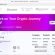
The Azurestaticapps.net POP-UP Scam is a problem that targets internet users. This scam uses pop-ups to redirect users to sites they didn’t plan to visit, all under the guise of the legitimate Azure Web Apps platform.
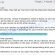
An Azurestaticapps phishing page (‘Tech Support Scam’ Scam):
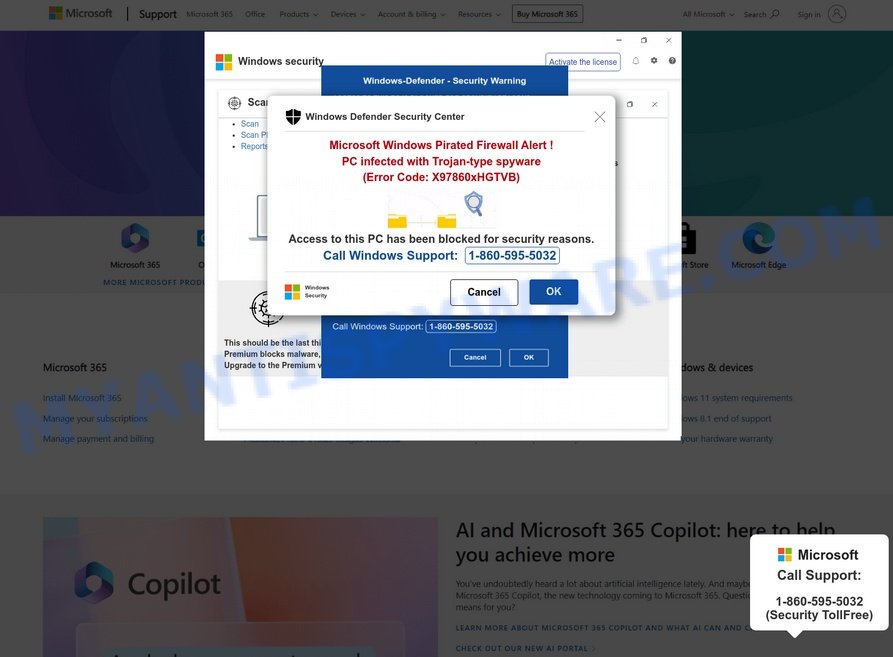
These unwanted pop-ups often appear out of nowhere and can be quite confusing and concerning. Many users have reported this issue on forums like the Microsoft Support Community and Reddit. These pop-ups aren’t just annoying; they can lead to more serious problems, like exposing your personal info or even installing unwanted software on your computer.

What is the Azurestaticapps Scam
The Azurestaticapps Scam is a deceptive technique where scammers misuse Microsoft Azure Web Apps service (Azure Static Web Apps) to lure users into interacting with harmful websites or content. This scam commonly surfaces through adware on devices, misleading push notifications, and fraudulent advertisements.
 Chains of Redirects
Chains of Redirects
This aspect of the scam involves using Azurestaticapps to create complex chains of redirects, leading unsuspecting users to harmful endpoints. The process is designed to evade security detections and make the scam’s source hard to trace, ultimately transferring users to sites that could host malware or phishing content.
 Tech Support Scams
Tech Support Scams
In these scams, perpetrators masquerade as well-known tech companies like Microsoft or Apple. They use Azurestaticapps and Azurestaticapps URLs to give an illusion of authenticity, issuing fake warnings about security breaches or system errors. The scam’s objective is to coerce users into buying unnecessary tech support services or to trick them into downloading software that compromises their device’s security.
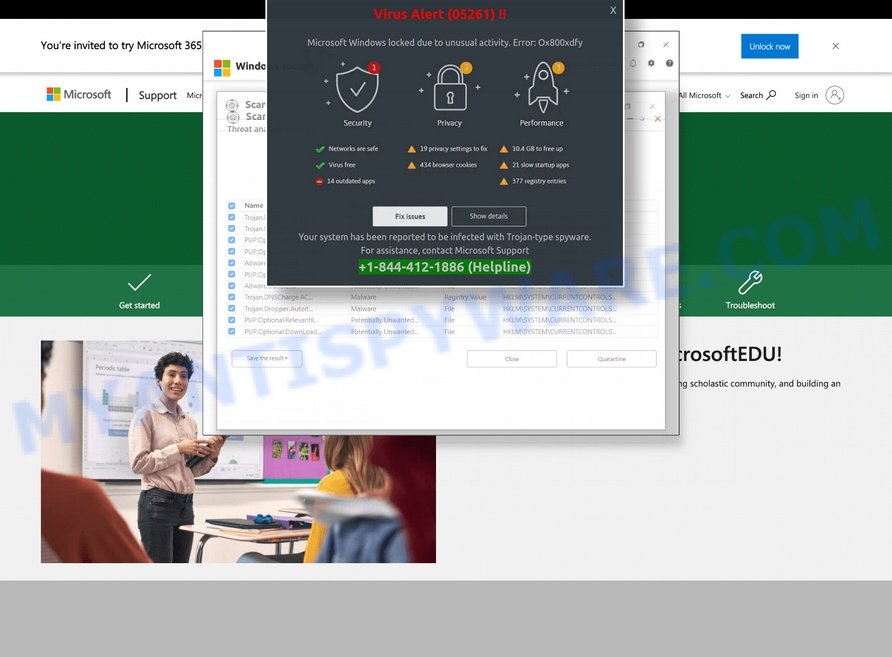
 ‘Click Allow’ Scams
‘Click Allow’ Scams
Here, users are deceived into permitting notifications from what appear to be benign Azurestaticapps URLs. These scams exploit notification permissions to send unwanted advertisements or malicious content directly to the user’s device. The scammers’ goals range from generating advertising revenue to distributing malware through these intrusive notifications.

 How to Identify Such Scams
How to Identify Such Scams
Understanding how to identify Azurestaticapps scams is crucial in safeguarding your online experience. Here are key signs to watch out for, helping you navigate and avoid these deceptive practices.

 Unexpected Pop-Ups and Redirects
Unexpected Pop-Ups and Redirects
Be cautious if sudden pop-ups appear or if you’re redirected to a website you didn’t intend to visit, particularly from a Azurestaticapps URL. These unexpected actions often signal the start of a redirect scam.
 Unfamiliar Domain Names
Unfamiliar Domain Names
Keep an eye on the address bar for URL changes. If the domain name shifts frequently or appears suspicious, it’s likely part of a redirect chain designed to lead you to a harmful site.
 Slow Website Performance
Slow Website Performance
A noticeable slowdown in your browser’s performance can indicate hidden processes running in the background, often associated with redirect chains or malware.
 Unsolicited Alerts
Unsolicited Alerts
Be wary of pop-up messages or emails that claim to be from major tech companies, especially if they prompt you for urgent action. These are common tactics in tech support scams.
 Requests for Personal Information or Payment
Requests for Personal Information or Payment
Genuine tech support entities do not typically ask for sensitive information or direct payments through pop-up alerts or unsolicited emails.
 Pressure Tactics
Pressure Tactics
High-pressure tactics, such as urging immediate action or instilling fear, are classic signs of a scam. Always take time to verify the authenticity of such alerts.
 Misleading ‘Allow’ Prompts
Misleading ‘Allow’ Prompts
Be skeptical of websites that prompt you to allow notifications, especially if the site’s content seems irrelevant or unclear. These can lead to an influx of unwanted and potentially harmful notifications.
 Increase in Unwanted Notifications
Increase in Unwanted Notifications
If you notice an increase in spammy or suspicious ads and alerts after visiting a website, it might be due to a ‘Click Allow’ scam that you unwittingly agreed to.
 Suspicious Content in Notifications
Suspicious Content in Notifications
Be alert to the content of notifications; scams often include unrealistic offers or alarming messages designed to provoke a reaction or engagement.
 Keep Software Updated
Keep Software Updated
Regularly updating your browser and operating system helps close security loopholes that scammers exploit. Always ensure your software is up-to-date.
 Use Security Software
Use Security Software
Employing reputable antivirus and anti-malware software can provide an additional layer of protection against various online threats, including Azurestaticapps scams.
 Be Skeptical
Be Skeptical
Maintain a healthy level of skepticism towards offers or alerts that seem too good to be true or excessively alarming. Taking a moment to assess their legitimacy can save you from falling for a scam.
Threat Summary
| Name | “Azurestaticapps” Scam |
| Type | Various, including Pop-Up Scams, Malware Distribution, Deceptive Practices |
| Damage | Financial Loss, Malware Infection, Privacy Breach |
| Distribution | Through Malicious Websites, Pop-Up Ads, and Deceptive Calendar Events |
| Scammers websites | gray-coast-0a8a87b10.1.azurestaticapps.net, zealous-grass-011487f1e.5.azurestaticapps.net, ashy-hill-037dfd210.5.azurestaticapps.net, etc |
| Tactics | Exploiting Azurestaticapps for Distribution, Misleading Pop-Ups, Deceptive Notifications |
| Prevention Tips | Close suspicious pop-ups, Avoid clicking links, Use security software, Stay informed, Report scams |
| Reporting Info | Report to your antivirus provider and appropriate authorities |
How to remove Azurestaticapps pop-ups
If you have encountered Azurestaticapps pop-ups, you should not trust the message and refrain from clicking any buttons or links that appear on the page. Instead, follow the steps below to remove the pop-up and any potential malware from your computer:
To remove Azurestaticapps pop ups, complete the steps below:
- Close the pop-up
- Clear your browsing history
- Disable push notifications
- Scan your computer for malware
- Reset your browser settings
Close the pop-up
Closing the pop-up is the first step you should take when dealing with the Azurestaticapps scam. Although it may seem like a simple task, some users may find it challenging, especially if the pop-up is designed to be persistent and difficult to close. This step is crucial because it prevents the user from falling into the trap set by the scammers and clicking on any of the buttons or links that can lead to further harm. In this section, we will provide a detailed guide on how to close the Azurestaticapps pop-up safely and effectively.
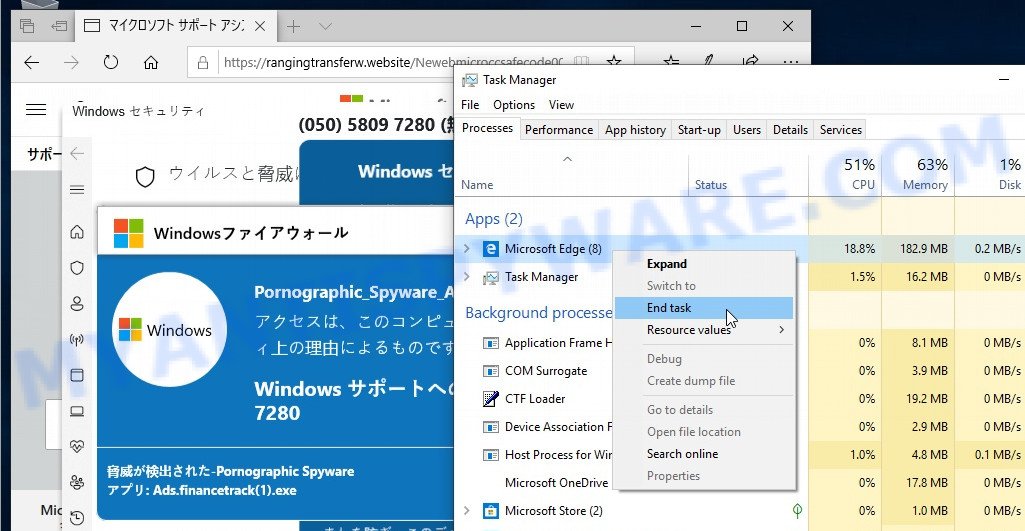
- Don’t click on anything within the pop-up as it could lead to further harm.
- Look for a small “X” or “Close” button within the pop-up window. Click on it to close the window.
- If there is no “X” or “Close” button, try pressing the “Esc” key on your keyboard to close the pop-up.
- If the pop-up still won’t close, try opening your computer’s Task Manager by pressing “Ctrl + Shift + Esc” on your keyboard (or “Ctrl + Alt + Delete” and then select “Task Manager”). Find the browser window that the pop-up is in, right-click on it, and select “End Task” to force close the window.
Clear your browsing history
Clearing your browsing history is an important step in removing Azurestaticapps pop-ups. These pop-ups often come from malicious websites that can be stored in your browsing history.
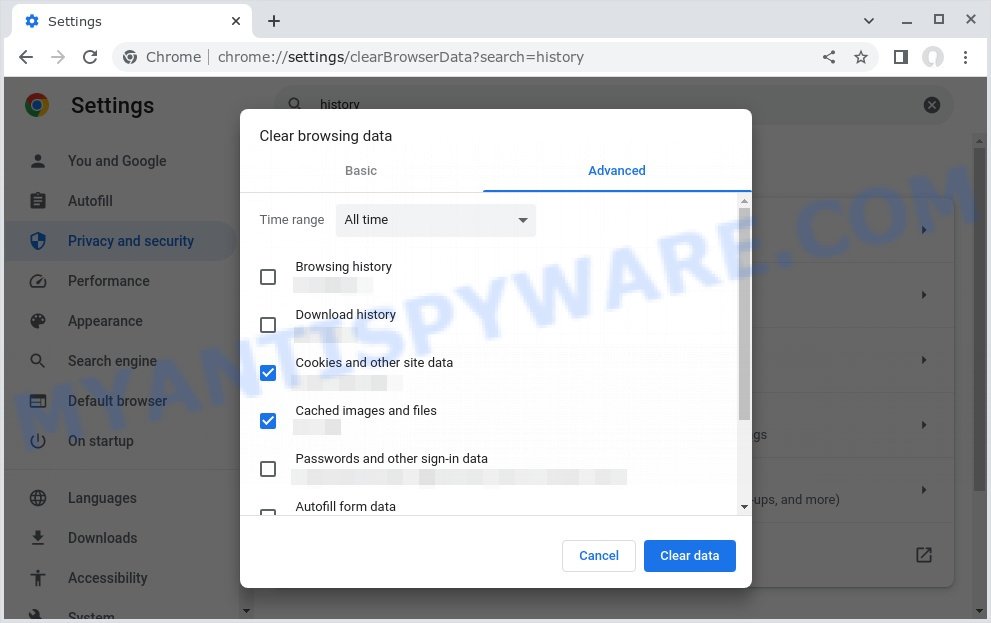
By clearing your browsing history, you can get rid of any traces of these websites and prevent the pop-ups from reappearing. In this step, we will walk you through how to clear your browsing history on different browsers.
- Open your browser’s settings or options menu. This can usually be accessed by clicking on the three dots or lines in the top right or left corner of the browser window.
- Scroll down to the “Privacy & Security” or “History” section of the settings menu.
- Click on “Clear Browsing Data” or “Clear History” (the wording may vary depending on the browser you are using).
- In the pop-up window that appears, choose the time range for which you want to clear your browsing history (e.g. “Last hour”, “Last 24 hours”, “All time”, etc.).
- Make sure that “Browsing history” or “History” is selected as one of the types of data to be cleared.
- Click on the “Clear Data” or “Clear History” button (the wording may vary depending on the browser you are using).
- Wait for the browser to finish clearing your browsing history. This may take a few moments, especially if you have a lot of browsing data stored on your computer.
- Close and restart your browser to ensure that the changes take effect.
Disable push notifications
If you’re experiencing persistent push notifications from websites that are showing Azurestaticapps scams, the best course of action is to disable push notifications altogether. Disabling push notifications prevents malicious websites from showing you unwanted pop-ups and alerts, which can help protect your computer from further harm. In this step, we’ll walk you through the process of disabling push notifications in your web browser.
Google Chrome:
- Click on ‘three dots menu’ button at the top-right corner of the Google Chrome window.
- Select ‘Settings’, scroll down to the bottom and click ‘Advanced’.
- At the ‘Privacy and Security’ section click ‘Site settings’.
- Click on ‘Notifications’.
- Locate the “Azurestaticapps” site and click the three vertical dots button next to it, then click on ‘Remove’.
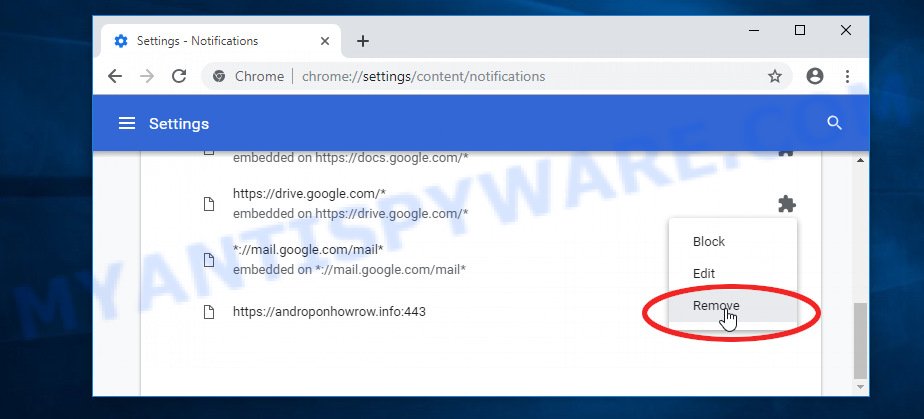
Android:
- Open Chrome.
- Tap on the Menu button (three dots) on the top right corner of the screen.
- In the menu tap ‘Settings’, scroll down to ‘Advanced’.
- In the ‘Site Settings’, tap on ‘Notifications’, locate the “Azurestaticapps” URL and tap on it.
- Tap the ‘Clean & Reset’ button and confirm.
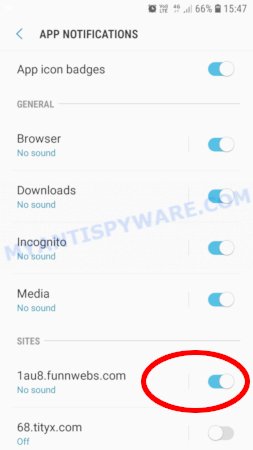
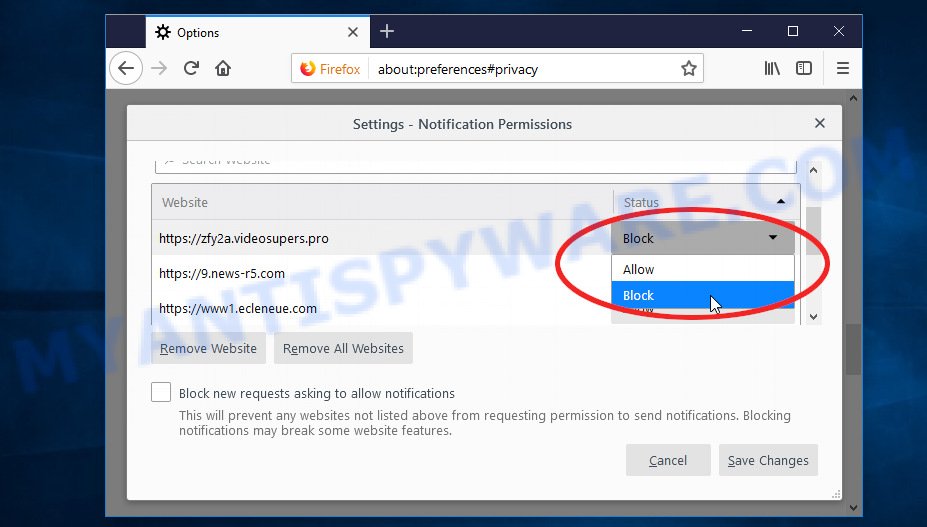
Mozilla Firefox:
- In the top right corner, click the Firefox menu (three bars).
- In the drop-down menu select ‘Options’. In the left side select ‘Privacy & Security’.
- Scroll down to ‘Permissions’ section and click ‘Settings…’ button next to ‘Notifications’.
- Find “Azurestaticapps”, other suspicious URLs, click the drop-down menu and select ‘Block’.
- Click ‘Save Changes’ button.
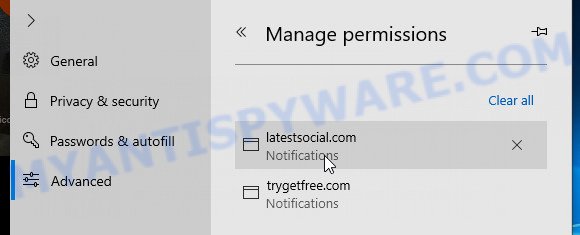
Edge:
- Click the More button (three dots) in the top-right corner of the window.
- Scroll down, locate and click ‘Settings’. In the left side select ‘Advanced’.
- In the ‘Website permissions’ section click ‘Manage permissions’.
- Disable the on switch for the “Azurestaticapps” domain.
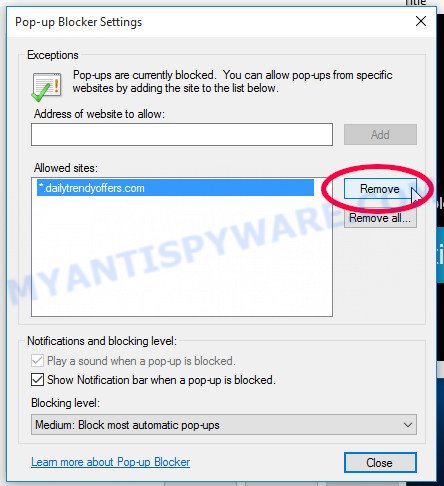
Internet Explorer:
- Click the Gear button on the top-right corner of the browser.
- Select ‘Internet options’.
- Click on the ‘Privacy’ tab and select ‘Settings’ in the pop-up blockers section.
- Locate the “Azurestaticapps” site and click the ‘Remove’ button to delete the site.
Safari:
- Go to ‘Preferences’ in the Safari menu.
- Select the ‘Websites’ tab and then select ‘Notifications’ section on the left panel.
- Find the “Azurestaticapps” site and select it, click the ‘Deny’ button.
Scan computer for malware
If you have encountered the Azurestaticapps scam, it is possible that your computer has been infected with malware. In order to ensure that your system is completely clean, it is important to perform a thorough scan for malware. This will help to identify any malicious files or programs that may be hiding on your computer and remove them to prevent further damage. In this step, we will guide you through the process of scanning your computer for malware using trusted antivirus software.
Malwarebytes is a reputable anti-malware program that can effectively detect and remove adware, potentially unwanted programs and malware. It has a user-friendly interface and offers both free and paid versions, with the paid version offering real-time protection and other advanced features. To use Malwarebytes to remove malicious software, you can download and install the program, perform a scan of your system, and follow the prompts to remove any detected threats.
Visit the following link and download the latest version of Malwarebytes. Once the download is complete, run the installer and follow the instructions to install the program on your computer.
327040 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
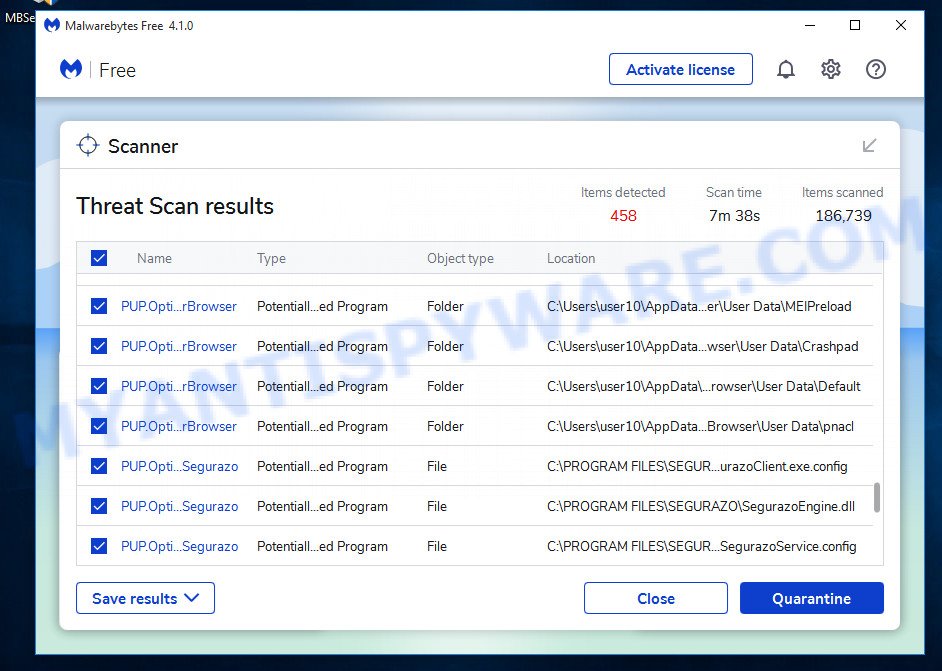
Open Malwarebytes and click on the “Scan” button. The program will start scanning your computer for any malware or potentially unwanted programs. Depending on the size of your hard drive, this may take a few minutes to complete.
Once the scan is complete, Malwarebytes will display a list of any threats it has found. Review the list carefully and make sure that all the items are checked for removal. Then, click on the “Quarantine” button to remove the threats from your computer. After the removal process is complete, you may be prompted to restart your computer to complete the process.
Please follow this step-by-step video tutorial to learn how to use Malwarebytes to scan and remove any potential threats from your computer. The video will guide you through the entire process, from downloading and installing Malwarebytes to running a scan and removing any identified threats.
Reset your browser settings
If the Azurestaticapps pop-ups persist even after clearing your browsing history, disabling push notifications, and scanning your computer for malware, resetting your browser settings might be the next step to take. Resetting your browser settings can remove any unwanted extensions or changes made to your browser that may be causing the pop-ups to appear. In this step, we will guide you through the process of resetting your browser settings in different popular browsers.
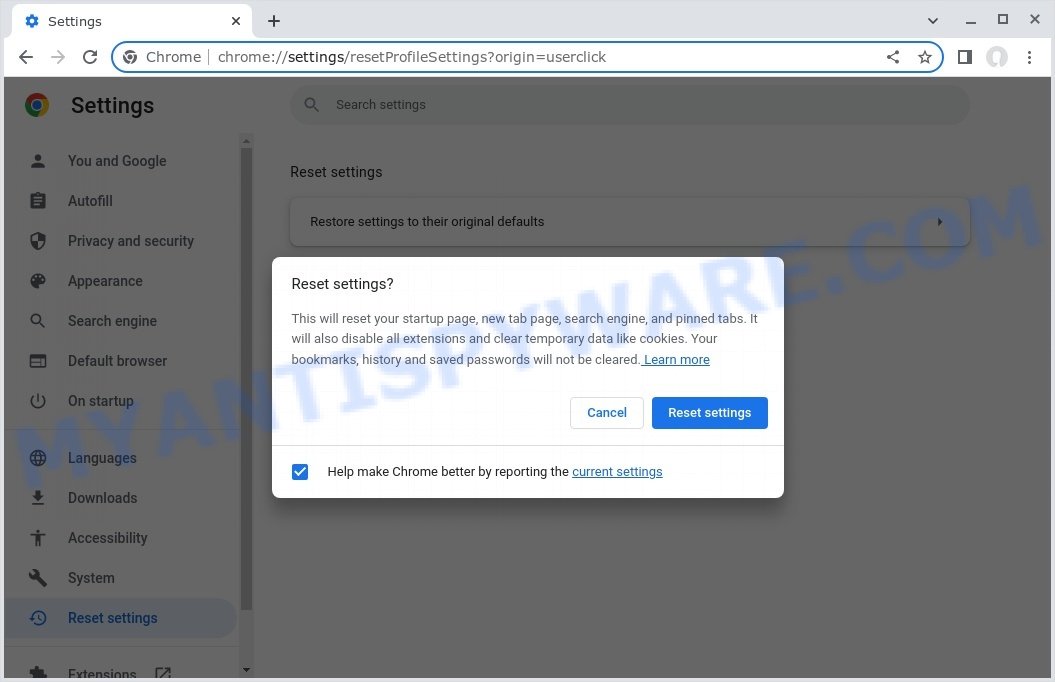
To reset your browser settings in Google Chrome:
- Open Chrome and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down to the bottom of the page and click on “Advanced”.
- Scroll down to the “Reset and cleanup” section and click on “Restore settings to their original defaults”.
- Click “Reset settings” to confirm.
To reset your browser settings in Mozilla Firefox:
- Open Firefox and click on the three-line icon in the top-right corner.
- Select “Help” from the drop-down menu and then click on “Troubleshooting Information”.
- Click on the “Refresh Firefox” button in the top-right corner.
- Click “Refresh Firefox” again to confirm.
To reset your browser settings in Microsoft Edge:
- Open Edge and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down and click on “Reset settings”.
- Click “Restore settings to their default values”.
- Click “Reset” to confirm.
After resetting your browser settings, be sure to check for any remaining suspicious extensions and remove them if necessary.
Conclusion
While Microsoft Azure Web Apps is a legitimate service, scammers have found ways to abuse it for malicious purposes. Staying cautious, informed, and following best practices for online security can help you avoid falling victim to the Azurestaticapps scam and other similar online threats.
Always exercise vigilance when encountering unexpected pop-ups, suspicious links, or misleading notifications while browsing the web. Legitimate companies will not display alarming messages or demand immediate action through aggressive pop-ups. Stay informed about common scams, rely on official support channels, and use reputable security software to safeguard your devices.