s so blatantly obvious these morons no absolutely nothing about me. They got ONE of my three email addresses. Big deal. It’s also the one I use least. I’m also a language teacher and I’m not even sure whoever wrote these is a native speaker, the English is so poor. My antivirus provider is Bitdefender, which I’ve had for years, so when they write, “Few months ago, I have gained access to your devices…”, my frequent virus scans show that to be complete nonsense.
Frankly, I wanted to reply to the scummy bastard to tell him exactly what I thought of him, but in German, Japanese and Russian, all, shall we say, highly uncomplimentary, with a heaping spoonful of, “You got this info, huh? Well, prove it, boyo.” I was hoping receiving such a reply would befuddle him and have him scurrying to Google Translate to see what it was. Too bad I couldn’t do that.
Rest assured I’m on to these chuckleheads. I’ve had credit cards that I don’t even have be ‘canceled’, my Amazon account has been ‘suspended’ any number of times, yet, oddly enough, I can still order things, both from Japan and the US. The only email account they seem to be able to access is that provided be my ISP with which I use Thunderbird in Win10, which tosses most of these fools into the JUNK file. It misses a few, but they’re obvious spam, and into the JUNK file they go. I look though them just for entertainment value, especially the ones offering me huge amounts of money.Those I snip out and keep because they’re so over-the-top goofy. Then it’s ‘Empty Junk’, click, bye-bye.
Anyway, many thanks again for this site. I’m very glad to learn the particulars of this scam. I’m going save it to pass it on to friends and family. Everybody needs to know this.
Oh drat. No edit function. This sentence should read “That should raise a huge red flag to anyone even slightLY computer literate.” Sorry.
Another thought occurred to me. It would seem harvesting email addresses is not all that hard given that these things seem to spread like the Omicron virus, but that’s all they get. The rest is pure BS.
I hope you’ll forgive me for mentioning another antivirus provider. It doesn’t mean I’m not indebted to you for giving a complete account and warning about how these lowlifes operate. Two thumbs up.
Im 14 so they are the ones in some trouble if they got naked photos of me. LOL