Have you ever seen a pop-up on your Apple device saying “Access To This Apple Device Has Been Blocked” and asking you to contact Apple at +1 (833) 456-0476?
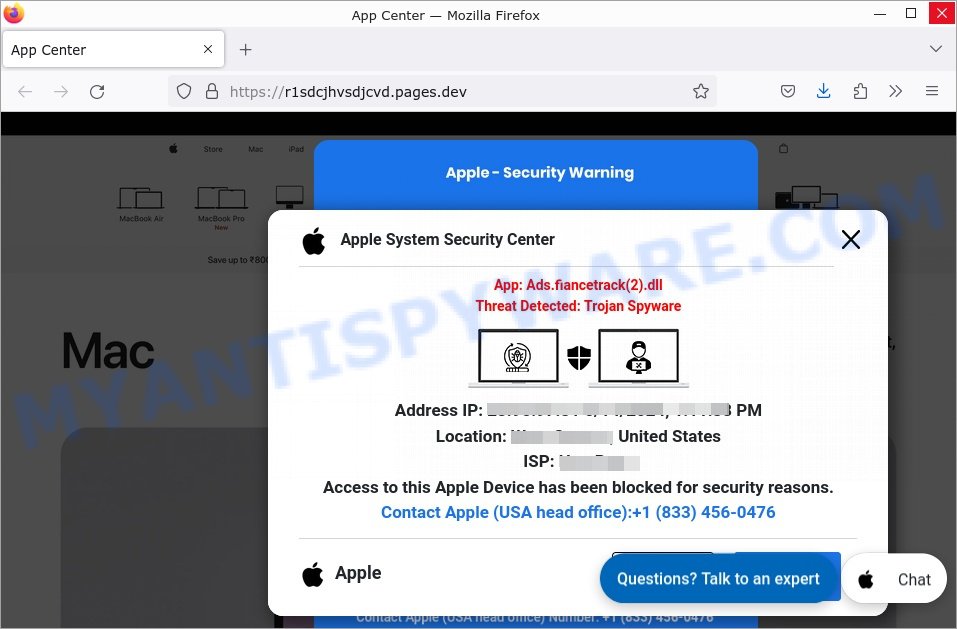
Question: Is this message real? Can my Apple device really be blocked?
Investigation Findings: No, this message is fake. The alert mentions a file called ‘Ads.fiancetrack(2).dll’, which isn’t something used on Macs. The phone number is linked to tech support scammers, and the scam comes from malicious websites with strange names like ‘r1sdcjhvsdjcvd.pages.dev’.
Answer: “Access To This Apple Device Has Been Blocked” pop-up is a fraudulent scam. 💡 To protect yourself from scams like this, always ignore pop-ups that ask you to call a number. Additionally, update your security software regularly and be cautious of suspicious websites.
Table of Contents
- 🚨 Is the “Access To This Apple Device Has Been Blocked” Pop-up a Scam?
- 🕵️♀️ How the “Access To This Apple Device Has Been Blocked” Pop-up Scam Works
- 📌 Beware of Similar Scams
- 🔍 How to Spot Fake Apple Security Pop-up Scams
- 🛡️ How to remove “Access To This Apple Device Has Been Blocked” pop-ups
- 🚫 Protecting Yourself from the”Access To This Apple Device Has Been Blocked” Scam
🚨 Is the “Access To This Apple Device Has Been Blocked” Pop-up a Scam?
Yes, the pop-up alert claiming your Apple device is infected with high-risk malware and urging you to call a support number is definitely a scam. 🚫 If you encounter such a pop-up, exercise extreme caution. The assertions are completely false and designed to create panic, misleading you into contacting fake support services where you may be manipulated into providing personal information or making payments.
Background on the “Access To This Apple Device Has Been Blocked” Scam:
This scam is a form of tech support fraud where fraudsters impersonate major tech companies like Apple. The scammers create alarming pop-up messages that warn of malware infections, compromised personal data, and blocked device access, insisting that the issues can only be resolved through the phone numbers provided in the message.
However, Apple and other legitimate tech companies have clarified that they do not send unsolicited warnings or demand remote access to devices via such pop-ups. Official support usually requires going through proper channels on the company’s official website, not through unsolicited pop-ups or phone calls.
According to the Federal Trade Commission, Americans lost over $328 million to tech support scams, a figure that underscores the prevalence of these fraudulent activities. Apple users also report numerous complaints globally from people who’ve been the victim of a tech support scam, highlighting the widespread nature of the issue.
These scams have become increasingly sophisticated, using scare tactics to trick users into panicking and acting hastily. Government and cybersecurity organizations have issued warnings about these scams, noting they have affected countless individuals globally, exploiting the trust people have in their devices and supposed tech support.
The fraudulent pop-ups often claim an “urgent need” to contact support and include alarming, but entirely false, reports of security breaches, directing victims to call a number where they are further scammed.
🚩 Red Flags to Watch Out For:
To protect yourself, be aware of these warning signs of the scam: 🔍🛡️
- 📧 Unsolicited Alerts: Unexpected pop-ups claiming that your Apple device is severely compromised.
- 🔗 Suspicious Phone Numbers: These scams include phone numbers that are not associated with the claimed company’s official support contacts.
- ⏳ Urgency and Imposed Deadlines: These messages create a sense of urgency, pressuring you into immediate action to fix problems that do not actually exist.
- 💳 Requests for Payment: Be wary of any demands for payment over the phone for tech support or malware removal, especially if you did not initiate the contact.
- 👤 Anonymity of the Communication: Scammers might use generic greetings or lack details that a legitimate tech company would have regarding your device or account status.
- 🔄 No Verifiable Evidence: Genuine alerts from tech companies will provide a clear path to verify the issue independently through official channels, not force immediate action over the phone.
🕵️♂️ How the “Access To This Apple Device Has Been Blocked” Pop-up Scam Works
The “Access To This Apple Device Has Been Blocked” pop-up scam is a form of social engineering designed to instill panic and urgency, tricking users into believing their devices are severely compromised. Understanding the mechanics of this scam is crucial for your digital safety. 💡🔐
🚨 Exploiting Your Security Concerns
The scam typically starts with a pop-up alert claiming your device has been infected with a high-risk virus or malware. It exploits your natural concern for personal data security, compelling you to follow the scammer’s instructions without skepticism.
🔗 Mimicking Official Apple Alerts
The fraudulent pop-up includes a phone number and often simulates an Apple security interface to appear legitimate. This deception is aimed at convincing you that the alert is genuinely from Apple.
🎭 Fabricated Threats and Immediate Actions
Upon engaging with the scam, you’re presented with alarming messages about stolen personal information and threats to your device’s integrity, creating a false sense of immediacy. Scammers pressure you to act quickly to resolve these non-existent threats.
📥 Soliciting Direct Contact
The pop-up urges you to call a specific phone number, where so-called technicians offer to help remove the malware. This step is aimed at establishing direct communication to further manipulate victims.
🔄 Creating a False Sense of Urgency
Scammers fabricate an emergency situation, insisting that immediate action is necessary to prevent data loss or further infections. This tactic is used to push victims into making hasty decisions without verifying the information.
🕳️ Remote Access and Financial Exploitation
Once contact is made, the fake technicians often request remote access to your device under the pretense of technical support, which they use to install actual malware or steal sensitive information. Additionally, they may ask for payment for their “services”, directly targeting your financial resources.
By understanding these tactics, you can better protect yourself against the “Access To This Apple Device Has Been Blocked” pop-up scam and similar threats. Always be skeptical of unsolicited warnings and contact tech support through verified channels only.
Beware of Similar Scams
The ‘Access To This Apple Device Has Been Blocked’ scam is only one example of many scams online that aim to trick you into giving up your personal information and money. Scammers are using more sophisticated methods, including phishing sites, fake security alerts, and disguising themselves as legitimate antivirus software. Other recent scams similar to this one include the Call Microsoft Support Pop-Up Scam, McAfee Safety Warning Pop-Up Scam, and the ‘A Malicious Item Has Been Detected’ Pop-Up Scam.
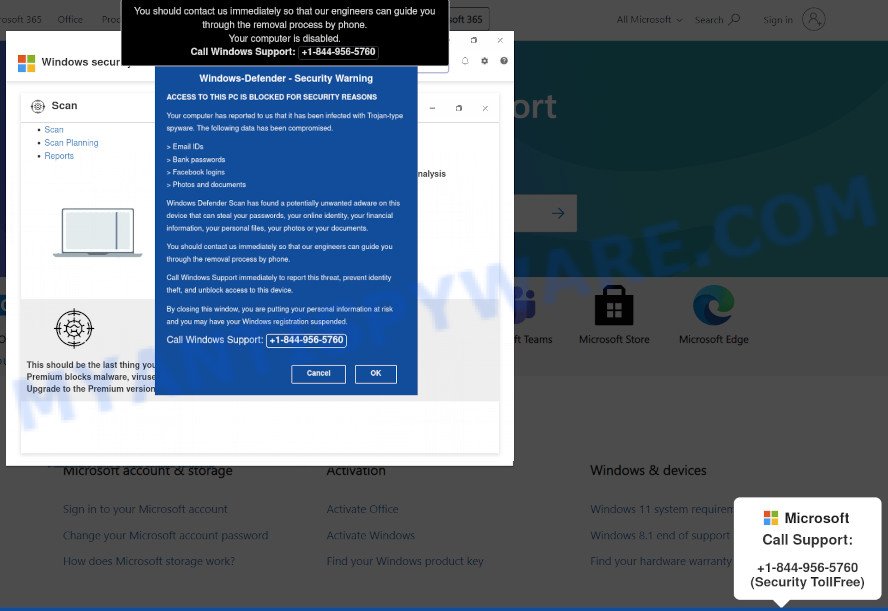
Call Microsoft Support Pop-Up Scam
This scam targets users with fake alerts claiming their computer is infected and urges them to call a fake Microsoft support number.
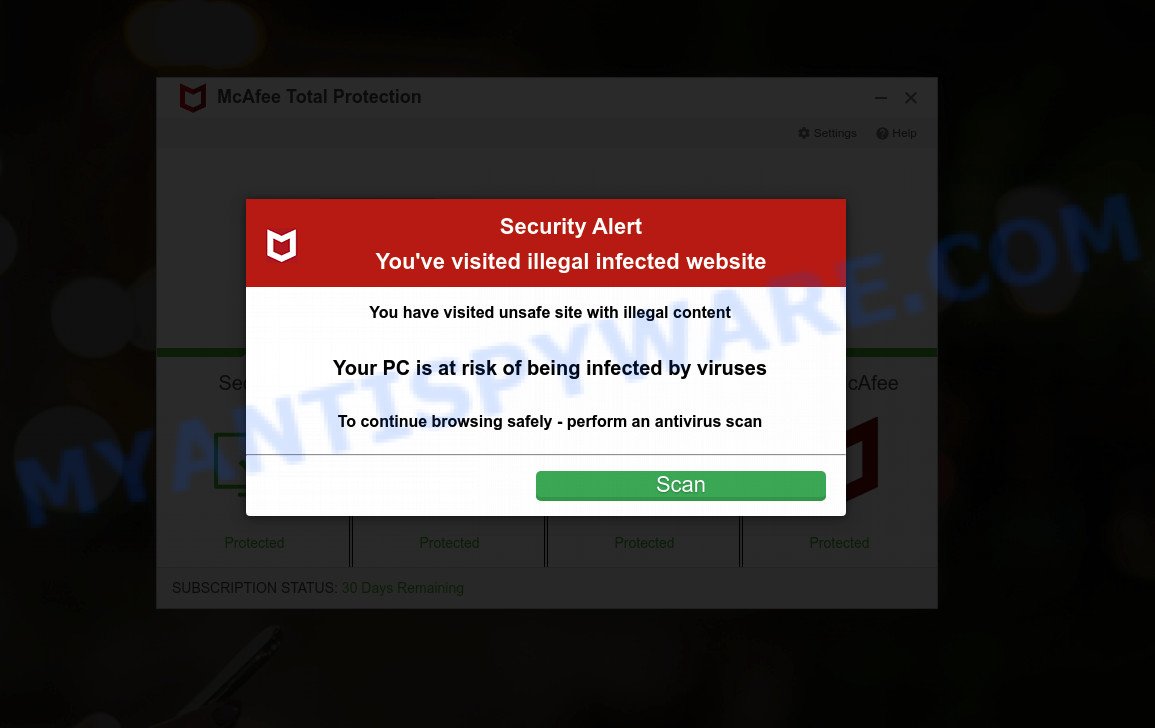
McAfee Safety Warning Pop-Up Scam
In this scam, users receive fake alerts that appear to be from McAfee, warning of security threats and prompting them to call a bogus support number.
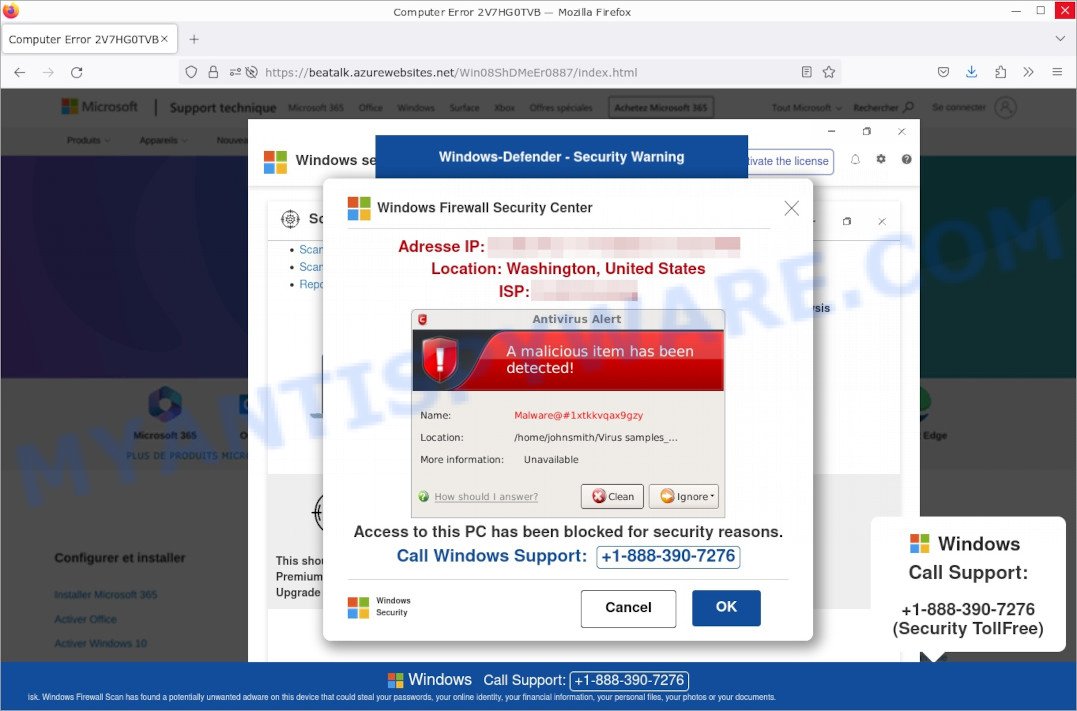
‘A Malicious Item Has Been Detected’ Pop-Up Scam
This particular scam involves fake warnings about malware detection, attempting to scare users into contacting fraudulent support services.
All these scams share a common strategy: they display alarming messages to trick you into contacting fake support numbers or visiting malicious websites.
How to Spot Fake Apple Security Pop-up Scams
Scammers are getting better at making fake alerts look real, especially those that falsely use the Apple name. These pop-ups are designed to scare you into thinking your device has serious problems. It’s important to know how to spot these fakes to keep your device safe from harm.

Here, we’ll show you how to identify “Access To This Apple Device Has Been Blocked” scams. These are fake warnings that pop up in your browser, falsely claiming that your computer is at risk and urging you to call a support number. Recognizing these scams helps you avoid them.
- Look at the pop-up’s design. Scam pop-ups might look similar to Apple’s actual alerts but often have small mistakes in the design or layout, such as low-quality logos or unusual fonts.
- Read the message carefully. Real Apple warnings never ask you to call a phone number. Be wary of any pop-up that does.
- Check the address in your browser’s address bar. A genuine Apple warning will not appear in your web browser but rather through official software. If a pop-up appears in your browser claiming to be from Apple, check the URL – it’s likely not from Apple if the website address seems odd or unrelated.
- Notice the greeting used. Fake alerts often start with vague greetings like “Dear user” or “Hello, Apple user,” which Apple does not use.
- Ignore sudden contact requests. If a pop-up unexpectedly says your device is infected and asks you to call a number, it’s almost certainly a scam. Apple does not alert you to viruses or security issues through your web browser.
- Be careful with pop-up interactions. Do not click anywhere on a suspicious pop-up, including the ‘close’ button, as this could start a malware download. Instead, close your entire browser using Force Quit Applications (press Command + Option + Escape).
Threat Summary
| Name | “Access To This Apple Device Has Been Blocked” Pop-up Scam |
| Type | Tech Support Scam |
| Fake Claims | Claims of an Apple device being blocked due to spyware infection, urging users to call a fake support number to prevent identity theft and unblock the device. |
| Scam texts | App: Ads.fiancetrack(2).dll Threat Detected: Trojan Spyware Access to this Apple Device has been blocked for security reasons. Contact Apple (Toll-Free): +1-888-238-0084 Apple Deny Allow |
| Related Domains | r1sdcjhvsdjcvd.pages.dev, vresdwaoijh00ms13.z20.web.core.windows.net, … |
| Scammers contacts | +1 (888) 238-0084, +1 (833) 456-0476, +1 (888) 683-7956, +1 (888) 926-9410, +1 (888) 741-8176, … |
| Distribution | Malicious advertisements, compromised websites, phishing emails, and software bundles |
| Damage | Deceives users into paying for unnecessary support services, risk of malware installation, and unauthorized access to personal information. |
| Symptoms | Unsolicited pop-ups claiming malware detection, fake Apple security alerts, and persistent prompts to call a bogus support number. |
| Removal | Terminate the browser process, reset browser settings, scan for malware using trusted security software, avoid restoring previous browsing sessions. |
How to remove Access To This Apple Device Has Been Blocked pop-ups
If you have encountered “Access To This Apple Device Has Been Blocked” pop-ups, you should not trust the message and refrain from clicking any buttons or links that appear on the page. Instead, follow the steps below to remove the pop-up and any potential malware from your computer:
To remove Access To This Apple Device Has Been Blocked pop ups, complete the steps below:
- Close the pop-up
- Clear your browsing history
- Disable push notifications
- Scan your computer for malware
- Reset your browser settings
Close the pop-up
Closing the pop-up is the first step you should take when dealing with the “Access To This Apple Device Has Been Blocked” scam. Although it may seem like a simple task, some users may find it challenging, especially if the pop-up is designed to be persistent and difficult to close. This step is crucial because it prevents the user from falling into the trap set by the scammers and clicking on any of the buttons or links that can lead to further harm.
- Don’t click on anything within the pop-up as it could lead to further harm.
- Look for a small “X” or “Close” button within the pop-up window. Click on it to close the window.
- If there is no “X” or “Close” button, try pressing the “Esc” key on your keyboard to close the pop-up.
- If the pop-up still won’t close, try forcing the browser to quit:
- On a Mac, press “Command + Option + Escape” to open the Force Quit Applications window. Select your browser and click “Force Quit.”
- On a PC, open Task Manager by pressing “Ctrl + Shift + Esc” on your keyboard (or “Ctrl + Alt + Delete” and then select “Task Manager”). Find the browser window that the pop-up is in, right-click on it, and select “End Task” to force close the window.
Clear your browsing history
Clearing your browsing history is an important step in removing “Access To This Apple Device Has Been Blocked” pop-ups. These pop-ups often come from malicious websites that can be stored in your browsing history.
By clearing your browsing history, you can get rid of any traces of these websites and prevent the pop-ups from reappearing. In this step, we will walk you through how to clear your browsing history on Safari.
- Open Safari on your Apple device.
- Click on “Safari” in the menu bar at the top of the screen.
- Select “Clear History” from the dropdown menu.
- In the pop-up window that appears, choose the time range for which you want to clear your browsing history (e.g., “the last hour,” “today,” “today and yesterday,” or “all history”).
- Click on the “Clear History” button.
- Wait for Safari to finish clearing your browsing history. This may take a few moments, especially if you have a lot of browsing data stored.
- Close and restart Safari to ensure that the changes take effect.
Disable push notifications
If you’re experiencing persistent push notifications from websites that are showing Access To This Apple Device Has Been Blocked scams, the best course of action is to disable push notifications altogether. Disabling push notifications prevents malicious websites from showing you unwanted pop-ups and alerts, which can help protect your computer from further harm. In this step, we’ll walk you through the process of disabling push notifications in your web browser.
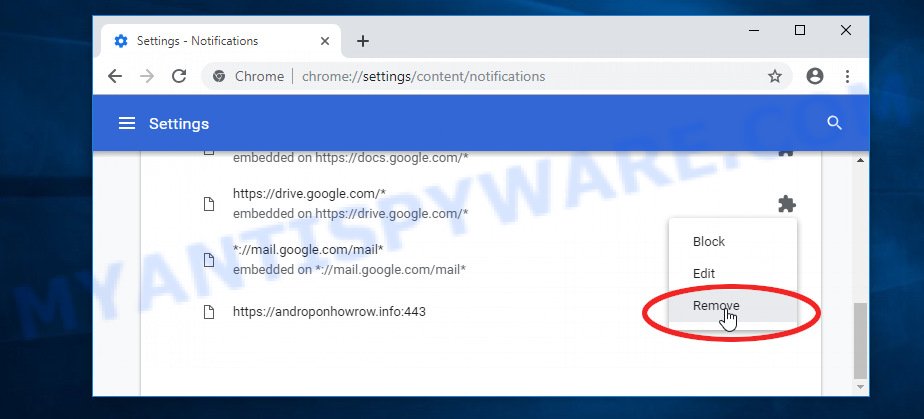
Google Chrome:
- Click on ‘three dots menu’ button at the top-right corner of the Google Chrome window.
- Select ‘Settings’, scroll down to the bottom and click ‘Advanced’.
- At the ‘Privacy and Security’ section click ‘Site settings’.
- Click on ‘Notifications’.
- Locate the Access To This Apple Device Has Been Blocked website and click the three vertical dots button next to it, then click on ‘Remove’.
Android:
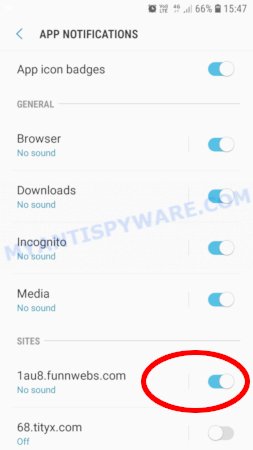
- Open Chrome.
- Tap on the Menu button (three dots) on the top right corner of the screen.
- In the menu tap ‘Settings’, scroll down to ‘Advanced’.
- In the ‘Site Settings’, tap on ‘Notifications’, locate the Access To This Apple Device Has Been Blocked URL and tap on it.
- Tap the ‘Clean & Reset’ button and confirm.
Mozilla Firefox:
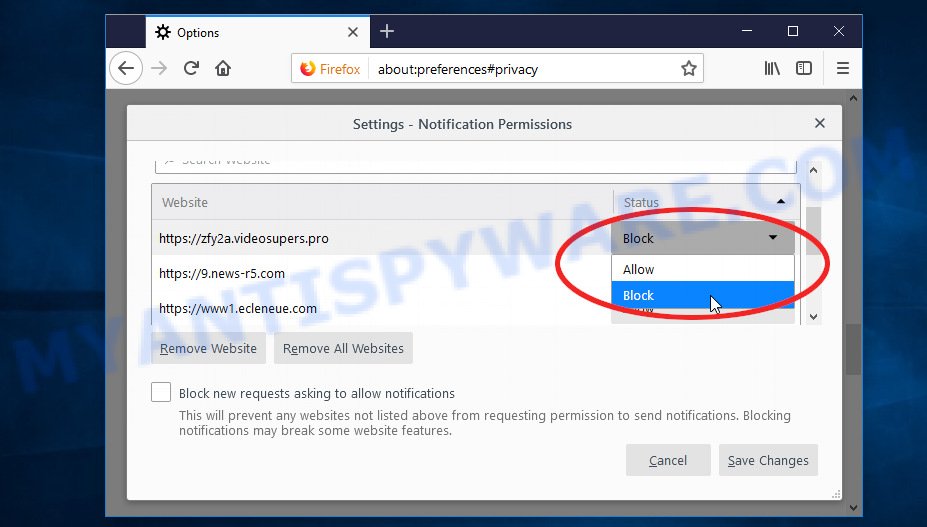
- In the top right corner, click the Firefox menu (three bars).
- In the drop-down menu select ‘Options’. In the left side select ‘Privacy & Security’.
- Scroll down to ‘Permissions’ section and click ‘Settings…’ button next to ‘Notifications’.
- Find the Access To This Apple Device Has Been Blocked website address, other suspicious URLs, click the drop-down menu and select ‘Block’.
- Click ‘Save Changes’ button.
Edge:
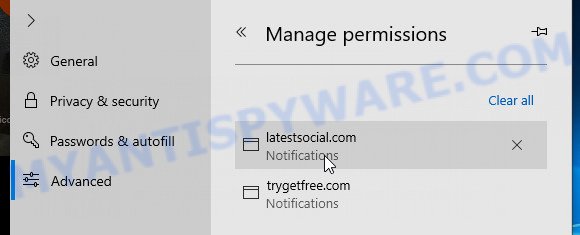
- Click the More button (three dots) in the top-right corner of the window.
- Scroll down, locate and click ‘Settings’. In the left side select ‘Advanced’.
- In the ‘Website permissions’ section click ‘Manage permissions’.
- Disable the on switch for the Access To This Apple Device Has Been Blocked domain.
Internet Explorer:
- Click the Gear button on the top-right corner of the browser.
- Select ‘Internet options’.
- Click on the ‘Privacy’ tab and select ‘Settings’ in the pop-up blockers section.
- Locate the Access To This Apple Device Has Been Blocked website and click the ‘Remove’ button to delete the site.
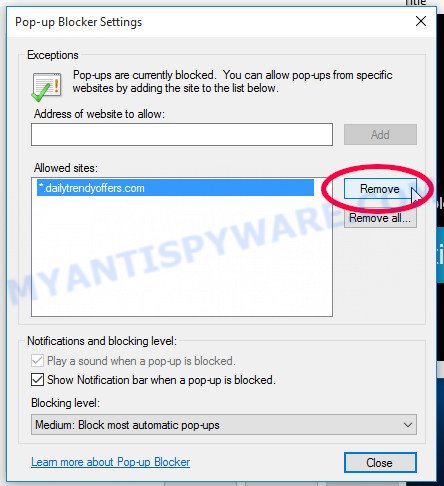
Safari:
- Go to ‘Preferences’ in the Safari menu.
- Select the ‘Websites’ tab and then select ‘Notifications’ section on the left panel.
- Find the Access To This Apple Device Has Been Blocked site and select it, click the ‘Deny’ button.
Scan computer for malware
If you have encountered the Access To This Apple Device Has Been Blocked pop-up scam, it is possible that your computer has been infected with malware. In order to ensure that your system is completely clean, it is important to perform a thorough scan for malware. This will help to identify any malicious files or programs that may be hiding on your computer and remove them to prevent further damage.
Malwarebytes is a reputable anti-malware program that can effectively detect and remove adware, potentially unwanted programs and malware. It has a user-friendly interface and offers both free and paid versions, with the paid version offering real-time protection and other advanced features. To use Malwarebytes to remove malicious software, you can download and install the program, perform a scan of your system, and follow the prompts to remove any detected threats.
Download MalwareBytes Free on your Mac by clicking the link below.
20944 downloads
Author: Malwarebytes
Category: Security tools
Update: September 10, 2020
Once the download is finished, close all software and windows on your MAC. Run the saved file. Follow the prompts.
MalwareBytes will automatically start, and you’ll see its main screen.
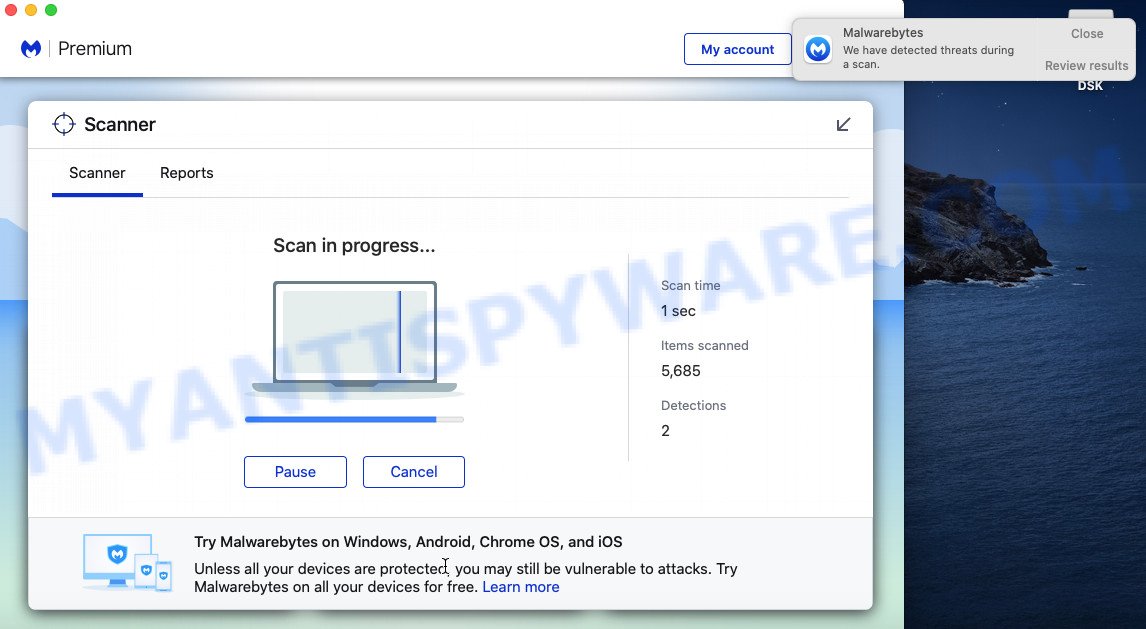
Now press the “Scan” button to perform a system scan for the adware causing the “Access To This MAC Has Been Blocked” pop-ups. This scan can take some time, so please be patient. While MalwareBytes is scanning, you may see the number of threats it has identified.
Once the system scan is complete, you’ll see a list of all detected threats on your Mac. All found threats will be marked. You can remove them by simply pressing the “Quarantine” button. MalwareBytes Anti-Malware will move the selected threats to Quarantine.
Reset your browser settings
If the Access To This Apple Device Has Been Blocked pop-ups persist even after clearing your browsing history, disabling push notifications, and scanning your computer for malware, resetting your browser settings might be the next step to take. Resetting your browser settings can remove any unwanted extensions or changes made to your browser that may be causing the pop-ups to appear.
To reset your browser settings in Safari:
- Open Safari and click on “Safari” in the top menu bar.
- Select “Preferences” from the drop-down menu.
- Go to the “Privacy” tab and click on “Manage Website Data.”
- Click “Remove All” to delete all website data.
- Go to the “Extensions” tab and disable any suspicious extensions.
- Restart Safari.
To reset your browser settings in Google Chrome:
- Open Chrome and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down to the bottom of the page and click on “Advanced.”
- Scroll down to the “Reset and cleanup” section and click on “Restore settings to their original defaults.”
- Click “Reset settings” to confirm.
To reset your browser settings in Mozilla Firefox:
- Open Firefox and click on the three-line icon in the top-right corner.
- Select “Help” from the drop-down menu and then click on “Troubleshooting Information.”
- Click on the “Refresh Firefox” button in the top-right corner.
- Click “Refresh Firefox” again to confirm.
After resetting your browser settings, be sure to check for any remaining suspicious extensions and remove them if necessary.
Protecting Yourself from the Access To This Apple Device Has Been Blocked Scam
Now that you know how the Access To This Apple Device Has Been Blocked scam works, how to identify similar scams, and how to remove the pop-ups, it’s important to take steps to protect yourself from falling victim to this or similar scams in the future.
Here are some additional steps you can take to protect yourself:
- Install reputable antivirus software. By installing antivirus software, you can help prevent these types of scams from infecting your computer in the first place. Make sure to keep your antivirus software up to date and run regular scans to ensure your computer remains protected.
- Be wary of emails or links that claim to be from legitimate companies, such as McAfee, especially if you didn’t request any information. Don’t click on links in emails from unknown sources or download attachments from them.
- Keeping your software up to date is one of the easiest and most effective ways to prevent security breaches. Software updates often contain security patches that fix vulnerabilities, so make sure to install them as soon as they become available.
- Educate yourself on common scams. Knowledge is power, and being aware of common scams and tactics used by cybercriminals can help you recognize and avoid them. Stay informed by reading up on the latest scams and how to protect yourself against them.
Conclusion
The “Access To This Apple Device Has Been Blocked” pop-up scam manipulates users with fake security alerts that resemble official Apple warnings. This scam skillfully deploys convincing pop-ups, alarming users with messages about non-existent malware infections, and prompts them to call a supposed support number for assistance. Individuals are misled into believing they are securing their computer by contacting these fake support lines. However, the actual intent behind these pop-ups is to deceive users into paying for unnecessary technical support services or granting remote access to their systems.
Bottom Line: Be wary of any unexpected security warnings that urge you to call a support number, especially those that mimic trusted entities like Apple. The safest course of action is to dismiss these pop-ups without interaction. 🛡️💻
Stay vigilant and always verify; any alert that urges immediate action or offers quick fixes over a phone call is likely a scam. 🤔