Have you ever encountered an email that starts with a message like “Hi! Sadly, there are some bad news that you are about to hear” and not only claims to have taken over your devices but also seems to have been sent from your own email account, including a password you recognize? Don’t be alarmed—it’s a scam.
These fraudsters are exploiting known passwords, likely obtained from previous data breaches, to scare you into paying a ransom. They’re counting on the shock of seeing your password and the fear of personal exposure to force you into paying up. We’re here to explain how this tactic is nothing but a high-tech con. For a comprehensive breakdown of this scam and practical advice on how to handle such situations, read our detailed article. Stay informed and protect yourself from being exploited.
Here’s an example of the “Sadly, there are some bad news that you are about to hear” email:
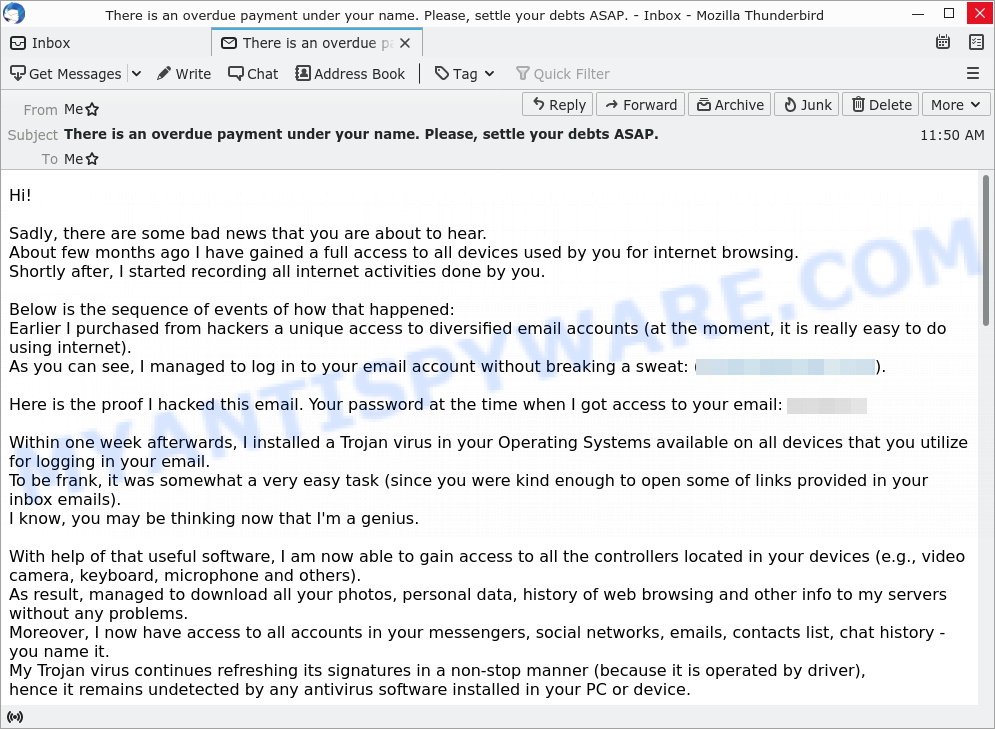
Table of Contents
Is this a scam email?
YES, this email claiming to have control over your personal devices is nothing but a scam, designed to create a sense of panic and urgency. The scammer relies on shock value, using details like a password from a past data breach to appear legitimate. They exploit fears about privacy invasion, demanding money in exchange for ‘protection’ that you actually don’t need because their claims are false.
Red Flags That Indicate a Scam:
- 📧 Email Spoofing: The fact that the email appears to come from your own email address is a major red flag. This technique, known as “spoofing”, is common among scammers. It’s designed to create instant credibility, but don’t be fooled—it’s just a facade.
- 🚨 Outdated Password Scare: Presenting an old or current password aims to rattle you. Scammers usually get these from publicly leaked databases from past breaches. It’s meant to lend authenticity to their claims, but it is not an indicator of a current threat.
- 🤥 No Proof Provided: While the email claims to have compromising videos, it fails to provide any tangible proof. Genuine breaches would likely be accompanied by actual evidence, which scammers don’t have.
- 🎥 Threats to Release Videos: The scammer’s threat to distribute videos to your contacts is designed to provoke immediate anxiety. However, this is a common intimidation technique, and if they had such material, they would likely show it to you to ‘prove’ their capability.
- 📝 Grammatical and Spelling Mistakes: Many scam emails contain noticeable language mistakes. This is often because scammers may not be native English speakers or because they are hastily put together without thorough proofreading.
In short, the email is a scam. Scammers are using your own email address to try to intimidate you, but this is just a tactic to make you worried enough to pay them. Do not engage or pay any money. Delete the email immediately, update your passwords, especially if you’ve used the same one for multiple accounts, and activate two-factor authentication where possible. Report the incident to your email provider and consider alerting the relevant cyber crime authorities in your country. Knowledge is power—stay informed and you’ll stay safe.
How the scam works
When you open your inbox and find an email that has your password and is full of threats, it’s normal to feel worried. You might ask yourself, “How did they get my email and password?” These details are often snatched up during data breaches and then sold in the shady corners of the internet.
The scam email will usually include vague threats about sharing personal videos or information. The sender doesn’t say where they got your details from, which might make you think, could this be real?
They then claim to have installed a virus on your devices, giving them full access to your data. Yet, they fail to provide any proof to support their claims, which is a classic sign of a scam.
The final move in their scheme is demanding a ransom. 💰 They’ll ask for a quick payment using Bitcoin, knowing that it’s hard to follow and almost impossible to get back. They’re betting on the fear factor to make you act fast, hoping you won’t have time to realize it’s all just a bluff.
The email read as follows:
There is an overdue payment under your name. Please, settle your debts ASAP.
Hi!
Sadly, there are some bad news that you are about to hear.
About few months ago I have gained a full access to all devices used by you for internet browsing.
Shortly after, I started recording all internet activities done by you.Below is the sequence of events of how that happened:
Earlier I purchased from hackers a unique access to diversified email accounts (at the moment, it is really easy to do using internet).
As you can see, I managed to log in to your email account without breaking a sweat: (xxxxxxxx).Here is the proof I hacked this email. Your password at the time when I got access to your email: xxxxxxxx
Within one week afterwards, I installed a Trojan virus in your Operating Systems available on all devices that you utilize for logging in your email.
To be frank, it was somewhat a very easy task (since you were kind enough to open some of links provided in your inbox emails).
I know, you may be thinking now that I’m a genius.With help of that useful software, I am now able to gain access to all the controllers located in your devices (e.g., video camera, keyboard, microphone and others).
As result, managed to download all your photos, personal data, history of web browsing and other info to my servers without any problems.
Moreover, I now have access to all accounts in your messengers, social networks, emails, contacts list, chat history – you name it.
My Trojan virus continues refreshing its signatures in a non-stop manner (because it is operated by driver),
hence it remains undetected by any antivirus software installed in your PC or device.So, I guess now you finally understand the reason why I could never be caught until this very letter…
During the process of your personal info compilation, I could not help but notice that you are a huge admirer and regular guest of websites with adult content.
You endure a lot of pleasure while checking out porn websites, watching nasty porn movies and reaching breathtaking orgasms.
Let me be frank with you, it was really hard to resist from recording some of those naughty solo scenes with you in main role and compiling them in special videos
that expose your masturbation sessions, which end with you cumming.In case if you still have doubts, all I need is to click my mouse and all those nasty videos with you will be shared to friends, colleagues, and relatives of yours.
Moreover, nothing stops me from uploading all that hot content online, so all public can watch it too.
I sincerely hope, you would really not prefer that to happen, keeping in mind all the dirty things you like to watch,
(you certainly know what I mean) it will completely ruin your reputation.However, don’t worry, there is still a way to resolve this:
You need to carry out a $1290 USD transfer to my wallet (equivalent amount in bitcoins depending on exchange rate at the moment of funds transfer),
hence upon receiving the transaction, I will proceed with deleting all the filthy videos with you in main role.
Afterwards, we can forget about this unpleasant accident. Furthermore, I guarantee that all the malicious software will also be erased from your devices and accounts.
Mark my words, I never lie.That is a great bargain with a low price, I assure you, because I have spent a lot of effort while recording
and tracking down all your activities and dirty deeds during a long period of time.
In case if you have no idea how to buy and transfer bitcoins – feel free to check the related info on the internet.Here is my bitcoin wallet for your reference: 17ychKgip2JpHf8uh5AJ6r5rXkmjSnQWaZ
From now on, you have only 48 hours and countdown has started once you opened this very email (in other words, 2 days).
The following list contains things you should definitely abstain from doing or even attempting:
> Abstain from trying to reply this email (since the email is generated inside your inbox alongside with return address).
> Abstain from trying to call or report to police or any other security services. In addition, it’s a bad idea if you want to share it with your friends,
hoping they would help. If I happen to find out (knowing my awesome skills, it can be done effortlessly,
because I have all your devices and accounts under my control and unceasing observation) – kinky videos of yours will be share to public the same day.
> Abstain from trying to look for me – that would not lead anywhere either. Cryptocurrency transactions are absolutely anonymous and cannot be tracked.
> Abstain from reinstalling your OS on devices or throwing them away. That would not solve the problem as well,
since all your personal videos are already uploaded and stored at remote servers.Things you may be confused about:
> That your funds transfer won’t be delivered to me.
Chill, I can track down any transactions right away, so upon funds transfer I will receive a notification as well,
since I still control your devices (my trojan virus has ability of controlling all processes remotely, just like TeamViewer).
> That I am going to share your dirty videos after receiving money transfer from you.
Here you need to trust me, because there is absolutely no point to still bother you after receiving money.
Moreover, if I really wanted all those videos would be available to public long time ago!I believe we can still handle this situation on fair terms!
Here is my last advice to you… in future you better ensure you stay away from this kind of situations!
My advice – don’t forget to regularly update your passwords to feel completely secure.
All in all, this scam uses tricks to make you scared and rushed. If you receive an email like this, do not engage with the scammer and do not send any money. Instead, delete the email. It is also important to ensure that your computer has up-to-date anti-virus software and that you use strong, unique passwords for all of your accounts to reduce the likelihood of falling victim to scams like this.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
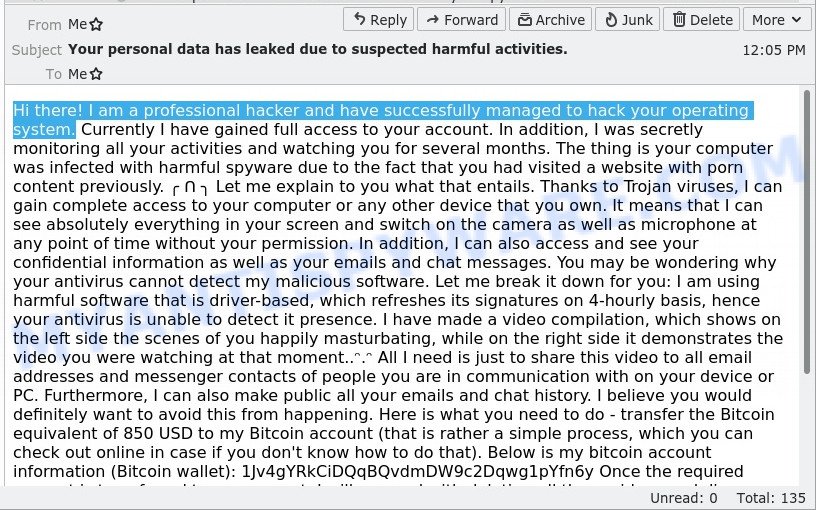
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
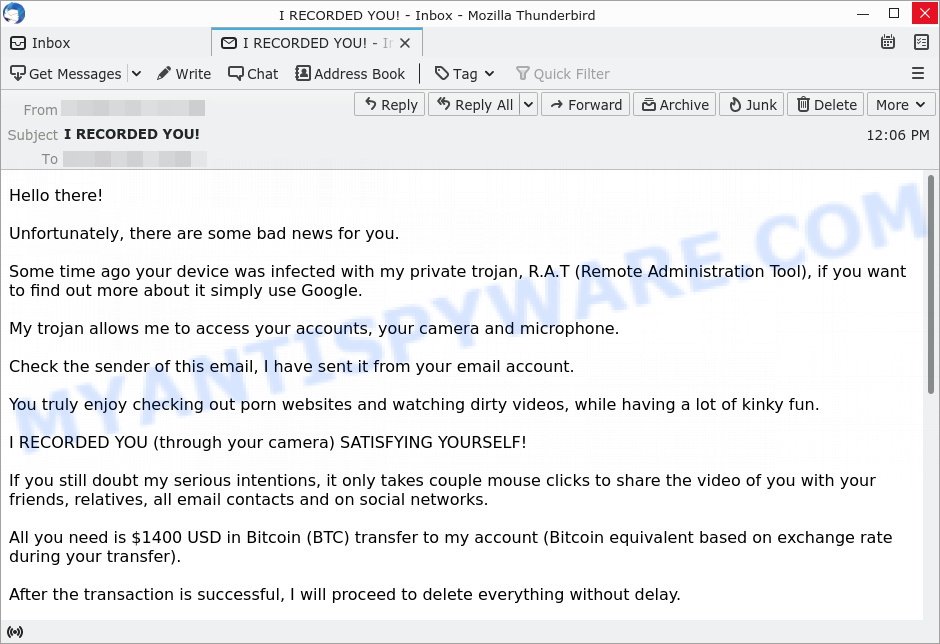
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
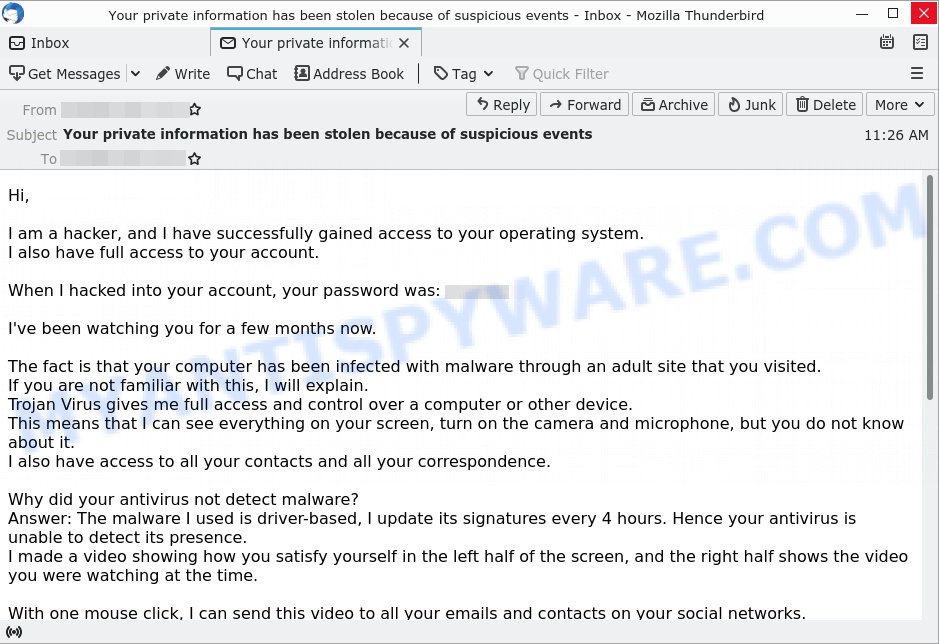
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “Sadly, there are some bad news that you are about to hear” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | Sadly, there are some bad news that you are about to hear |
| Type | Phishing/Sextortion |
| Ransom amount | $1290, $1490 (in Bitcoin equivalent) |
| Bitcoin Address | 17ychKgip2JpHf8uh5AJ6r5rXkmjSnQWaZ, 1K8g3n8Z9t265pMYuhpKc8jfmPS6cY7Qcr |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The ‘Sadly, there are some bad news that you are about to hear’ email scam shows how cybercriminals try to scare people into giving them money. They do things like pretending to send emails from your own address and making big claims without any real proof. The best way to deal with these scams is to understand how they work. Always be careful online, don’t make quick decisions based on these emails, and focus on keeping your information safe.












I found a scam with the exact words from above in my Spam-box. It was sent from my email account to my email account! How is that possible??
Email spoofing, a technique used in spam and phishing attacks.