In my daily email check, I recently came across yet another sextortion scam email, a common sight these days. The subject line read ‘YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED CHECK THIS MESSAGE NOW‘, a jarring message designed to create panic. If you’ve checked your spam folder lately, you might have seen a similar email. These messages are part of a growing trend where scammers use fear-inducing tactics like threatening language and demands for Bitcoin payments to exploit victims.
This kind of scam has become increasingly prevalent, with fraudsters blasting out these emails in bulk, hoping to scare a few into paying up, even though they don’t actually have any compromising information. The tactic is simple: instill fear and urgency to manipulate people into acting hastily.
Remember, the aim of these emails is to leverage fear. If you encounter such an email, don’t react in a rush. This article will delve into how these scams work, and most importantly, provide guidance on what steps you should take if you receive such a threatening message.
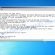
Here’s an example of the “YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED” email:
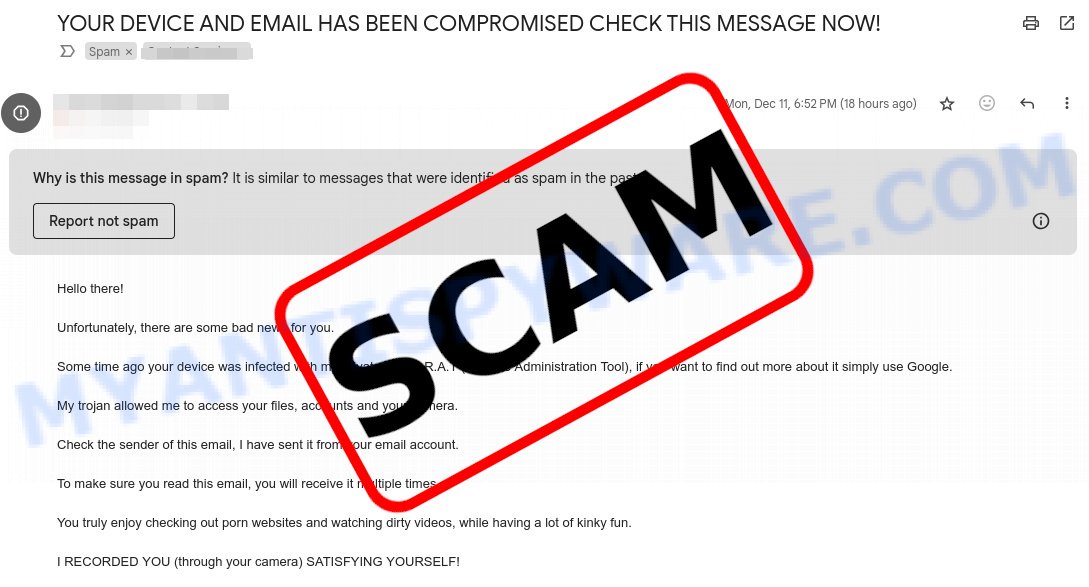
Table of Contents
Is this a scam email?
YES. The “YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED” email is a phishing scam that preys on fear and blackmail tactics. It begins with a message informing you that your device and account has been compromised by a supposed hacker. The email asserts that the hacker has control of your computer, webcam, and personal information. The email threatens to expose sensitive content, including video footage of you, unless you comply with the scammer’s demands. These demands usually involve sending a ransom payment in Bitcoin to a specified wallet address within a given timeframe.
Red-Flags Indicating It’s a Scam:
- Threatening Language: The email begins with alarming statements, such as claiming that your account has been hacked. It may even suggest that you’re being watched.
- Video Threat: The scammer claims to have recorded you through your webcam while you were browsing the adult content website, attempting to make you believe they have compromising footage.
- Bitcoin Wallet Address: The use of Bitcoin is a way for scammers to try to receive money anonymously. It’s worth noting that once you send Bitcoin, it’s almost impossible to get it back.
- Short Deadline: The email sets a tight deadline, 3 days, for you to comply with their demands.
- No Mention of Specific Personal Details: Aside from the generic “hacked content”, they won’t mention any specific personal information about you, like your full name, address, or other data, which a genuine hacker would probably use to prove their claims.
In summary, 🚫 If you encounter such emails, it’s crucial to remain calm and not engage with the sender. Remember, these are empty threats designed to exploit your fears. It’s always best to protect your online presence and be wary of such tactics. 🛡️ Always ensure the safety of your devices, change passwords regularly, and be cautious about sharing personal information online.
How the scam works
Initially, you might wonder, “Where did they get my email address?” The answer lies in the numerous data breaches and online lists circulating on the dark web. Scammers can acquire vast lists of email addresses, sometimes coupled with other personal information, from various sources. They target these addresses in hopes that at least a few individuals will respond.
The ambiguous threats are their next weapon. 🚫 With a broad approach, they send out countless emails, betting on the chance that some recipients might be alarmed. They intentionally avoid mentioning any specific website or source of their alleged information, leading you to wonder, “Could there be any truth to this?”
Their narrative then deepens with a fictitious tale 🎭 of supposed system infiltration. They spin stories of having implanted malicious software on your device, insinuating they have access to your every move. Yet, conspicuously, they offer no real evidence to substantiate their claims.
In the final step of their ploy, they demand a ransom. 💰 Emphasizing quick payment, often via hard-to-trace channels like Bitcoin, is key to their strategy. By imposing a stringent timeframe, they hope to pressure you into acting impulsively, driven by fear and uncertainty.
The email read as follows:
Hello there!
Unfortunately, there are some bad news for you.
Some time ago your device was infected with my private trojan, R.A.T (Remote Administration Tool), if you want to find out more about it simply use Google.
My trojan allowed me to access your files, accounts and your camera.
Check the sender of this email, I have sent it from your email account.
To make sure you read this email, you will receive it multiple times.
You truly enjoy checking out porn websites and watching dirty videos, while having a lot of kinky fun.
I RECORDED YOU (through your camera) SATISFYING YOURSELF!
After that I removed my malware to not leave any traces.
If you still doubt my serious intentions, it only takes couple mouse clicks to share the video of you with your friends, relatives, all email contacts, on social networks, the darknet and to publish all your files.
All you need is $800 USD in Bitcoin (BTC) transfer to my account.
After the transaction is successful, I will proceed to delete everything.
Be sure, I keep my promises.
You can easily buy Bitcoin (BTC) here:
https://cex.io/buy-bitcoins
https://nexo.com/buy-crypto/bitcoin-btc
https://bitpay.com/buy-bitcoin/?crypto=BTC
https://paybis.com/
https://invity.io/buy-cryptoOr simply google other exchanger.
After that send the Bitcoin (BTC) directly to my wallet, or install the free software: Atomicwallet, or: Exodus wallet, then receive and send to mine.
My Bitcoin (BTC) address is: 16RrKqp6gvepFSBMTcoVzdJZ1NSbA7PjZA
Yes, that’s how the address looks like, copy and paste my address, it’s (cAsE-sEnSEtiVE).
You are given not more than 3 days after you have opened this email.
As I got access to this email account, I will know if this email has already been read.
Everything will be carried out based on fairness.
An advice from me, regularly change all your passwords to your accounts and update your device with newest security patches.
All in all, this scam uses tricks to make you scared and rushed. If you receive an email like this, do not engage with the scammer and do not send any money. Instead, delete the email and report it to the relevant authorities. It is also important to ensure that your computer has up-to-date anti-virus software and that you use strong, unique passwords for all of your accounts to reduce the likelihood of falling victim to scams like this.
Examples of such scams
The “YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED” email scam is just one of the many deceptive schemes that prey on individuals’ fears and exploit their privacy concerns. Unfortunately, this type of scam is not unique, and there are various similar scams circulating online.
By examining these examples, you can better recognize the warning signs and arm yurself with knowledge to avoid becoming victims of fraudulent schemes. Take a closer look at the following scams: I RECORDED YOU Email Scam, Your Private Information has been Stolen Email Scam, and I am a professional hacker EMAIL SCAM and let’s learn how to safeguard ourselves from their deceitful tactics. Remember, knowledge is power.
- Cash Settlement Awarded Email Scam
- Financial Assistance Department Email Scam
- Geek Squad Email Scam (May 2023)
- Your account is hacked. Your data is stolen. Email Scam
- Reconfirm Shipping Documents Scam email
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “‘YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED'” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | ‘YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED’ |
| Type | Phishing/Sextortion |
| Ransom amount | $800 USD (in Bitcoin equivalent) |
| Bitcoin Address | 1EV3qSyz4XKoZAWvB1eVSYqHyqCNRdv9i7, 16RrKqp6gvepFSBMTcoVzdJZ1NSbA7PjZA |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The ‘YOUR DEVICE AND EMAIL HAS BEEN COMPROMISED’ email scam shows how cybercriminals try to scare people into giving them money. They do things like pretending to send emails from your own address and making big claims without any real proof. The best way to deal with these scams is to understand how they work. Always be careful online, don’t make quick decisions based on these emails, and focus on keeping your information safe. If something sounds too alarming or too good to be true, it’s a good idea to double-check and not rush into any action.