Smss32.exe, winlogon32.exe, helper32.dll are components of trojan FakeAlert. Once installed, the trojan will configure itself to run automatically when Windows starts. When the trojan is started, it will display a screen that stats that Worm.Win32.Netsky detected on your computer as an attempt to make you think your computer in danger. The alert is fake and you can safety ignore it.
What is more, the “smss32.exe, winlogon32.exe, helper32.dll” trojan may display a lot of popups, disable Windows Task Manager, change a desktop background, block the ability to run any applications including antivirus and antispyware programs. The trojan will also download and install Internet Security 2010 onto computer automatically without your permission. Internet Security 2010 is a rogue antispyware program, that reports false infections and shows fake security alerts as method to to trick you into purchase so-called “full” version of the software.
Use the removal guide below to remove smss32.exe, winlogon32.exe, helper32.dll and any associated malware from your computer for free.
Symptoms in a HijackThis Log
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon32.exe
O4 – HKLM\..\Run: [smss32.exe] C:\WINDOWS\system32\smss32.exe
O10 – Unknown file in Winsock LSP: c:\windows\system32\helper32.dll
O10 – Unknown file in Winsock LSP: c:\windows\system32\helper32.dll
Use the following instructions to remove remove smss32.exe, winlogon32.exe, helper32.dll (Remove Worm.Win32.Netsky Spyware Alert)
Step 1.
Download HijackThis from here and save it to your Desktop.
If you cannot run HijackThis, then re-download it, but before saving HijackThis.exe, rename it first to explorer.exe and click Save button to save it to desktop.
Run HijackThis. Click “Do a system scan only” button. Now select the following entries by placing a tick in the left hand check box, if present:
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon32.exe
O4 – HKLM\..\Run: [smss32.exe] C:\WINDOWS\system32\smss32.exe
Place a checkmark against each of them. Once you have selected all entries, close all running programs then click once on the “fix checked” button. Close HijackThis.
Step 2.
Download LSPFix from here and unzip it to your Desktop.
Run LSPFix. Place a tick in the “I know what i`m doing”.
In the KEEP box select helper32.dll and press “>>” button.
Press Finish>> button. When LSPFix is done removing the LSP you will see a summary box. Press OK.
Step 3.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
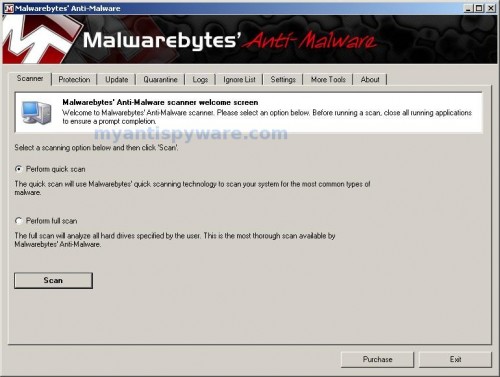
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for remove smss32.exe, winlogon32.exe, helper32.dll. This procedure can take some time, so please be patient.
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
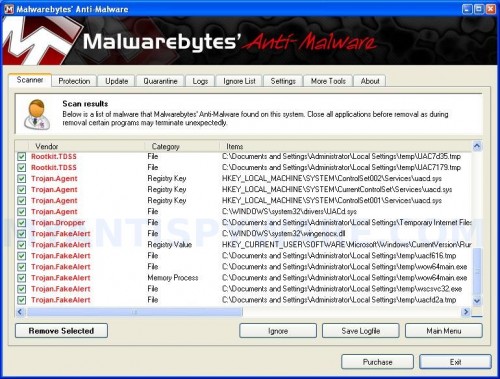
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove THREATNAME. MalwareBytes Anti-malware will now remove all of associated remove smss32.exe, winlogon32.exe, helper32.dll files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Smss32.exe, winlogon32.exe, helper32.dll creates the following files and folders
C:\WINDOWS\system32\helper32.dll
C:\WINDOWS\system32\smss32.exe
C:\WINDOWS\system32\winlogon32.exe
C:\WINDOWS\system32\41.exe
C:\WINDOWS\system32\warning.html
Smss32.exe, winlogon32.exe, helper32.dll creates the following registry keys and values
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\ActiveDesktop | NoChangingWallpaper = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer | NoSetActiveDesktop = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer | NoActiveDesktopChanges = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run | smss32.exe = “C:\WINDOWS\system32\smss32.exe”
HKEY_CURRENT_USER\Software | 8636065b-fef0-4255-b14f-54639f7900a4 = “8636065b-fef0-4255-b14f-54639f7900a4”
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Desktop\General | Wallpaper = “C:\WINDOWS\system32\warning.html”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer | NoSetActiveDesktop = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer | NoActiveDesktopChanges = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop | NoChangingWallpaper = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System | DisableTaskMgr = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon | Userinit = “C:\WINDOWS\system32\winlogon32.exe”









I tried this today, and it worked…that you so much for this. You’ve really saved a noob a lot of time, trouble and money.
Hey there, I followed the steps but helper32.dll was not there in step 2. I comtinued on to step 3 and it did get rid of the pop-ups but my background is still showing that warning about my system being infected. The lspfix showed mswsock.dll, winrnr.dll, mdsnNSP.dll and rsvpsp.dll. Should I remove any of these?
Thanks so much.
No, mswsock.dll, winrnr.dll, mdsnNSP.dll and rsvpsp.dll are legitimate files.
Right click to Desktop, choose Properties, Desktop tab and set your background.
Worked like a Charm!!!
Just follow step by step & if necessary apply your logical thinking too.
Even my company tech. was not able to fix it says “I will come tomorrow after consulting my senior officer”
I worked on it & did it. thanks to this site.
I got infected but since im using sandboxie, i deleted contents and it went away. Try using a virtual web browser like this to prevent getting viruses online.
HELP: I have this virus on my desktop computer and before I found this thread, I ran a McAfee scan and it deleted the file: C:/Windows/System32/SMSS32.exe and now when I go to log on after a restart it keeps taking me back to the log on screen to hit ctrl alt delete to log on with my password, I enter my password and it keeps taking me back to the log on screen??? Any suggestions?
Thanks Patrick, I thought maybe my computer was still infected because that warning on the background was still there. I changed it and there are no more problems.
Thanks for all your help… this is a great site.
Jason, looks like McAfee also removed winlogon32.exe.
You need to boot your computer in Recovery console, then copy userinit.exe to winlogon32.exe and reboot your PC. Read comments here (only replace winlogon86 to winlogon32).
So far these steps seem to be fitting my problem the most. Like Heather, I did not have the helper32.dll show up.
However my problem with the virus is that it seems to be preventing me from opening any programs. I run the Malwarebytes and it closes instantly. It pops up in the task manager for barely a second. Is there something else that needs to be changed in order to run that program successfully? Something in the registry maybe?
(my computer is a samsung notebook with windows xp if that helps any)
Denise, if you have done step1 and still Malwarebytes is blocked, then ask for help in our Spyware removal forum.
I have smss32 on my dell and have now lost my desktop icons and my start button. Anybody know how I can get my desktop back. I ran superantispyware a buch of times and found the problem but it kept coming back after the program removed it.
jim, you have done 1-2 steps ?
If you need a help, then go to our Spyware removal forum.
Since Internet Security 2010 solicits credit card payments, can’t the account holder be tracked and shut down?
I had the virus smss32.exe on my desktop yesterday and since i didn’t know this website, spent hours to try to take the smss32.exe off the registry using regseeker but it came back always. So finally I had to reinstall my windows and all the 3 sce packs.
below’s how i manually removed this virus/spyware:
1. delete from c:\windows\system32 (some of these files may also be in C:\ root folder)
smss32.exe
41.exe
IS15.exe
khkil.exe
2. remove smss32.exe from startup profile using
-> control panel -> admin tools -> system configuration
3. edit registry (computer\hkey_local_machine\software\microsoft\windowsNT\currentversion\winlogon\)
replace “winlogon32.exe” with “userinit.exe”
4. restart windows, if everything’s normal, delete “winlogon32.exe” and “helper32.dll” from c:\windows\system32
5. as a final check, do a complete system search for all above files to confirm files are completely removed.
6. I haven’t done this but I plan to go into system restore to remove all the days where I know the computer is infected so I don’t end up restoring to an infected system.
Thanks for the steps they successfully removed the trojan FakeAlert from my system in a few minutes, after I wasted two hours letting Symantic scan my system in hopes it would fix it. So yay for you!! 🙂
This helped a lot!
One comment: I was unable to login at all and can’t run the necessary tools in Recovery Console. So, started a XP REPAIR then hit SHIFT-F10 as soon as it rebooted into XP, while the repair counted down from 39 minutes. SHIFT-F10 opens a command window, where you can run REGEDIT, HijackThis, etc to fix the problems. Not sure a repair would be possible without doing this.
My computer had Win32.NetSky,
Symptoms:
1. Desktop on the computer showed that your computer is infected with Win32.NetSky
2. In the system tray I see RED “X “ icon.
3. Task Manager is disabled
4. View->Field Options in Windows Explorer is also disabled.
5. If I try to system restore to previous restore point it display the following message: “System restore has been turned off by your group policy. To turn on system restore; contact your domain administrator.”
System restore was enabled on my system.
What I did:
I rebooted the system in safe mode, same behavior (task manager disable, system restore is not available etc.).
Investigation:
I found following files under C:\Windows\System32 with most recent date time stamp (say 1/13/2010):
1. IS15.exe 0 bytes
2. Helper32.dll 0 bytes
3. IE Warning.htm 3kb
4. wpa.dbl 2kb
5. winlogon32.exe 21kb
6. smss32.exe 21kb
7. oh77tim.dll 145kb
8. info.tmp 40kb
Uncheck through MSCONFIG
In Startup Tab I also UNCHECKED
1. SMSS32 which point to C:\Windows\System32\SMSS32.EXE
2. AWY84 which point to C:\Documents and Settings\\Local Settings\Temp\AWY84.EXE
Deleting files while logged in SAFE mode:
1. I deleted all the files from C:\Documents and Settings\\Local Settings\Temp.
There were couple EXE (e.g. AWY84.EXE) files with most recent date time stamp.
2. Deleted files form C:\Windows\System32
a. IS15.exe 0 bytes
b. Helper32.dll 0 bytes
c. IE Warning.htm 3kb
d. wpa.dbl 2kb
e. winlogon32.exe 21kb
f. smss32.exe 21kb
g. oh77tim.dll 145kb
h. info.tmp 40kb
Rebooted:
Now when I go to log on after a restart it keeps taking me back to the log on screen to hit ctrl alt delete to log on with my password, I enter my password and it keeps taking me back to the log on screen?
Same behavior is happening in SAFE Mode as well.
1. Put in your your Windows Disc and boot into Repair, you will see a dos mode, press “1″ go into “C:\Windows” directory and type in your user/admin password.
after that go into your “System32″ folder by typing “cd System32″ without “quotes”
then enter in:
“copy winlogon.exe winlogon86.exe” and
“copy winlogon.exe winupdate86.exe” <— just incase
type: "exit" to restart
I am unable to log-in to my system. When I log on after a restart it keeps taking me back to logon screen.
I really, really appreciate if someone helps to resolve this issue.
Thanks in anticipation.
Please HELP! I have this virus on my computer and before I found this thread, I deleted the file: C:/Windows/System32/SMSS32.exe, C:/Windows/System32/IS15.exe,
C:/Windows/System32/helper32.exe and now when I go to log on after a restart it keeps taking me back to the log on screen to hit ctrl alt delete to log on with my password, I enter my password and it keeps taking me back to the log on screen?
I followed the instruction what U8MYR!CE suggested on
But I am still unable to logon. System keeps taking me back to the log on screen.
Any suggestions?
In the Recovery console use the following commands:
copy userinit.exe winlogon32.execopy userinit.exe winlogon86.exe
Thanks so much tried and worked perfectly. Did not find the file at step 2 but everything else worked great thank you.
I used your steps and was able to rid my pc of the virus but after I restarted it I was no longer able to connect to the internet. I actually had my service provider send out a tech who found nothin wrong with the router….it works fine. I was on the internet following your steps but I haven’t been able to get on since. Do you know why that my be?
Hi, thanx for help, it worked for me.
Got a question, how could i get infected (or how do you get infected with this)… my computer is not in a network. Is there any patch/update for windows (mine is xp64) recomendend for protecting for this?
Seeyo and thanx again. Sol from Argentina.
Sam Gil,
the steps I outlined on my 10-Jan post are in sequence for a reason. The one thing I found during my trial and error of trying to remove the virus is that if I manually delete winlogon32.exe, I could not logon properly — not sure if that’s the same root cause for you. winlogon32.exe has to be properly removed via editing the registry. what i also found out is that winlogon32.exe spawns smss32.exe (and maybe other files too) during every startup and puts it into the startup profile — sneaky. You seem to have a bunch of other additional files listed (hope you don’t have more than one virus on your system).
I didn’t include this on my previous post but thought I should add that my system is running regular Vista windows with Norton internet security 2009 when I got hit with the virus.
Thank you, Patrik, and to all the people you may have worked with to put out this info. My computer is now disinfected. God bless
javier, try run WinSock XP Fix.
I followed these steps, but, like Jim above, have lost all desktop icons, start button, etc. (after windows explorer repeatedly crashes).
Help.
I did everything, but I cannot change my desktop or run taskmanger..any help would be great!
I had this annoying “Worm.win32.netsky” warning message poping up on my Windows 7 pc…. my current AV software (well known brand) kept spotting a “generic fake alert!htm” and kept removing the “00000035.js” file. however, everytime I started the Pc the same pop-up with the virus warning kept coming up and the AV software kept removing the same file… In addition, I also kept seeing a pop-up that said the pc was infected and it was going to download some AV software (Internet Security 2010??).. My AV software was NOT stopping this….
Your steps 1 to 3 above saved the day… all seems to be removed…. I did not find helper32.dll as per your step 2 (I think that it is still there – I saw a file in a windows directory with same name and size 0kb) but step 3 went well.. rebooted the pc and the “fake virus” seems to be GONE! Thank you for the help… the PC seems to be working well.
nb. Malwarebytes’ Anti-Malware found a lot more “malwares” on my PC and removed them (My old/current Anti-virus program did NOT find them)
Thank you so much! The instructions were very detailed and they worked. And I’m not very good with computers.
You’re great!