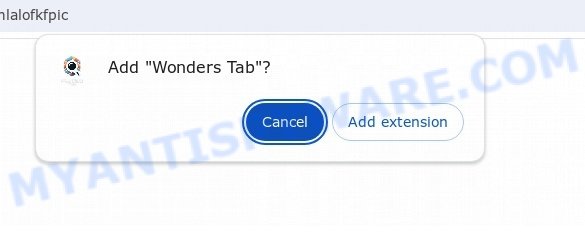
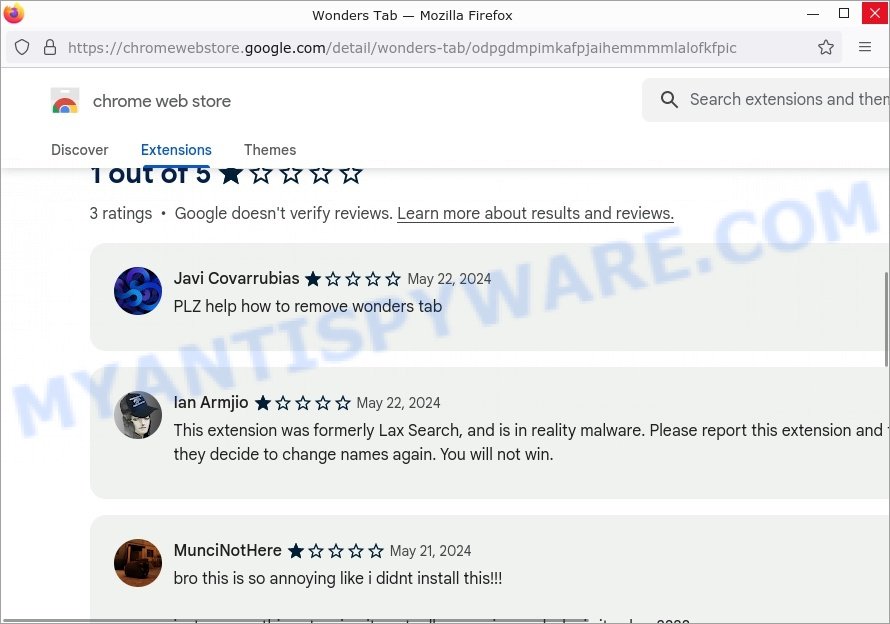
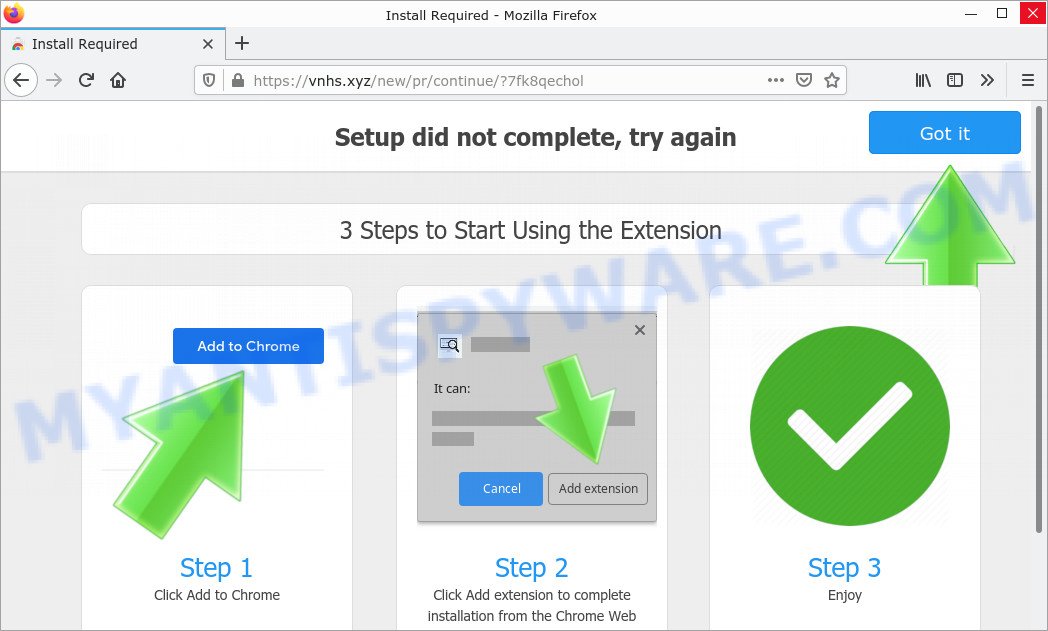
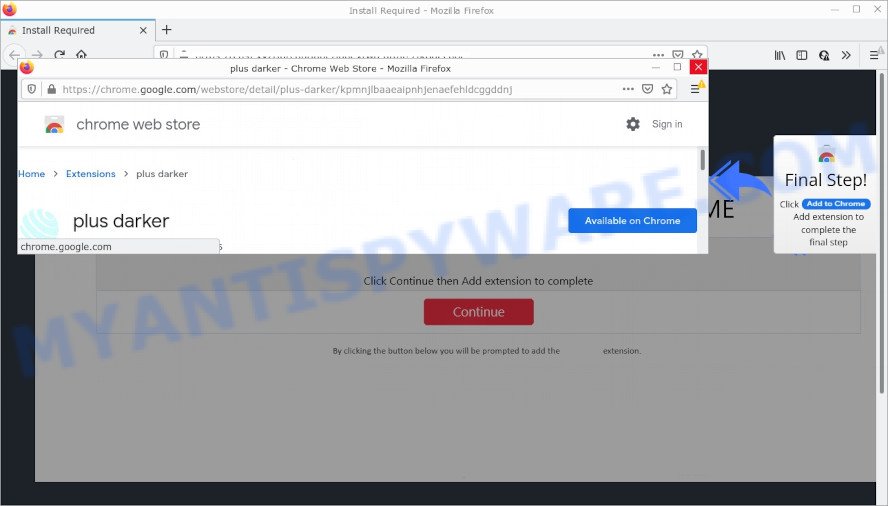
Wonders Tab is a browser extension categorized as a browser hijacker. This type of threat hijacks the user’s browser settings, causing unwanted changes such as redirecting search queries through suspicious websites like wonderstab.com. While the final destination may seem harmless, the intermediary sites can expose users to various dangers.
Browser hijackers like Wonders Tab not only disrupt the user’s browsing experience by altering search results but also pose significant risks to their online safety. By redirecting through websites like wonderstab.com, users are at higher risk of encountering malicious content or falling victim to malware attacks. The ultimate goal of such threats is often to compromise the user’s system, leading to potential data theft and privacy breaches.
If you are experiencing unwanted ‘Wonders Tab’ redirects, it is crucial to take immediate action to safeguard your online security. Read on to understand the threat posed by this browser hijacker and learn how to effectively remove it from your system.
Table of Contents
The Wonders Tab Hijacker Explained 🔍🔀
The Wonders Tab is a browser hijacker. Unlike some that might take you to a completely unknown or harmful website, this one directs you to the bing.com or Yahoo Search page, which is a legitimate and recognized search engine. Its main peculiarity is that it leverages Yahoo’s genuine platform as a facade, masking its dubious activities behind a reputable site.
Why Redirect to Yahoo Search? 💰
Scammers or cybercriminals use the redirect mechanism to gain financial benefits. Each time a user is redirected to bing.com via these intermediary sites, and they engage with the content or ads, it can generate revenue through ad clicks or affiliate schemes for those behind the scenes. Essentially, the cybercriminals get a cut or commission, using bing.com as an unintentional accomplice.
How Does This Happen? 🌐
Criminals employ a variety of cunning techniques to manipulate your browser and redirect your searches to Yahoo Search. Here’s a closer look at some of the key methods they use:
- Replacing the Homepage: The hijacker alters your default homepage to a controlled page. Each time you launch your browser, you’re greeted by this altered page, which could further lead you to other malicious sites or generate ad revenue for the criminals.
- Malicious Extensions: Cybercriminals can introduce rogue extensions to your browser. These extensions can monitor and redirect your browsing activities, often without any visible signs, making them particularly insidious.
- Tampering with Legitimate Extensions: Sometimes, instead of adding a new extension, criminals might replace or modify a legitimate one you already trust and use. This can be harder to detect because you believe you’re using a trusted tool.
- Proxy Server or Browser Settings: By altering the settings of your system’s proxy server or browser, the hijacker can control and redirect all your internet traffic. This gives them a significant level of control over your online activities.
- Modifying System Settings: More advanced hijackers can change specific system settings of your computer. By altering DNS settings, for example, they can decide which servers your system communicates with when trying to access a website, effectively controlling your entire online experience.
- Blocking Restoration of Normal Settings: To ensure their changes aren’t easily undone, these hijackers often employ mechanisms to block or limit your ability to restore regular settings. They might disable certain settings within the browser, introduce additional software that counters any restoration attempts, or even modify system permissions to prevent changes.
The techniques used by criminals for browser hijacking are not only diverse but also constantly evolving. Their aim is to remain unnoticed for as long as possible while maximizing their control over your online activities.
Methods of Infiltration 🚪
There are multiple ways Wonders Tab can sneak onto your computer:
- Bundling: The hijacker can be packaged with other software, especially free or pirated versions. When users install the primary software, the hidden browser hijacker gets installed too.
- Fake Updates: Pop-ups or banners urging users to update software, especially popular ones like Flash Player, might be disguises for the hijacker.
- Malicious Attachments: Phishing emails with dubious attachments can introduce the hijacker when opened.
- Compromised Websites: Merely visiting a hacked or malicious website might initiate a background download of the hijacker.
- TO CONTINUE – ADD EXTENSION TO CHROME pop-ups promote a browser hijacker
In Summary, the Wonders Tab hijacker is a wolf in sheep’s clothing. While it might seem harmless since it leads to a reputable search engine, the journey there is riddled with dubious detours that benefit scammers. To fully protect yourself and ensure uninterrupted, safe browsing, it’s crucial to understand removal techniques and preventive measures – something we’ll delve into in the next section. Always remember: knowledge is the best defense! 🛡️🌐
Examples of Browser hijackers
Browser hijackers are a persistent and growing threat to computer security. They are often distributed through free software downloads, and once installed, they can cause a range of problems such as changing browser settings, redirecting search queries, displaying unwanted ads, and collecting personal data. Wonders Tab is just one example of such hijackers, and unfortunately, there are many more out there. Myhoroscopepro.com, Trendysearches.com, Searchmenow.gg, and BestSearch.Ai are examples of other browser hijackers similar to Wonders Tab that you should be aware of. By learning to recognize these threats, you can take steps to protect your computer and your privacy.
- BestSearchConverter is a hijacker
- Bar1 New Tab is a browser hijacker
- Media Tab browser hijacker
- Quick App is a browser hijacker
- SearchMusicStream is a browser hijacker
Threat Summary
| Name | Wonders Tab, wonderstab.com redirect |
| Type | Browser Hijacker |
| Primary Objective | Redirect users to bing.com or search.yahoo.com to generate revenue and potentially collect user data. |
| Common Symptoms | Unwanted redirects to wonderstab.com, Altered browser homepage, New toolbars or extensions |
| Primary Infiltration Methods | Malicious Chrome extensions, Bundling with other software, Fake updates |
| Associated Risks | Data breaches, Malware infections, Privacy invasion, Financial losses |
| Underlying Techniques | Replacing legitimate browser extensions, Altering browser or system settings, Blocking restoration of normal settings |
| Primary Target | Google Chrome, but can affect other browsers |
| Removal | Resetting browser settings, Scanning and removal with reputable antivirus software |
How to remove Wonders Tab from Windows 11 (10, 8, 7, XP) 🛠️🚀
When Wonders Tab infiltrates your Windows computer, immediate action is essential. Such potentially unwanted software doesn’t just disrupt your browsing; it poses a genuine threat to your digital safety. In the subsequent steps, we’ll guide you through a clear and concise method to remove Wonders Tab from your Windows system. Dive in, and let’s restore your computer’s health.
To remove Wonders Tab, perform the steps below:
- Uninstall any suspicious programs
- Fix Windows Policies
- Remove Wonders Tab from Chrome
- Scan your computer for malware
Read this section to know how to manually remove the Wonders Tab hijacker. Even if the step-by-step guide does not work for you, there are several free removers below which can easily handle such hijackers.
Uninstall any suspicious programs
The first step is to check your computer for any suspicious programs or extensions and remove them. To do this, go to the Control Panel (on Windows) or Applications (on Mac) and uninstall any programs that you don’t recognize or that you think may be associated with the Wonders Tab hijacker.
|
|
|
|
Fix Windows Policies to Remove a malicious hijacker
Sometimes, the removal is hindered by certain malware-induced policies. By making changes to the Windows Registry and addressing group policies, you can overcome this obstacle. Here’s how:
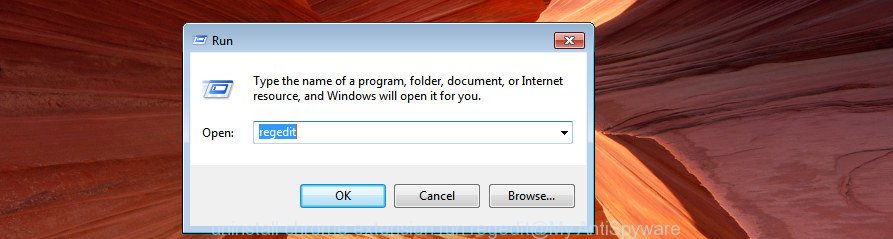
- Open Windows Registry Editor:
- Press the Windows key (🪟) and “R” simultaneously. This will bring up the Run dialog box.
- Type “regedit” and hit Enter. The Windows Registry editor will now be visible.

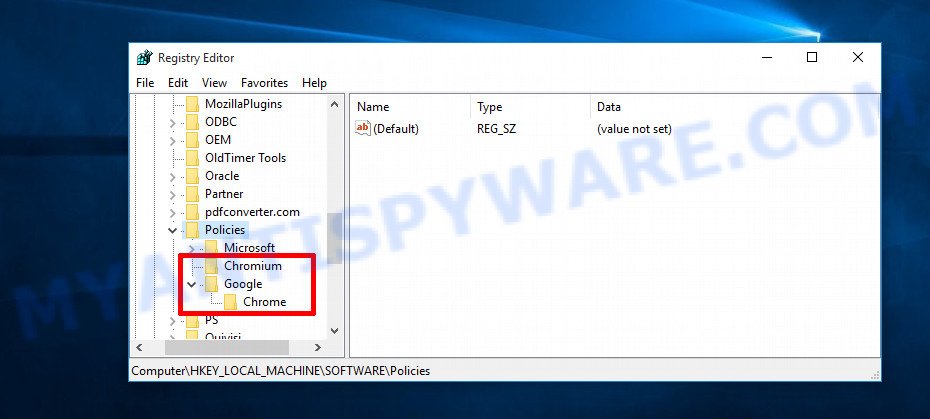
- Navigate and Remove Malicious Registry Entries:
- Head over to “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\”. Use this path as your guide.
- Identify and delete the folders named Chromium and Chrome which are associated with the “Managed by your organization” malware.
- Once done, exit the Windows Registry editor.

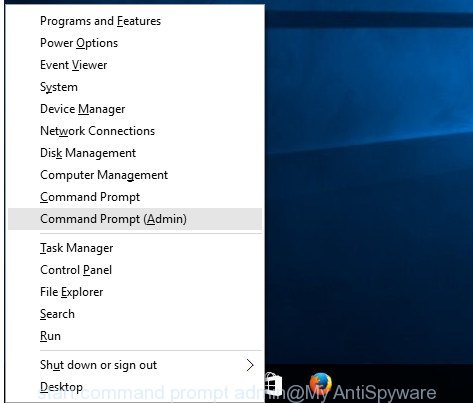
- Address Group Policy Folders:
- Hold the Windows key (🪟) and “X” together to open a quick-access menu.
- From the menu, choose Command prompt (Administrator). You’ll be presented with a command prompt window.

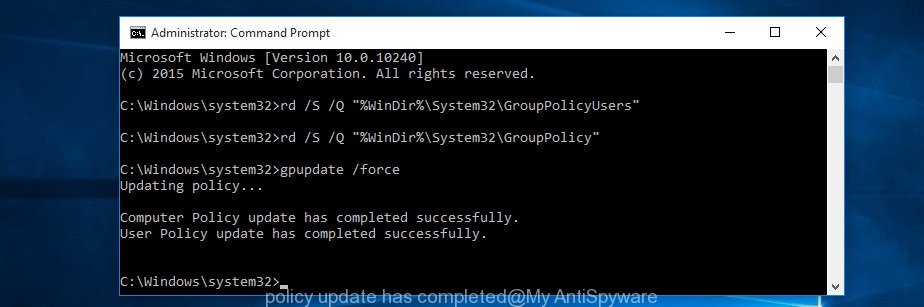
- Execute the Following Commands:
- Input
rd /S /Q "%WinDir%\System32\GroupPolicyUsers"and hit Enter. - Next, type
rd /S /Q "%WinDir%\System32\GroupPolicy"and press Enter. - Lastly, enter
gpupdate /forceand press Enter. If executed correctly, you’ll be greeted with messages indicating both the Computer Policy and User Policy have been updated successfully.

- Input
- Restart Your Computer:
- After executing the above steps, it’s crucial to restart your computer to ensure the changes take effect.
Remember, modifying the registry and group policies are advanced actions. Always proceed with caution and ensure you’re following the steps correctly.
Remove Wonders Tab from Chrome
Having successfully fixed any restrictions that might have prevented the removal of unwanted extensions, it’s now time to tackle and eliminate Wonders Tab from your Chrome browser.
- Access Chrome Extensions: Open your Google Chrome browser. Locate the three horizontal dots at the top-right corner (the Chrome menu button) and click it to reveal a drop-down. From this list, opt for ‘More Tools’ and subsequently select ‘Extensions’. Alternatively, quickly navigate by typing
chrome://extensionsinto Chrome’s address bar. - Inspect and Remove: Examine the list of installed extensions. Identify any unfamiliar or suspicious ones, or those you simply don’t need anymore. Click the “Remove” button beneath these extensions. A confirmation pop-up will appear; press “Remove” again.
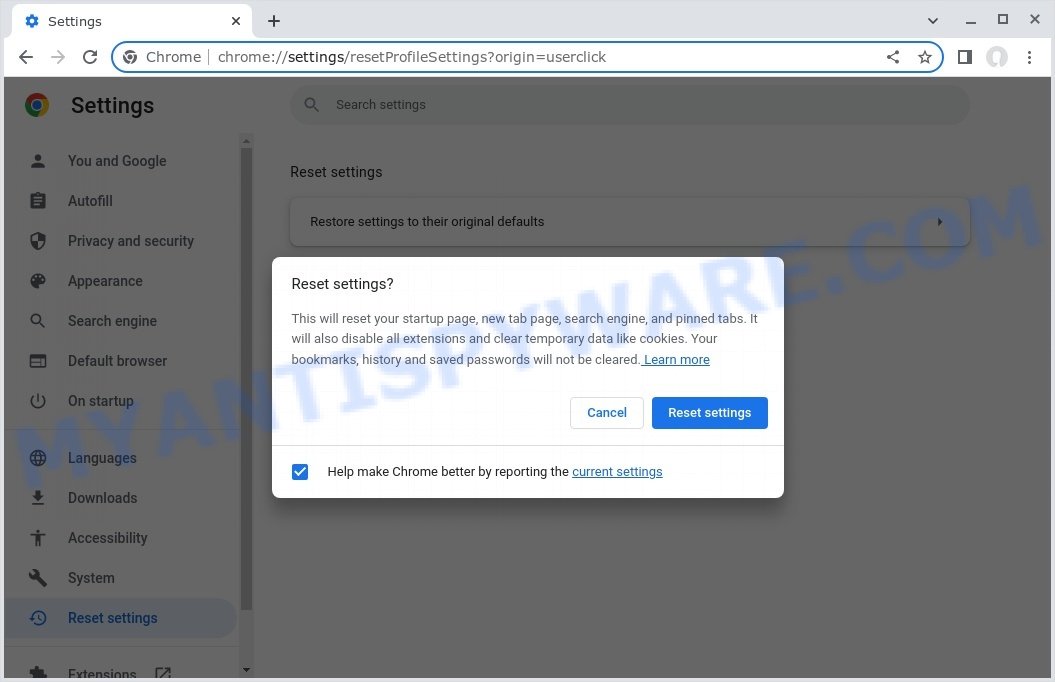
- Reset Your Browser: To ensure no traces remain, consider resetting your browser settings. This action disables all extensions, clears cookies, and undoes unwanted changes but preserves your bookmarks and saved passwords. To do this:
- Revisit the Chrome main menu.
- Choose “Settings”.
- Find and select “Reset settings”.
- Click on “Restore settings to their original defaults”.
- Confirm by selecting the “Reset settings” button.

Note: If an unwanted extension remains despite these steps, consider using a trustworthy antivirus tool to scan your computer for any related malware or threats.
Scan your computer for malware
After you’ve tried to remove Wonders Tab and reset your browser, there might still be hidden problems. Some bad files can stay hidden or look like normal ones. It’s always a good idea to do a full computer scan to catch these. This way, you can be sure everything harmful is gone. Let’s make sure your computer is clean and safe!
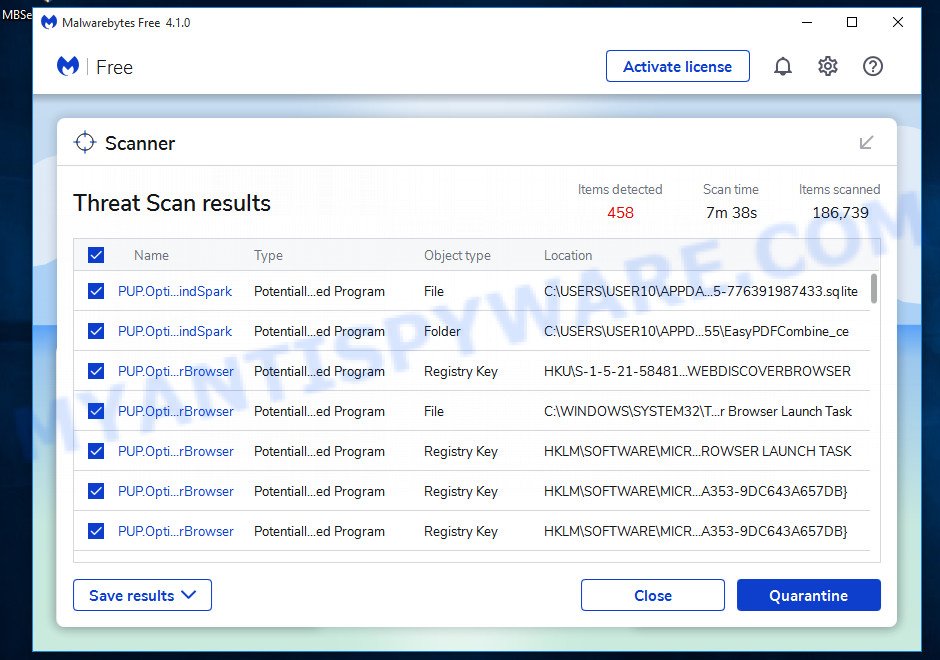
To fully ensure your computer’s safety, consider using MalwareBytes to automatically remove the Wonders Tab hijacker. MalwareBytes is a trusted anti-malware tool with a strong track record. It’s been widely recognized for its efficiency in detecting and eliminating a broad range of threats, from sneaky browser extensions to more aggressive forms of malware. By employing advanced scanning techniques, MalwareBytes digs deep into your system, ensuring no malicious elements go unnoticed. Simply download, install, and run a full scan with MalwareBytes to clear out any lingering threats related to the Wonders Tab or other potential risks.
- Download Malwarebytes by clicking on the link below. Save it on your Windows desktop.
Malwarebytes Anti-malware
327057 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- Once the download is done, close all applications and windows on your personal computer. Open a folder in which you saved it. Double-click on the icon that’s named MBsetup.
- Choose “Personal computer” option and press Install button. Follow the prompts.
- Once installation is finished, scan your computer. Run a full scan of your computer to detect and remove any browser hijackers and other forms of malware. The scan may take several minutes to complete, depending on the size of your hard drive and the speed of your computer.
- Remove detected threats. If the scan finds any threats, click Quarantine to remove them. The software will automatically remove the browser hijacker and any associated malware. After the removal process is complete, restart your computer to ensure that any changes made by the hijacker are fully removed.
The following video demonstrates how to remove hijackers, adware and other malware with MalwareBytes.
What to Do After Removing the hijacker 🤔✅
After successfully removing the Wonders Tab hijacker from your computer, it is important to take some additional steps to ensure that your computer and personal information remain secure. Here are some recommended actions to take:
- It’s important to change your browser settings back to your preferred search engine and homepage. Make sure that Wonders Tab is completely removed from your browser’s settings and that it cannot reappear.
- If you entered any sensitive information such as login credentials or passwords while the browser hijacker was active, change them immediately. This will prevent any potential identity theft or unauthorized access to your accounts.
- To remove any traces of the browser hijacker, clear your browser history and cache. This will help ensure that any data or information collected by the hijacker is removed from your system.
- Use a reputable anti-malware program like Malwarebytes to scan your computer for any remaining malware or potentially unwanted programs (PUPs). This can help ensure that there are no hidden threats or malicious files on your computer.
- Make sure that your browser and operating system are up-to-date with the latest security patches and updates. This can help prevent future security issues and keep your system protected.
- To avoid getting infected with similar malware in the future, be cautious of downloads and only download from reputable sources. Avoid clicking on suspicious links or downloading attachments from unknown sources.
Conclusion 📝👋
The Wonders Tab is a malicious Chrome extension that acts as a browser hijacker. Similar browser hijackers often hide in misleading ads or software bundles, making it easy to sneak onto your computer. When you install them, they can change where your searches go, often sending you to a fake search engine instead of your chosen search site. It’s important to be careful about what apps you install to your computer and where you download them from.
Remember, removing the Wonders Tab hijacker is just the first step. It’s important to remain vigilant and proactive in protecting yourself from similar threats that may emerge in the future. Stay informed, stay cautious, and enjoy a safer browsing experience!