Have you received an email claiming a programmer has hacked your device’s operating system? The email might assert that they infiltrated your device via adult websites you’ve visited and that they now have control over your screen, microphone, and camera. It could also claim to have compiled a video showing you viewing adult content and demand $1200 in Bitcoin to delete the video and cease further contact.
Question: Is it true that my system has been hacked, and do I need to pay them?
Investigation Findings: This type of email is a classic example of a “sextortion scam“. Scammers do not actually have access to your device. They use these threats to intimidate you into sending money.
Answer: The ‘Hey. I am a programmer who hacked your device’s operating system.’ email is a deceptive scam. 💡 To protect yourself from scams like this, never respond to such emails or send money. Ensure your antivirus software is current and perform a virus scan if you’re concerned. Consider changing your email passwords to strengthen your security.
Table of Contents
🚨 Is the ‘Programmer who hacked your device’ Email a Scam?
Yes, the email claiming that a programmer has hacked your operating system, has been monitoring you, and threatening to expose compromising information unless you pay $1200 in Bitcoin is a scam. 🚫 If you’ve received such an email, exercise extreme caution. The claims are fabricated and designed to instill urgency, misleading you into paying money to the scammer.
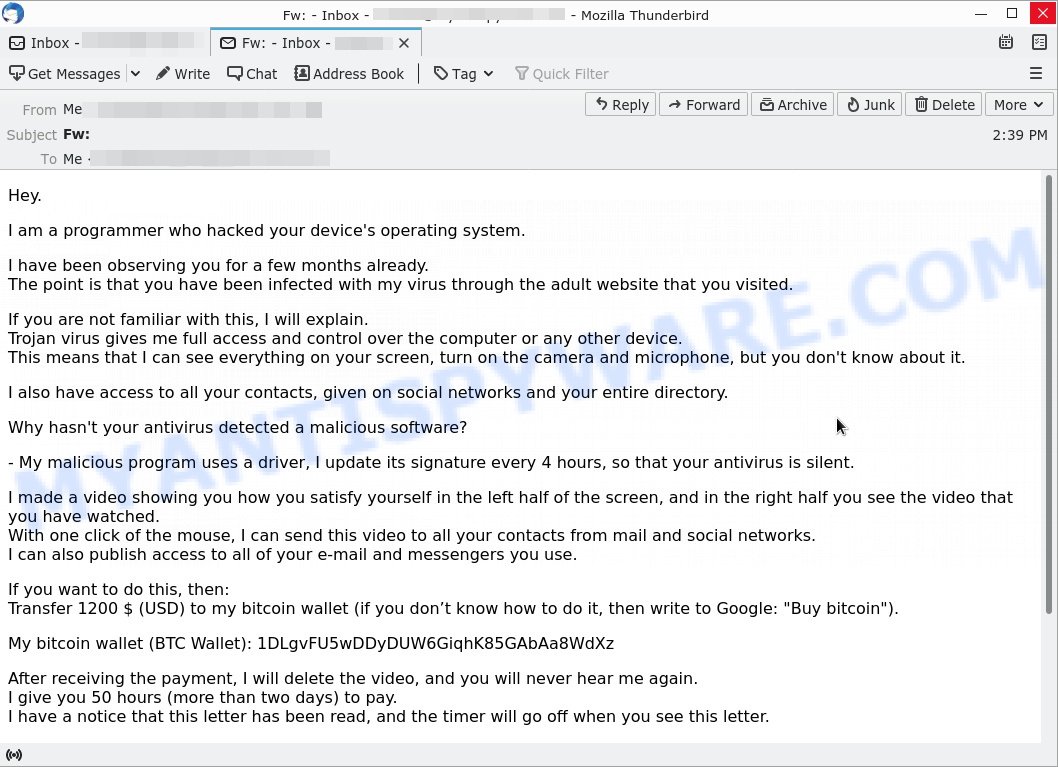
A typical “Programmer who hacked your device’s operating system” scam email reads as follows:
Hey.
I am a programmer who hacked your device’s operating system.
I have been observing you for a few months already.
The point is that you have been infected with my virus through the adult website that you visited.If you are not familiar with this, I will explain.
Trojan virus gives me full access and control over the computer or any other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you don’t know about it.I also have access to all your contacts, given on social networks and your entire directory.
Why hasn’t your antivirus detected a malicious software?
– My malicious program uses a driver, I update its signature every 4 hours, so that your antivirus is silent.
I made a video showing you how you satisfy yourself in the left half of the screen, and in the right half you see the video that you have watched.
With one click of the mouse, I can send this video to all your contacts from mail and social networks.
I can also publish access to all of your e-mail and messengers you use.If you want to do this, then:
Transfer 1200 $ (USD) to my bitcoin wallet (if you don’t know how to do it, then write to Google: “Buy bitcoin”).My bitcoin wallet (BTC Wallet): 1DLgvFU5wDDyDUW6GiqhK85GAbAa8WdXz
After receiving the payment, I will delete the video, and you will never hear me again.
I give you 50 hours (more than two days) to pay.
I have a notice that this letter has been read, and the timer will go off when you see this letter.Do not try to answer me. This is meaningless (the address of the sender is generated automatically).
There is no sense in filing a complaint anywhere, because this writing cannot be separated, like my bitcoin-address.
I don’t make mistakes.If I discover that you have shared this message with someone else, the video will be circulated immediately.
Best wishes!
Background on the ‘Programmer who hacked your device’s operating system’ Email Scam:
This scam involves fraudsters sending emails that claim they have hacked your computer and recorded compromising footage of you. The scammers demand a ransom in Bitcoin to prevent the release of this alleged footage.
However, legitimate cybersecurity experts and organizations confirm that these claims are baseless. No real hacking has occurred; the email is designed to scare you into paying the ransom. Scammers often send these emails in bulk, hoping to catch unsuspecting victims.
The alarming spread of these scams has prompted various government and consumer protection agencies, including the FBI and the Better Business Bureau, to issue warnings. These agencies have reported that these scams have been widespread, using similar tactics to exploit individuals’ fears of privacy invasion and public embarrassment.
The fraudulent emails often claim they have installed malware on your device and threaten to share embarrassing footage unless you pay. They provide a Bitcoin wallet address for the payment and set a deadline to increase the urgency and pressure.
🚩 Red Flags to Watch Out For:
To protect yourself, be aware of these warning signs of the scam: 🔍🛡️
- 📧 Threats: Unexpected emails that claim your device has been hacked and demand payment to prevent the release of compromising information.
- 💸 Ransom Demands: The scam includes demands for payment in Bitcoin, claiming it is the only way to prevent the release of the alleged footage.
- ⏳ Urgency and Imposed Deadlines: These emails impose a tight deadline to pressure you into acting hastily, using fear of embarrassment or reputational damage to coerce you into paying immediately.
- 🔄 No Evidence of Hacking: The email provides no real evidence that your device has been hacked or that any compromising footage exists.
- 👤 Anonymity of the Sender: Scammers use anonymous email addresses and provide untraceable Bitcoin wallet addresses, making it difficult to verify the source.
- 🔗 Suspicious Claims: Be skeptical of any email that makes extraordinary claims about hacking and demands for money.
💡 To protect yourself from scams like this, never respond to such emails or send money. Additionally, ensure your antivirus software is up to date. If you are concerned, run a virus scan on your device and change your email passwords for safety.
Understanding the ‘Programmer who hacked your device’s operating system’ Email Scam
If you receive an email that says “Programmer who hacked your device’s operating system“, it’s normal to be alarmed 🚨. These emails typically start with frightening statements to grab your attention immediately. You might think, How could they access my devices? In reality, the sender doesn’t have any access to your personal information; their goal is to intimidate you into acting hastily.
These emails include baseless threats, claiming they have videos or other compromising information that could humiliate you 🎥. The wording is intentionally vague and menacing, crafted to make you feel uneasy: Could any of this actually be true?
The scammer may claim they’ve installed sophisticated malware, like a Trojan Virus, on your device, purporting to have the ability to monitor all your online activities 💻. A clear sign this is a scam is the lack of any concrete evidence 🚩. They use the threat of high-tech surveillance to frighten you, not genuine hacking abilities.
The email typically concludes with a request for a payment 💰, with the scammer demanding a ransom in Bitcoin because it’s difficult to track. The scam is orchestrated to coerce you into paying swiftly. However, making a payment doesn’t guarantee your safety and may even mark you for further scams.
Upon reading the email, you might question, Am I truly in danger? or Can this individual actually do what they claim? Generally, these threats are fictitious; they are merely exploiting your fears.
What should you do? It’s advisable not to respond to the scammer or send any money. Concentrate on securing your online presence: update your passwords, ensure your devices are protected, and consider reporting to the police if the scam involves threats or extortion 🔐. Such incidents underscore the importance of vigilance and proactive online security measures.
Essentially, this scam relies on instilling fear and urgency to deceive you. If you receive an email like this, do not engage with the scammer or transfer any money. Simply delete the email. Also, keep your computer safeguarded with up-to-date anti-virus software, and use strong, unique passwords for all your accounts to help prevent falling victim to such scams.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
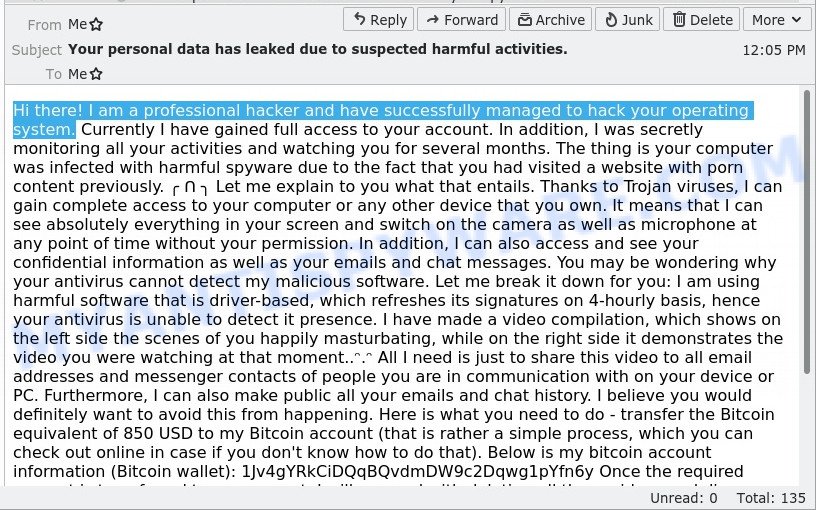
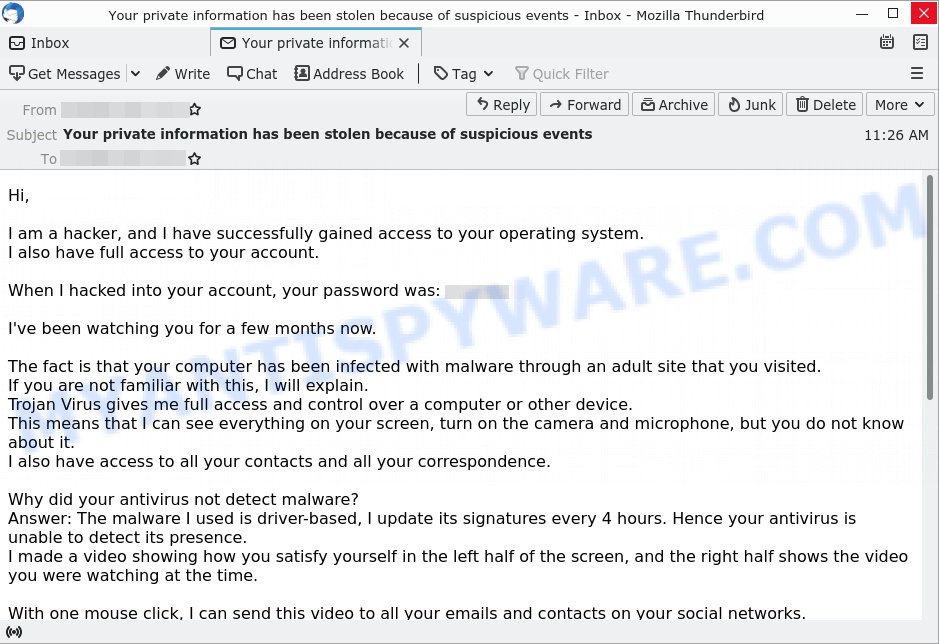
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
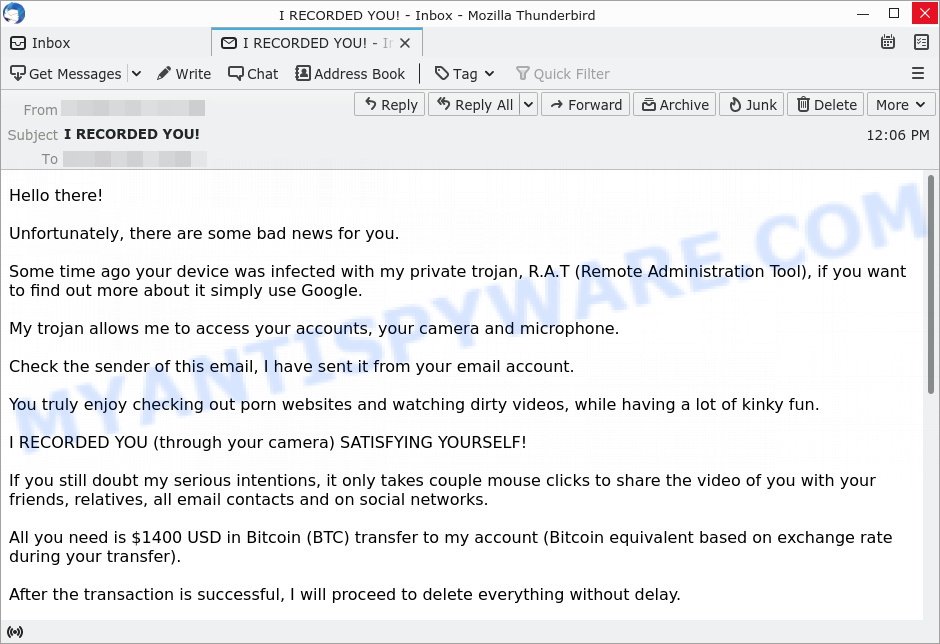
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you send the money?
No, don’t give the scammer any money. It’s a scam, and giving them money will only encourage them to continue their criminal activities. Plus, if you pay once, they might target you again. To keep your personal information safe, always use strong and unique passwords for each of your accounts, enable two-factor authentication for an extra layer of security, and keep your computer’s antivirus software up to date. If you receive an email like this, it’s important to report it to the authorities and your email provider.

What to Do if You Get This Scam Email
Getting an email that says someone hacked your devices and has compromising information can be scary, but there are easy and safe ways to handle it.

Here’s what to do:
First, stay calm. The email is meant to scare you and make you act without thinking. Remember, it’s just a scam to make you feel afraid.
Don’t pay them. Paying won’t make the problem go away. It only shows the scammer that you are an easy target for future scams.
Don’t reply to the scammer. Responding can give them more information about you and confirm that your email is active, which could lead to more scams.
If the email mentions a password you recognize, check where it came from. Use sites like haveibeenpwned.com to see if your email or passwords have been part of a data breach.
Then, change your passwords. Use strong, unique passwords and set up two-factor authentication where you can.
For safety, run a full security scan on your device. The email’s claims about malware are usually false, but it’s good to make sure your system is clean.
Report the email to the authorities (like the FTC). Reporting helps with investigations and can stop these scams from happening to others.
Finally, tell others. Let your friends, family, and coworkers know about this scam so they can avoid it too. Sharing this information makes everyone safer.
Threat Summary
| Name | ‘Programmer who hacked your device’s operating system’ Email Scam |
| Type | Phishing/Sextortion |
| Ransom amount | $1200 USD (in Bitcoin equivalent) |
| Bitcoin Address | 1DLgvFU5wDDyDUW6GiqhK85GAbAa8WdXz |
| Fake Claims | Access to personal data and browsing history, control over messengers and social networks, possession of embarrassing videos |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Inducing fear, creating urgency, deceptive claims |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The “Programmer who hacked your device’s operating system” email is a typical sextortion scam that uses threats to try to get money from you. The scammer says they’ve taken control of your devices, gotten your contacts, and even recorded you, and they threaten to share these made-up recordings unless you pay a ransom in Bitcoin. These threats are just scare tactics, made up to trick you into paying.
Bottom Line: Ignore these emails. It’s important to mark these messages as spam and delete them, which helps your email provider keep similar ones out of your inbox in the future. Also, make sure your device’s security is up to date. 🛡️💻
Stay alert and use common sense; an email that makes you feel scared or seems too pushy is probably a scam. 🤔