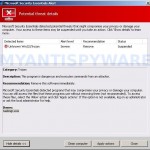
 If you are seeing a Microsoft Security Essentials Alert box that states that Unknown Win32/Trojan was detected on your computer, then you have become infected with a trojan FakeAlert that uses this fake alert to trick you into thinking your PC is infected so that you will then install and purchase one of 5 rogue antivirus programs: Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard.
If you are seeing a Microsoft Security Essentials Alert box that states that Unknown Win32/Trojan was detected on your computer, then you have become infected with a trojan FakeAlert that uses this fake alert to trick you into thinking your PC is infected so that you will then install and purchase one of 5 rogue antivirus programs: Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard.
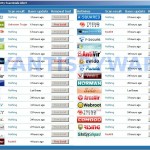
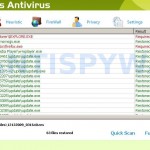
The “Microsoft Security Essentials Alert” trojan come from fake malware online scanners or malicious websites that ask users to download an Adobe Flash Player update or player needed to view a movie online. Once running, it will display a fake alert that looks like an alert from legitimate Windows Microsoft Security Essentials. As already stated above, it will state that your computer is infected with a trojan that have Severe level and then prompt you to clean your PC by clicking on the Clean Computer or Apply actions buttons. When you click on these buttons, it will say that unable to cure your computer and then prompt your to perform an online scan. During the scan, it will list various antivirus programs and only 5 of which find that your computer is infected with a trojan or rootkit. These 5: Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard. The “Microsoft Security Essentials Alert” trojan does it to force you into clicking to the Free Install button to install a rogue antivirus from the list above onto your PC. All of these rogues are perfectly similar to each other, just have different names and GUI interfaces.
When a selected rogue antivirus is installed, it will reboot your computer to complete the installation process. Once Windows loaded, it will simulate a system scan and detect a lot of infected files. When the scan is complete, the rogue will report that was able to clean the majority of infected files, but was not able to cure a few important Windows files, such as firefox.exe, taskmgr.exe, iexplore.exe and offer to purchase its full version to clean them.
While is running, the “Microsoft Security Essentials Alert” trojan can block the Windows Task Manager, legitimate Windows applications, as well as display numerous fake security warnings and alerts. Some of the alerts:
Microsoft Security Essentials Alert
Microsoft Security Essentials detected potential threats that might compromise your privacy or damage your
computer. Your access to these items may be suspender until you take an action.
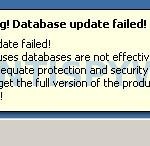
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can`t
guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update
the database!
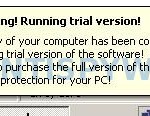
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software
and get full protection for your PC!
Like false scan results above, all of these alerts and warnings are just a fake and you can safely ignore them.
As you can see, Microsoft Security Essentials Alert trojan wants to trick you into thinking your computer is infected with a lot of viruses and malware as a method to force to install and next purchase one of Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard. Do not be fooled into buying it! Instead of doing so, follow the removal guidelines below in order to remove fake Microsoft Security Essentials Alert and the related rogues from your computer for free.
More screen shoots of Microsoft Security Essentials Alert
Symptoms in a HijackThis Log
O4 – HKCU\..\Run: [tmp] C:\Documents and Settings\comp\Application Data\defender.exe
O4 – HKCU\..\RunOnce: [SelfdelNT] cmd /C del “C:\Documents and Settings\username\Desktop\111\exe.exe”
Use the following instructions to remove Microsoft Security Essentials Alert
Click Start, Run. Type %AppData% and press Enter. It will open the contents of Application Data folder (for Windows XP) or the contents of Roaming folder (for Windows Vista, Windows 7). Rename defender to defender1, antispy to antispy1, hotfix to hotfix1, tmp to tmp1. This is normal if some files listed above does not exist. Next, reboot your computer.
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
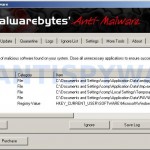
Once the program has loaded you will see window similar to the one below.
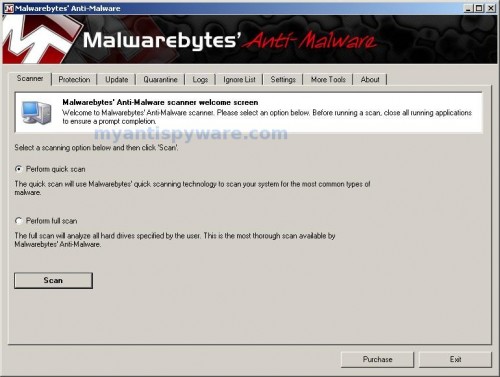
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer for Microsoft Security Essentials Alert infection. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
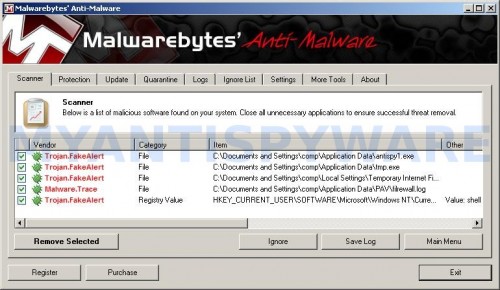
Malwarebytes Anti-malware, list of infected items
Make sure that everything is checked, and click Remove Selected for start Microsoft Security Essentials Alert removal process. When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
Microsoft Security Essentials Alert removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Microsoft Security Essentials Alert creates the following files and folders
%UserProfile%\Application Data\PAV\
%UserProfile%\Application Data\antispy.exe
%UserProfile%\Application Data\defender.exe
%UserProfile%\Application Data\tmp.exe
Microsoft Security Essentials Alert creates the following registry keys and values
HKEY_CURRENT_USER\Software\PAV
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings | “WarnonBadCertRecving” = “0”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings | “WarnOnPostRedirect” = “0”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | “tmp”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce | “SelfdelNT”
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon | “Shell” = “%UserProfile%\Application Data\antispy.exe”













Meghan,
1. check proxy settings of Internet Explorer. Reset them if need be (run Internet Explorer, Click Tools -> Internet Options. Select Connections Tab and click to Lan Settings button. Uncheck “Use a proxy server” box. Click OK and click OK again).
2-3. download Malwarebytes to another PC, then move this file to your infected computer using a flash/cd disk. Run it and perform a scan. Remove what it found.
Thank you for all the help.
Got the virus yesterday while surfing with Firefox. I am running Vista with Windows Defender supposodely on the watch.
Did not run scan or anything else on virus screen but I must have pushed something because I had no internet, taskmanager etc on reboot.
I ran windows defender full scan, and MS removal tool (search MRT.exe) full scan and did not cure.
Searched for %AppData% and found in “roaming” directory hotfix.exe and jsdfgs.bat
renamed them hotfix8.exe and jsdfgs8.bat
rebooted and everything worked
deleted hotfix8.exe and jsdfgs8.bat
Have not downloaded malwarebytes but everything is seeming ok now.
I’ve tried everything suggested and am having no luck. I can’t perform the directions prior to running Malwarebytes. I’ve tried searching and can’t find those files anywhere on my computer. I’ve run Malwarebytes anyways and it picked up 14 infected objects, however, the alert continues to pop up.
Jason, probably your PC is infected with a new variant of the malware. Start a new topic in our Spyware removal forum. I will help you to remove this malware.
Followed all instructions & it did the trick – thanks!
when i tried to run the %AppData% but did not find any of the files. I also tried to search (using MS search)with no luck. Can I just run the MBAM without renaming any of the files ??
Sam, yes of course, you can run MBAM. Remove all, what it found.
Trying to remove fake spyware per instruct on this site downloaded malware and got kicked off
when i log on in safe mode … black screen, normal mode … XPS on blackgroud ( which is desktop backgroup i think)
worm.win32.netsky detected on machine is warning message
can’t do anything on that computer….using desktop to find HELPPPPPPP
Thanks so much, the malware program worked perfectly
kim, what is XPS ?
i have two users on my laptop, and the only one was attacked by this fake alert. The administrator is fine and i can access the internet with it, but the probem is that the rogue (which i thankfully didn’t pay for) is on the other user. And on that user, if i click on internet explorer or chrome, a message comes up saying that those programs shut down because they were a risk. How can i download the malwarebytes onto the infected user if i cannot even open any sort of internet explorer?
This ‘microsoft security essentials’ just duped me, the warning popped up while browsing failblog of all places – I thought it was a genuine alert until it forced the reboot and killed the desktop, I tried killing the ‘anti spyware’ program with ctrl+alt+del, when that wouldn’t even come up I knew I’d been had.
Very clever software – thanks to a quick google I found the advice on this page, I used the library/explorer window that popped up at the end of the scan when selecting ‘continue without protection’, I found hotfix in my users/user/appdata folder and renamed it hotfix1 and did a reboot – BOOM! Computer is alive again!
I downloaded the free anti-malware and it’s scanning as I write this – already identified 3 infected files! Thank you to the author so much for sharing your knowledge!
What is the best way to get the word out to the anti-virus companies about this? Antivir didn’t even notice it…
Just to clarify – this virus totally paralyzed my computer except for the library/file explorer function at the end of it’s mock scan. If it hadn’t had that, I would have been very stuck.
I googled this page using my iphone.
spoke too soon. came right back
I changed “hotfix.exe” in %appdata% and followed the rest of the instructions and it worked perfectly….thx
Found a loop-hole. In windows explorer, make a copy of cmd.exe and rename it (ie:Hello.exe) it will run!
Used it to run Pstools
This was so easy. I spent days wanting to hunt down the creators of this awfull malware. Malwarebytes saved the day and my santity!
to be able to get control of my computer, I restarted in safe mode and restored my computer to a date a couple of weeks ago. That got rid of the alert window. I will go ahead and search for the hotfix file so I can rename it as well.
Thanks a bunch. Worked perfectly just by following the instructions.
Just want to say thanks to everyone. I had to look at the site on my iPhone while I removed it on my computer, because I could not run IE. Anyway, renaming and removing hotfile worked. Thanks again
Thx a lot! I reboot my XP in safe mode with networking then launched taskmgr to kill trojan – I had to do several times before succeeding; downloaded then ran both TDSSKiller and MalwareBytes fixed my problem.
MalwareBytes log lists these infections on my XP:
Registry Keys Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{f03c6151-5d0e-4675-9e4b-01910a278c1f} (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\shell (Trojan.Agent) -> Quarantined and deleted successfully.
Files Infected:
C:\Documents and Settings\Administrator\Application Data\hotfix.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\END (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{8D290BB5-E59C-462B-A0EE-E8949A1E4344}\RP938\A0117738.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
I had a particularly bad time with this virus because it would cause a “blue screen of death” within just a few seconds after first appearing on my desktop. The computer would then go through a crash dump and reboot. This same thing was happening over and over and over again.
Here’s how I solved it:
When the system started to reboot, I pushed F8 and brought up the Advanced Options Menu. I selected the first option, “Repair”, which brought up another screen that allowed me to select an option to run System Restore.
I ran it an restore the system to a two day old pre-virus configuration. Keep in mind that when running in this mode, System Restore takes a while.
That worked for me. I could then get in there and run Malware.
Simple but took me three hours to figure out.
Good luck!
Steven
My mother’s PC got infected with the “hotfix.exe” variant of this. AVG had quarantined that file, but did not find the rootkit that it installed.
Malwarebytes found all but one infected file, and the popups were continuing in Firefox (and the system was generally very slow). Ran TDSSKiller, which found and removed one additional infected file (C:\WINDOWS\system32\DRIVERS\mouclass.sys), and that seems to have finally fixed the problem.
Many thanks to this site and others who help solve these problems, and a POX on the malware developers who make this crap!
I just had this problem as well. I was stupid enough to click Clean Computer, but the moment I saw that selection of virus software I knew something was up… and my brain caught up and asked “how is it possible a Microsoft piece of security caught something that slipped through Symantec’s net?… not in this dimension!!!”
It blocked my Firefox, a firefox plugincontainer file, and WinAmp.exe files.
I rebooted and had no taskbar, just the default file explorer popped up on an empty desktrop (which I almost never use as I prefer XYplorer). Behaved the exact same way in Safe Mode.
After looking at the Task Manager I spotted a hotfix.exe…. you have to kill that before your renaming of it has any effect. THEN you can delete it.
For me, I found the hotfix entry in the Winlogon registry thread BUT there is one thing I’m still uncertain of. I don’t ever remember seeing a symbol in the registry before:
HKEY_CURRENT_USER\ __
Where the “__” is, there is a symbol for the female gender. It only has one entry, REG_SZ, and its value is is “not set”.
I also noticed a BAT file above the hotfix.exe in my Roaming folder… that pointed to the original trojan that installer that was still sitting in the Local/TEMP folder.
I’m going to take a chance and delete that female gender symbol entry (I can’t seem to C&P the character).
Thank you very much! Worked like a charm.
I can’t delete hotfix.exe or rename it to hotfix.bak, can anyone help me? And this virus won’t let me open my taskmanager or open any of my browser.
I’ve actually had this one twice now at work (Forefront doesn’t recognize it at all). It came through malicious banner ads and opened Windows Media Player for some reason before giving me the popups. I keep Malware Bytes and a program called “rkill” on a flash drive for this very reason — most anti-virus programs aren’t very good at blocking the fake anti-virus programs!
Hi I also had this pain, after reading many posts and considering the software option this is how I deleted it. I did not use any of the down load SW options
Searched for the hotfix.exe by the date
Created a new user ID with admin rights (took admin rights off the main user)
closed all users and opened the new user, repeated the search for hotfix, here I was able to delete and then empty the recycle box. Problem gone. Thanks to all who posted before
I got hit with this trojan yesterday. It blocked all my browsers. And stopped me opening task manager. I managed to use another program to stop the hotfix problem however it was running under the guise of wses.exe and not hotfix.exe. the dat file was asdsada.dat. I had Malwarebytes already installed just updated it and ran it. Points to note the same time I got hit I had a wwwerd32.exe installed that windowsdefender stopped and i deleted. I also a task bar message saying \blocked startup programs\ the blocked program was malwarebytes. Might be worth while for them to stay one step ahead of this.