“Trojan:Slocker” Pop-Up is a Scam! Have you ever stumbled upon a warning while online, saying your device has been infected by “Trojan:Slocker”? And it tells you to call a number, “+1 (866) 777-1016”, claiming it’s Microsoft’s support line? Beware, this is a fake alert! These alarming messages often pop up when you’re on risky websites or after you’re redirected from another site. It’s not a real warning from Microsoft.
To safeguard yourself from falling victim to this scam and others like it, it’s crucial to understand the red flags and take preventive measures. Read on to learn more about the “Trojan:Slocker” scam and how to protect yourself from its deceptive grip.
QUICK LINKS
How the Scam Works 🚫🔍
The “Trojan:Slocker” scam is a sophisticated scheme that preys on users’ fears of malware infections and illegal activities. Scammers employ various tactics to redirect users to their fraudulent websites, often through malicious ads, compromised websites, or email phishing campaigns. Once you land on one of these deceptive pages, a pop-up message appears, claiming to be from a reputable company like Microsoft.
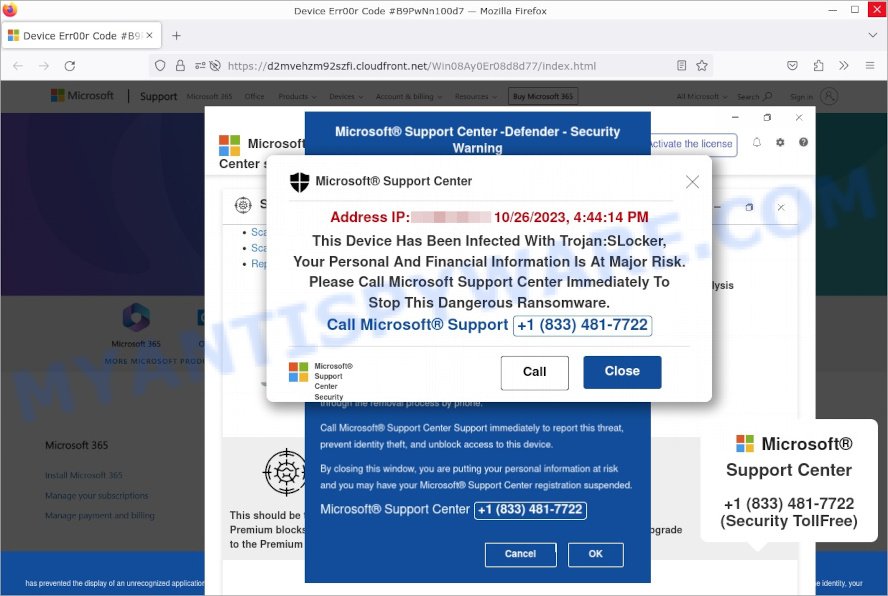
Highlighted below is the text that appears in the ‘Trojan:Slocker’ topmost pop-up:
Microsoft® Support Center
Address IP: – 10/25/2023, 9:55:23 AMThis Device Has been Infected With Trojan:Slocker,
Your Personal And Financial Information Is At Major Risk.
Please Call Microsoft Support Center Immediately To Stop This Dangerous Ransomware.Call Microsoft Support +1 (866) 777-1016
The “Official” Warning 🚨
The message claims to be from the “Microsoft® Support Center” and asserts that your device has been compromised by the “Trojan:Slocker” malware. The aim is to make you panic and act without thinking.
The Call to Action ☎️
To create a sense of urgency, the scam insists that your personal and financial information is in grave danger. They urge you to call a specific number, “+1 (866) 777-1016”, immediately for help.
The Endgame 💸
If you call, the scammers might try various tactics:
- Remote Access: They’ll ask to remotely access your computer, supposedly to “fix” the issue, but in reality, they might steal your data or install real malware.
- Phony Fees: They could claim you need to pay a fee to remove the nonexistent “Trojan”, exploiting you financially.
- Sell Useless Software: They might persuade you to purchase unnecessary and often fake software to “protect” your device.
Your Real Risk 🛑
While the pop-up’s threats are bogus, the real danger is in engaging with the scammers, which can lead to loss of money or personal data.
Remember, always be skeptical of unsolicited warnings or calls to action, especially when they provoke panic. Instead, arm yourself with knowledge and stay one step ahead.
Examples of such scams
Scammers are continually coming up with new tactics to deceive unsuspecting individuals, and the “Trojan:Slocker” scam is just one example of their deceptive techniques. However, it is important to note that this is not an isolated case. There are numerous scams out there that exploit similar strategies, aiming to trick people into falling for their fraudulent schemes.
Here are some links to examples of similar scams: Virus Has Been Found On Your PC Scam, Your Card Payment Has Failed – McAfee Renew Subscription Scam, and McAfee Virus found (3) Pop-Up Scam.
- McAfee TROJAN Virus/Emotet Detected pop-up on Windows
- Fake “McAfee Potential Viruses (3)” Alert Scam
- Foylosd.xyz McAfee Scam
- Validitysupport.com McAfee Scam
- “Your card payment has failed” McAfee Scam
Origins of “Trojan:Slocker” Scam Pop-ups
The “Trojan:Slocker” scam pop-ups can come from various sources, including malicious websites, spam emails, or pop-up advertisements. One of the most common methods is through the use of adware, which is a type of software that displays unwanted ads or redirects users to unwanted websites. Adware can be bundled with legitimate software or downloaded unintentionally from the internet.
Another source of these scams is through the use of malicious push notifications, which are notifications that appear on your desktop or mobile device without your consent. These push notifications can be triggered by visiting a malicious website or by downloading a malicious app.
In some cases, scammers use fraudulent ad networks to display fake ads that look like legitimate security warnings, tricking users into clicking on them and installing malware on their computers.
How to Identify Such Scams 🔍🚫
By recognizing these red flags, you can confidently steer clear of such scams and protect both your device and personal information. Always prioritize your online safety! 🛡️🔒

🖥️ Unexpected Pop-Ups
Genuine software or operating system messages will never just pop up from a web browser. If you see sudden warnings or alerts while browsing, especially on streaming, downloading, or redirected sites, be wary.
⏳ Urgent Language
Scammers use phrases like “immediate action required” or “your data is at major risk” to pressure you into acting quickly without thinking.
🤳 Request for Personal Info
Official support teams, especially those from big names like Microsoft, won’t ask for personal or financial details through a browser pop-up.
📞 Suspicious Phone Numbers
The pop-up urges you to call a specific number, such as “+1 (866) 777-1016”. Always double-check any helpline numbers on the company’s official website before calling.
🛡️ Generic Titles and Logos
Scams often use generic terms like “PC Support” or display blurry or stretched logos. Authentic messages will have clear, high-quality branding and specific company names.
💰 Offers to “Fix” for a Fee
If the alert quickly leads to demands for payment, especially for services or software you’ve never heard of, it’s likely a scam.
📝 Poor Grammar and Spelling
Many scams have errors in their messages. If the wording seems off, or there are blatant spelling mistakes, be suspicious.
Threat Summary
| Name | “Trojan:Slocker” Scam |
| Type | Tech Support Scam |
| Fake claims | Claims device is infected with dangerous ransomware |
| Fake err | Claims device is infected with Trojan.SLocker. A dangerous ransomware, Error Code: WinError.h 6001(0x1770) |
| Scammers websites | d2mvehzm92szfi.cloudfront.net |
| Scammers contacts | +1 (866) 777-1016 |
| Distribution | Adware, malicious websites, push notifications, social engineering |
| Damage | Financial loss, data compromise, installation of malicious software |
| Indicators of the Scam | Alarming pop-up messages with urgent warnings; Fake security warning with error codes; Claims of illegal activities leading to device blockage; Urgent call to action to contact the provided phone number; Poorly designed websites with spelling errors and unprofessional elements |
| Prevention Tips | Be cautious of unsolicited pop-ups and calls; Do not provide remote access to your device to unknown individuals; Use reliable security software and keep it updated; Educate yourself about common scams and their indicators |
How to remove “Trojan:Slocker” pop-ups
If you have encountered “Trojan:Slocker” pop-ups, you should not trust the message and refrain from clicking any buttons or links that appear on the page. Instead, follow the steps below to remove the pop-up and any potential malware from your computer:
To remove “Trojan:Slocker” pop ups, complete the steps below:
- Close the pop-up
- Clear your browsing history
- Disable push notifications
- Scan your computer for malware
- Reset your browser settings
Close the pop-up
Closing the pop-up is the first step you should take when dealing with the “Trojan:Slocker” scam. Although it may seem like a simple task, some users may find it challenging, especially if the pop-up is designed to be persistent and difficult to close. This step is crucial because it prevents the user from falling into the trap set by the scammers and clicking on any of the buttons or links that can lead to further harm. In this section, we will provide a detailed guide on how to close the “Trojan:Slocker” pop-up safely and effectively.
- Don’t click on anything within the pop-up as it could lead to further harm.
- Look for a small “X” or “Close” button within the pop-up window. Click on it to close the window.
- If there is no “X” or “Close” button, try pressing the “Esc” key on your keyboard to close the pop-up.
- If the pop-up still won’t close, try opening your computer’s Task Manager by pressing “Ctrl + Shift + Esc” on your keyboard (or “Ctrl + Alt + Delete” and then select “Task Manager”). Find the browser window that the pop-up is in, right-click on it, and select “End Task” to force close the window.
Clear your browsing history
Clearing your browsing history is an important step in removing “Trojan:Slocker” pop-ups. These pop-ups often come from malicious websites that can be stored in your browsing history.
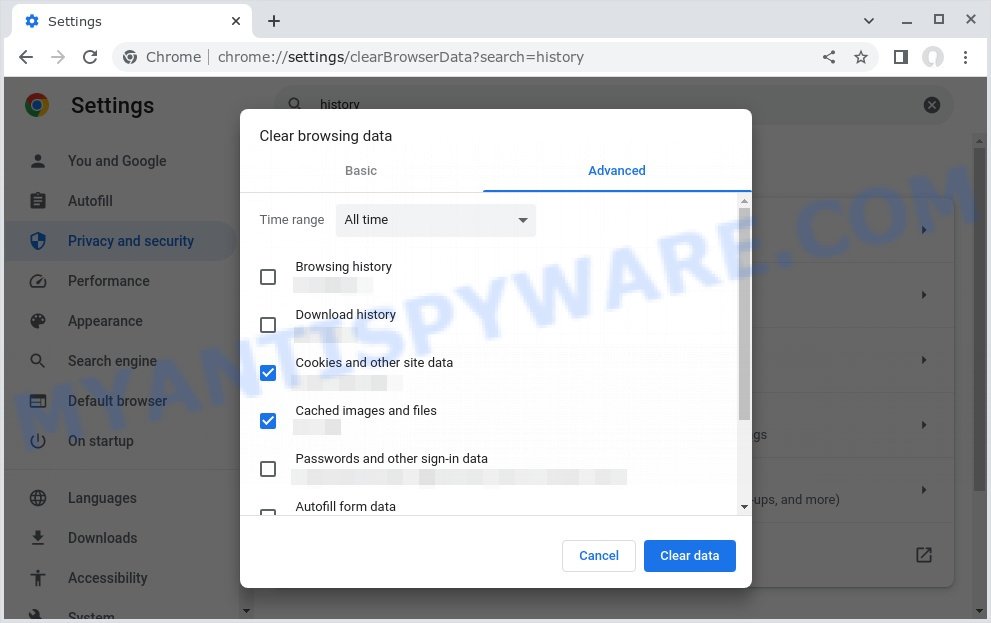
By clearing your browsing history, you can get rid of any traces of these websites and prevent the pop-ups from reappearing. In this step, we will walk you through how to clear your browsing history on different browsers.
- Open your browser’s settings or options menu. This can usually be accessed by clicking on the three dots or lines in the top right or left corner of the browser window.
- Scroll down to the “Privacy & Security” or “History” section of the settings menu.
- Click on “Clear Browsing Data” or “Clear History” (the wording may vary depending on the browser you are using).
- In the pop-up window that appears, choose the time range for which you want to clear your browsing history (e.g. “Last hour”, “Last 24 hours”, “All time”, etc.).
- Make sure that “Browsing history” or “History” is selected as one of the types of data to be cleared.
- Click on the “Clear Data” or “Clear History” button (the wording may vary depending on the browser you are using).
- Wait for the browser to finish clearing your browsing history. This may take a few moments, especially if you have a lot of browsing data stored on your computer.
- Close and restart your browser to ensure that the changes take effect.
Disable push notifications
If you’re experiencing persistent push notifications from websites that are showing “Trojan:Slocker” scams, the best course of action is to disable push notifications altogether. Disabling push notifications prevents malicious websites from showing you unwanted pop-ups and alerts, which can help protect your computer from further harm. In this step, we’ll walk you through the process of disabling push notifications in your web browser.
Google Chrome:
- Click on ‘three dots menu’ button at the top-right corner of the Google Chrome window.
- Select ‘Settings’, scroll down to the bottom and click ‘Advanced’.
- At the ‘Privacy and Security’ section click ‘Site settings’.
- Click on ‘Notifications’.
- Locate the “Trojan:Slocker” site and click the three vertical dots button next to it, then click on ‘Remove’.
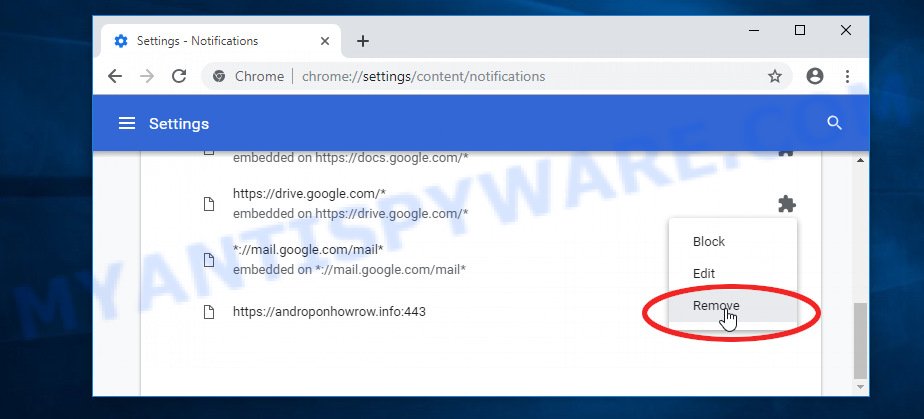
Android:
- Open Chrome.
- Tap on the Menu button (three dots) on the top right corner of the screen.
- In the menu tap ‘Settings’, scroll down to ‘Advanced’.
- In the ‘Site Settings’, tap on ‘Notifications’, locate the “Trojan:Slocker” URL and tap on it.
- Tap the ‘Clean & Reset’ button and confirm.
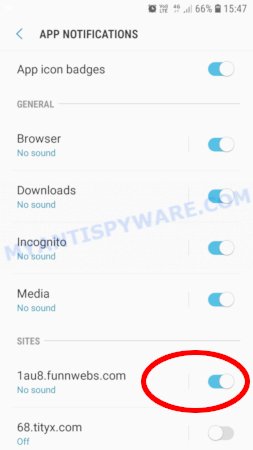
Mozilla Firefox:
- In the top right corner, click the Firefox menu (three bars).
- In the drop-down menu select ‘Options’. In the left side select ‘Privacy & Security’.
- Scroll down to ‘Permissions’ section and click ‘Settings…’ button next to ‘Notifications’.
- Find “Trojan:Slocker”, other suspicious URLs, click the drop-down menu and select ‘Block’.
- Click ‘Save Changes’ button.
Edge:
- Click the More button (three dots) in the top-right corner of the window.
- Scroll down, locate and click ‘Settings’. In the left side select ‘Advanced’.
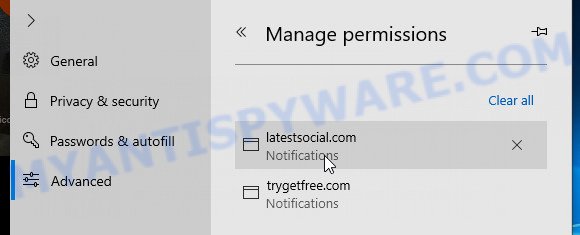
- In the ‘Website permissions’ section click ‘Manage permissions’.
- Disable the on switch for the “Trojan:Slocker” domain.
Internet Explorer:
- Click the Gear button on the top-right corner of the browser.
- Select ‘Internet options’.
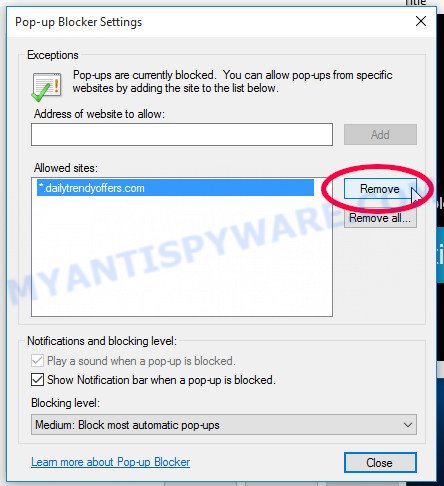
- Click on the ‘Privacy’ tab and select ‘Settings’ in the pop-up blockers section.
- Locate the “Trojan:Slocker” site and click the ‘Remove’ button to delete the site.
Safari:
- Go to ‘Preferences’ in the Safari menu.
- Select the ‘Websites’ tab and then select ‘Notifications’ section on the left panel.
- Find the “Trojan:Slocker” site and select it, click the ‘Deny’ button.
Scan computer for malware
If you have encountered the “Trojan:Slocker” scam, it is possible that your computer has been infected with malware. In order to ensure that your system is completely clean, it is important to perform a thorough scan for malware. This will help to identify any malicious files or programs that may be hiding on your computer and remove them to prevent further damage. In this step, we will guide you through the process of scanning your computer for malware using trusted antivirus software.
Malwarebytes is a reputable anti-malware program that can effectively detect and remove adware, potentially unwanted programs and malware. It has a user-friendly interface and offers both free and paid versions, with the paid version offering real-time protection and other advanced features. To use Malwarebytes to remove malicious software, you can download and install the program, perform a scan of your system, and follow the prompts to remove any detected threats.
Visit the following link and download the latest version of Malwarebytes. Once the download is complete, run the installer and follow the instructions to install the program on your computer.
327077 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
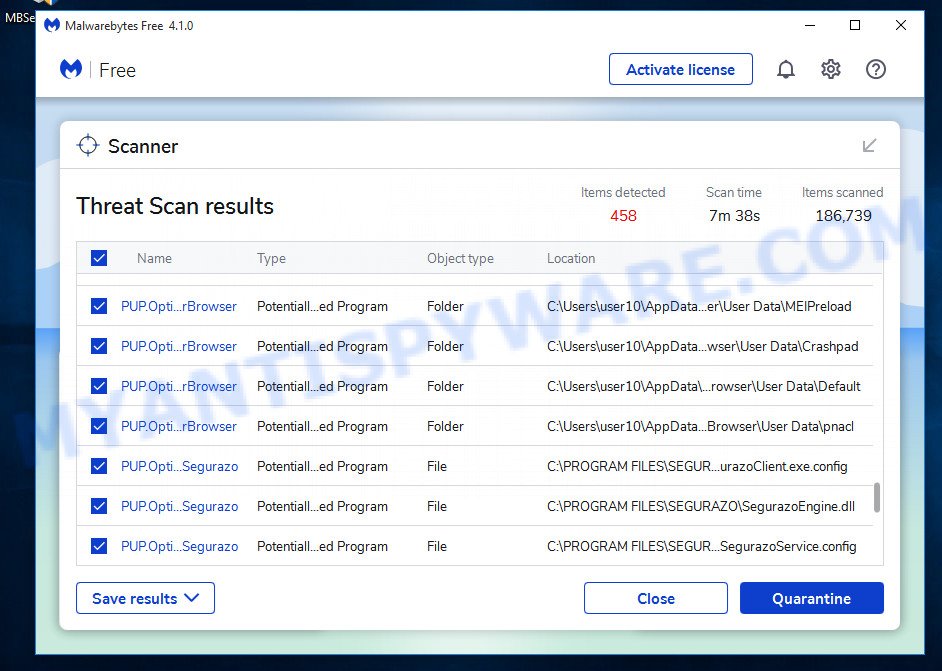
Open Malwarebytes and click on the “Scan” button. The program will start scanning your computer for any malware or potentially unwanted programs. Depending on the size of your hard drive, this may take a few minutes to complete.
Once the scan is complete, Malwarebytes will display a list of any threats it has found. Review the list carefully and make sure that all the items are checked for removal. Then, click on the “Quarantine” button to remove the threats from your computer. After the removal process is complete, you may be prompted to restart your computer to complete the process.
Please follow this step-by-step video tutorial to learn how to use Malwarebytes to scan and remove any potential threats from your computer. The video will guide you through the entire process, from downloading and installing Malwarebytes to running a scan and removing any identified threats.
Reset your browser settings
If the “Trojan:Slocker” pop-ups persist even after clearing your browsing history, disabling push notifications, and scanning your computer for malware, resetting your browser settings might be the next step to take. Resetting your browser settings can remove any unwanted extensions or changes made to your browser that may be causing the pop-ups to appear. In this step, we will guide you through the process of resetting your browser settings in different popular browsers.
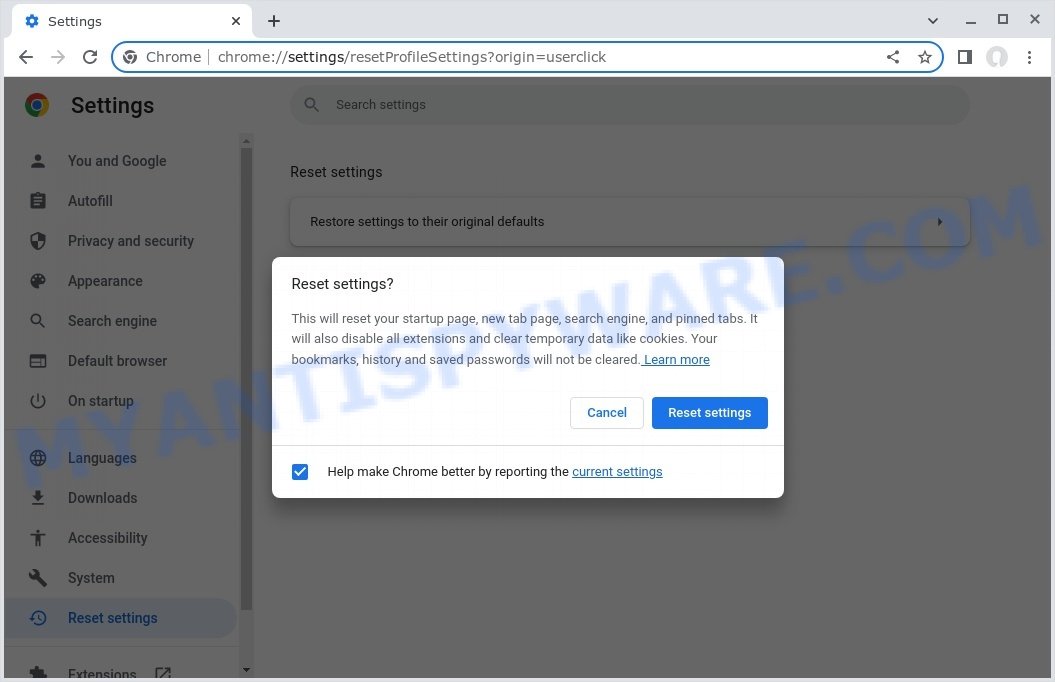
To reset your browser settings in Google Chrome:
- Open Chrome and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down to the bottom of the page and click on “Advanced”.
- Scroll down to the “Reset and cleanup” section and click on “Restore settings to their original defaults”.
- Click “Reset settings” to confirm.
To reset your browser settings in Mozilla Firefox:
- Open Firefox and click on the three-line icon in the top-right corner.
- Select “Help” from the drop-down menu and then click on “Troubleshooting Information”.
- Click on the “Refresh Firefox” button in the top-right corner.
- Click “Refresh Firefox” again to confirm.
To reset your browser settings in Microsoft Edge:
- Open Edge and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down and click on “Reset settings”.
- Click “Restore settings to their default values”.
- Click “Reset” to confirm.
After resetting your browser settings, be sure to check for any remaining suspicious extensions and remove them if necessary.
Conclusion
In conclusion, the “Trojan:Slocker” scam and similar deceptive schemes continue to pose a threat to unsuspecting individuals. By understanding the tactics employed by scammers, recognizing the red flags, and taking preventive measures, you can protect yourself from falling victim to these fraudulent schemes.
Remember to be cautious of suspicious pop-ups, unsolicited contact, and requests for personal or financial information. Legitimate companies will not display alarming messages or demand immediate action through aggressive pop-ups. Stay informed about common scams, rely on official support channels, and use reputable security software to safeguard your devices.