 Virus Protector is a rogue antispyware program that installed through the use of trojans and uses false scan results and fake security alerts informing that your computer is infected in order to trick you into purchasing the full licensed version.
Virus Protector is a rogue antispyware program that installed through the use of trojans and uses false scan results and fake security alerts informing that your computer is infected in order to trick you into purchasing the full licensed version.
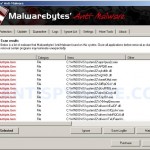
Once installed, the rogue will configure itself to run automatically when you logon to Windows and drop numerous files with random names on to your computer that are made to appear as infections, but are in reality harmless. These files, during the scan, Virus Protector will label as malware, trojans and viruses. Of course, the scan results are a fake. The malicious program is unable to find the infections, as will not protect you from possible infection in the future. Important, do not trust the scan results, simply ignore them.
In order to create the fully simulation that you computer is infected, Virus Protector will display various fake security warnings that stats:
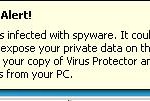
Spyware Alert
Your computer is infected with spyware. It could damage your
critical files and expose your private data on the Internet. Click
here to register your copy of Virus Protector and remove
spyware threats from your PC.
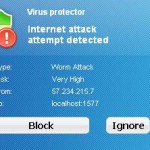
Process is blocked!
Harmful memory infections detected.
Process [filename] was terminated.
Virus Protector
Internet attack
attempt detected
However, all of these alerts are fake and like false scan results should be ignored!
If you get infected with Virus Protector, please do not be fooled into buying it. Instead of doing so, follow the removal guide below in order to remove Virus Protector and any associated malware from your computer for free.
More screen shoots of Virus Protector
Symptoms in a HijackThis Log
F2 – REG:system.ini: Shell=C:\WINDOWS\system32\
O20 – AppInit_DLLs:
Spyware software are surreptitiously installed on user`s computer to collect information about computer’s configuration, user`s private information, user’s activity without his consent. Spyware may also change Windows settings, download and install other malicious programs without the user’s knowledge.
.dllUse the following instructions to remove Virus Protector (Uninstall instructions)
Read the article: How to reboot computer in Safe mode and reboot your computer in the Safe mode with command prompt.
Once Windows loaded, command prompt (black window) opens. Type notepad and press Enter.
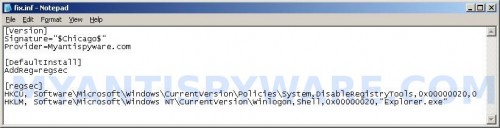
A notepad window opens. Type the following text into notepad:
[Version]
Signature="$Chicago$"
Provider=Myantispyware.com
[DefaultInstall]
AddReg=regsec
[regsec]
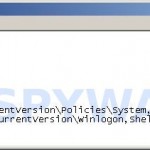
HKCU, Software\Microsoft\Windows\CurrentVersion\Policies\System,DisableRegistryTools,0x00000020,0
HKLM, Software\Microsoft\Windows NT\CurrentVersion\Winlogon,Shell,0x00000020,"Explorer.exe"
Once finished, please checkup the text twice. You will see a screen similar to the one below.
Notepad
Save this as fix.inf to your Desktop (remember to select Save as file type: All files in Notepad). Close Notepad.
In the command prompt type Explorer.exe and Press Enter. Windows Explorer opens. Locate the fix.inf, click right button and select Install. Close Windows Explorer.
In the command prompt type shutdown -r and press Enter. Your computer will be rebooted.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for Virus Protector infection. This procedure can take some time, so please be patient.
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
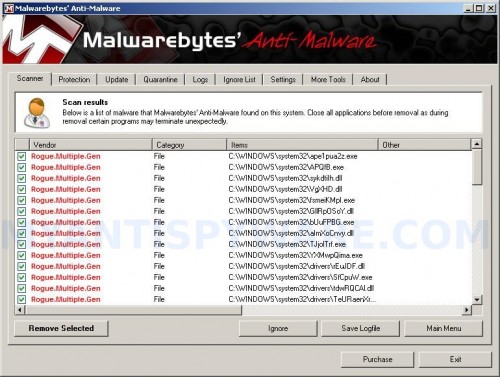
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove Virus Protector. MalwareBytes Anti-malware will now remove all of associated Virus Protector files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Virus Protector creates the following files and folders
The rogue uses random filenames to hide itself.
Virus Protector creates the following registry keys and values
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Virus Protector”











i tried all and it worked !! THX YOU MATE !! thought my computer was going to die 🙁 but it didnt thx to you <33 i love you 😀
I tried to access via safe mode with command line prompt, but it responds with a msg “The command prompt has been disabled by your administrator”
How am I supposed to enable my command prompt again via safe mode so that I can do the the rest you taught above?
Martin, what is your Windows version ?
sry I didn’t mention b4, it’s vista SP1
Hello i have currently been attacked by what i think is a newer version of this Virus Protector program when i first got it i thought oh just another one of these anoying things and i have already had Malware bytes on my computer for some time i tried running the malwarebytes and i got that it found 9 viruses but when i tried to remove them it made my computer shutdown. Then as i tried to get it running again i logged onto my account and the virus scanner pops up and gives me that false info i went to open in safe mode and it did nothing to fix the problem so i went to open in safe mode with command prompt and tried opening my malwares again but as i foudnd the nine viruses the same thing happened again and when i tried to delete them i got shutdown on my computer please help
also when i try to install the fix file you had me save to my desktop says that the file does not allow this support method of instillation
when i tried updating my malware it code 732gave error
i tried manually fixing the udate problem to malware but i cant get on teh internet when in or out of safe mode because of the protector virus thing
Thank you, it worked. It all worked!:)
i cant restart in safe mode or safe mode without network or command prompt, shows a window with files and stays that way
what can i do????
Martin, boot your computer from Windows installation disk. Once loaded, select Repair option.
Tyler, try run Registry editor (type regedit and Press Enter in the command prompt). Then navigate to HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon, click twice to Shell and type Explorer.exe. Click Ok and close Registry editor. Restart your PC.
Niko, what is a window ? Windows explorer ? you can open any folders and run anything ?
thankyou for all your help with Virus Protector bug (or as I call it, the big pain in the ***). Although I didnot have to interact with you your posts here what I needed. The first time I got it I was able to resolve it with ctrl+alt+del with no problem, but this time the program disabled the task mgr. Again thank you for your help.
Paco
thankyou for your help. Although I didnot interact with you your postings helped clear up my problem. I think that what ever government dept that controls what Virus Protection in doing should fine them millions and shut them down.
Paco
Thank you so much for this extremely valuable information. I was getting my but whipped for about 4 hrs. trying to run Malwarebytes and could not get it to run. After booting in safe mode w/ command prompt and following your instructions, I was able to get to the desktop, update Malwarebytes and clean this thing up. You guys rock!!!!!
This worked flawlessly! Thanks! That fix file was the key!
I had/have the Virus Protector bug on my system, and performed ALL of the removal procedures involved to get rid of this pesky bug. Problem is, I get REDIRECTED to other sites regularly. I’ve used Hijackthis to verify what files I have on my machine (log below) and the only thing I can see that might be the problem is a lsass.exe that is running in the background. Attempted to End the process for this program and tried to delete this file from its location, but to no avail. anyone with a CLEAR understanding of Hijackthis & systems, please advise.
HEEEEEEEEEEEEEEEELP! 🙁
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 6:09:34 PM, on 4/10/2010
Platform: Windows 2000 SP4 (WinNT 5.00.2195)
MSIE: Internet Explorer v6.00 SP1 (6.00.2800.1106)
Boot mode: Normal
Running processes:
C:\WINNT\System32\smss.exe
C:\WINNT\system32\winlogon.exe
C:\WINNT\system32\services.exe
C:\WINNT\system32\lsass.exe
C:\WINNT\system32\ibmpmsvc.exe
C:\WINNT\system32\Ati2evxx.exe
C:\WINNT\system32\svchost.exe
C:\WINNT\System32\svchost.exe
C:\WINNT\system32\ZoneLabs\vsmon.exe
C:\WINNT\system32\LEXBCES.EXE
C:\WINNT\system32\spoolsv.exe
C:\WINNT\system32\LEXPPS.EXE
C:\Program Files\Alwil Software\Avast4\aswUpdSv.exe
C:\Program Files\Alwil Software\Avast4\ashServ.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\WINNT\system32\MSTask.exe
C:\WINNT\system32\stisvc.exe
C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
C:\Program Files\Alwil Software\Avast4\ashWebSv.exe
C:\Program Files\Alwil Software\Avast4\ashMaiSv.exe
C:\WINNT\system32\Ati2evxx.exe
C:\WINNT\Explorer.EXE
C:\WINNT\System32\WBEM\WinMgmt.exe
C:\DOCUME~1\THINKP~1\LOCALS~1\Temp\RarSFX2\RegCure.exe
C:\Program Files\Lexmark X6100 Series\lxbfbmgr.exe
C:\Program Files\Cisco Systems\Aironet Client Monitor\ACUMon.Exe
C:\Program Files\Common Files\InstallShield\UpdateService\issch.exe
C:\Program Files\Common Files\Java\Java Update\jusched.exe
C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
C:\PROGRA~1\ALWILS~1\Avast4\ashDisp.exe
C:\Program Files\Lexmark X6100 Series\lxbfbmon.exe
C:\PROGRA~1\Yahoo!\MESSEN~1\YahooMessenger.exe
C:\Program Files\Spyware Doctor\swdoctor.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\WINNT\system32\taskmgr.exe
C:\Program Files\Hijackthis\HijackThis.exe
R0 – HKCU\Software\Microsoft\Internet Explorer\Main,Local Page =
R0 – HKLM\Software\Microsoft\Internet Explorer\Main,Local Page =
O2 – BHO: &Yahoo! Toolbar Helper – {02478D38-C3F9-4efb-9B51-7695ECA05670} – C:\PROGRA~1\Yahoo!\Companion\Installs\cpn0\yt.dll
O2 – BHO: AcroIEHelperStub – {18DF081C-E8AD-4283-A596-FA578C2EBDC3} – C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll
O2 – BHO: Spybot-S&D IE Protection – {53707962-6F74-2D53-2644-206D7942484F} – C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 – BHO: PCTools Site Guard – {5C8B2A36-3DB1-42A4-A3CB-D426709BBFEB} – C:\PROGRA~1\SPYWAR~1\tools\iesdsg.dll
O2 – BHO: PCTools Browser Monitor – {B56A7D7D-6927-48C8-A975-17DF180C71AC} – C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O2 – BHO: Java(tm) Plug-In 2 SSV Helper – {DBC80044-A445-435b-BC74-9C25C1C588A9} – C:\Program Files\Java\jre6\bin\jp2ssv.dll
O2 – BHO: JQSIEStartDetectorImpl – {E7E6F031-17CE-4C07-BC86-EABFE594F69C} – C:\Program Files\Java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
O2 – BHO: SingleInstance Class – {FDAD4DA1-61A2-4FD8-9C17-86F7AC245081} – C:\PROGRA~1\Yahoo!\Companion\Installs\cpn0\YTSingleInstance.dll
O3 – Toolbar: Yahoo! Toolbar – {EF99BD32-C1FB-11D2-892F-0090271D4F88} – C:\PROGRA~1\Yahoo!\Companion\Installs\cpn0\yt.dll
O3 – Toolbar: @msdxmLC.dll,-1@1033,&Radio – {8E718888-423F-11D2-876E-00A0C9082467} – C:\WINNT\system32\msdxm.ocx
O4 – HKLM\..\Run: [Synchronization Manager] mobsync.exe /logon
O4 – HKLM\..\Run: [Lexmark X6100 Series] “C:\Program Files\Lexmark X6100 Series\lxbfbmgr.exe”
O4 – HKLM\..\Run: [Adobe Reader Speed Launcher] “C:\Program Files\Adobe\Reader 9.0\Reader\Reader_sl.exe”
O4 – HKLM\..\Run: [ACUMon] “C:\Program Files\Cisco Systems\Aironet Client Monitor\ACUMon.Exe” -a
O4 – HKLM\..\Run: [ISUSPM Startup] C:\PROGRA~1\COMMON~1\INSTAL~1\UPDATE~1\ISUSPM.exe -startup
O4 – HKLM\..\Run: [ISUSScheduler] “C:\Program Files\Common Files\InstallShield\UpdateService\issch.exe” -start
O4 – HKLM\..\Run: [SunJavaUpdateSched] “C:\Program Files\Common Files\Java\Java Update\jusched.exe”
O4 – HKLM\..\Run: [Zone Labs Client] “C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe”
O4 – HKLM\..\Run: [avast!] C:\PROGRA~1\ALWILS~1\Avast4\ashDisp.exe
O4 – HKLM\..\Run: [RegistryMechanic] C:\Program Files\Registry Mechanic\RegMech.exe /QS
O4 – HKCU\..\Run: [Messenger (Yahoo!)] “C:\PROGRA~1\Yahoo!\MESSEN~1\YahooMessenger.exe” -quiet
O4 – HKCU\..\Run: [Spyware Doctor] “C:\Program Files\Spyware Doctor\swdoctor.exe” /Q
O4 – Global Startup: Adobe Gamma Loader.lnk = C:\Program Files\Common Files\Adobe\Calibration\Adobe Gamma Loader.exe
O8 – Extra context menu item: E&xport to Microsoft Excel – res://C:\PROGRA~1\MICROS~2\OFFICE11\EXCEL.EXE/3000
O9 – Extra button: Spyware Doctor – {2D663D1A-8670-49D9-A1A5-4C56B4E14E84} – C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O17 – HKLM\System\CCS\Services\Tcpip\..\{2B7C04D2-0898-43A3-B374-B7AFA580EA23}: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CCS\Services\Tcpip\..\{7A5AF047-9CE4-40A2-8954-F491000044CC}: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CS1\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CS2\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CS3\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CCS\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O23 – Service: avast! iAVS4 Control Service (aswUpdSv) – ALWIL Software – C:\Program Files\Alwil Software\Avast4\aswUpdSv.exe
O23 – Service: Ati HotKey Poller – ATI Technologies Inc. – C:\WINNT\system32\Ati2evxx.exe
O23 – Service: avast! Antivirus – ALWIL Software – C:\Program Files\Alwil Software\Avast4\ashServ.exe
O23 – Service: avast! Mail Scanner – ALWIL Software – C:\Program Files\Alwil Software\Avast4\ashMaiSv.exe
O23 – Service: avast! Web Scanner – ALWIL Software – C:\Program Files\Alwil Software\Avast4\ashWebSv.exe
O23 – Service: Logical Disk Manager Administrative Service (dmadmin) – VERITAS Software Corp. – C:\WINNT\System32\dmadmin.exe
O23 – Service: ThinkPad PM Service (IBMPMSVC) – Unknown owner – C:\WINNT\system32\ibmpmsvc.exe
O23 – Service: Java Quick Starter (JavaQuickStarterService) – Sun Microsystems, Inc. – C:\Program Files\Java\jre6\bin\jqs.exe
O23 – Service: LexBce Server (LexBceS) – Lexmark International, Inc. – C:\WINNT\system32\LEXBCES.EXE
O23 – Service: TrueVector Internet Monitor (vsmon) – Zone Labs, LLC – C:\WINNT\system32\ZoneLabs\vsmon.exe
O23 – Service: Yahoo! Updater (YahooAUService) – Yahoo! Inc. – C:\Program Files\Yahoo!\SoftwareUpdate\YahooAUService.exe
—
End of file – 7215 bytes
amazing… Thanks a lot.. I had lost hope for recovering my Laptop.
Thanks a ton..
🙂
Tony, follow the steps below.
Run HijackThis. Click “Do a system scan only” button.
Now select the following entries by placing a tick in the left hand check box, if still present:
O17 – HKLM\System\CCS\Services\Tcpip\..\{2B7C04D2-0898-43A3-B374-B7AFA580EA23}: NameServer = 93.188.163.113,93.188.161.83O17 – HKLM\System\CCS\Services\Tcpip\..\{7A5AF047-9CE4-40A2-8954-F491000044CC}: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CS1\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CS2\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CS3\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
O17 – HKLM\System\CCS\Services\Tcpip\Parameters: NameServer = 93.188.163.113,93.188.161.83
Once you have selected all entries, close all running programs then click once on the “fix checked” button.
Click Start, Run, type
cmdand click OK.In the command prompt type in
ipconfig /flushdnsand then press ENTER (notice the space after ipconfig).Close the command prompt window.
Reboot your computer.
Then download, update and run Malwarebytes Anti-malware. Perform a scan.
Thank you thank you Nick! Your solution worked for me!
“Very simple fix… Go into safe mode with command prompt and type the following:
%systemroot%\system32\restore\rstrui.exe
I tried all the other things and nothing worked. I did this and restored my computer to 3 days prior and it works perfectly!
Hope this helps!!!!”
thanks heaps for your advice.i found that the fix file worked perfectly.back to normal after a week,phew!!
I do not manage to open the downloaded file, I doubleclick but nothing happens. I did the TDSS killer but he found no infection.
If I run the inf file and then reboot, the virus does not bother as long as I do not open internet explorer. As soon as I open IE the virus is there again.
What to do?
Dr.Robert, run fix.inf once again, then click Start, Run, type regedit and press Enter.
Registry editor opens.
Navigate in the left panel to HKEY_LOCAL_MACHINE \ SOFTWARE \ Clients \ StartMenuInternet \ IEXPLORE.EXE \ shell \ open \ command
I the right part of window click twice to “@”. You will see a screen with the contents like below: “C:\Documents and Settings\user\Local Settings\Application Data\av.exe” /START “C:\Program Files\Internet Explorer\iexplore.exe”
Remove left part, leave only “C:\Program Files\Internet Explorer\iexplore.exe”.
Reboot your PC and try Internet Explorer.
i Downloaded MalwareBytes Anti-malware and ran it. it restarted and said “some programs can not be removed” and i still have virus protector popping up even more. PLEASE HELP!
cannot load after entering safemode with command promt
sean, open a new topic in our Spyware removal forum. I will check your PC.
don, in the Safe mode you need only fix your Windows registry, then reboot in Normal mode and download Malwarebytes.
hello, please help asap i installed the programme and run it through promote word screen it detected infected files and deleted all of them. but yet still when i got told to restart laptop i did so. and the ‘virus protector’ still did get removed of my system. as im turing the laptop on the virus protector is not allowing me to access any files and is running scan on its own straight away. please give me a solution to do.
Mariam, after following to the above steps you still can`t boot your PC in Normal mode ?