Beware! A new email scam called “Got You”, “You Got Owned” is targeting unsuspecting individuals, and you could be the next victim. This deceitful email, claiming to be from well-known companies like QuickBooks and Coinbase, is filled with alarming threats. The scammer asserts that they’ve infected your computer with a sneaky tool that lets them control everything, including your camera and microphone. They even go as far as saying they have private pictures and videos that they’ll expose unless you pay $400 in Bitcoin within three days.
Don’t panic just yet! In this article, we’ll break down this scam email, reveal the tricks used by scammers, and give you practical tips to keep yourself safe. Stay informed and take action! Read on to uncover the truth about the “Got You, You Got Owned” scam email and shield yourself from its harmful consequences.
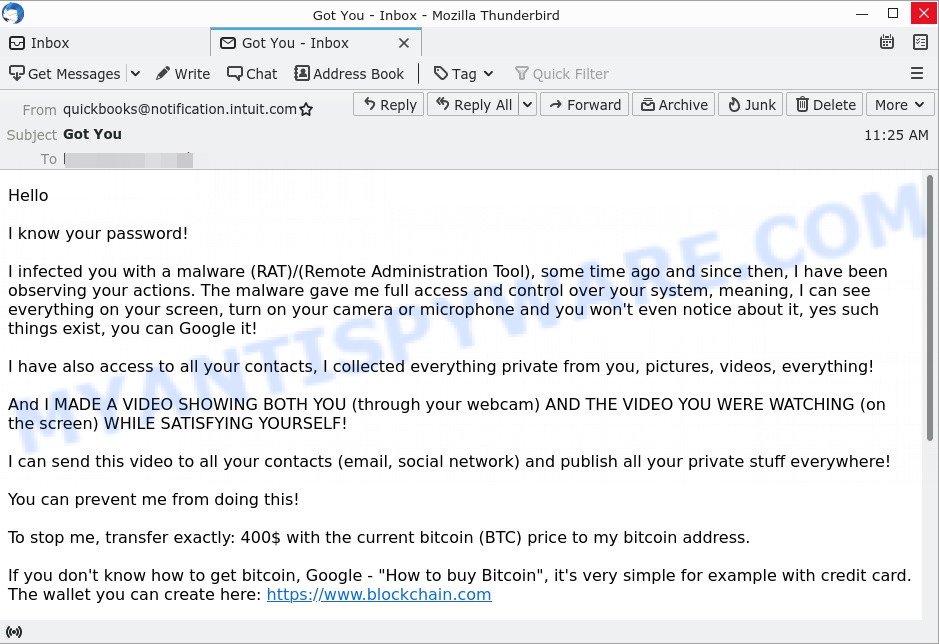
Here’s an example of the “Got You”, “You Got Owned” scam email:
QUICK LINKS
Is this a scam email?
Yes, without a doubt, the “Got You, You Got Owned” email is a classic example of a scam designed to exploit fear and manipulate individuals. Scammers employ deceptive tactics, making false claims about malware infections, unauthorized access to personal information, and threats of exposing compromising material. However, it’s important to recognize the common signs of a scam: unsolicited emails, generic sender addresses, poor grammar and spelling, anonymous threats, and requests for payment in Bitcoin. If you receive this email, do not engage with the scammers, respond, or provide personal information. Report it as spam and seek guidance from authorities. Stay informed and stay safe.
How the scam works
The “Got You, You Got Owned” email scam is a deceptive scheme designed to exploit people’s fears and coerce them into paying money to scammers. Here’s how this scam unfolds:
The scammers initiate contact by sending out mass emails to random individuals, hoping to reach someone who will fall for their tricks. These emails often use subject lines that grab attention or create a sense of urgency, while the sender addresses might impersonate well-known companies or even use personal contacts.
Once you open the email, it claims that your computer has been infected with a Remote Administration Tool (RAT) that allows the scammers to take complete control over your system. They assert that they can see everything on your screen, activate your camera and microphone without your knowledge, and have collected private files, photos, videos, and sensitive information about you.
To escalate the fear and pressure, the scammers threaten to expose this alleged compromising material unless you comply with their demands. They demand a ransom payment, often in Bitcoin due to its anonymity, and provide instructions on how to obtain the required amount. They usually specify a deadline, typically three days, within which the payment must be made, or else they claim they will distribute the material to your contacts.
Throughout the email, the scammers use intimidation tactics, emphasizing the importance of secrecy and warning you not to share the email with anyone. They may mention having access to all your contacts, attempting to make you believe that the consequences of non-compliance will be severe.
It’s crucial to remember that these scammers are trying to manipulate and deceive you. The claims they make are usually false, and they often send these emails to random individuals without any real evidence of the alleged compromising material.
The scam email read as follows:
Hello
I know your password!
I infected you with a malware (RAT)/(Remote Administration Tool), some time ago and since then, I have been observing your actions. The malware gave me full access and control over your system, meaning, I can see everything on your screen, turn on your camera or microphone and you won’t even notice about it, yes such things exist, you can Google it!
I have also access to all your contacts, I collected everything private from you, pictures, videos, everything!
And I MADE A VIDEO SHOWING BOTH YOU (through your webcam) AND THE VIDEO YOU WERE WATCHING (on the screen) WHILE SATISFYING YOURSELF!
I can send this video to all your contacts (email, social network) and publish all your private stuff everywhere!
You can prevent me from doing this!
To stop me, transfer exactly: 400$ with the current bitcoin (BTC) price to my bitcoin address.
If you don’t know how to get bitcoin, Google – “How to buy Bitcoin”, it’s very simple for example with credit card. The wallet you can create here: https://www.blockchain.com
My bitcoin address is: bc1qn8lf2w0v24uvk7x7epmmftuqyhtlkvf44ng6td
Copy and paste my address – it’s (CASE-sensitive).
You know this all isn’t a joke, you got the proof above!
I think it’s a very good price compared to the damage and hell it can bring into your life!
After receiving the payment, I will delete everything from you and you can life your live in peace like before. I give you 3 days to get the bitcoins!
Don’t share this email with anyone, this should stay our little secret!
If you receive an email like this, do not engage with the scammer and do not send any money. Instead, delete the email and report it to the relevant authorities. It is also important to ensure that your computer has up-to-date anti-virus software and that you use strong, unique passwords for all of your accounts to reduce the likelihood of falling victim to scams like this. Stay informed, stay vigilant, and protect yourself from falling victim to scams like the “Got You, You Got Owned” email.
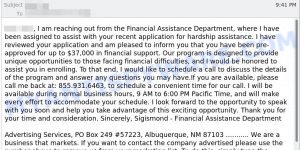
Examples of such scams
Scammers are constantly finding new ways to exploit individuals, using various tactics to trick and manipulate their targets. Understanding the different types of scams circulating can help us stay vigilant and protect ourselves from falling victim. In this section, we will explore a range of scams similar to the “Got You, You Got Owned” email scam, highlighting their methods and potential consequences.
By examining these examples, we can better recognize the warning signs and arm ourselves with knowledge to avoid becoming victims of fraudulent schemes. Take a closer look at the following scams: Financial Hardship Department Scam, Geek Squad Email Scam, and USPS Redelivery Scam, and let’s learn how to safeguard ourselves from their deceitful tactics. Remember, knowledge is power.
- Geek Squad Email Scam (May 2023)
- Your account is hacked. Your data is stolen. Email Scam
- Reconfirm Shipping Documents Scam email
- Cash Settlement Awarded Email Scam
- Financial Assistance Department Email Scam
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Scam Email
If you receive an email with the subject line “Got You” do not panic. The scammers are trying to intimidate you, but remember that their threats are empty and baseless. Here are some steps you can take:
- Do not panic! While these emails are designed to instill fear and panic in the victim, it is important to stay calm and take a measured response to the situation. Remember that the email is fake, and that the attacker does not have access to the sensitive information they are threatening to release
- Do not respond or engage with the scammer in any way.
- Do not click on any links or attachments in the email as they may contain malware or viruses that could harm your computer.
- Mark the email as spam or phishing and delete it immediately.
- Report the scam to the FTC at https://www.ftc.gov/ and relevant authorities, such as your email provider or local law enforcement, to help prevent others from falling victim to it.
- Check your online accounts and make sure that your passwords are strong and unique.
- Take steps to secure your online accounts and personal information, such as enabling two-factor authentication.
- Stay informed about current scams and the tactics used by attackers, so that you can better recognize and avoid them in the future.
- If you suspect that your computer is infected with spyware or malware, or if you clicked on a link in the scam email, it’s always a good idea to scan your computer for viruses. Use a reputable anti-virus program to scan your computer thoroughly, and make sure it’s up-to-date with the latest virus definitions.
Remember, the scammers are counting on you to be scared and make impulsive decisions. Don’t fall for their tricks and take the necessary steps to protect yourself.
Threat Summary
| Name | Got You, You Got Owned SCAM |
| Type | Sextortion scam, hacker email scam |
| Email subject | Got You; You Got Owned |
| Sender | quickbooks@notification.intuit.com, coinbase@pro.space, christenson@my.email |
| Ransom amount | $400 (in Bitcoin equivalent) |
| Bitcoin Address | 1D9E953D6A38pH6EhnjzZXJVHXfEu13iCF, bc1qn8lf2w0v24uvk7x7epmmftuqyhtlkvf44ng6td |
| Fake Claims | Alleged malware infection and remote access to victim’s system; Possession of compromising material; Threats to expose the material to contacts. |
| Disguise | Impersonating reputable companies or using personal contact information. |
| Damage | Psychological distress, potential financial loss |
| Distribution | Mass-sent emails to random individuals. |
| Tactics | False claims of malware infections; Varying ransom amounts and Bitcoin addresses. |
| Variations | Different subject lines, variations in ransom amount and Bitcoin address |
| Reporting Info | Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
Scam emails, such as the “Got You, You Got Owned” email scam, are a constant threat in our increasingly digital world. These deceptive tactics aim to exploit our fears, emotions, and vulnerabilities for the financial gain of the scammers. However, by staying informed and exercising caution, we can protect ourselves from falling victim to these schemes.
Throughout this article, we’ve explored how the “Got You, You Got Owned” scam operates, the potential consequences it poses, and ways to identify and prevent such scams. We’ve also discussed examples of other common scams that employ similar tactics, highlighting the importance of being aware of the diverse methods scammers employ.
It’s crucial to remember that reputable companies will never request personal information, financial details, or ransom payments through unsolicited emails. By being skeptical, verifying the authenticity of senders, and following prevention tips, we can significantly reduce our risk of becoming victims.
As individuals, we have the power to protect ourselves and others by staying informed, sharing knowledge, and reporting suspicious activities. By doing so, we contribute to creating a safer digital environment for everyone.
Remember, if you receive a suspicious email like the “Got You, You Got Owned” scam, don’t panic, engage with the scammers, or pay any ransom. Report the email as spam or phishing, and consider reaching out to local authorities or cybercrime units to help combat these scams.
Together, let’s stay vigilant, educate ourselves and our communities, and stay one step ahead of scammers in the ongoing battle against fraud and deception. By being informed and proactive, we can navigate the digital landscape with confidence and security.












Since they want payment in Bitcoin, the scammer has no idea who has paid them because when someone sends Bitcoin to a Bitcoin address the only information provided is the amount and the seender’s address, no personal information is included.
Also that Bitcoin address and any of it’s transactions can be viewed and unfortunately there are people that paid the scammers.
Again by viewing the address on blockchain.com there is no personal information for the addresses that sent the bitcoin.