 Windows Vista Recovery is a misleading computer optimization and hard disk drive defragmenter software from the same family of malware as Windows XP Recovery. The program may look legitimate computer’s optimization tool, but remember, its only an imitation! In reality, the malicious software blocks legitimate Windows applications, detects fake hard drive problems and displays various fake error messages that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Do not pay for the bogus software! Simply ignore all that it will display you and remove Windows Vista Recovery from your computer as quickly as possible!
Windows Vista Recovery is a misleading computer optimization and hard disk drive defragmenter software from the same family of malware as Windows XP Recovery. The program may look legitimate computer’s optimization tool, but remember, its only an imitation! In reality, the malicious software blocks legitimate Windows applications, detects fake hard drive problems and displays various fake error messages that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Do not pay for the bogus software! Simply ignore all that it will display you and remove Windows Vista Recovery from your computer as quickly as possible!
Windows Vista Recovery is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software as you do not even notice that. Moreover, the authors of of the fake program may also distribute this malware on social networks (Twitter, My Space, Facebook, etc) and spam emails. Please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC.
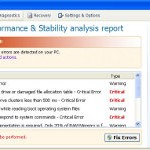
During installation, Windows Vista Recovery will be configured to run automatically when Windows starts. Once installed, the rogue will say that it needs to run in Safe Mode and then will show faked Safe Mode. Next, WindowsVistaRecovery does a fake scan of your computer then tells you it has found numerous critical errors, e.g. “Ram Temperature is 83 C. Optimization is required for normal operation.”, “32% of HDD space is unreadable”, “Registry Error – Critical Error”, “Bad sectors on hard drive or damaged file allocation table”, etc. It will require you to pay for the fake software before it “repairs” your machine of the problems. Of course, all of these errors are a fake. So, you can safety ignore the false scan results.
In addition to the above-described, while Windows Vista Recovery is running, it will block legitimate Windows applications on your computer and won’t let you download anything from the Internet. Last, but not least, the rogue will display a lot of messages and alerts with such fake information:
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Windows – No Disk
Exception Processing Message 0×0000013
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Of course, all of these warnings are a fake. This is an attempt to make you think your computer in danger. Like false scan results you can safely ignore them.
What is more, Windows Vista Recovery hides files and folders on your system drive (disk C by default).
![]() To see all hidden files and folders you need to open Folder options (click Organize, next “Folder and search options”, next “View” tab). Select “Show hidden files and folders” option and click OK button.
To see all hidden files and folders you need to open Folder options (click Organize, next “Folder and search options”, next “View” tab). Select “Show hidden files and folders” option and click OK button.
As you can see, obviously, Windows Vista Recovery is a scam. You should not trust any problem alerted by the program and do not purchase it because you will simply give your money for cyber criminals. You need as quickly as possible to remove the malicious software. Follow the removal instructions below, which will remove Windows Vista Recovery and any other infections you may have on your computer for free.
Automated Removal Instructions for Windows Vista Recovery
Step 1. Reboot your computer in Safe mode with networking
![]() It is possible that Windows Vista Recovery will not allow you to start the Malwarebytes Anti-malware or another malware remover. Then you will need to reboot your computer in Safe mode with networking.
It is possible that Windows Vista Recovery will not allow you to start the Malwarebytes Anti-malware or another malware remover. Then you will need to reboot your computer in Safe mode with networking.
Restart your computer.
After hearing your computer beep once during startup, start pressing the F8 key on your keyboard. On a computer that is configured for booting to multiple operating systems, you can press the F8 key when the Boot Menu appears.
Instead of Windows loading as normal, Windows Advanced Options menu appears similar to the one below.
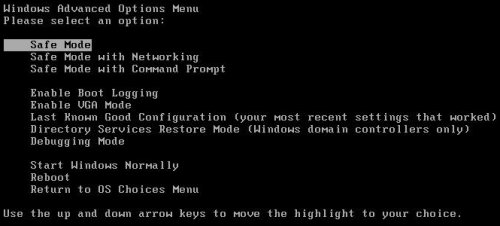
Windows Advanced Options menu
When the Windows Advanced Options menu appears, select Safe mode with networking and then press ENTER.
Step 2. Unhide hidden files
![]() Windows Vista Recovery hides the folders and files on your system drive (disk C by default). To unhide those files and folders you need to complete this step.
Windows Vista Recovery hides the folders and files on your system drive (disk C by default). To unhide those files and folders you need to complete this step.
Click Start. Type in Search field cmd and press Enter. Command console “black window” opens. Type attrib -h /s /d and press Enter. Close Command console.
Step 3. Remove TDSS trojan-rootkit
![]() Windows Vista Recovery may be bundled with TDSS trojan-rootkit, so you should run TDSSKiller to detect and remove this infection.
Windows Vista Recovery may be bundled with TDSS trojan-rootkit, so you should run TDSSKiller to detect and remove this infection.
Download TDSSKiller from here and unzip to your desktop.
Open TDSSKiller folder. Right click to tdsskiller and select rename. Type a new name (123myapp, for example). Press Enter. Double click the TDSSKiller icon. You will see a screen similar to the one below.
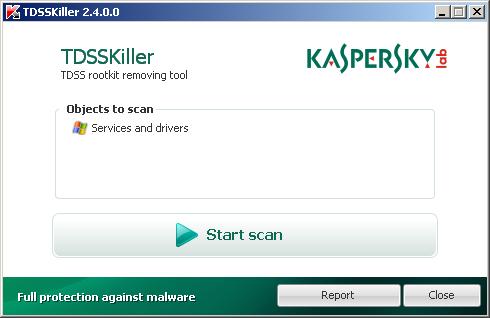
TDSSKiller
Click Start Scan button to start scanning Windows registry for TDSS trojan. If it is found, then you will see window similar to the one below.
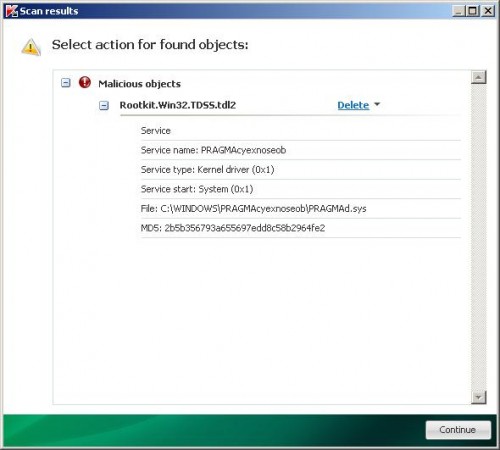
TDSSKiller – Scan results
Click Continue button to remove TDSS trojan.
Step 4. Remove Windows Vista Recovery associated malware
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
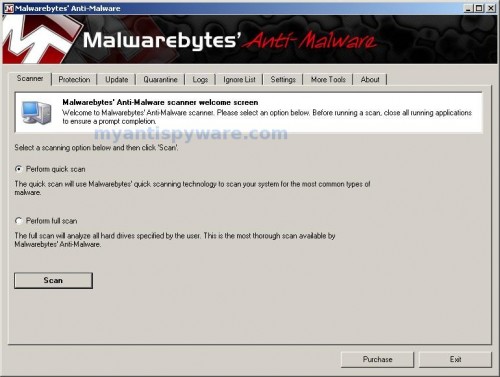
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer for Windows Vista Recovery associated malware. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
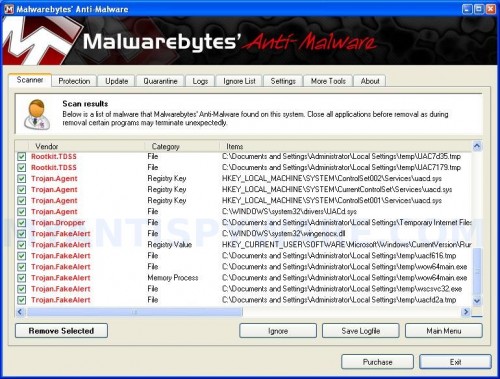
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove Windows Vista Recovery. MalwareBytes Anti-malware will now remove all of associated Windows Vista Recovery files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Windows Vista Recovery removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Windows Vista Recovery creates the following files and folders
%UserProfile%\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
%CommonAppData%\[RANDOM]
%CommonAppData%\~[RANDOM]
%UserProfile%\Start Menu\Programs\Windows Vista Recovery\Uninstall Windows Vista Recovery.lnk
%UserProfile%\Start Menu\Programs\Windows Vista Recovery\Windows Vista Recovery.lnk
%UserProfile%\Desktop\Windows Vista Recovery.lnk
%CommonAppData%\[RANDOM].exe
Note: %CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista)
Windows Vista Recovery creates the following registry keys and values
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\USE FORMSUGGEST = Yes
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CERTIFICATEREVOCATION = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WARNONBADCERTRECVING = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WARNONZONECROSSING = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\3\1601 = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\WINTRUST\TRUST PROVIDERS\SOFTWARE PUBLISHING\STATE = 146944
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\CONTROL\SESSION MANAGER\PENDINGFILERENAMEOPERATIONS = \??\%CommonAppData%\[RANDOM].exe









I followed the instructions above, ran the TDSSkiller and it showed nothing, ran the malwarebytes and it showed 8 files. All was good. I removed them, restarted the computer as it asked and poof the *Windows Vista Recovery* program is still up and running. I ran everything a 2nd time, this time it only removed 1 file, restarted my computer when prompted and poof still there. 🙁
Thank you so much. This one really had it’s guard up. If it wasn’t for this guide I’d be screwed.
🙂
thank u very much. well done!
Tis one reallt scared me lol thankyou for the instructions on removing it. I willuse this site again. Also I got it from a fake fed ex email saying here’s mt package rout number click here to track package and boom it started dowloading crap so beware :))
when I type in the cmd and then the attrib…. and hit enter, the computer starts listing the files, but then reads “Not resetting sytem file”. Further, the TDSS killer is not detecting any virus. Do you have any suggestions? thanks
You saved my laptop’s life!! Thank you so much!!! 😀
If I have AVG anti virus, will it be affected if I install those two softwares you said?
Mark, you have completed the last step ?
I completed all the steps. It appears as if I am not getting into the actual safe mode while networking. Is it possible that the virus isn’t allowing me to do get into actual system? Thank you.
i have gone through all the steps. after the restart, i still only see the black screen like i am still in “safe mode” and none of my files are appearing.
i can click on “all programs” and still see they are there… so i’m not sure what to do now. any suggestions would be greatly appreciated
grywolf9, Malwarebytes should fix the problem. Try update it and perform a fresh scan.
Matt, you can use both tools above with AVG.
i’ve done the above steps, then ran MBAM, then a couple of other command prompts like dds and something else i can’t remember, but a lot of my files are still hidden! what can i do please??
You are my hero. Thanks a lot man!
So yeah, I have Avira on my laptop. But it obviously did not keep this virus from coming through. Any suggestion/tips, as to which free antivirus might be the best one to use, that can warn user rightaway if something suspicious is trying to download?
Thanks again!
I have the same problem as grywolf9. I ran the scan several times and it doesn’t find anything, yet still have the black screen with only this program on the desktop. I have my taskmanager back but nothing else seems to be fixed.
Hi. I followed everything and afterwards restart the computer. However it still shows the black background with almost all desktop icon missing. can you clarify the part where you use cmd to unhide files? When I typed in ” attrib -h /s /d” it doesn’t work so instead i just entered “attrib”. Could that be why the icons/background are still missing?
The steps are working perfectly……got rid of the virus…….thanks guys…….
i downloaded and ran Tdss killer and it didnt not find the program but my laptop still has the virus why? i have not ran malware yet
I am having the same issue as grywolf9 in that when I complete all steps and restart my computer I still get the black screen and no desktop icons.
After runing TDSSKiller it found nothing so I continued on to Malwarebytes’ Anti-Malware where it found 30 files to fix. Now I don’t get the anoying pop ups and it looks like the Windows Vista Recovery virus is gone, but still a black screen. I am not an expert at fixing computers. Might there be something I missed or some other step so I get my files back. I cannot see them still.
I checked for updates like you suggested to grywolf9 and ran another scan, but still there are no more files to be found. I will try restarting and see what happens.
I tried going back to the second step and opening cmd and entering attrib -h /s /d, and I get the same thing as Matt:
“when I type in the cmd and then the attrib…. and hit enter, the computer starts listing the files, but then reads “Not resetting sytem file”. Further, the TDSS killer is not detecting any virus.”
Unsure what to do next.
This only works for some variants. I’ve seen at least 4-5 over the last two weeks that block Malwarebytes, Combofix and completely wipe out the start menu (sometimes the icons are in the temp folder but sometimes NOT). Everywhere on the internet are these generic removal instructions – unhide, run malwarebytes, profit. Not so anymore.
I’ve got through all the procedure.
I can see the files.
However I cannot see the program
when I click all program on start menu.
Some program such as MS WORD is shown as empty so that it cannot be started.
How can i fix it?
Thank you.
Thnx mate for posting these ! It helps me alot! I get crazy cz I thot it’s a real stupid virus from shit fedex spam! Then my pc got black background nd my icons programs nd the most imp my saved photos where fuckd up! But I try to search any sol. Nd guess wut…. I just followed this steps given above till step2 only iv done but my pc where back all to normal ! Didn’t even take me further til step 3 ! Great job thnx fr posting this! Bless me!
when I type in the cmd and then the attrib…. and hit enter, the computer starts listing the files, but then reads “Not resetting sytem file”. Further, the TDSS killer is not detecting any virus. What do I do to fix this?
Ive downloaded tdsskiller and Malwarebytes but when i try to open tdsskiller nothing happens and when i try to install malwarebytes it say access denied. Please help