⚠️ Have you received an email with the subject “Re:” claiming to have compromising information on you? Be cautious, as this is a scam known as “Sextortion”.
Here’s what happens: The email starts off with an unsettling greeting ‘Hey There. The following is your very last notification.’ and quickly moves to inform you that they’ve supposedly compromised your operating system through the WiFi modem you were connecting to. They allege to have accessed all the information from your electronics and devices, including cellphone messengers, social media sites, emails, chats, and contact lists. The scammer threatens to release a supposed recording of you watching adult content and masturbating, along with your browsing history, to all your contacts unless you pay a ransom, usually in Bitcoin, to a specified wallet address.
But here’s the catch: these claims are false, designed to exploit your fear and coerce you into paying money without any real evidence of the recordings they claim to have.
The “Re:” Email Scam preys on fear and embarrassment to manipulate victims into complying. It’s crucial to remember that engaging with or paying the scammers does not guarantee your safety; it only marks you as an easy target for future scams. Always be skeptical of alarming emails that demand money or personal information and prioritize your online security with regular updates and caution about the links you click on. Awareness and skepticism are your best defenses against such online scams.
Table of Contents
🚨 Is the “I compromised your operating system” Email a Scam?
Yes, the email claiming that “I compromised your operating system” is definitely a scam. 🚫 If you’ve received an email with claims of having compromised your devices and having sensitive information or videos of you, proceed with extreme caution. These threats are fabricated and aim to exploit your fear to coerce you into paying a ransom.
Examples of claims made in the scam email:
- I compromised your operating system through the WiFi modem you were connecting to.
- I have recorded a video of you engaging in private activities and will distribute it to your contacts unless you pay.
- You must transfer $1300 USD in Bitcoin to my wallet to prevent the dissemination of these videos.
- Do not attempt to contact the police or interfere with your devices, as it will lead to the immediate release of the videos.
- This message was sent from an untraceable email, so do not reply.
The email employs threats and intimidation to create urgency and fear. 🚨 The objective? To deceive you into transferring money to the scammer without any real evidence that the claimed videos or information exist. These scammers prey on the potential embarrassment and panic of their victims to succeed. Remember: legitimate communication regarding personal issues will never occur through such menacing and anonymous messages. Always check the validity of such claims through reliable channels before reacting.
🚩 Red Flags to Watch Out For:
Be vigilant and question the authenticity of such emails if you encounter these warning signs. 🔍🛡️
- 📧 Intimidating Content: Emails that threaten and claim to have compromising information or videos of you.
- 🔗 Demands for Cryptocurrency: The scammer requests payment in Bitcoin, exploiting its anonymity.
- ⏳ Urgency and Deadlines: The email includes a tight deadline to coerce you into acting hastily out of fear.
- 🖼️ Claims of Hacking: Skepticism is warranted for emails claiming to have hacked your devices without providing any proof.
- ✍️ Language of Blackmail: These emails frequently contain explicit threats to share private videos or information with your contacts.
- 👤 Anonymity of the Sender: Scammers often use temporary or hard-to-trace email addresses to avoid being caught.
- 🔄 No Evidence Provided: Legitimate claims would likely be accompanied by some evidence, whereas scammers rely solely on intimidation without backing up their claims.
The email read as follows:
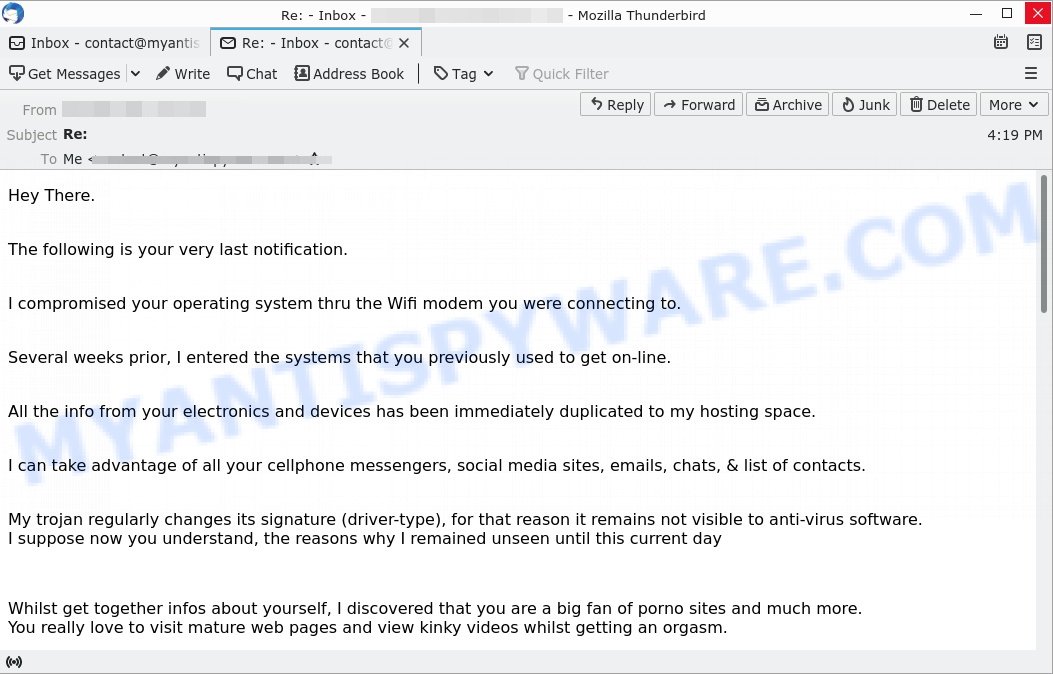
Hey There.
The following is your very last notification.
I compromised your operating system thru the Wifi modem you were connecting to.
Several weeks prior, I entered the systems that you previously used to get on-line.
All the info from your electronics and devices has been immediately duplicated to my hosting space.
I can take advantage of all your cellphone messengers, social media sites, emails, chats, & list of contacts.
My trojan regularly changes its signature (driver-type), for that reason it remains not visible to anti-virus software.
I suppose now you understand, the reasons why I remained unseen until this current dayWhilst get together infos about yourself, I discovered that you are a big fan of porno sites and much more.
You really love to visit mature web pages and view kinky videos whilst getting an orgasm.I have surely created a cam recording of you jacking off.
The cropping and editing of the videos you were seeing at the same time and your masturbation.
Your own facial expression is clearly seeable. I don’t believe this sort of information will be good for your personal status.I can direct this video footage out to everybody who know who you are.
I also have no trouble with making all your confidential information open public on the net.
I do believe you know what I mean.It may be an absolute frustration for you personally.
I can wreck your life forever.
I suspect that you seriously don’t want this to occur.
Let us fix it this way: you transfer me 1300 $ (usd) using btc equivalent at the moment of exchange), and i’ll promptly get rid of all of your data from my machines.
Proceeding that, we’ll forget about one another.My bitcoin wallet address for transfering: 112b2rLHpqs6fjmpvxmEEghhDWTY6HL1v3
If you do not realize how to transmit money and what exactly btc is. Then key in the Google “Get btc”.
I give you 3 days to send the funds.
The time launched counting automatically after you opened this e
mail.
I will see a message when this email is exposed.Do not try and search for help, as the wallet address cannot be monitored, e-mail the letter is coming from & cannot be followed either & generated automatically, so there is no reason for messaging me.
Don’t try to get hold of the police and other security services, & should you choose to do, your own information will undoubtedly be posted.Changing passwords online in social network sites, e mail, & devices will not help you, since all the info is already downloaded to my servers.
Good luck and try to not do something foolish. Think of your possible future.
🕵️♂️ How the “Re:” Email Scam Works
The ‘The following is your very last notification’ email scam with the subject “Re:” is a sophisticated form of digital extortion. Understanding its tactics is crucial for protecting yourself from becoming a victim. 💡🔐
🚨 Exploitation of Fear and Embarrassment
The scam initiates with an email falsely accusing the recipient of having engaged in compromising activities through their device’s camera. It exploits the natural human emotions of fear and shame, pushing recipients to comply with the scammer’s demands without questioning the legitimacy of the claims.
🔗 False Claims of Operating System Compromise
The email falsely claims that the scammer has compromised the recipient’s operating system through the WiFi modem they were connecting to. This supposed breach is said to grant the scammer access to sensitive information and the ability to monitor the victim’s activities, including access to messengers, social media sites, emails, chats, and contact lists.
False Claims Examples:
- Compromise of your operating system through the WiFi modem
- Access to all your electronics and devices, including social media and emails
- Installation of a trojan that regularly changes its signature to stay undetected by antivirus software
- Threats to distribute recorded videos of private moments to your contacts
🎭 Fabricated Evidence and Ultimatums
Scammers create a sense of urgency by falsely claiming they have recorded videos of the victim engaging in private activities. They then issue an ultimatum, demanding a ransom in cryptocurrency within a short timeframe, typically 72 hours.
📥 Demands for Cryptocurrency Payment
The scammer demands a payment, usually in Bitcoin, to allegedly delete the gathered data and videos from their servers. This method is chosen for its anonymity, making it difficult to trace the scammer.
🔄 Illusion of Control and Anonymity
The scammer maintains an illusion of omnipotence and anonymity, claiming to have total control over the victim’s devices and to be untraceable due to the use of cryptocurrency and sophisticated tactics that allegedly make them invisible to law enforcement and antivirus software.
🕳️ Threats and Psychological Manipulation
The email includes multiple threats to share the alleged recordings and sensitive information with the victim’s contacts, coupled with a pretense of offering mercy in exchange for money. This psychological manipulation is designed to make the victim act out of fear and desperation.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
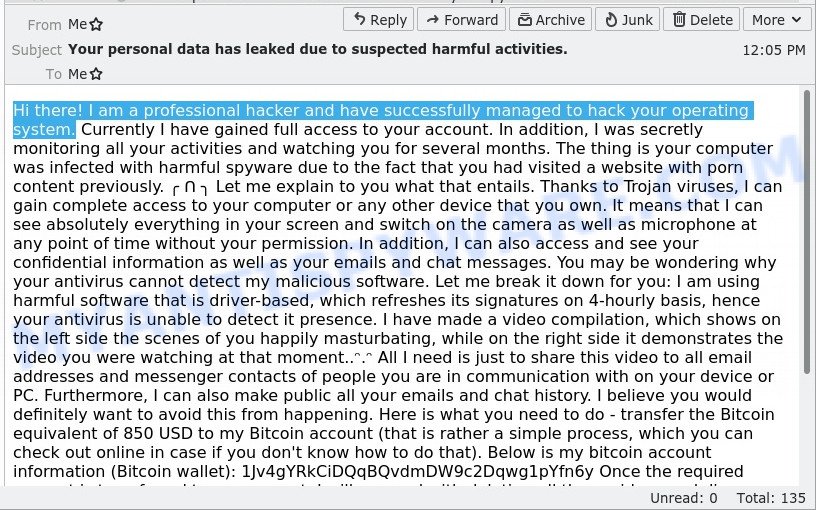
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
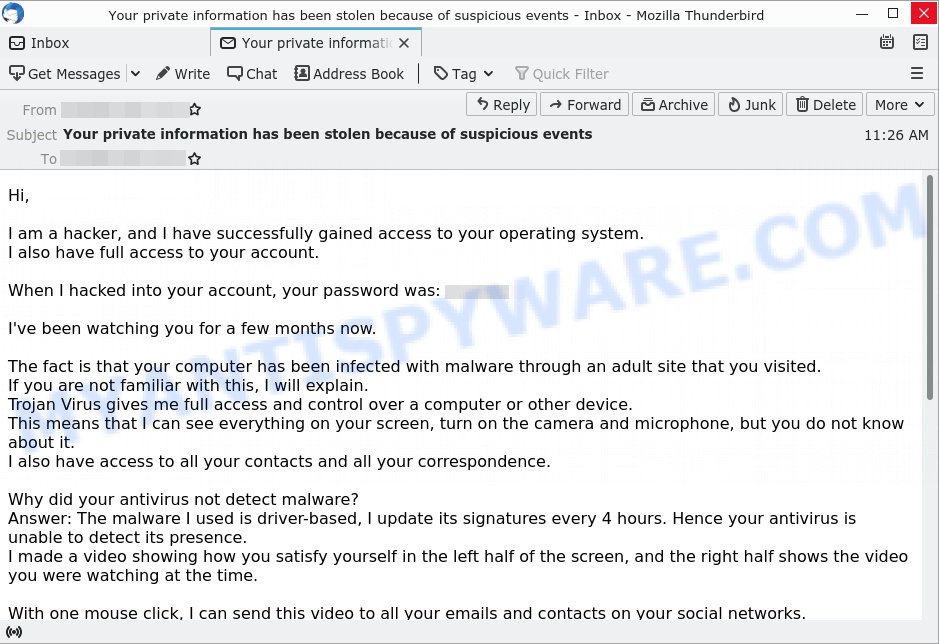
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
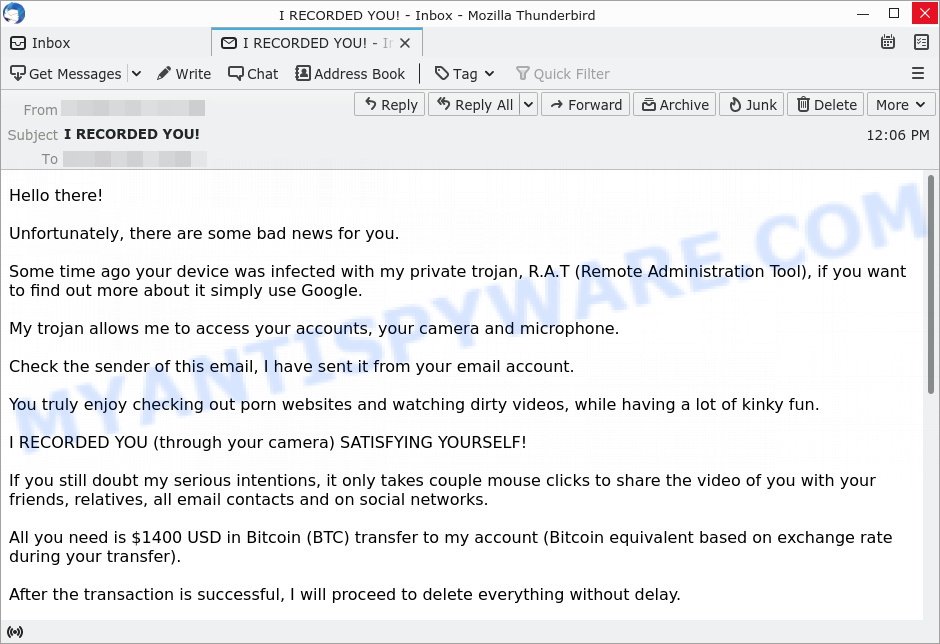
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “I compromised your operating system” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | ‘The following is your very last notification’ Email Scam, ‘I compromised your operating system’ Email Scam |
| Type | Phishing/Sextortion |
| Email Subject | Re: |
| Ransom amount | $1300 USD (in Bitcoin equivalent) |
| Bitcoin Address | 112b2rLHpqs6fjmpvxmEEghhDWTY6HL1v3 |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The email with the subject “Re:” claiming to have compromised your operating system through the WiFi modem and possessing compromising information is a scam designed to extort money from its victims. Scammers use fear tactics, falsely asserting they’ve accessed all your information and have recorded you visiting adult websites, threatening to expose these non-existent recordings to your contacts unless you pay a ransom, typically in Bitcoin for its perceived anonymity. It’s crucial to understand that these claims are almost always unfounded.
Bottom Line: Do not respond to these emails. The most effective strategy is to ignore their demands and focus on enhancing your online security. 🛡️💻
Remain alert and apply critical thinking; an email that immediately instills fear or appears too threatening is likely a scam. 🤔