What is Targetchain-flow.com?
Targetchain-flow.com domain is part of a redirect chain. Redirect chain is a sequence of URLs starting from the first – initial URL, ending with the last – final destination URL.
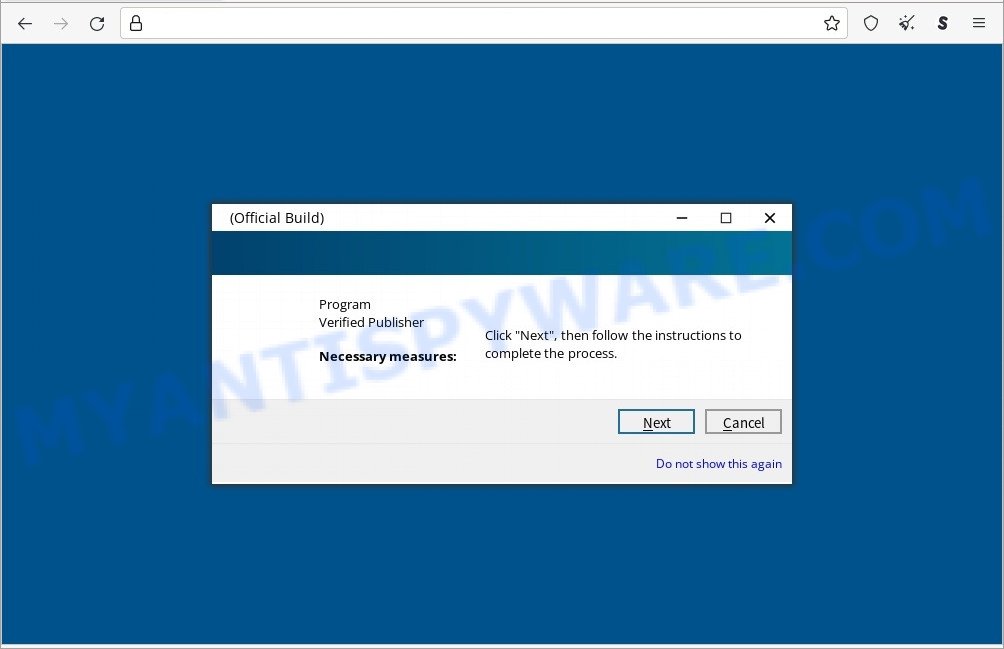
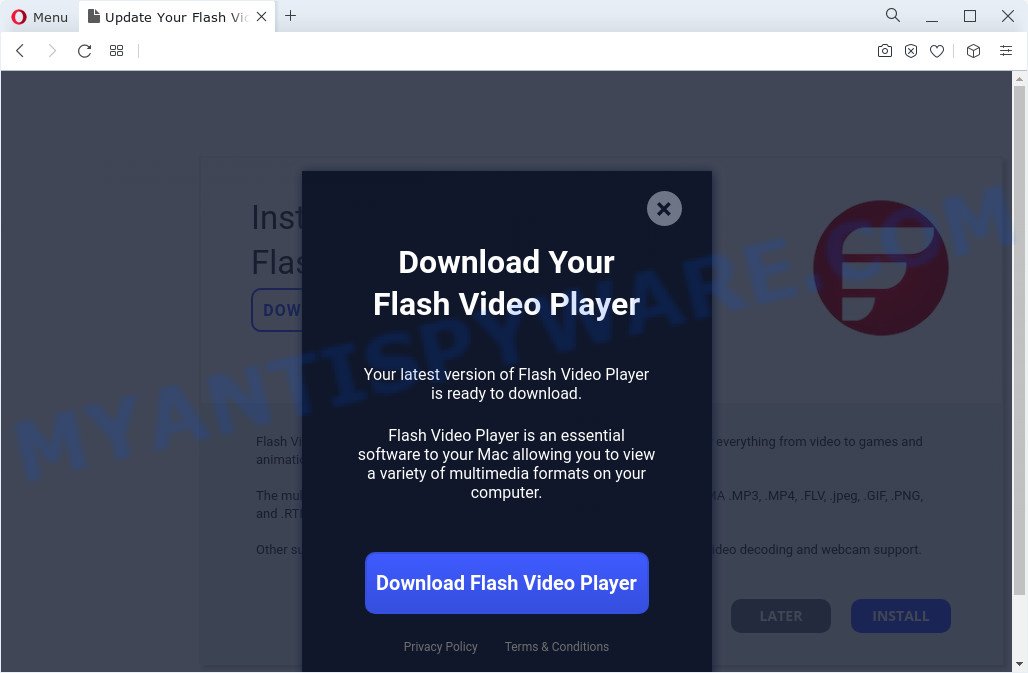
Attackers may use long redirect chains to hide malicious content. Most malicious redirects are conditional. It means that redirection only occurs when a certain condition is met. For example, search traffic redirects only occur when someone clicks from Google’s search results.
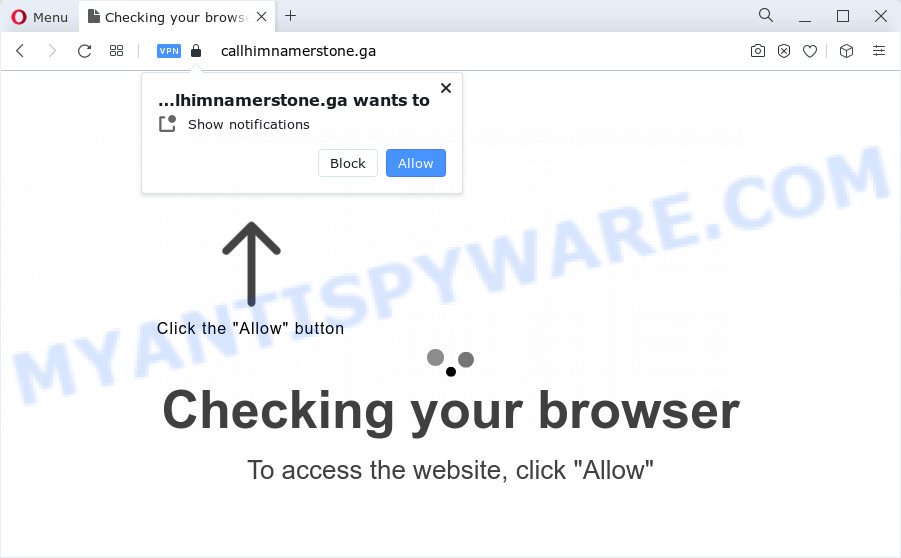
In some cases, unsuspecting users are taken to a rogue web page containing a pretend CAPTCHA examine, clicking which serves unwanted ads which are disguised to look as if they come from the working system and never from a web browser. In other cases, users are redirected to pages containing malware.
VirusTotal flagged Targetchain-flow.com as malicious:
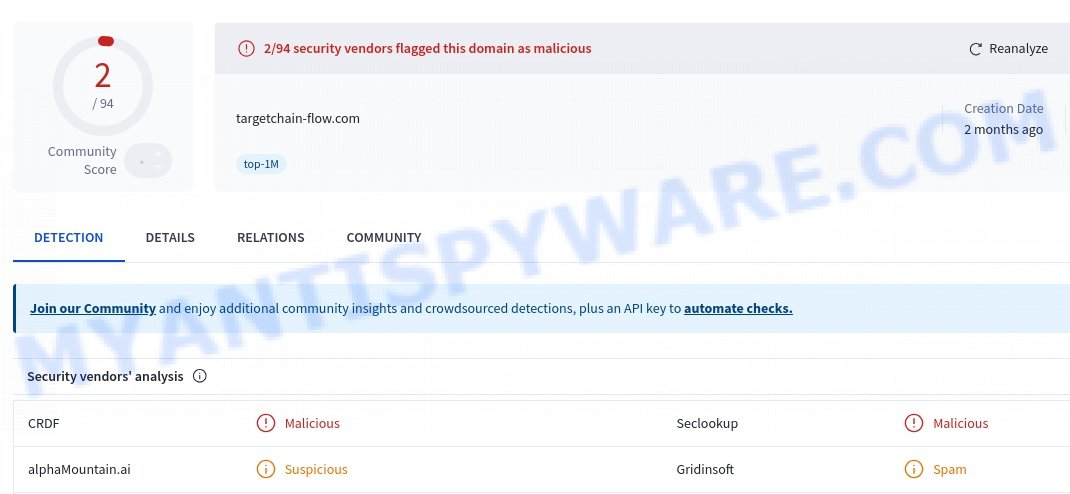
Table of Contents
Targetchain-flow.com redirect in detail
In most cases, malicious redirects occur when users browse high-risk websites, when users click on a malicious link from push notifications and spam emails. In addition, they can be redirected to the first – initial URL by malicious advertisements (malvertising) and Adware. Adware is a type of software that displays advertisements on a user’s device. While many forms of adware are benign and simply show unwanted ads, some forms of adware can also be spyware. Spyware is a type of software that is designed to collect personal information from a user’s device without their knowledge or consent.

Adware can gather data such as user browsing habits, search terms, and sensitive information such as login credentials and financial information. The gathered information is then sent to a third party, who may use it for malicious purposes, such as identity theft or targeted advertising.
Adware can be used by attackers as a means of redirecting users to other websites without their knowledge or consent. This is known as “malicious redirects”. Attackers can use these redirects to carry out various malicious activities, such as phishing, malware delivery, and ad fraud, among others.
In a phishing attack, a user may be redirected to a fake website that appears to be a legitimate site, in order to steal sensitive information such as login credentials or financial information. In a malware delivery attack, the user may be redirected to a website that downloads malware onto their device, compromising their security and privacy. Ad fraud involves redirecting users to websites that artificially inflate ad impressions and generate revenue from advertising.
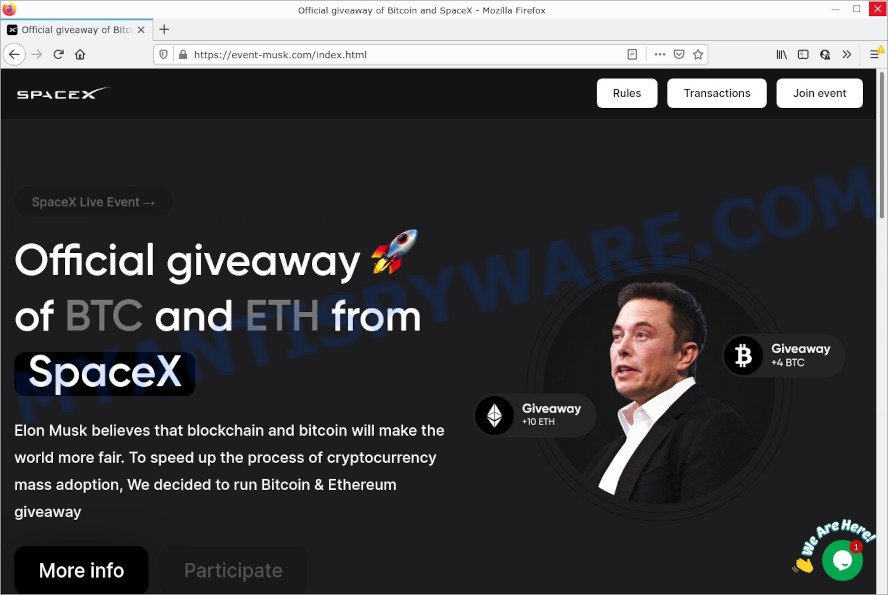
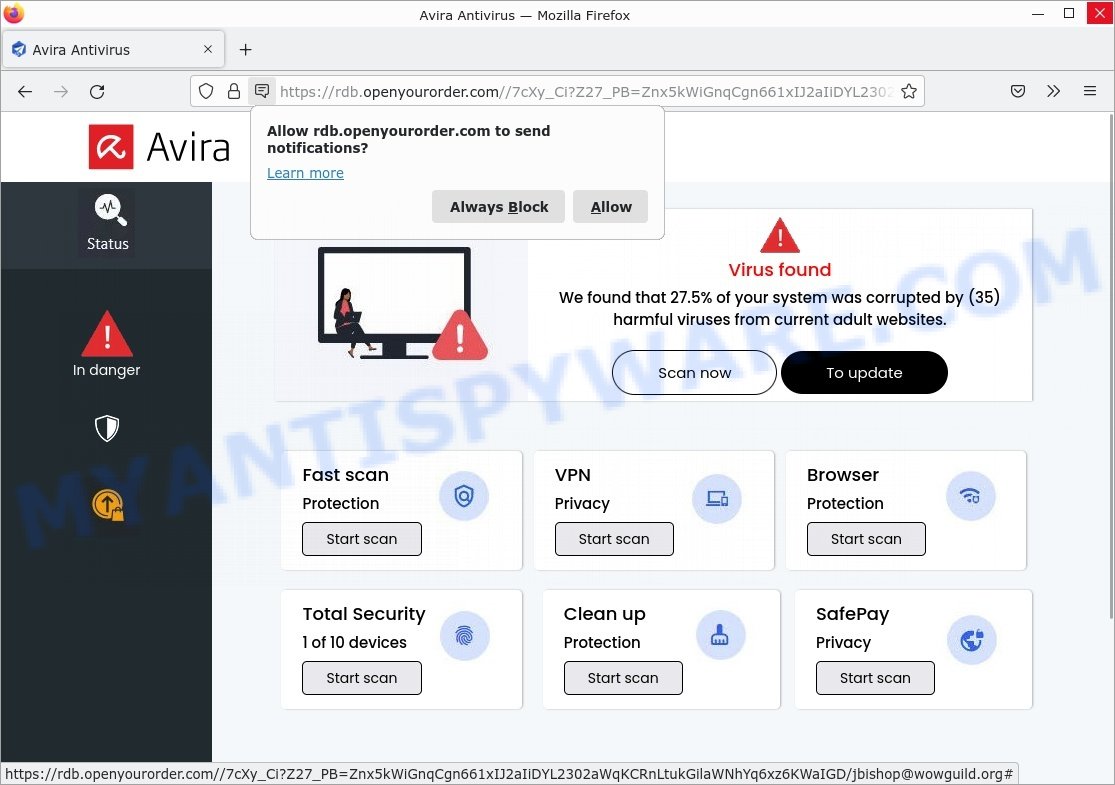
Below are some examples of malicious sites (phishing, malware delivery, ad fraud, etc):
In summary, malicious redirects can trick users into making security mistakes or giving away sensitive information, exploit vulnerabilities on their computer and install malicious software.
Threat Summary
| Name | Targetchain-flow.com, ‘Targetchain-flow.com redirect’, ‘Targetchain-flow.com pop-up’ |
| Type | redirect chain, redirects |
| Example URLs | targetchain-flow.com/video-player-2/?domain=baseclickflow.com… |
| Whois Details | Domain Details: Domain Name: TARGETCHAIN-FLOW.COM Registrar: NameCheap, Inc. Creation Date: 2024-07-12 Registry Expiry Date: 2025-07-12 Name Server: ALARIC.NS.CLOUDFLARE.COM Registrant Information: |
| Distribution method | compromised websites, spam email campaigns, social networks, deceptive ads, adware and potentially unwanted applications |
| Symptoms | unwanted ads, fake security warnings, fake system messages, pop-up errors, spam notifications |
| Damage | malware infection, loss of personal data, disclosure of confidential information, financial losses |
| Removal | Targetchain-flow.com removal guide |
Examples of malicious redirects
We have reported several other scam and malicious sites in the past. Examples: Windows Defender Security Center, Your File Is Ready To Download, McAfee TROJAN Virus Detected, You’ve made the 5-billionth search, and VPN Update Scam.
Users never visit sites like Targetchain-flow.com themselves. Typically, users are redirected to them after they click on misleading ads, visit torrent, illegal movie streaming and similar websites. Sometimes, users are redirected to the sites due to installed browser hijackers, adware or other unwanted software.
How can you protect against malicious redirects?
To protect against malicious redirects, you can take the following steps:
- Install and use reliable antivirus software to protect your computer from malware and other threats. Regularly update your antivirus software to ensure that it can detect and remove the latest threats.
- Malicious redirects can take advantage of security vulnerabilities in outdated software. Make sure to regularly update your browser, plugins, and other software to the latest version to reduce the risk of being redirected to harmful websites.
- Be cautious when clicking on links or visiting unfamiliar websites. If a website looks suspicious or offers free downloads or other too-good-to-be-true deals, it’s best to avoid it. Try to use paid (premium) versions of popular services and avoid free online converters, free online cinemas, and other similar websites.
- Use an ad blocker. Ad-blockers can help prevent unwanted pop-ups and advertisements that may redirect you to harmful websites.
- Most modern browsers offer features like pop-up blockers, phishing and malware protection, and notifications when attempting to redirect you to a different website. Enable these features to add an extra layer of protection against malicious redirects.
By following these best practices and taking the necessary precautions, you can significantly reduce the risk of being redirected to harmful websites and protect your computer from malware.
How to remove Targetchain-flow.com pop-up redirect
We can assist you in eliminating Targetchain-flow.com redirects from your browser without the need to contact an IT technician. Simply follow the removal instructions provided below. If you find it challenging to get rid of scam pop-ups on your browser, do not hesitate to ask for help in the comments section below. Certain steps may require you to restart your computer or exit this webpage. Therefore, please read this guide carefully, and then bookmark this page or open it on your smartphone for future reference.
To remove Targetchain-flow.com, follow the steps below:
- Remove spam notifications
- Check the list of installed software
- Scan computer for malware
- Reset your browser settings
- Stop Targetchain-flow.com pop-ups
Remove spam notifications
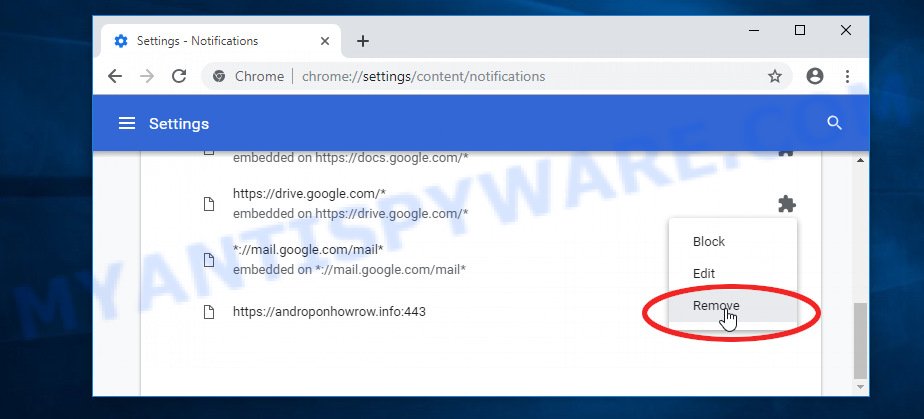
In certain instances, the reason behind the appearance of Targetchain-flow.com pop-ups and redirects could be push notifications. These push notifications can come from fraudulent sites that use fake captcha to subscribe the user to them without their consent. To disable these push notifications, you will need to access the settings of your browser and locate the section where push notifications are managed. From there, you can disable any unwanted notifications. If you are unsure how to do this, we can provide you with step-by-step instructions to help you navigate your browser settings and disable these notifications
Google Chrome:
- Click on ‘three dots menu’ button at the top-right corner of the Google Chrome window.
- Select ‘Settings’, scroll down to the bottom and click ‘Advanced’.
- At the ‘Privacy and Security’ section click ‘Site settings’.
- Click on ‘Notifications’.
- Locate a malicious site and click the three vertical dots button next to it, then click on ‘Remove’.
Android:
- Open Chrome.
- Tap on the Menu button (three dots) on the top right corner of the screen.
- In the menu tap ‘Settings’, scroll down to ‘Advanced’.
- In the ‘Site Settings’, tap on ‘Notifications’, locate a scam URL and tap on it.
- Tap the ‘Clean & Reset’ button and confirm.
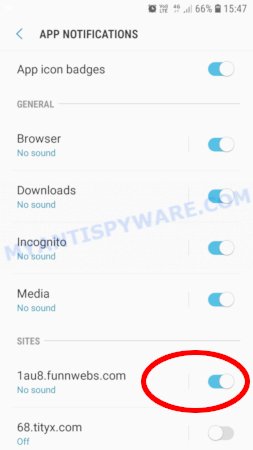
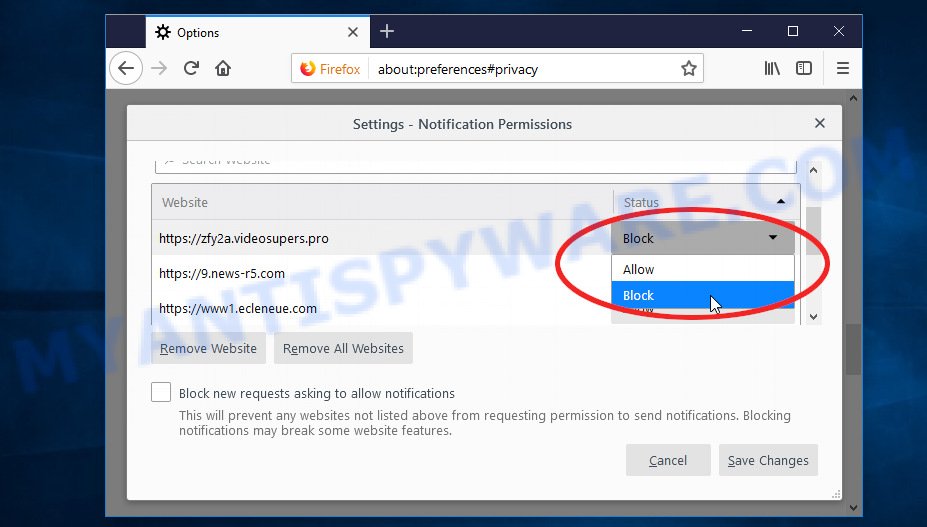
Mozilla Firefox:
- In the top right corner, click the Firefox menu (three bars).
- In the drop-down menu select ‘Options’. In the left side select ‘Privacy & Security’.
- Scroll down to ‘Permissions’ section and click ‘Settings…’ button next to ‘Notifications’.
- Find suspicious URLs, click the drop-down menu and select ‘Block’.
- Click ‘Save Changes’ button.
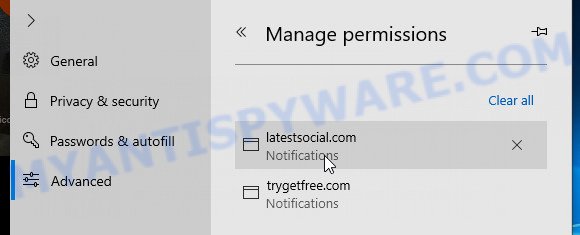
Edge:
- Click the More button (three dots) in the top-right corner of the window.
- Scroll down, locate and click ‘Settings’. In the left side select ‘Advanced’.
- In the ‘Website permissions’ section click ‘Manage permissions’.
- Disable the on switch for scam domains.
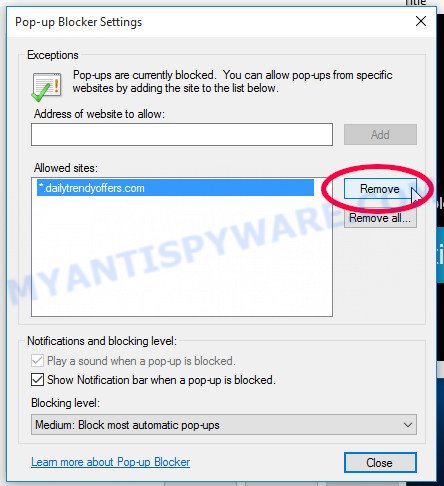
Internet Explorer:
- Click the Gear button on the top-right corner of the browser.
- Select ‘Internet options’.
- Click on the ‘Privacy’ tab and select ‘Settings’ in the pop-up blockers section.
- Locate a scam site and click the ‘Remove’ button to delete the site.
Safari:
- Go to ‘Preferences’ in the Safari menu.
- Select the ‘Websites’ tab and then select ‘Notifications’ section on the left panel.
- Find a scam site and select it, click the ‘Deny’ button.
Check the list of installed software
Take a look at the list of apps installed on your computer and uninstall any that you don’t recognize or that were recently installed. If you come across a program with a suspicious name, misspellings, or inconsistent capitalization, it may have been installed by malware. In this case, use a reputable malware removal tool like Malwarebytes to remove it from your system.
|
|
|
|
Scan computer for malware
Malicious redirects, such as those caused by Targetchain-flow.com, can be a sign of malware or viruses on your computer. To ensure that your computer is not infected with any malicious software, there are several methods you can use to check for and remove potential threats. One option is to perform a thorough scan of your system using reputable antivirus software. This will help you identify any known threats and take the necessary steps to remove them.
Additionally, you can use anti-malware software that can detect and remove more sophisticated threats that may not be caught by traditional antivirus programs. Finally, you can also check for malware manually by reviewing your system logs and removing any suspicious files or processes. By taking these proactive steps, you can help protect your computer from malicious redirects and other harmful software.
An excellent option for scanning your computer for malware is Malwarebytes. This software is a powerful anti-malware tool that can detect and remove a wide range of malicious software, including viruses, spyware, Trojans, and other threats. With its advanced scanning technology, Malwarebytes can quickly identify and remove any malicious software that may be causing redirects, such as Targetchain-flow.com. Additionally, Malwarebytes is regularly updated to stay ahead of new threats, so you can be confident that your computer is protected against the latest malware. If you suspect that your computer may be infected with malware, using Malwarebytes is an effective way to identify and remove any potential threats.
Visit the following link and download the latest version of Malwarebytes. Once the download is complete, run the installer and follow the instructions to install the program on your computer.
327035 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
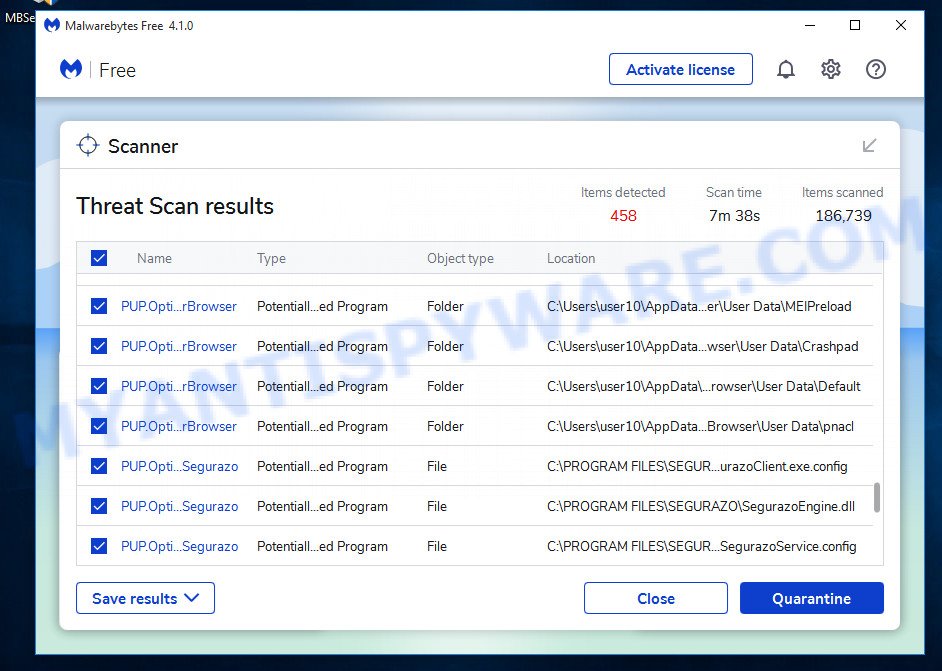
Open Malwarebytes and click on the “Scan” button. The program will start scanning your computer for any malware or potentially unwanted programs. Depending on the size of your hard drive, this may take a few minutes to complete.
Once the scan is complete, Malwarebytes will display a list of any threats it has found. Review the list carefully and make sure that all the items are checked for removal. Then, click on the “Quarantine” button to remove the threats from your computer. After the removal process is complete, you may be prompted to restart your computer to complete the process.
Please follow this step-by-step video tutorial to learn how to use Malwarebytes to scan and remove any potential threats from your computer. The video will guide you through the entire process, from downloading and installing Malwarebytes to running a scan and removing any identified threats.
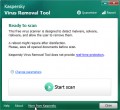
While Malwarebytes is an excellent tool for detecting and removing malware, sometimes a more thorough scan is necessary to ensure that all traces of the malware are removed. In these cases, using Kaspersky Virus Removal Tool (KVRT) can be a helpful option. This software is a free, powerful anti-virus tool that can help you identify and remove even the most complex and persistent malware.
KVRT is designed to run alongside your existing antivirus software, making it an effective additional layer of protection. By using Kaspersky Virus Removal Tool in conjunction with Malwarebytes or another antivirus program, you can be confident that your computer is thoroughly protected against malware and other threats, including those that may be causing redirects such as Targetchain-flow.com.
Download Kaspersky virus removal tool by clicking on the following link. Save it directly to your Windows Desktop.
129227 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
After the downloading process is complete, double-click on the KVRT icon. Once initialization procedure is complete, you’ll see the KVRT screen as displayed below.
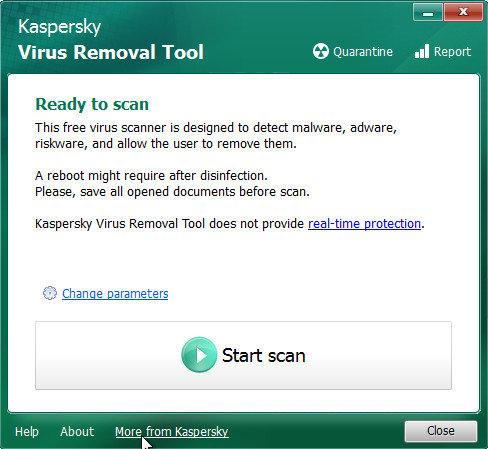
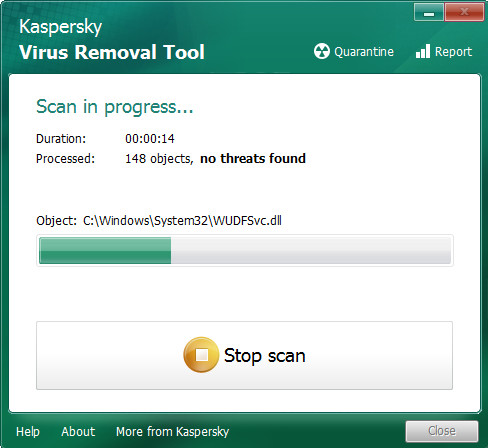
Click “Change Parameters” and set a check near all your drives. Click OK to close the Parameters window. Next click “Start scan” button to scan your computer for the Communique adware and other known infections. This task can take quite a while, so please be patient. While the tool is scanning, you can see how many objects and files has already scanned.
As the scanning ends, Kaspersky virus removal tool will create a list of malware found, as displayed in the figure below.
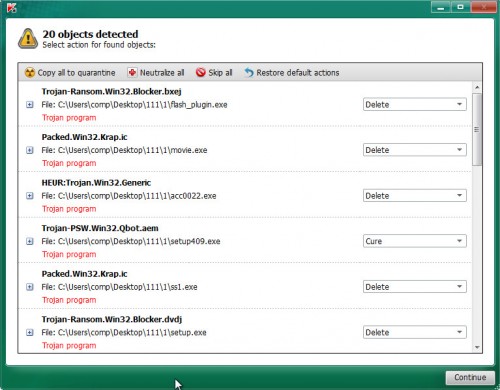
All detected threats will be marked. You can delete them all by simply clicking Continue.
Reset your browser settings
If you have performed a thorough scan of your computer and removed any detected malware, but the redirects caused by Targetchain-flow.com still persist, resetting your browser settings may be necessary. This will help remove any unwanted extensions, add-ons, or settings that may be causing the redirects. Once you have reset your browser settings, restart your browser and test to see if the redirects have been eliminated. If the problem persists, further troubleshooting may be necessary.
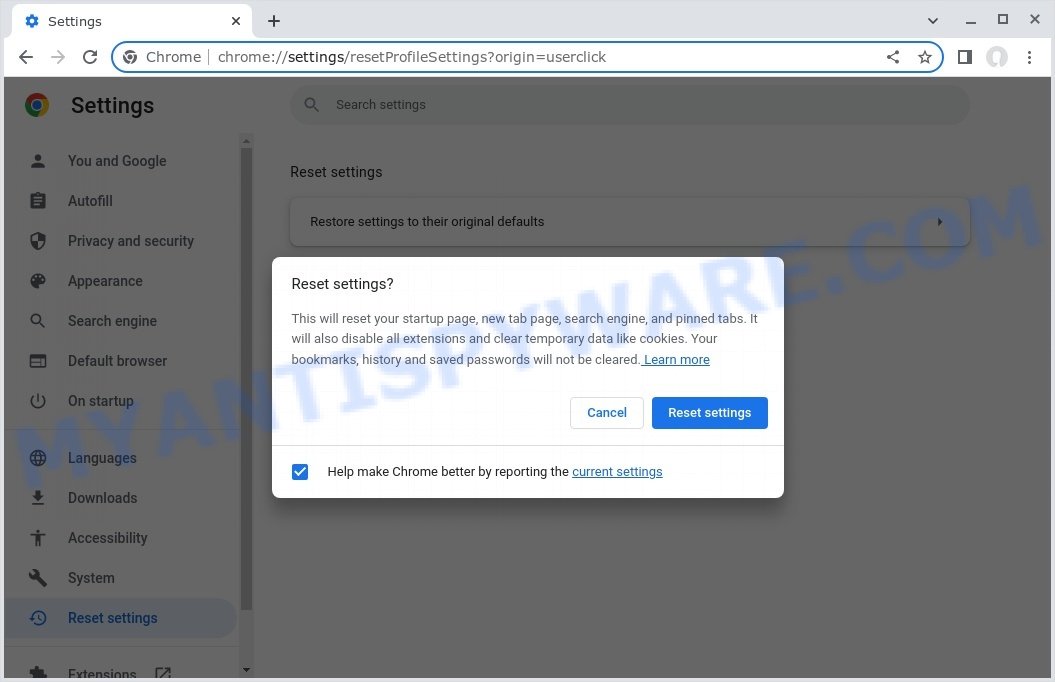
To reset your browser settings in Google Chrome:
- Open Chrome and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down to the bottom of the page and click on “Advanced.”
- Scroll down to the “Reset and cleanup” section and click on “Restore settings to their original defaults.”
- Click “Reset settings” to confirm.
To reset your browser settings in Mozilla Firefox:
- Open Firefox and click on the three-line icon in the top-right corner.
- Select “Help” from the drop-down menu and then click on “Troubleshooting Information.”
- Click on the “Refresh Firefox” button in the top-right corner.
- Click “Refresh Firefox” again to confirm.
To reset your browser settings in Microsoft Edge:
- Open Edge and click on the three-dot icon in the top-right corner.
- Select “Settings” from the drop-down menu.
- Scroll down and click on “Reset settings.”
- Click “Restore settings to their default values.”
- Click “Reset” to confirm.
After resetting your browser settings, be sure to check for any remaining adware components or suspicious extensions and remove them if necessary.
Stop Targetchain-flow.com pop-ups
Another effective way to remove Targetchain-flow.com redirects and popups is to use an adblocker. Ad blockers can help remove unwanted ads and pop-ups that may be causing redirects on your browser. By preventing these ads from loading, you can significantly reduce the risk of being redirected to malicious websites. Adblockers can also help improve your browsing experience by reducing page load times and minimizing distractions. There are several free and paid adblocker extensions available for different browsers, such as uBlock Origin, AdBlock Plus, and AdGuard. By installing an adblocker and customizing its settings to your preferences, you can help prevent malicious redirects and enjoy a cleaner browsing experience.
Visit the following page to download AdGuard. Save it on your Windows desktop.
26838 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to launch it. The “Setup Wizard” window will show up on the computer screen as displayed on the image below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick tutorial as shown in the figure below.

Press “Skip” button to close the window and use the default settings, or click “Get Started” to see an quick guidance which will allow you get to know AdGuard better.
Each time, when you start your computer, AdGuard will start automatically and stop unwanted advertisements, block Targetchain-flow.com, as well as other malicious or misleading sites. For an overview of all the features of the program, or to change its settings you can simply double-click on the AdGuard icon, that is located on your desktop.
Conclusion
Targetchain-flow.com is known for causing unwanted redirects, often leading to sites that could threaten your online security. This can disrupt your browsing experience and potentially expose your personal and financial information to cyber threats.
Bottom Line: If you notice strange pop-ups or your browser keeps redirecting you, it’s important to clean your browser and computer right away to keep things safe online. 🛡️💻
Stay cautious about the websites you visit and the permissions you allow. Remember to regularly scan your computer for malware using reliable software like Malwarebytes or Kaspersky Virus Removal Tool, reset your browser settings if necessary, and use an adblocker to prevent unwanted ads and pop-ups from loading. By following these tips, you can enjoy a safer and more secure browsing experience. 🤔