The “We Hacked Your System” email is a scam, and you should not worry or pay the scammers. This message tries to scare you by saying your computer was hacked, that your screen and camera were secretly recorded, and your private videos will be sent to your contacts unless you pay them money in cryptocurrency. The scammers use threatening language and fake technical details to make you panic and act quickly.

In reality, these emails are sent out to thousands of people, hoping that someone gets scared enough to pay. The scammers have not hacked your device. They do not have videos or private data. They know nothing about you except your email address. Their only goal is to frighten you into sending them money.
Remember: These emails are fake and meant to scare and trick you. If you have questions or feel worried, you can talk to a trusted friend or a tech professional. Most importantly, do not pay, and do not let scammers convince you that their threats are real.
A typical “We Hacked Your System” scam email reads as follows:
Consider this message as your last warning.
We hacked your system!
We have copied all the data from your device to our own servers.
Curious videos were recorded from your camera and your actions while watching porn.
Your device was infected with our virus when you visited the porn site.
The Trojan virus gives us full access, allows us to control your device.The virus allows not only to see your screen, but also to turn on your camera, microphone, without your knowledge.
We took over the video from your screen and camera, then we mounted a video in which you can see you watching porn in one part of the screen and masturbating in the other.But that’s not all! We have access to all the contacts in your phone book and social networks.
It won’t take us long to send this video to your friends, family and friends on social networks, messengers and email in minutes.
We have a lot of audio recordings of your personal conversations, where a lot of “interesting” things are revealed!
This information can destroy your reputation once and for all in a matter of minutes.
You have an opportunity to prevent irreversible consequences.To do this:
Transfer 1300 $ USD (US dollars) to our bitcoin wallet.
Don’t know how to make a transfer? Enter the query “Buy bitcoins” into the search field.Our bitcoin wallet bc1qj2aesryeq0yhg6ntk4s8n2sssgtpde4a2jt5eq
After making the payment, your video and audio recordings will be completely destroyed and you can be 100% sure that we won’t bother you again.You have time to think about it and make the transfer – 50 hours!
After you read this letter, we will get an automatic notification. From that moment on, the timer will start.It is useless to complain, because bitcoin-wallets cannot be tracked, as well as the mail from which the letter arrived to you.
We also do not advise you to send this letter to anybody.
In this case the system will automatically send a request to the server, and all data will be published in social networks and messengers.You will not be able to solve the problem by changing passwords in social networks, as all the information is already downloaded to the cluster of our servers.
Think about what your reputation means to you and how much the consequences will be.
You have 50 hours.
🚨 Is the “We Hacked Your System” Email a Scam?
The “We Hacked Your System” email is a common scam designed to scare you into sending money. It claims hackers have taken over your device, recorded embarrassing videos, and copied your contacts. The scammers threaten to share these videos with your friends and family unless you pay them in Bitcoin.
Key Red Flags:
- 💰 Demands Payment in Bitcoin: The message demands $1,300 in Bitcoin, saying only then will your “videos” be deleted. Scammers use Bitcoin because the money can’t be traced.
- 😱 Scare Tactics: The email is written to frighten you. It talks about “ruining your reputation” and gives you a timer to push you into acting fast.
- 📸 Claims of Accessing Your Camera and Data: The scammers say they have hacked your device, turned on your camera, recorded personal videos, and downloaded your contacts. In reality, they do not have this access. This is a bluff to scare you.
- 🔒 Phony Technical Details: The email names “Trojans” and “clusters of servers,” but includes no real details. These are just generic tech terms to make the scam seem real.
- 🚫 Threats Against Contacting Anyone: The email warns you not to tell anyone and says everything will be deleted once you pay. These are fake threats to isolate you and stop you from seeking help.
- 🔗 Random Bitcoin Wallet: Scammers provide a Bitcoin wallet address. If you send money, the scammers simply keep it. There is no real “data” to delete.
In summary, this email is a lie. The scammers are trying to scare you into sending money by making up stories about hacking your device and recording you. If you get this kind of message, do not reply, do not pay, and do not worry. Delete the email, consider changing your passwords just in case, and keep your device and email account secure with strong passwords and up-to-date security software. Never send money or personal details to people who contact you in this way.
Summary Table
| Name | We Hacked Your System Email Scam |
| Type | Sextortion Email Scam |
| How it works | Scammer claims they hacked your device, threaten to share fake videos unless you pay in Bitcoin |
| What they ask for | Payment of $1300 in Bitcoin to the wallet bc1qj2aesryeq0yhg6ntk4s8n2sssgtpde4a2jt5eq |
| Typical signs | Threatening language, fake claims about camera and contacts, urgent timer, asks for payment in cryptocurrency |
| What to do | Do not pay or reply, mark as spam, delete the email, change your passwords if needed, optionally scan your device with antivirus |
🕵️♂️ How the “We Hacked Your System” Email Scam Operates
Scammers behind the “We Hacked Your System” email begin by blasting out threatening messages to thousands of email addresses. These messages claim that the victim’s device has been completely compromised by malware or a trojan installed while visiting an adult website. The email uses intimidating language, such as “Consider this message as your last warning”, and asserts that the scammer has recorded embarrassing videos using the victim’s webcam, copied their files, and stolen their contacts.
To amplify the fear, the scammer claims to have explicit footage of the recipient—often describing fabricated videos showing side-by-side screens of the victim watching adult content and allegedly engaging in private acts. They threaten to send this “evidence” to family, friends, social contacts, and even work colleagues if payment is not received swiftly.
The core of the scam is an urgent demand for payment—typically in untraceable bitcoin—with detailed instructions on how to buy and transfer the funds. Often, the scammer gives the victim a strict countdown, such as “50 hours to pay or else”, pressing emotional panic buttons to rush the victim into compliance. Additional scare tactics include threats to release compromising information, audio recordings, and sensitive conversations, all supposedly ready to be exposed if their demands are not met.
The email insists that it is futile to contact the authorities or try to counteract the scam, warning that any attempts to forward the email, change passwords, or alert anyone will lead to immediate public exposure. The hackers further cement their intimidation with technical-sounding language, mentioning “trojan viruses”, “bitcoin wallets”, and “server clusters” to appear sophisticated and credible.
However, these scams are almost always completely fabricated. The scammers have no actual access to your device, files, webcam, or accounts. They rely on scare tactics, psychological pressure, and the embarrassing subject matter to trick recipients into paying money they do not owe. Frequently, recipients who pay are targeted for additional blackmail or are added to lists of “responsive victims” for future scams.
All of the testimonials, threats, and technical jargon in the emails are either fake or exaggerated. Trusted cybersecurity sources and law enforcement warn that there is no real threat, and advising victims to ignore the scam, change their passwords if needed, and report the email as phishing or spam.
In summary, the “We Hacked Your System” email scam uses widespread, fear-based phishing tactics, fake technical threats, and emotional blackmail to con unsuspecting recipients into sending money—most commonly via untraceable cryptocurrency. Ultimately, victims risk financial loss, stress, and anxiety, all for a threat that is entirely empty and without any technical backing.
🤔 Why Such Scams Are Possible
Making Money From Fear
Scammers behind “We Hacked Your System” emails try to scare people into sending money. They use shocking claims—like saying they have a video of you—to make you panic and pay quickly. Most people imagine the worst and may pay just to make them go away, even if nothing was really hacked.
Easy to Send to Thousands of People
It’s simple and cheap for scammers to send these emails to thousands or even millions of people at once. They don’t need to hack anyone—they just hope a few will believe their threats and pay. Spam filters do block many of these messages, but not all are caught, so some get through.
Knowing People Will Worry
The scammers take advantage of everyone’s fear of being embarrassed or having their privacy invaded. They hope you’ll feel so scared and pressured you’ll pay without thinking, instead of asking if the threat is real.
Hard to Trace and Punish
These criminals usually use fake email accounts and cryptocurrency, making it very hard for the police to find and stop them. They also use scary language, like saying you only have “50 hours” to pay, to pressure you into acting fast before you can think it over.
📧 What to Do When You Receive the “We Hacked Your System” Scam Email
We advise everyone who receives this email to follow the simple steps below to protect yourself from potential scams:
- ❌ Do not believe this email.
- 🔒 NEVER share your personal information and login credentials.
- 📎 Do not open unverified email attachments.
- 🚫 If there’s a link in the scam email, do not click it.
- 🔍 Do not enter your login credentials before examining the URL.
- 📣 Report the scam email to the FTC at www.ftc.gov.
If you accidentally click a phishing link or button in the “We Hacked Your System” Email, suspect that your computer is infected with malware, or simply want to scan your computer for threats, use one of the free malware removal tools. Additionally, consider taking the following steps:
- 🔑 Change your passwords: Update passwords for your email, banking, and other important accounts.
- 🛡️ Enable two-factor authentication (2FA): Add an extra layer of security to your accounts.
- 📞 Contact your financial institutions: Inform them of any suspicious activity.
- 🔄 Monitor your accounts: Keep an eye on your bank statements and credit reports for any unusual activity.
🔍 How to Spot a Phishing Email
Phishing emails often share common characteristics; they are designed to trick victims into clicking on a phishing link or opening a malicious attachment. By recognizing these signs, you can detect phishing emails and prevent identity theft:
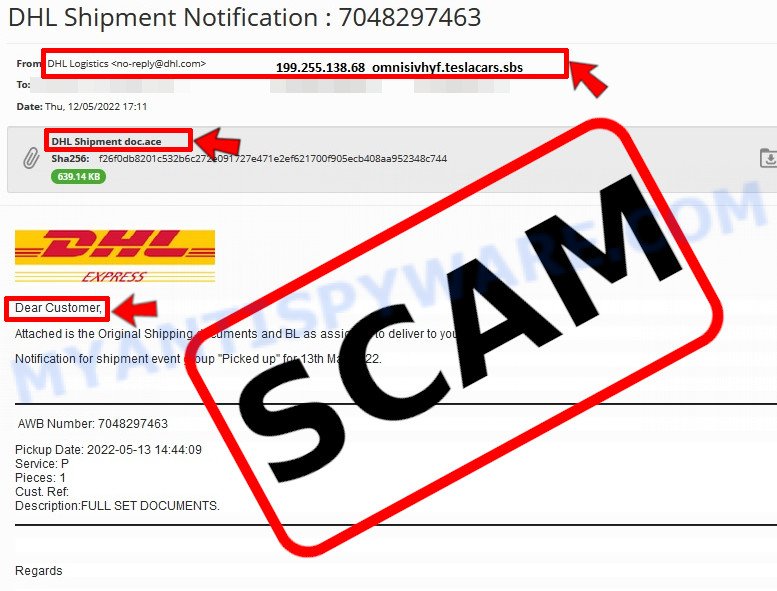
💡 Here Are Some Ways to Recognize a Phishing Email
- ✉️ Inconsistencies in Email Addresses: The most obvious way to spot a scam email is by finding inconsistencies in email addresses and domain names. If the email claims to be from a reputable company, like Amazon or PayPal, but is sent from a public email domain such as “gmail.com”, it’s probably a scam.
- 🔠 Misspelled Domain Names: Look carefully for any subtle misspellings in the domain name, such as “arnazon.com” where the “m” is replaced by “rn,” or “paypa1.com,” where the “l” is replaced by “1.” These are common tricks used by scammers.
- 👋 Generic Greetings: If the email starts with a generic “Dear Customer”, “Dear Sir”, or “Dear Madam”, it may not be from your actual shopping site or bank.
- 🔗 Suspicious Links: If you suspect an email may be a scam, do not click on any links. Instead, hover over the link without clicking to see the actual URL in a small popup. This works for both image links and text links.
- 📎 Unexpected Attachments: Email attachments should always be verified before opening. Scan any attachments for viruses, especially if they have unfamiliar extensions or are commonly associated with malware (e.g., .zip, .exe, .scr).
- ⏰ Sense of Urgency: Creating a false sense of urgency is a common tactic in phishing emails. Be wary of emails that claim you must act immediately by calling, opening an attachment, or clicking a link.
- 📝 Spelling and Grammar Errors: Many phishing emails contain spelling mistakes or grammatical errors. Professional companies usually proofread their communications carefully.
- 🔒 Requests for Sensitive Information: Legitimate organizations typically do not ask for sensitive information (like passwords or Social Security numbers) via email.
Conclusion
The “We Hacked Your System” Email is a scam, relying on fabricated threats, fake evidence, and manipulative scare tactics to create a false sense of urgency and fear. The scammers behind this email use baseless claims and alarming language to pressure victims, threatening to leak embarrassing personal content and damage reputations unless a ransom is paid.
Instead of having any real access to your device, the perpetrators use generic messages meant to frighten as many people as possible. The email tries to appear legitimate with technical jargon and urgent deadlines, but provides zero authentic evidence of a hack.
Bottom Line: Do not respond to or pay the ransom demanded in the “We Hacked Your System” email. This is a common extortion scam designed to exploit your fears with no real proof of compromise. Always verify unsolicited threats before taking action. If you receive such emails, report them as spam, do not engage with the sender, and consider running a security scan on your devices for peace of mind. If something seems suspicious, it’s likely a scam. Stay cautious.