⚠️ Did you get an email with the subject “Your personal data has leaked due to suspected harmful activities” that starts with “Hi there! I am a professional hacker”?
Here’s what’s going on: The email claims to have hacked your system, monitored your activities, and threatens to expose compromising videos and messages unless you pay $1450 in Bitcoin. You’re told to transfer the money quickly to avoid embarrassment.
But here’s the truth: There’s no actual evidence or compromising material. The scammer is trying to scare you into paying by making false threats. Paying won’t make the problem go away; it might even make you a target for more scams.
💡 The “Your personal data has leaked due to suspected harmful activities” email is a scam. Despite its convincing tone, it’s a classic scam tactic known as sextortion. The scam uses fear to manipulate people. Remember, paying these scammers doesn’t protect you; it just makes you a target for further scams. Always be skeptical of emails that demand money or personal information. Being aware of these scams and vigilant is your best defense online.
Table of Contents
🚨 Is the “Your personal data has leaked” Email a Scam?
Yes, this email, which starts with “Hi there! I am a professional hacker“, is a classic example of an extortion scam. 🚫 If you’ve received an email with this subject line or a similar message attempting to blackmail you by claiming to have compromising information, be very cautious. These threats are not based on real incidents but are designed to exploit your fear and coerce you into paying a ransom.
Scam Claims:
- I have successfully managed to hack your operating system.
- I was secretly monitoring all your activities and watching you for several months.
- Your computer was infected with harmful spyware due to visiting a website with porn content.
- I can gain complete access to your computer or any other device that you own.
- I can see absolutely everything on your screen and switch on the camera as well as microphone at any point of time without your permission.
- I can access and see your confidential information as well as your emails and chat messages.
- Your antivirus cannot detect my malicious software because it refreshes its signatures on a 4-hourly basis.
- I have made a video compilation showing scenes of you masturbating while watching a video.
- All I need is for you to transfer $1450 USD to my Bitcoin account.
- Once the required amount is transferred, I will delete all the videos and disappear from your life.
- You must complete the transfer within 50 hours.
- If you share this message with others, I will make your private videos public.
The email uses threats and fear to create a sense of urgency. 🚨 The goal? To coerce you into sending money to the scammer without any real proof of the claimed videos. These scammers capitalize on the panic and shame of their victims to extort money.
The email read as follows:
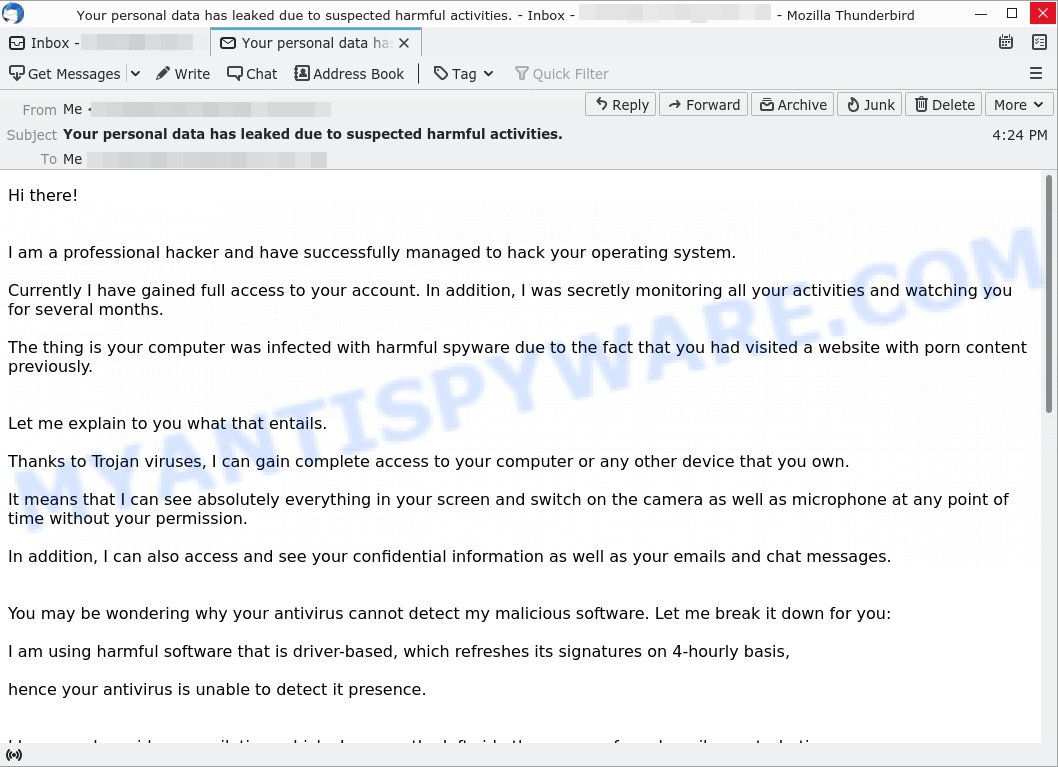
Hi there!
I am a professional hacker and have successfully managed to hack your operating system.
Currently I have gained full access to your account. In addition, I was secretly monitoring all your activities and watching you for several months.
The thing is your computer was infected with harmful spyware due to the fact that you had visited a website with porn content previously.
Let me explain to you what that entails.
Thanks to Trojan viruses, I can gain complete access to your computer or any other device that you own.
It means that I can see absolutely everything in your screen and switch on the camera as well as microphone at any point of time without your permission.
In addition, I can also access and see your confidential information as well as your emails and chat messages.
You may be wondering why your antivirus cannot detect my malicious software. Let me break it down for you:
I am using harmful software that is driver-based, which refreshes its signatures on 4-hourly basis,
hence your antivirus is unable to detect it presence.
I have made a video compilation, which shows on the left side the scenes of you happily masturbating,
while on the right side it demonstrates the video you were watching at that moment. (“)
All I need is just to share this video to all email addresses and messenger contacts of people you are in communication with on your device or PC.
Furthermore, I can also make public all your emails and chat history.
I believe you would definitely want to avoid this from happening.
Here is what you need to do – transfer the Bitcoin equivalent of 1450 USD to my Bitcoin account
(that is rather a simple process, which you can check out online in case if you don’t know how to do that).
Below is my bitcoin account information (Bitcoin wallet): 18spbm7ZkFBtuNK9hAE32ktGwvRdV77S7K
Once the required amount is transferred to my account, I will proceed with deleting all those videos and disappear from your life once and for all.
Kindly ensure you complete the abovementioned transfer within 50 hours (2 days +).
I will receive a notification right after you open this email, hence the countdown will start.
Trust me, I am very careful, calculative and never make mistakes.
If I discover that you shared this message with others, I will straight away proceed with making your private videos public.
Good luck!
How the scam works
When you get an unexpected email with the subject “Your personal data has leaked due to suspected harmful activities“, it can be really shocking 🚨. This feeling is especially strong if the email starts off with scary or threatening language meant to catch you off guard. You might wonder, “How do they know so much about me?” But in reality, these scammers probably don’t have your personal information; they’re just trying to scare you into doing what they want.
The email will likely have fake threats, claiming they’ve recorded you in embarrassing videos 🎥. They make the message sound confusing and scary on purpose, to make you panic: “Is this really happening?”
Then, they might say they’ve used advanced technology to hack into your devices, saying they have total access to your and your contacts’ digital lives 💻. The fact that they don’t show any real proof is a clear sign this is a scam 🚩. They’re playing on your fear of technology to scare you, not actually hacking anything.
Finally, they’ll ask for money 💰. They demand payment in Bitcoin, because it’s hard to trace. They try to make you feel like you have to pay right away. But even if you do pay, it doesn’t mean you’re safe and they might come back for more.
As you think about the email, you might wonder, “Am I really in danger?” or “Can this person actually do what they say?” 🕵️♂️ Usually, these threats are just meant to scare you, not real cyber threats.
What should you do? It’s best not to reply to the scammer or give them any money. Instead, focus on your online security: change your passwords, check your devices for real threats, and think about telling the authorities if the email includes threats or demands for money 🔐. This situation reminds us to always be careful and take steps to protect ourselves online.
To sum up, this scam tries to make you scared and rushed. If you get an email like this, don’t talk to the scammer and don’t send any money. Just delete the email. And make sure your computer has good antivirus software and you use strong, unique passwords for all your accounts to avoid scams like this.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
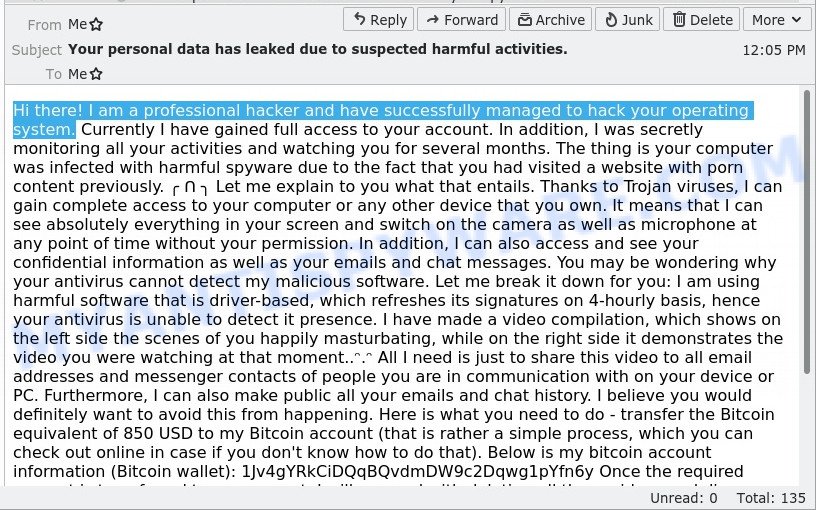
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
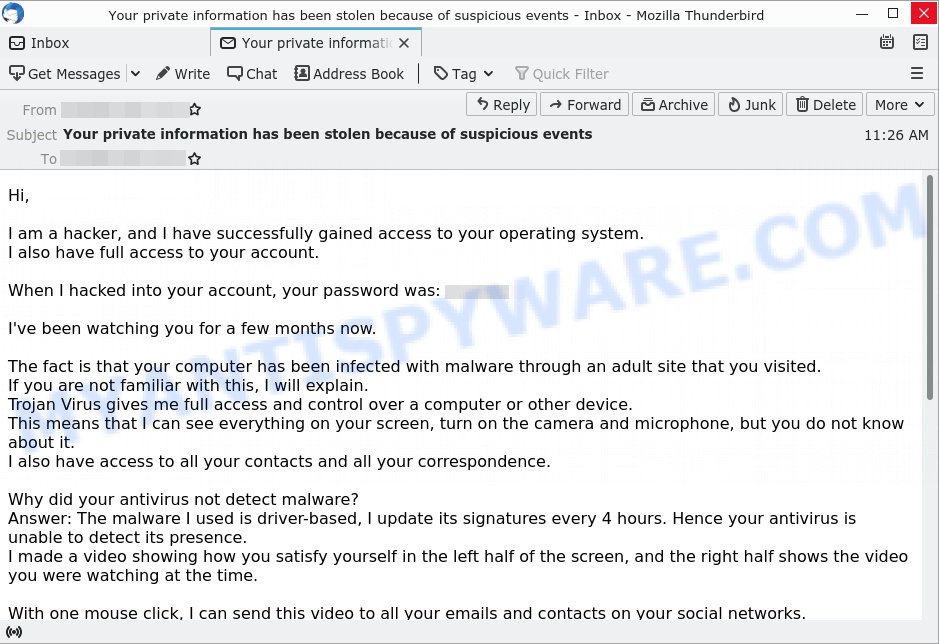
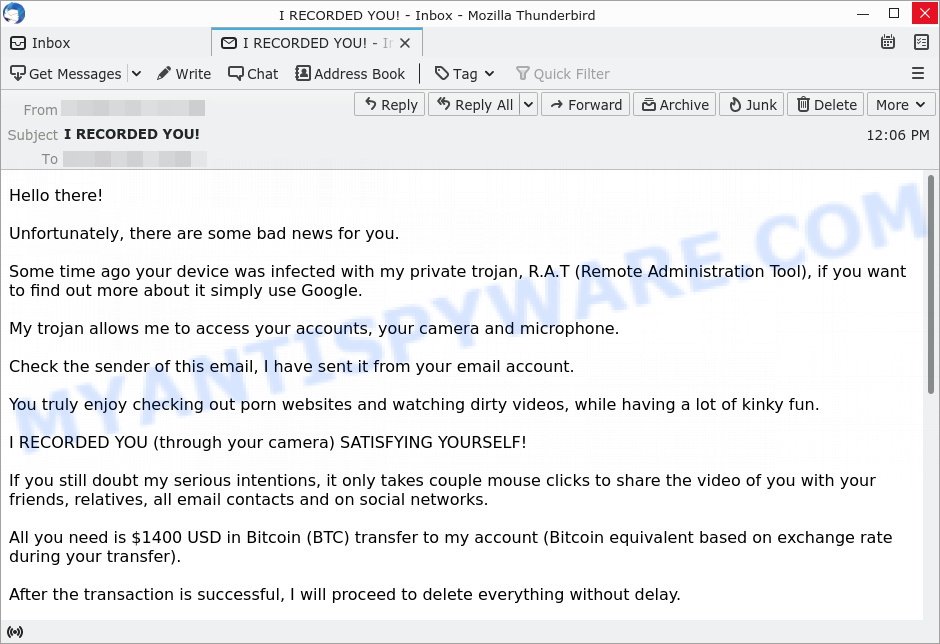
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “Your personal data has leaked” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | ‘Your personal data has leaked due to suspected harmful activities.’ Email Scam |
| Type | Phishing/Sextortion |
| Email Subject | Your personal data has leaked due to suspected harmful activities. |
| Ransom amount | $1450 USD (in Bitcoin equivalent) |
| Bitcoin Address | 1LWRhKpawKGeRjxTxGyUjK4tzaAsmG8KSm, 18cHDBUwV1WQMc2GKfdp8viEgmDpExaPT6, 1JuQpPQjYcpuTugMh4RJ5R7YPQCqjzuyh3, 1KZnEyumPFBVNK7jdedYL5XwaCLNW3G5Ty, 14MRXnsQhQ7LQSfKPMsESdJsEPFDyMCmMg, 1CHVFbjh2KjUa6HhZEMcZK8sYHsA61L9y1, 18spbm7ZkFBtuNK9hAE32ktGwvRdV77S7K |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The “Your personal data has leaked due to suspected harmful activities” email is a typical example of a sextortion scam, aiming to scare and trick you into sending money. These emails make scary threats and ask for payment, usually in Bitcoin, pretending to protect your reputation. But don’t be fooled – these threats are fake, meant to make you panic.
Key Point: Don’t interact with these emails. The best thing to do is to ignore them and focus on keeping your online accounts safe. 🛡️💻
Stay alert and think carefully; an email that immediately frightens you or seems overly complex is likely a scam. 🤔