⚠️ Did you get an email with the subject “I own very sensitive information about your web activities” that starts with “Greetings! First of all, let me tell you, you are one of a kind”?
Here’s what’s going on: The email claims to have gained full access to your devices and accounts several months ago, threatening to release videos and other private data unless you pay $1280 in Bitcoin. You’re instructed to act quickly, within 48 hours, to prevent this.
But here’s the truth: There is no real evidence or compromising material. The scammer uses intimidation and false claims to frighten you into paying. Sending money won’t solve the problem; it may increase your risk of further scams.
💡 The “I own very sensitive information about your web activities” email is a scam. Despite its alarming content, it’s a common form of online extortion known as sextortion. This scam uses fear as a weapon to manipulate its targets. Remember, complying with the scammer’s demands doesn’t guarantee safety; it just exposes you to more risks. Always question the legitimacy of emails that demand money or threaten to expose personal information. Being informed and cautious is your strongest protection online.
Table of Contents
🚨 Is the “I own very sensitive information” Email a Scam?
Yes, this email, which starts with “Greetings! First of all, let me tell you, you are one of a kind!“, is a classic example of an extortion scam. 🚫 If you’ve received an email with this subject line or a similar message attempting to blackmail you by claiming to have compromising information, be very cautious. These threats are not based on real incidents but are designed to exploit your fear and coerce you into paying a ransom.
Scam Claims:
- I hacked your operating system several months ago and gained full access to all your devices and accounts.
- I have been monitoring your activities, including your visits to adult websites, through a keylogger and webcam streaming.
- Your devices were compromised with malware, allowing me full access to view and record your screen and use your camera and microphone without permission.
- I have obtained your confidential information contained in your emails and chat messages.
- Your antivirus and spyware defender software were ineffective against my sophisticated methods.
- I have created a video compilation that shows you engaging in private activities, juxtaposed with the content you were viewing.
- All I require is a payment of $1280 USD in Bitcoin to a specified account.
- Once the payment is received, I will delete all recordings and cease further contact.
- You have only 48 hours to complete the transaction after opening this email.
- If you disclose this communication to anyone, I will distribute the compromising material to your contacts.
The email uses threats and fear to create a sense of urgency. 🚨 The goal? To coerce you into sending money to the scammer without any real proof of the claimed videos. These scammers capitalize on the panic and shame of their victims to extort money.
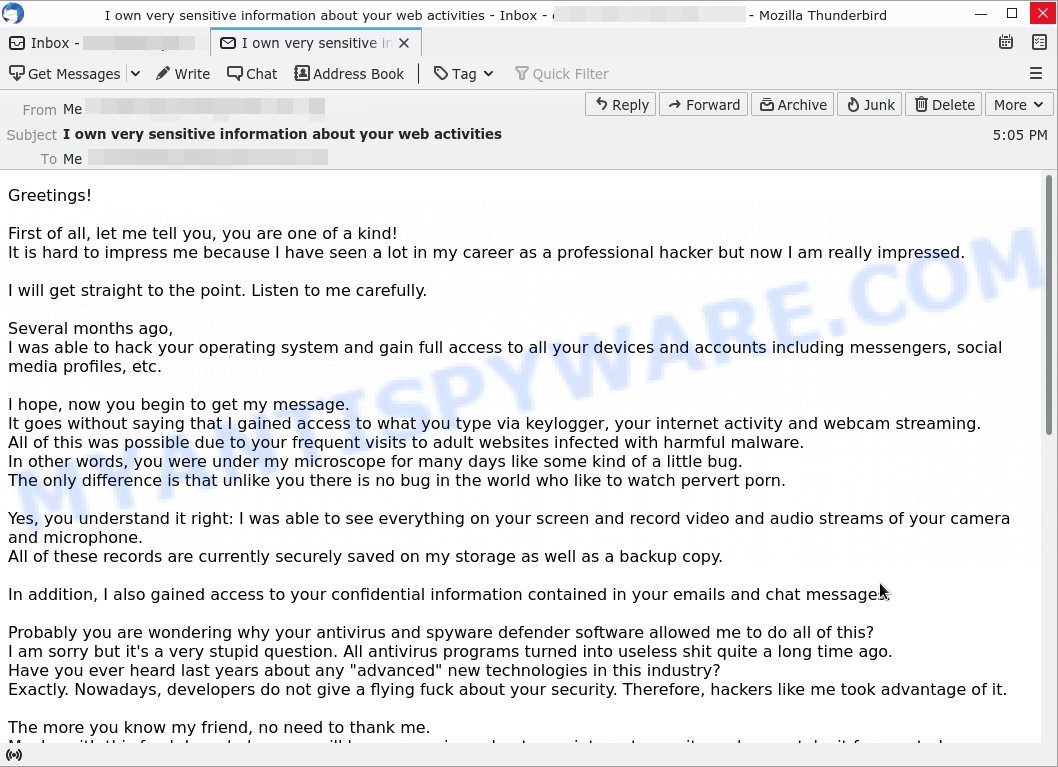
The email read as follows:
Greetings!
First of all, let me tell you, you are one of a kind!
It is hard to impress me because I have seen a lot in my career as a professional hacker but now I am really impressed.I will get straight to the point. Listen to me carefully.
Several months ago,
I was able to hack your operating system and gain full access to all your devices and accounts including messengers, social media profiles, etc.I hope, now you begin to get my message.
It goes without saying that I gained access to what you type via keylogger, your internet activity and webcam streaming.
All of this was possible due to your frequent visits to adult websites infected with harmful malware.
In other words, you were under my microscope for many days like some kind of a little bug.
The only difference is that unlike you there is no bug in the world who like to watch pervert porn.Yes, you understand it right: I was able to see everything on your screen and record video and audio streams of your camera and microphone.
All of these records are currently securely saved on my storage as well as a backup copy.In addition, I also gained access to your confidential information contained in your emails and chat messages.
Probably you are wondering why your antivirus and spyware defender software allowed me to do all of this?
I am sorry but it’s a very stupid question. All antivirus programs turned into useless shit quite a long time ago.
Have you ever heard last years about any “advanced” new technologies in this industry?
Exactly. Nowadays, developers do not give a flying fuck about your security. Therefore, hackers like me took advantage of it.The more you know my friend, no need to thank me.
Maybe with this fresh knowledge, you will be more serious about your internet security and never take it for granted anymore.With that out of the way, let’s cut to the chase. Using your recordings I made a video compilation,
which shows on the left side the controversial porn scenes of you happily masturbating to,
while on the right side it demonstrates the video you were watching at that moment.. ^.^There are only 48 hours left since the moment you receive this email until I send this video to all your email and messenger contacts.
But there is more, guess what? I can also make public all your emails and chat history.You are sick fuck in love with freaky adult content but you are not mentally retarted so I would like to believe, you do not want to let this happen.
Right? Only the most stupid man in the world would be happy if his friends, loved ones and colleagues suddenly knew about something like this.In other words, there is no way back. It cannot be fixed. However, there is a way forward that both of us can benefit from.
I am a reasonable guy and have no intention to ruin your life for nothing. I’d better like to gain something instead.Here is your salvation – transfer the Bitcoin equivalent of 1280 USD to my Bitcoin account
(you can google the process in case you don’t know how to do that).Here is my Bitcoin address: 16UqxYLX49MkFkgqsj1NcKiNVQMRCL8pnp
Once I am notified of receiving it, I will delete all those videos and disappear from your life for good.
As I mentioned, you have only 48 hours to make a transaction after you open this email.Believe me, I am always one step ahead so no way in hell you could fool me.
If I discover that you shared this message with others, I will send and publish your videos in no time.P.S. It’s in your power to make it nice for both of us.
How the scam works
When you receive an unexpected email with the subject “I own very sensitive information about your web activities“, it can be really shocking 🚨. This feeling is especially strong if the email starts off with an intimidating tone meant to catch you off guard. You might wonder, “How do they know so much about me?” But in reality, these scammers probably don’t have any information about you; they’re just trying to scare you into doing what they want.
The email will likely contain fake threats, claiming they’ve hacked your devices and recorded you in compromising situations 🎥. They make the message sound alarming and frightening on purpose, to make you panic: “Is this really happening?”
Then, they might claim they’ve used advanced hacking techniques to gain complete access to your devices and accounts, asserting they can control your digital life 💻. The fact that they don’t show any real proof is a clear sign this is a scam 🚩. They’re exploiting your fear of technology to intimidate you, not actually employing any real hacking.
Finally, they’ll ask for money 💰. They demand payment in Bitcoin because it’s difficult to trace. They try to make you feel like you must pay immediately. But even if you do pay, it doesn’t guarantee safety, and they might target you again.
As you reflect on the email, you might wonder, “Am I really in danger?” or “Can this person actually do what they claim?” 🕵️♂️ Typically, these threats are just designed to intimidate you, not actual cyber threats.
What should you do? It’s best not to respond to the scammer or send any money. Instead, focus on your online security: change your passwords, check your devices for real threats, and consider reporting the scam to the authorities if the email includes threats or demands for money 🔐. This situation reminds us to always be vigilant and take steps to protect ourselves online.
To sum up, this scam tries to make you feel scared and rushed. If you receive an email like this, don’t engage with the scammer and don’t send any money. Just delete the email. And ensure your computer is protected with good antivirus software and you use strong, unique passwords for all your accounts to prevent scams like this.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
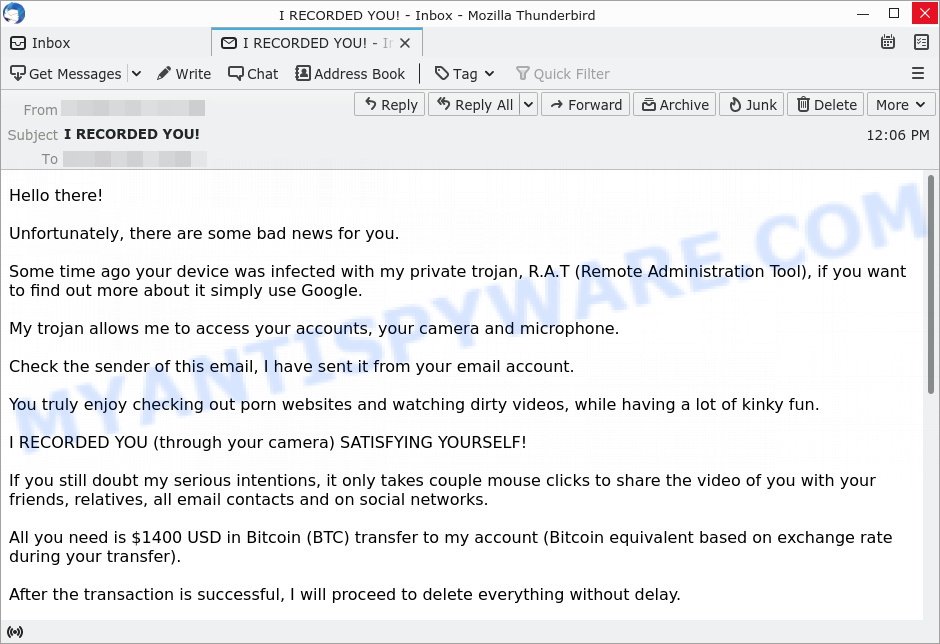
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
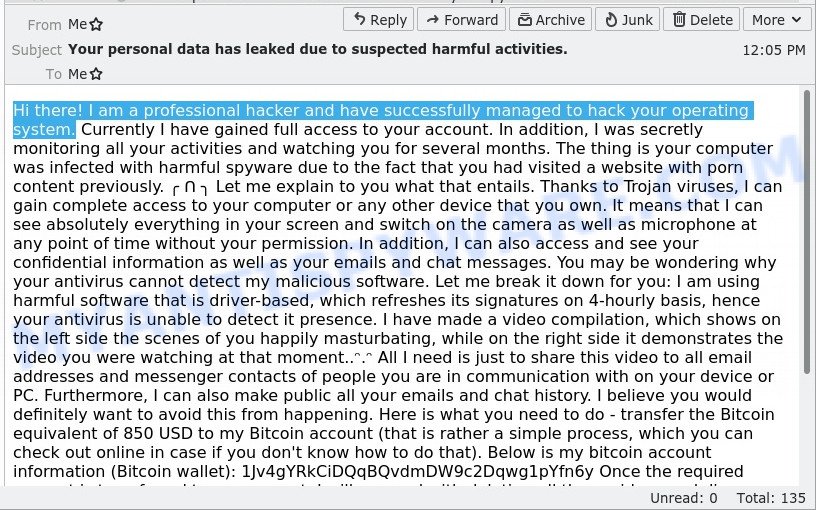
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
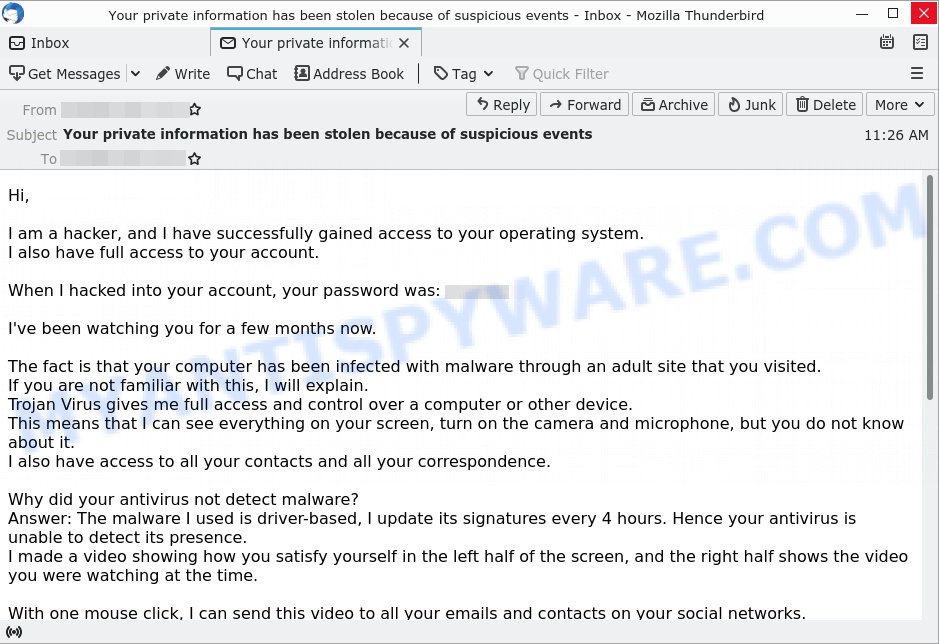
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “I own very sensitive information” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | ‘I own very sensitive information about your web activities.’ Email Scam |
| Type | Phishing/Sextortion |
| Email Subject | I own very sensitive information about your web activities. |
| Ransom amount | $1280 USD (in Bitcoin equivalent) |
| Bitcoin Address | 16UqxYLX49MkFkgqsj1NcKiNVQMRCL8pnp |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The “I own very sensitive information about your web activities” email is a typical example of a sextortion scam, aiming to scare and trick you into sending money. These emails make scary threats and ask for payment, usually in Bitcoin, pretending to protect your reputation. But don’t be fooled – these threats are fake, meant to make you panic.
Key Point: Don’t interact with these emails. The best thing to do is to ignore them and focus on keeping your online accounts safe. 🛡️💻
Stay alert and think carefully; an email that immediately frightens you or seems overly complex is likely a scam. 🤔