It pops into your inbox: an email claiming a hacker has control of your computer, and worse, they’ve filmed you. This intimidating message, often accompanied by an old password of yours, demands Bitcoin payment to keep the supposed video under wraps. Called the “Your private information has been stolen” scam, it’s successfully frightened countless individuals into paying large sums of money. But how real are these threats? And what should you do if you receive one of these chilling emails? Read on to get the full breakdown and learn how to protect yourself.
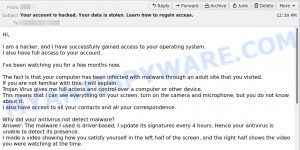
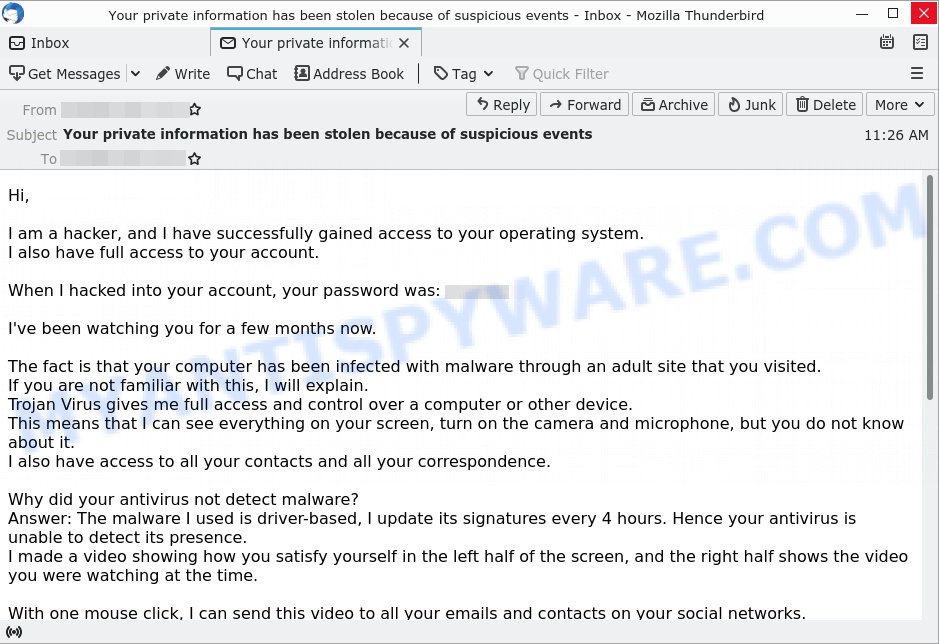
Here’s an example of the “Your private information has been stolen because of suspicious events” email:
QUICK LINKS
- Is this a scam email?
- How the scam works
- Should you pay
- What to Do if You Receive the Email
- The Latest Update in the Scam
Is this a scam email?
Absolutely. The “Your private information has been stolen” email is a textbook example of a sextortion scam. While it may seem alarming—especially when the message includes a password you once used or are currently using—the intention is purely to instill fear and urgency.

Let’s break down the red flags:
- Generic Language: The email is often vague about the supposed evidence they have, relying on your fear to fill in the blanks. They don’t provide specifics because they don’t actually have any genuine information.
- Urgent Deadlines: The scammer’s insistence on a tight deadline, like the mentioned 50 hours, is a tactic to push you to act without thinking or seeking advice.
- Bitcoin Payment: They ask for payment in Bitcoin, a decentralized and relatively anonymous digital currency, because it’s harder to trace than traditional payment methods.
- Untrackable Claims: The assertion that the email or Bitcoin address can’t be tracked is misleading. While it’s true that it might be challenging to track them, it’s not impossible. This claim is just another scare tactic.
- Lack of Real Evidence: Think about it—if they had genuine compromising material, they would offer undeniable proof rather than generic claims.
If you ever receive such an email or one with similar undertones, it’s crucial to remember not to panic, not to pay, and to recognize the hallmarks of a scam. Understanding the signs and staying informed are your best defenses against these digital predators.
How the scam works
The “Your private information has been stolen” email scam is engineered to exploit our deepest fears about personal privacy breaches in an age dominated by digital footprints. Here’s a dive into the anatomy of this deceit:
The email starts with a shock factor, claiming unauthorized access to the recipient’s operating system and account. This is designed to immediately grab attention and incite anxiety. By then revealing an actual password—often one that might have been leaked in past data breaches—the scammer crafts an illusion of credibility. For someone unaware of data breaches, seeing a familiar password can be deeply unsettling.
Next, the scam narrative delves into espionage-like tales of months-long surveillance, asserting that malware has been secretly installed on the victim’s computer. They claim this malware originated from an adult site, attempting to capitalize on potential feelings of guilt or embarrassment. With the stage set, they introduce the threat: a video of the recipient, juxtaposed with the content they were supposedly viewing.
To add a sense of immediacy and pressure, the scammer sets a countdown, pushing the recipient to make hasty decisions. The demanded ransom is typically in Bitcoin, as its semi-anonymous nature can make tracing transactions more challenging. The scammer rounds off by claiming infallibility, asserting that their methods are untraceable and that any attempt to outsmart or expose them would lead to immediate public shaming.
Throughout the email, the scammer’s aim is to weave a narrative so daunting that the victim feels trapped, making payment seem like the only viable escape. But in reality, this entire scenario is a fabrication, a mirage constructed to extract money from those who might be too afraid to question its authenticity.
The email read as follows:
Subject: Your private information has been stolen because of suspicious events
Hi,I am a hacker, and I have successfully gained access to your operating system.
I also have full access to your account.When I hacked into your account, your password was: xxxxxxx
I’ve been watching you for a few months now.
The fact is that your computer has been infected with malware through an adult site that you visited.
If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.
I also have access to all your contacts and all your correspondence.Why did your antivirus not detect malware?
Answer: The malware I used is driver-based, I update its signatures every 4 hours. Hence your antivirus is unable to detect its presence.
I made a video showing how you satisfy yourself in the left half of the screen, and the right half shows the video you were watching at the time.With one mouse click, I can send this video to all your emails and contacts on your social networks.
I can also make public all your e-mail correspondence and chat history on the messengers that you use.If you don’t want this to happen, transfer $950 in Bitcoin equivalent to my Bitcoin address (if you do not know how to do this, just search “buy bitcoin” on Google).
My Bitcoin address (BTC Wallet) is: 12FvRPR4s9ziuGW4CveDGD5oCro46PPsa6
After confirming your payment, I will delete the video immediately, and that’s it. You will never hear from me again.
I will give you 50 hours (more than 2 days) to pay. I will get a notice, when you open this email, and the timer will start.
Filing a complaint somewhere does not make sense because this email cannot be tracked like my Bitcoin address.I never make any mistakes.
If I find that you have shared this message with someone else, the video will be immediately distributed.Best regards!
If you receive an email like this, do not engage with the scammer and do not send any money. Instead, delete the email and report it to the relevant authorities. It is also important to ensure that your computer has up-to-date anti-virus software and that you use strong, unique passwords for all of your accounts to reduce the likelihood of falling victim to scams like this. Stay informed, stay vigilant, and protect yourself from falling victim to scams like the “Your Private Information has been Stolen” email.
Examples of such scams
The “Your private information has been stolen” email scam is just one of the many deceptive schemes that prey on individuals’ fears and exploit their privacy concerns. Unfortunately, this type of scam is not unique, and there are various similar scams circulating online.
By examining these examples, we can better recognize the warning signs and arm ourselves with knowledge to avoid becoming victims of fraudulent schemes. Take a closer look at the following scams: ‘Got You, You Got Owned’ Email Scam, Your Account is Hacked. Your Data is Stolen. Email Scam, I am a professional hacker EMAIL SCAM and let’s learn how to safeguard ourselves from their deceitful tactics. Remember, knowledge is power.
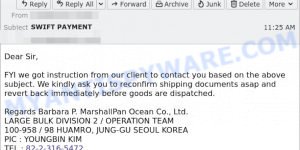
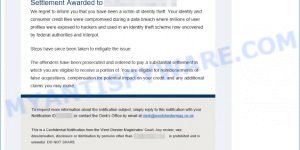
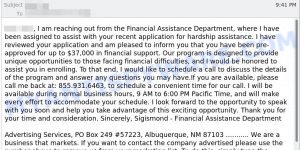
- Reconfirm Shipping Documents Scam email
- Cash Settlement Awarded Email Scam
- Financial Assistance Department Email Scam
- Geek Squad Email Scam (May 2023)
- Your account is hacked. Your data is stolen. Email Scam
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “Your private information has been stolen” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | Your private information has been stolen SCAM |
| Type | Sextortion scam, hacker email scam |
| Email subject | Your private information has been stolen because of suspicious events |
| Ransom amount | $950, $750 (in Bitcoin equivalent) |
| Bitcoin Address | 12vxjNEg6i3L1kopjfoQ7YXAet1TGS6H5P, 12FvRPR4s9ziuGW4CveDGD5oCro46PPsa6, 15wQk4AHFCtWGyAzjsG9c947prqdeR2tGb, 1KC52sZYGPYsCRfNLo1N48K3Fb5nYhvW4i |
| Fake Claims | Alleged malware infection and remote access to victim’s system; Possession of compromising material; Threats to expose the material to contacts. |
| Disguise | Impersonation of a hacker. |
| Damage | Emotional distress, financial loss |
| Distribution | Email spamming, targeted phishing. |
| Tactics | Fear, urgency, manipulation, impersonation, intimidation. |
| Variations | Varying email subjects, sender names, and claims |
| Reporting Info | Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The “Your private information has been stolen because of suspicious events” email is more than just a nefarious attempt to extract money; it’s a stark reminder of the vulnerabilities many feel in our digital age. At its core, this scam thrives on the blend of real-life data breaches and the imagined worst-case scenarios of personal exposure. For those caught off guard by the sudden appearance of a familiar password and tales of covert surveillance, the impulse to resolve the issue quietly can be overwhelming.
However, knowledge remains the best defense. By understanding the mechanics behind this scam and recognizing its fabricated threats, individuals can confidently discard such messages and continue their online activities without fear. As with many things on the internet, a blend of skepticism and awareness proves invaluable in distinguishing between genuine threats and manipulative hoaxes.
Remember, if you receive a suspicious email like the “Your private information has been stolen” scam, don’t panic, engage with the scammers, or pay any ransom. Report the email as spam or phishing, and consider reaching out to local authorities or cybercrime units to help combat these scams.
The Latest Update in the Scam
The “Your Private Information has been Stolen” email scam has seen a new iteration. Here are the distinct changes:
- Introduction: Instead of an aggressive opening, the scammer opts for a more casual “Would like to introduce myself” line, posing as a “specialized hacker.”
- Ransom Amount: The demanded ransom is now 750 USD, different from the previously asked sum.
- Bitcoin Address: The payment address has changed to ’15wQk4AHFCtWGyAzjsG9c947prqdeR2tGb’.
- Narrative: The email details how the hacker allegedly spied on the victim’s activities, highlighting the acquisition of malware through an adult website visit. There’s also a direct mention of a video that supposedly juxtaposes the recipient’s personal activities with adult content they viewed.
The email read as follows:
Greetings!
Would like to introduce myself – I am a specialized hacker, and have succeeded in hacking your operating system.
At this moment, I have obtained a complete access to account of yours.
On top of that, I was also unnoticeably observing all your activities and spying on you for few past months.
It was possible because your computer was infected with malicious spyware,
which infiltrated your computer while you were visiting a website containing adult videos.Give me a few minutes to clarify how that affects you.
Because of Trojan viruses, I am now able to have an unrestricted access to your computer as well as any other devices owned by you.
In other words, I can see without any restrictions everything in your screen and even activate the camera together with microphone anytime I want,
and you won’t even know about that.
Moreover, I have complete access to confidential data of yours including emails, chat history etc.You may be rightfully puzzled how come your antivirus is not able to detect the harmful software of mine.
I don’t mind explaining that at all: my malicious software is driver-based; hence it refreshes its signatures every 4 hours,
which makes it impossible for your antivirus to identify it.I have come up with a video exposing the scenes of your passionate masturbation sessions on the left side,
whereas on the right side it shows the dirty videos you were watching during that time. `.`Trust me, it takes several mouse clicks to distribute this video to your entire email addresses list as well as messenger contacts on your PC or other devices.
Additionally, I can easily share all your emails as well as chat history to public too.I honestly think you would certainly like to abstain from letting that happen.
There is a solution for you in this case – perform 750 USD transfer in Bitcoin equivalent to Bitcoin account of mine
(it is really not difficult to do, and you can find online the step-by-step guide, if you have no idea about it).My bitcoin account details are below as follows (Bitcoin wallet): 15wQk4AHFCtWGyAzjsG9c947prqdeR2tGb
Once the aforementioned amount gets transferred to my account, I will straight away erase all those kinky videos and vanish from your life completely.
Please, settle this payment within 50 hours (2 days).
A notification will be sent to me right after this email gets opened, which will trigger the countdown.Believe me, I am very cautious, professional and never fail.
If I get to know about you sharing this message with anyone else, I will right away distribute your private videos to public.Best of luck!