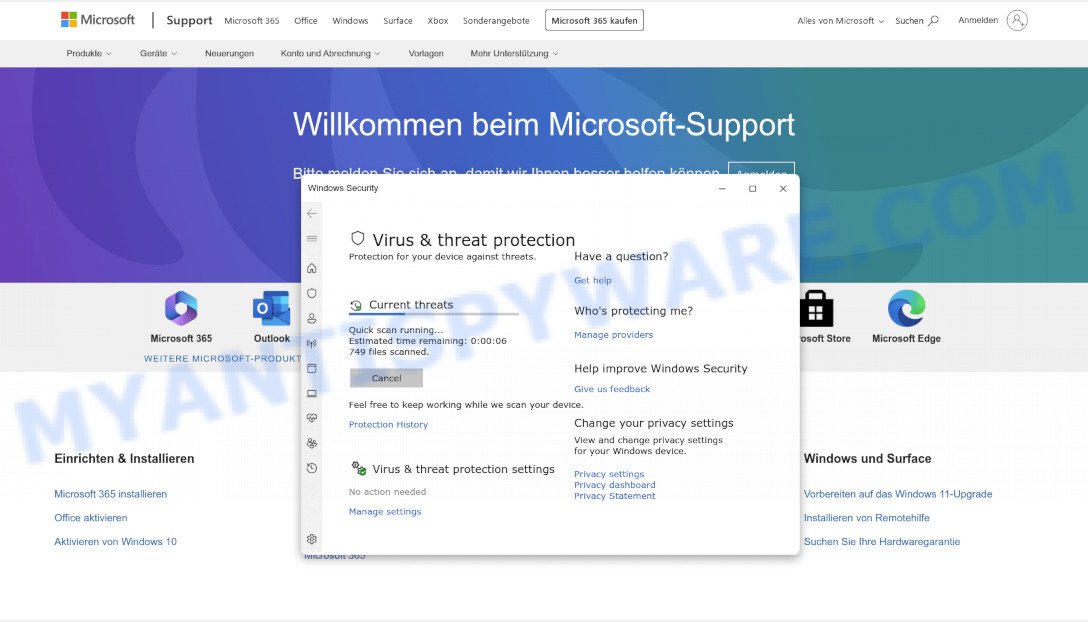
Search-good.com is a fake search engine that can be installed on a user’s browser through a malicious Chrome extension named “Apps”. Once installed, the hijacker alters the user’s browser settings without their knowledge or consent, including modifying their default search engine and homepage.
In this article, we’ll take a closer look at Search-good.com, how it works, and what you can do to remove it from your browser.
QUICK LINKS
- How Did the Search-good.com Hijacker Get Into Your Browser?
- How to remove Search-good.com
- What to Do After Removing the Search-good.com Hijacker
Search-good.com in detail
At the time of research, Search-good.com was observed to redirect user searches to Yahoo (search.yahoo.com) and Bing (bing.com). The exact search engine to which the hijacker redirects may vary depending on various factors such as the user’s location or IP address. However, it is important to note that Search-good.com does not generate legitimate search results and may lead users to potentially malicious or scam websites.
Furthermore, Search-good.com may display intrusive and harmful advertisements, which are designed to deceive users into purchasing questionable products or services. It is important to keep in mind that Search-good.com is not a legitimate search engine, and its primary goal is to generate revenue for its creators by promoting shady products and services while collecting users’ personal information.
Search-good.com is a fake search engine that poses a significant security risk to users. It is usually distributed through malicious browser extensions or through deceptive tactics such as fake software updates, spam emails, or other similar methods. Once installed, it alters the user’s browser settings, redirecting their web traffic to specific sites that may include harmful or fraudulent pages. Below are some examples of deceptive, misleading, or malicious pages:
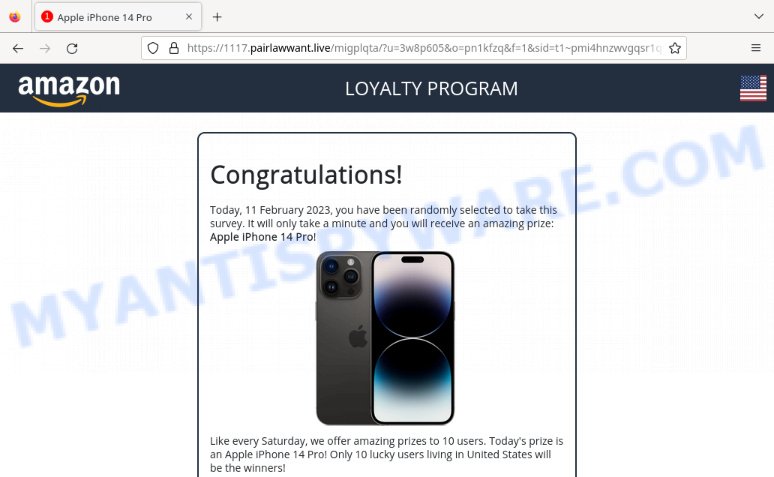
- Your Captcha Now Virus Amazon LOYALTY PROGRAM Scam
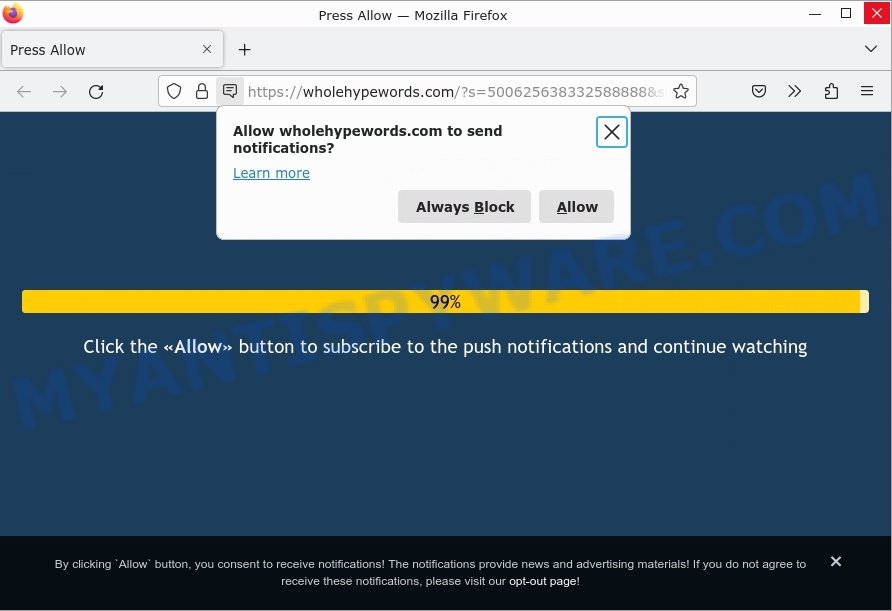
- Wholehypewords.com Press Allow Scam
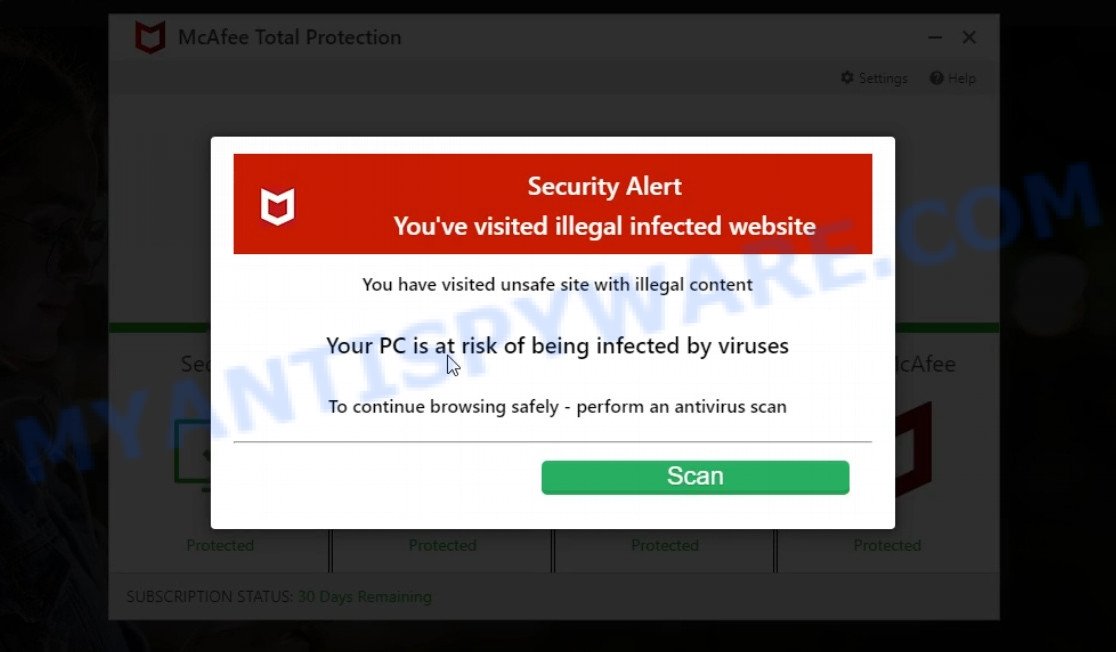
- Validityprotocol.com McAfee Scam
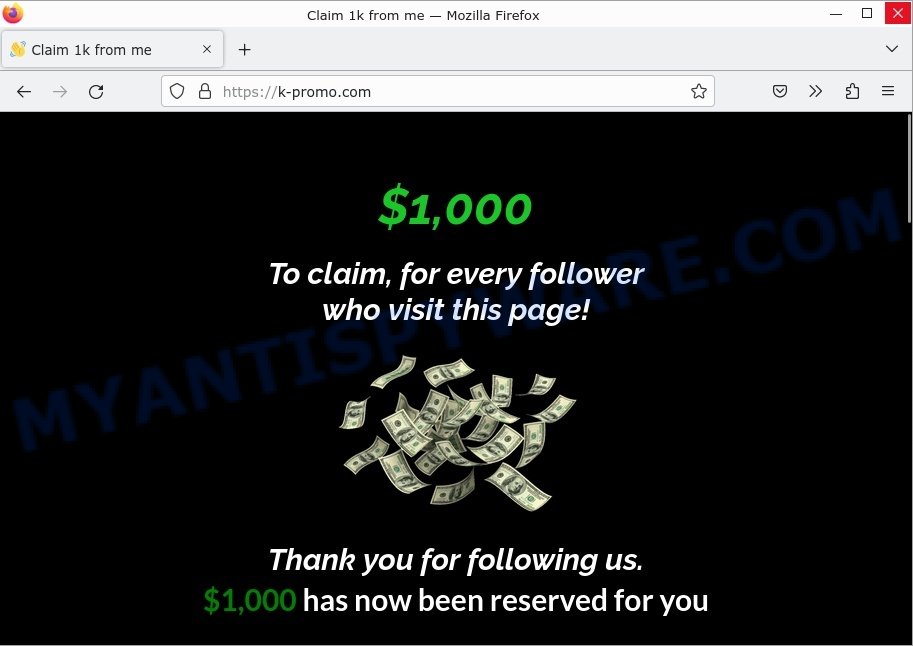
- Mr Beast Giveaway scam k-promo.com
- Showtaggers.com Netflix Tag Career Scam
- “Windows Firewall Protection Alert” Pop-Up Scam
In addition, the Search-good.com hijacker can use the Managed by your organization feature in the Chrome browser to prevent users from changing their browser settings, such as the default search engine or homepage. This feature is designed for use by organizations to manage and enforce policies on Chrome browser settings for their employees, but hijackers can use it to maintain control over the user’s browser and prevent them from removing the hijacker.
Overall, the Search-good.com hijacker poses a serious security risk to users, as it can compromise their sensitive data and make it difficult to remove from their browser. It is recommended to take immediate action to remove the hijacker, such as using anti-malware software or manually removing any suspicious extensions or programs from the browser.
How Did the Search-good.com Hijacker Get Into Your Browser?
Search-good.com is usually distributed through malicious browser extensions or through deceptive tactics such as fake software updates, spam emails, or other similar methods. In many cases, users unknowingly download and install browser hijackers alongside free software from untrusted sources.
For example, the Search-good.com hijacker can be distributed through a “Your File Is Ready To Download” Scam virus, which tricks users into downloading and installing a malware-ridden file. Additionally, this hijacker can be installed through a malicious “Apps” extension, which is designed to mimic a system Chrome extension.
Here’s an example of a “Your File Is Ready To Download” Scam (Virus):
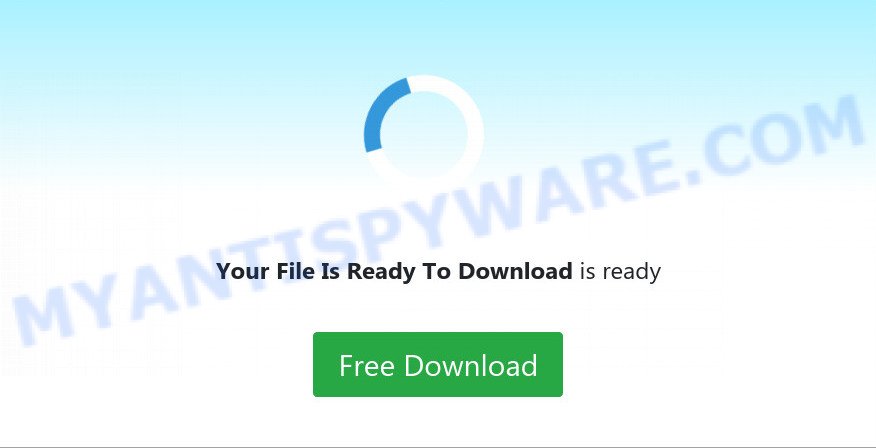
There are several other ways that the Search-good.com hijacker can get into your browser. Here are some possible methods:
- Browser hijackers can be bundled with free software that you download from the internet. When you install the free software, Search-good.com may be installed as well, without your knowledge or consent.
- Cybercriminals can also spread browser hijackerss through spam emails. The emails may contain attachments that, when opened, can install the hijacker onto your computer.
- Some websites may host malicious scripts that can install browser hijackers onto your computer. These websites may be disguised as legitimate websites, such as online shopping sites, gaming sites, or social networking sites.
- Cybercriminals can also create fake software update notifications that appear legitimate. When you click on the notification and download the update, a hijacker may be installed onto your computer along with the supposed update.
It is important to be cautious when downloading and installing software from the internet, opening email attachments, and clicking on suspicious links. Always use reputable sources for software downloads and keep your anti-virus and anti-malware software up to date to help protect against potential threats.
Threat Summary
| Name | Search-good.com, “Search Good”, “Search-good.com redirect”, “Search-good.com virus” |
| Type | browser hijacker, home page hijacker, PUP, search provider hijacker, redirect virus |
| Affected Browser Settings | home page, newtab page URL, default search engine |
| Distribution | bundled software, spam email attachments, malicious websites, fake software updates |
| Damage | Privacy invasion: browser hijackers can collect and transmit personal information, such as search queries, browsing history, and login credentials; security risks: browser hijackers can expose the computer to other forms of malware; ad revenue generation: browser hijackers can display unwanted pop-up ads; performance degradation: browser hijackers can cause the affected web browser to become slow; altered search results: browser hijackers can alter search results to display sponsored or unwanted websites. |
| Symptoms | Changes to the homepage: browser hijackers may change the homepage of the affected web browser; changes to the default search engine: browser hijackers may change the default search engine of the affected web browser; new toolbars or extensions: browser hijacker may install new toolbars or extensions; pop-up ads: browser hijackers may cause the display of unwanted pop-up ads while the user is browsing the web; redirection to unfamiliar and scam websites; slow or unresponsive web browser. |
| Removal | If you experience any of these symptoms above, it is a sign that your web browser has been hijacked. To remove the hijacker, Search-good.com removal guide |
How to remove Search-good.com from Windows 11 (10, 8, 7, XP)
To remove Search-good.com from your browser, go to the browser’s extensions or add-ons settings and uninstall any suspicious extensions. Then, change the default search engine in the browser’s settings to a trusted source such as Google or Bing. If the fake search engine is still present, reset the browser to its default settings. Additionally, it’s important to scan your computer for malware using an antivirus program.
If you have any questions or need help, write a comment below. Some steps will require you to restart your device or exit this web page. So, read this guide carefully and then bookmark this page or open it on your smartphone for future reference.
To remove Search-good.com, perform the steps below:
- Uninstall any suspicious programs
- Remove the Search-good.com extension
- Scan your computer for malware
Read this section to know how to manually remove the Search-good.com hijacker. Even if the step-by-step guide does not work for you, there are several free removers below which can easily handle such hijackers.
Uninstall any suspicious programs
The first step is to check your computer for any suspicious programs or extensions and remove them. To do this, go to the Control Panel (on Windows) or Applications (on Mac) and uninstall any programs that you don’t recognize or that you think may be associated with the Search-good.com hijacker.
|
|
|
|
Remove Search-good.com from Google Chrome
Open the Google Chrome menu by clicking on the button in the form of three horizontal dotes (![]() ). It will display the drop-down menu. Choose More Tools, then click Extensions. You can also type chrome://extensions into Chrome’s address bar.
). It will display the drop-down menu. Choose More Tools, then click Extensions. You can also type chrome://extensions into Chrome’s address bar.
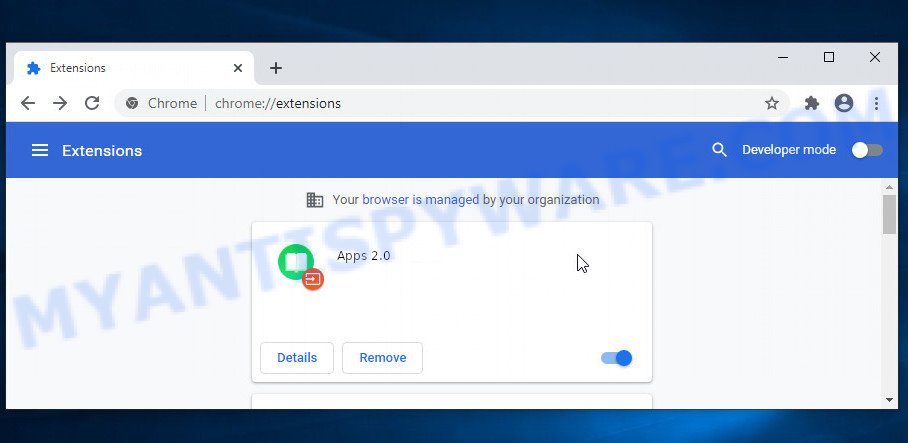
Examine your list of installed extensions and find any that you don’t recognize, you know are malicious or simply want to remove. Click the “Remove” button below the extensions you want to remove. In the pop-up that comes up, click “Remove” once again. The extension box and icon should disappear from the screen.

If the “Remove” option is not available as the extension is being detected as “Installed by administrator” or “Managed by your organization” then the easiest way to fix this is to follow the instructions: Remove Google Chrome extensions installed by enterprise policy, Chrome Managed by your organization malware removal guide.
To completely remove any changes made by the Search-good.com hijacker, reset your browser settings to their default values. To do this, go to the Chrome main menu again, click “Settings”. Click Reset settings and then “Restore settings to their original defaults”.
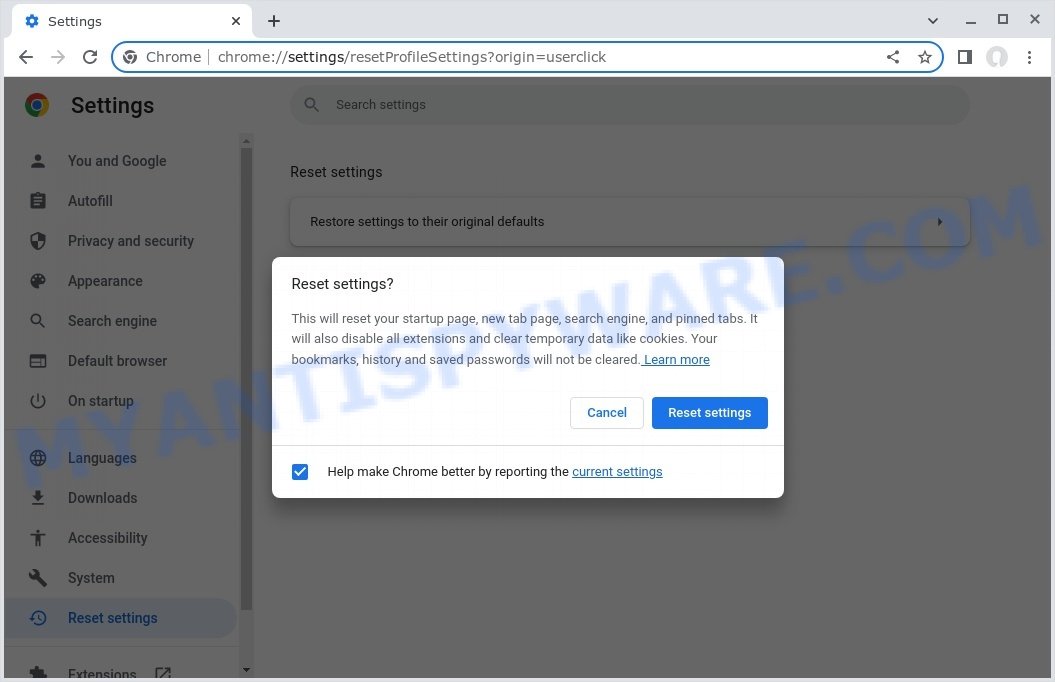
Confirm your action, click the “Reset settings” button.
Scan your computer for malware
It is possible that the Search-good.com hijacker came bundled with other malware or viruses. To ensure that your computer is clean, run a full system scan with a reputable antivirus software.
You can automatically get rid of the browser hijacker with MalwareBytes. Malwarebytes is a reputable anti-malware software that is commonly used to remove various types of malware, including browser hijackers like Search-good.com.
- Download Malwarebytes by clicking on the link below. Save it on your Windows desktop.
Malwarebytes Anti-malware
327049 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- Once the download is done, close all applications and windows on your personal computer. Open a folder in which you saved it. Double-click on the icon that’s named MBsetup.
- Choose “Personal computer” option and press Install button. Follow the prompts.
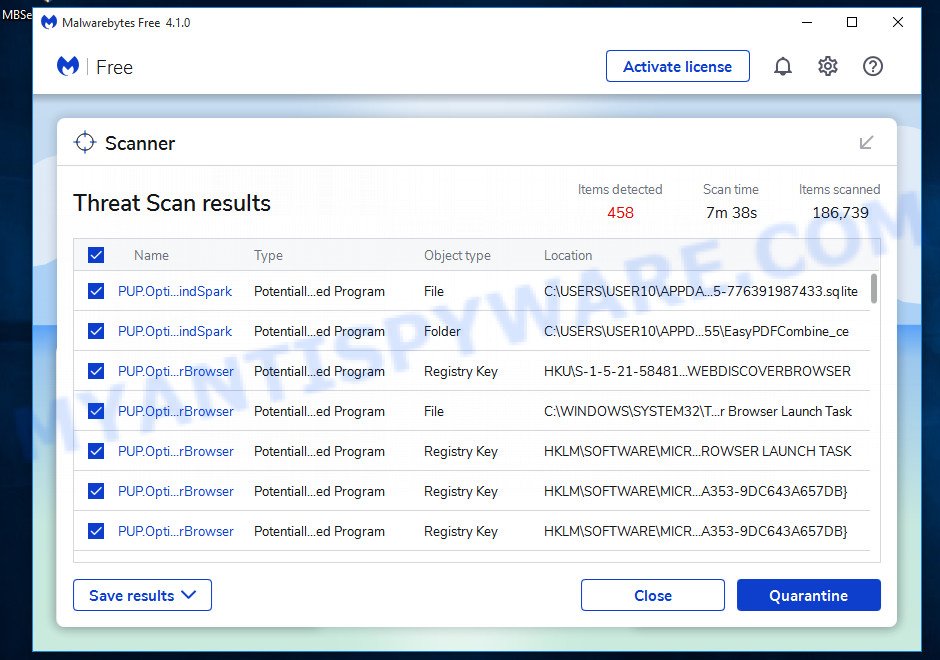
- Once installation is finished, scan your computer. Run a full scan of your computer to detect and remove any browser hijackers and other forms of malware. The scan may take several minutes to complete, depending on the size of your hard drive and the speed of your computer.
- Remove detected threats. If the scan finds any threats, click Quarantine to remove them. The software will automatically remove the browser hijacker and any associated malware. After the removal process is complete, restart your computer to ensure that any changes made by the hijacker are fully removed.
The following video demonstrates how to remove hijackers, adware and other malware with MalwareBytes.
What to Do After Removing the Search-good.com Hijacker
After successfully removing the Search-good.com hijacker, there are a few important steps you should take to ensure that your browser and computer are fully secure:
- It’s important to change your browser settings back to your preferred search engine and homepage. Make sure that Search-good.com is completely removed from your browser’s settings and that it cannot reappear.
- Use a reputable anti-malware program like Malwarebytes to scan your computer for any remaining malware or potentially unwanted programs (PUPs). This can help ensure that there are no hidden threats or malicious files on your computer.
- Make sure that your browser and operating system are up-to-date with the latest security patches and updates. This can help prevent future security issues and keep your system protected.
- To avoid getting infected with similar malware in the future, be cautious of downloads and only download from reputable sources. Avoid clicking on suspicious links or downloading attachments from unknown sources.
Finish Words
To conclude, the Search-good.com hijacker is a dangerous threat to your online security and privacy. It can be installed on your browser without your knowledge or consent, and can cause a number of problems including intrusive advertisements, browser redirects, and the theft of your personal data. It’s important to take action to remove this hijacker from your browser as soon as possible.
If you suspect that your browser has been hijacked by Search-good.com or any other similar threat, follow the steps outlined above to remove it. Be sure to also take steps to protect yourself from future threats by using reputable antivirus and anti-malware software, keeping your browser and other software up to date, and avoiding suspicious websites and downloads.
Remember, staying vigilant and taking proactive measures to protect your online security is key to staying safe in today’s digital world. By taking the necessary steps to protect yourself, you can browse the web with confidence and peace of mind.