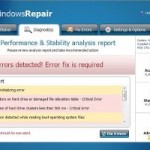
 Windows Repair is a malicious program that pretends to be a computer defragmenter and system analysis software. It hijacks your computer, blocks Windows legitimate applications from running, presents various fake critical errors alerts that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Do not pay for the bogus software! Simply ignore all that it will display you and remove Windows Recovery from your computer as quickly as possible!
Windows Repair is a malicious program that pretends to be a computer defragmenter and system analysis software. It hijacks your computer, blocks Windows legitimate applications from running, presents various fake critical errors alerts that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Do not pay for the bogus software! Simply ignore all that it will display you and remove Windows Recovery from your computer as quickly as possible!
Windows Repair from same family of malware as Windows Recovery, Windows Diagnostic, Windows Disk, etc which has already caused much damage to many computes. It is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software. Moreover, the scammers may also distribute this malware on Twitter, My Space, Facebook, and other social networks. Remember, “Windows Repair” name is only a trick. Cyber criminals uses legitimate names in order to get trust from computer users as most of them do not pay attention to what they download from the Internet. Thus, please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC.
When WindowsRepair is installed, it will state that your computer has some critical problems. It will imitate a scan computer`s hard disks, Windows registry and computer memory for errors. The rogue will report that “Read time of hard drive clusters less than 500 ms”, “32% of HDD space is unreadable”, “Bad sectors on hard drive or damaged file allocation table”, etc. The scan look legitimate, but you should never trust anything that the fake diagnostic tool will display you. Remember, all of these errors are a fake! So, simply ignore the false scan results.
Windows Repair will block legitimate Windows applications on your computer and won’t let you download anything from the Internet. Last, but not least, the rogue will display numerous fake warnings and nag screens. Some of the warnings are:
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Windows – No Disk
Exception Processing Message 0×0000013
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Of course, all of these warnings are a fake. This is an attempt to make you think your computer in danger. Like false scan results you can safely ignore them.
As you can see, WindowsRepair is a totally scam, which created with one purpose to scare you into purchasing so-called “full” version of the program. Most important do not purchase it! Please use the removal guide below in order to remove Windows Repair and any associated malware from your computer for free. If you have already purchase the program, contact your credit card company and tell them what has happened.
Automated Removal Instructions for Windows Repair
Step 1. Reboot your computer in Safe mode with networking
Restart your computer.
After hearing your computer beep once during startup, start pressing the F8 key on your keyboard. On a computer that is configured for booting to multiple operating systems, you can press the F8 key when the Boot Menu appears.
Instead of Windows loading as normal, Windows Advanced Options menu appears similar to the one below.
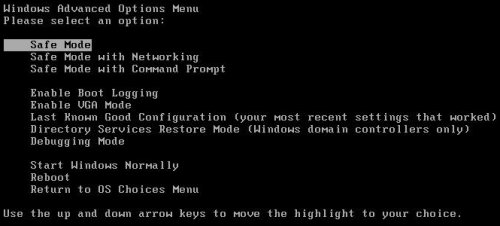
Windows Advanced Options menu
When the Windows Advanced Options menu appears, select Safe mode with networking and then press ENTER.
Step 2. Stop Windows Repair from running
Download HijackThis from here. Run HijackThis and click Scan button to perform a system scan. Place a checkmark against each of lines:
O4 – HKCU\..\Run: [{RANDOM}.exe] %CommonAppData%\{RANDOM}.exe
O4 – HKCU\..\Run: [{RANDOM}] %CommonAppData%\{RANDOM}.exe
Example:
O4 – HKCU\..\Run: [CvdCEPoYRb.exe] C:\DOCUME~1\ALLUSE~1\APPLIC~1\CvdCEPoYRb.exe
O4 – HKCU\..\Run: [SaMFLunm] C:\DOCUME~1\ALLUSE~1\APPLIC~1\SaMFLunm.exe
O4 – HKCU\..\Run: [SaMFLunm] C:\ProgramData\SaMFLunm.exe
Note: list of infected items may be different. Template of the malicious entries:
Variant 1: O4 – HKCU\..\Run: [{random string}] %CommonAppData%\{random string}.exe;
Variant 2: O4 – HKCU\..\Run: [{random string}.exe] %CommonAppData%\{random string}.exe;
%CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista).
If you unsure, then check it in Google. Skip this step, if you does not find any malicious lines.
Place a checkmark against each of them. Once you have selected all entries, close all running programs then click once on the “fix checked” button. Close HijackThis.
Step 3. Clean temp folder
WindowsRepair may store its files in Windows temp folder. You need to clean the folder manually or automatically using ATF-Cleaner (the program is used to cleanout temporary files & temp areas used by internet browsers).
Please download ATF Cleaner by Atribune from here, saving it to your desktop. Start ATF-Cleaner.exe to run the program.
Under Main choose: Select All and click the Empty Selected button.
Step 4. Remove Windows Repair associated malware
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
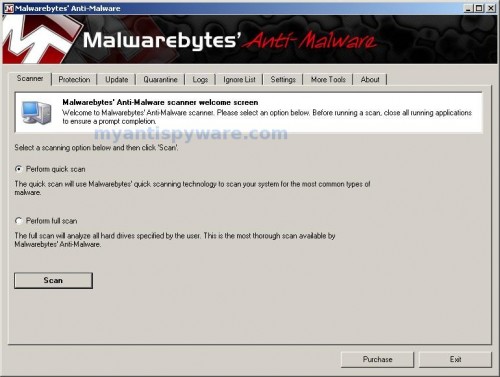
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer for Windows Repair infection. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
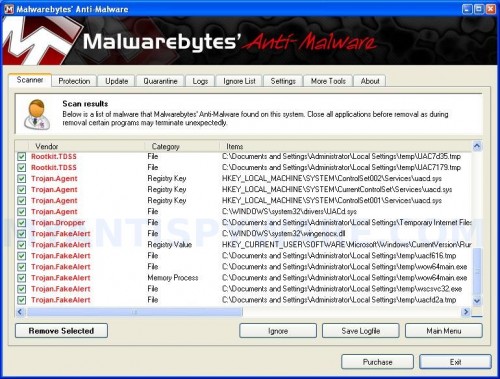
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove Windows Repair. MalwareBytes Anti-malware will now remove all of associated WindowsRepair files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Windows Repair removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Windows Repair creates the following files and folders
%UserProfile%\Desktop\Windows Repair.lnk
%UserProfile%\Start Menu\Programs\Windows Repair\Windows Repair.lnk
%UserProfile%\Start Menu\Programs\Windows Repair\Uninstall Windows Repair.lnk
%CommonAppData%\{RANDOM}.exe
%CommonAppData%\{RANDOM}
%CommonAppData%\{RANDOM}.dat
Note: %CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista)
Windows Repair creates the following registry keys and values
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | {RANDOM}
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | {RANDOM}.exe










Hi,
I have this exact virus right now on my computer…. It’s currently not running but when I go to my computer and click on C drive its just empty and when I hit start and all programs it also says empty.
I tried booting into safemode with networking and as soon as it starts up in the desktop it just shuts down but on regular boot it stay on.
What can I do????? Please help!!!!! 🙁
Martin, you hardisk is ok. Try the following:
If you using Windows 7/Vista:
click Start, type in Search:
C:\C:\ProgramData
Press Enter. It will open a contents of ProgramData. Locate randomly named files (CvdCEPoYRb.exe, for example) and rename them. Reboot your PC. Now try to download and run Malwarebytes.
Patrik,
I have the same situation as Martin. I’m running XP Pro SP2. I erased what I could find of Windows Repair filed throughout the C deive. Downloaded and updated Malwarebytes’ and ran in safe mode. No avail. Still no visibility to my docs, the program list or most of the desk top icons. must be a new malware. caught it Mar 26, Also ran AVG, and 3 other virus scanners. HELP>>>!!!???
in your search or run bar type; regedit run that then go hkey_current_user, software, microsoft, windows, current version, explorer, advanced then right click hidden and then modify change the 0 to a 1.
Hey patrik thanks for that it really helped but now I got rid of the malware but at startup I get a popup that says “Catalyst control center error. -Host application has stopped working” so I click on find a solution and close application but it does it all the time I reboot my computer, how can I fix that or what seems to be the problem?? And also I’m trying to uninstall my recent antivirus software to install a new one but it won’t let me it gives me an error saying – unable to uninstall security software- ” A serious operating system error has stopped the program. Please restart your computer before trying again”…
Can u help me out? Is this something caused by the malware???
Thanks,
Jeff/Patrik
The malware hides the folders on your c:\ drive. In windows explorer select “show hidden folders” and they will all appear. Then select all the folders and the folders properties, untick the hidden option, your folders, icons, programs etc should then return.
Thanks Wattie!!
Really cool,
One last item. Still can’t see the any items in the Start, Programs menu nor the quick start items on the lower left corner. Any thoughts??
Hi Guys:
My Computer is infected with this virus,
I tried each of the steps but the problem still exists,does any of you know a place that fixes this virus?
Wow, this virus or spyware is spreading so fast!
Jonny…you are the man….nice and simple, worked like a charm
Gents, the mail ware bytes step got rid of it for me. Many thanks for this. I too could not see any of my files in Vista, but for me I went into the “USERS” folders properties and un checked read only from blue square back to white. It took a while to load all folders back in but it did work. I had to do this for other folders as well. Keep it up Patrik
Hi,
My computer is also infected by the Windows Repair virus. I’m currently on Safe Mode with Networking as stated on Step 2 but after running HijackThis I’m not really sure if I should place a checkmark against each line or only the malicious ones (dunno how to recognize those) – I dont want to delete any important stuff. Can someone please help?
Many thanks – below is the logfile:
Logfile of Trend Micro HijackThis v2.0.4
Scan saved at 16:29:19, on 31/03/2011
Platform: Windows Vista SP2 (WinNT 6.00.1906)
MSIE: Internet Explorer v8.00 (8.00.6001.19019)
Boot mode: Safe mode with network support
Running processes:
C:\Windows\Explorer.EXE
C:\Windows\helppane.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Users\Lee & Steph\Desktop\HiJackThis.exe
R1 – HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.skybroadband.com
R1 – HKCU\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 – HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://uk.msn.com/?ocid=getmsn
R1 – HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://en.uk.acer.yahoo.com
R1 – HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 – HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 – HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://en.uk.acer.yahoo.com
R0 – HKLM\Software\Microsoft\Internet Explorer\Search,SearchAssistant =
R0 – HKLM\Software\Microsoft\Internet Explorer\Search,CustomizeSearch =
R1 – HKCU\Software\Microsoft\Internet Explorer\Main,Window Title = Internet Explorer Provided By Sky Broadband
R1 – HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyOverride = *.local
R0 – HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName =
O1 – Hosts: ::1 localhost
O2 – BHO: (no name) – {02478D38-C3F9-4efb-9B51-7695ECA05670} – (no file)
O2 – BHO: Adobe PDF Reader Link Helper – {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} – C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
O2 – BHO: WormRadar.com IESiteBlocker.NavFilter – {3CA2F312-6F6E-4B53-A66E-4E65E497C8C0} – C:\Program Files\AVG\AVG8\avgssie.dll (file missing)
O2 – BHO: Windows Live ID Sign-in Helper – {9030D464-4C02-4ABF-8ECC-5164760863C6} – C:\Program Files\Common Files\Microsoft Shared\Windows Live\WindowsLiveLogin.dll
O2 – BHO: Windows Live Messenger Companion Helper – {9FDDE16B-836F-4806-AB1F-1455CBEFF289} – C:\Program Files\Windows Live\Companion\companioncore.dll
O2 – BHO: Google Toolbar Helper – {AA58ED58-01DD-4d91-8333-CF10577473F7} – C:\Program Files\Google\Google Toolbar\GoogleToolbar_32.dll
O2 – BHO: SkypeIEPluginBHO – {AE805869-2E5C-4ED4-8F7B-F1F7851A4497} – C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll
O2 – BHO: Google Toolbar Notifier BHO – {AF69DE43-7D58-4638-B6FA-CE66B5AD205D} – C:\Program Files\Google\GoogleToolbarNotifier\5.6.6209.1142\swg.dll
O2 – BHO: Java(tm) Plug-In 2 SSV Helper – {DBC80044-A445-435b-BC74-9C25C1C588A9} – C:\Program Files\Java\jre6\bin\jp2ssv.dll
O3 – Toolbar: Acer eDataSecurity Management – {5CBE3B7C-1E47-477e-A7DD-396DB0476E29} – C:\Program Files\Acer\Empowering Technology\eDataSecurity\x86\eDStoolbar.dll
O3 – Toolbar: (no name) – {CCC7A320-B3CA-4199-B1A6-9F516DD69829} – (no file)
O3 – Toolbar: Google Toolbar – {2318C2B1-4965-11d4-9B18-009027A5CD4F} – C:\Program Files\Google\Google Toolbar\GoogleToolbar_32.dll
O4 – HKLM\..\Run: [Windows Defender] %ProgramFiles%\Windows Defender\MSASCui.exe -hide
O4 – HKLM\..\Run: [RtHDVCpl] RtHDVCpl.exe
O4 – HKLM\..\Run: [Acer Empowering Technology Monitor] C:\Program Files\Acer\Empowering Technology\SysMonitor.exe
O4 – HKLM\..\Run: [EmpoweringTechnology] C:\Program Files\Acer\Empowering Technology\Framework.Launcher.exe boot
O4 – HKLM\..\Run: [eDataSecurity Loader] C:\Program Files\Acer\Empowering Technology\eDataSecurity\x86\eDSloader.exe
O4 – HKLM\..\Run: [PCMMediaSharing] C:\Program Files\Acer Arcade Live\Acer HomeMedia Connect\Kernel\DMS\PCMMediaSharing.exe
O4 – HKLM\..\Run: [Adobe Reader Speed Launcher] “C:\Program Files\Adobe\Reader 8.0\Reader\Reader_sl.exe”
O4 – HKLM\..\Run: [BkupTray] “C:\Program Files\NewTech Infosystems\NTI Backup Now 5\BkupTray.exe”
O4 – HKLM\..\Run: [Google Desktop Search] “C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe” /startup
O4 – HKLM\..\Run: [Skytel] Skytel.exe
O4 – HKLM\..\Run: [kdx] “C:\Program Files\Kontiki\KHost.exe” -all
O4 – HKLM\..\Run: [PlayMovie] “C:\Program Files\Acer Arcade Live\Acer PlayMovie\PMVService.exe”
O4 – HKLM\..\Run: [QuickTime Task] “C:\Program Files\QuickTime\QTTask.exe” -atboottime
O4 – HKLM\..\Run: [iTunesHelper] “C:\Program Files\iTunes\iTunesHelper.exe”
O4 – HKCU\..\Run: [msnmsgr] “C:\Program Files\Windows Live\Messenger\msnmsgr.exe” /background
O4 – HKCU\..\Run: [SUPERAntiSpyware] C:\Program Files\SUPERAntiSpyware\SUPERAntiSpyware.exe
O4 – HKCU\..\Run: [TomTomHOME.exe] “C:\Program Files\TomTom HOME\TomTomHOMERunner.exe”
O4 – HKCU\..\Run: [swg] “C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe”
O4 – HKCU\..\Run: [WMPNSCFG] C:\Program Files\Windows Media Player\WMPNSCFG.exe
O4 – HKCU\..\Run: [kdx] C:\Program Files\Kontiki\KHost.exe -all
O4 – HKCU\..\Run: [vpmeah] RUNDLL32.EXE C:\Users\LEE&ST~1\AppData\Local\Temp\mslwaukm.dll,w
O4 – HKCU\..\Run: [PXXpEKijomnAXjk] C:\ProgramData\PXXpEKijomnAXjk.exe
O4 – HKUS\S-1-5-19\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User ‘LOCAL SERVICE’)
O4 – HKUS\S-1-5-19\..\Run: [WindowsWelcomeCenter] rundll32.exe oobefldr.dll,ShowWelcomeCenter (User ‘LOCAL SERVICE’)
O4 – HKUS\S-1-5-20\..\Run: [Sidebar] %ProgramFiles%\Windows Sidebar\Sidebar.exe /detectMem (User ‘NETWORK SERVICE’)
O4 – Global Startup: hpoddt01.exe.lnk = ?
O4 – Global Startup: NETGEAR WPN111 Smart Wizard.lnk = ?
O4 – Global Startup: Nikon Monitor.lnk = C:\Program Files\Common Files\Nikon\Monitor\NkMonitor.exe
O8 – Extra context menu item: E&xport to Microsoft Excel – res://C:\PROGRA~1\MICROS~2\Office12\EXCEL.EXE/3000
O8 – Extra context menu item: Google Sidewiki… – res://C:\Program Files\Google\Google Toolbar\Component\GoogleToolbarDynamic_mui_en_D183CA64F05FDD98.dll/cmsidewiki.html
O9 – Extra button: @C:\Program Files\Windows Live\Companion\companionlang.dll,-600 – {0000036B-C524-4050-81A0-243669A86B9F} – C:\Program Files\Windows Live\Companion\companioncore.dll
O9 – Extra button: Sky – {08E730A4-FB02-45BD-A900-01E4AD8016F6} – http://www.skybroadband.com (file missing)
O9 – Extra button: @C:\Program Files\Windows Live\Writer\WindowsLiveWriterShortcuts.dll,-1004 – {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} – C:\Program Files\Windows Live\Writer\WriterBrowserExtension.dll
O9 – Extra ‘Tools’ menuitem: @C:\Program Files\Windows Live\Writer\WindowsLiveWriterShortcuts.dll,-1003 – {219C3416-8CB2-491a-A3C7-D9FCDDC9D600} – C:\Program Files\Windows Live\Writer\WriterBrowserExtension.dll
O9 – Extra button: Send to OneNote – {2670000A-7350-4f3c-8081-5663EE0C6C49} – C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 – Extra ‘Tools’ menuitem: S&end to OneNote – {2670000A-7350-4f3c-8081-5663EE0C6C49} – C:\PROGRA~1\MICROS~2\Office12\ONBttnIE.dll
O9 – Extra button: Skype Plug-In – {898EA8C8-E7FF-479B-8935-AEC46303B9E5} – C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll
O9 – Extra ‘Tools’ menuitem: Skype Plug-In – {898EA8C8-E7FF-479B-8935-AEC46303B9E5} – C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll
O9 – Extra button: Research – {92780B25-18CC-41C8-B9BE-3C9C571A8263} – C:\PROGRA~1\MICROS~2\Office12\REFIEBAR.DLL
O10 – Unknown file in Winsock LSP: c:\windows\system32\nvlsp.dll
O10 – Unknown file in Winsock LSP: c:\windows\system32\nvlsp.dll
O10 – Unknown file in Winsock LSP: c:\windows\system32\nvlsp.dll
O10 – Unknown file in Winsock LSP: c:\windows\system32\nvlsp.dll
O16 – DPF: {0CCA191D-13A6-4E29-B746-314DEE697D83} (Facebook Photo Uploader 5 Control) – http://upload.facebook.com/controls/2008.10.10_v5.5.8/FacebookPhotoUploader5.cab
O16 – DPF: {4F1E5B1A-2A80-42CA-8532-2D05CB959537} (MSN Photo Upload Tool) – http://gfx1.hotmail.com/mail/w3/resources/VistaMSNPUpldfr-fr.cab
O16 – DPF: {8100D56A-5661-482C-BEE8-AFECE305D968} (Facebook Photo Uploader 5 Control) – http://upload.facebook.com/controls/2009.07.28_v5.5.8.1/FacebookPhotoUploader55.cab
O16 – DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) – http://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab
O16 – DPF: {E77F23EB-E7AB-4502-8F37-247DBAF1A147} (Windows Live Hotmail Photo Upload Tool) – http://gfx1.hotmail.com/mail/w4/pr01/photouploadcontrol/VistaMSNPUpldfr-fr.cab
O18 – Protocol: skype-ie-addon-data – {91774881-D725-4E58-B298-07617B9B86A8} – C:\Program Files\Skype\Toolbars\Internet Explorer\skypeieplugin.dll
O18 – Protocol: skype4com – {FFC8B962-9B40-4DFF-9458-1830C7DD7F5D} – C:\PROGRA~1\COMMON~1\Skype\SKYPE4~1.DLL
O18 – Protocol: wlpg – {E43EF6CD-A37A-4A9B-9E6F-83F89B8E6324} – C:\Program Files\Windows Live\Photo Gallery\AlbumDownloadProtocolHandler.dll
O20 – AppInit_DLLs: AVGRSSTX.DLL C:\PROGRA~1\GOOGLE\GOOGLE~1\GOEC62~1.DLL
O20 – Winlogon Notify: !SASWinLogon – C:\Program Files\SUPERAntiSpyware\SASWINLO.DLL
O22 – SharedTaskScheduler: Component Categories cache daemon – {8C7461EF-2B13-11d2-BE35-3078302C2030} – C:\Windows\system32\browseui.dll
O23 – Service: Acer HomeMedia Connect Service – CyberLink – C:\Program Files\Acer Arcade Live\Acer HomeMedia Connect\Kernel\DMS\CLMSServer.exe
O23 – Service: Apple Mobile Device – Apple Inc. – C:\Program Files\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe
O23 – Service: Bonjour Service – Apple Inc. – C:\Program Files\Bonjour\mDNSResponder.exe
O23 – Service: NTI Backup Now 5 Agent Service (BUNAgentSvc) – NewTech Infosystems, Inc. – C:\Program Files\NewTech Infosystems\NTI Backup Now 5\Client\Agentsvc.exe
O23 – Service: eDataSecurity Service – Egis Incorporated – C:\Program Files\Acer\Empowering Technology\eDataSecurity\x86\eDSService.exe
O23 – Service: Empowering Technology Service (ETService) – Unknown owner – C:\Program Files\Acer\Empowering Technology\Service\ETService.exe
O23 – Service: ForceWare Intelligent Application Manager (IAM) – Unknown owner – C:\Program Files\bin32\nSvcAppFlt.exe
O23 – Service: Google Desktop Manager 5.9.1005.12335 (GoogleDesktopManager-051210-111108) – Google – C:\Program Files\Google\Google Desktop Search\GoogleDesktop.exe
O23 – Service: Google Update Service (gupdate1c9cc9d5e423763) (gupdate1c9cc9d5e423763) – Google Inc. – C:\Program Files\Google\Update\GoogleUpdate.exe
O23 – Service: Google Software Updater (gusvc) – Google – C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 – Service: InstallDriver Table Manager (IDriverT) – Macrovision Corporation – C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 – Service: iPod Service – Apple Inc. – C:\Program Files\iPod\bin\iPodService.exe
O23 – Service: KService – Kontiki Inc. – C:\Program Files\Kontiki\KService.exe
O23 – Service: LightScribeService Direct Disc Labeling Service (LightScribeService) – Hewlett-Packard Company – C:\Program Files\Common Files\LightScribe\LSSrvc.exe
O23 – Service: McAfee Real-time Scanner (McShield) – Unknown owner – C:\PROGRA~1\McAfee\VIRUSS~1\mcshield.exe (file missing)
O23 – Service: McAfee SystemGuards (McSysmon) – Unknown owner – C:\PROGRA~1\McAfee\VIRUSS~1\mcsysmon.exe (file missing)
O23 – Service: ForceWare IP service (nSvcIp) – Unknown owner – C:\Program Files\bin32\nSvcIp.exe
O23 – Service: NTI Backup Now 5 Backup Service (NTIBackupSvc) – NewTech InfoSystems, Inc. – C:\Program Files\NewTech Infosystems\NTI Backup Now 5\BackupSvc.exe
O23 – Service: NTI Backup Now 5 Scheduler Service (NTISchedulerSvc) – Unknown owner – C:\Program Files\NewTech Infosystems\NTI Backup Now 5\SchedulerSvc.exe
O23 – Service: NVIDIA Display Driver Service (nvsvc) – NVIDIA Corporation – C:\Windows\system32\nvvsvc.exe
O23 – Service: Rapport Management Service (RapportMgmtService) – Trusteer Ltd. – C:\Program Files\Trusteer\Rapport\bin\RapportMgmtService.exe
O23 – Service: Cyberlink RichVideo Service(CRVS) (RichVideo) – Unknown owner – C:\Program Files\CyberLink\Shared Files\RichVideo.exe
O23 – Service: TomTomHOMEService – TomTom – C:\Program Files\TomTom HOME\TomTomHOMEService.exe
—
End of file – 12258 bytes
Sorry I’ve just read the rules on how to ask for help and created a new thread there http://myantispyware.com/forum/windows-repair-t4762.html thanks
I’m in no way a computers expert, if I follow these steps, will it be obvious to me that I’ve gotten rid of this virus?
Also, will this program delete the virus for free?
Please help =\
Martin, try reinstall video drivers (Catalyst control center) in Safe mode.
pirouz, ask for help in our Spyware removal forum.
These instuctions worked great. I did have to unhide the files and directories.
With one exception, the WindowsRepair Icon still appeared on my desktop after everything appeared normal again. I clicked on it and the bogus alerts started all over. I ran thru the instructions again but found no infections in Malwarebytes scanned list.
I found the directory where the EXE file was hiding (documents and setting\all users\application data) and deleted it and emptied the recycle bin.
Everything looks like it is back to normal but I’m afraid that Malwarebytes might need an upadate
Please comment
Steph, fix the following entries:
O4 – HKCU\..\Run: [vpmeah] RUNDLL32.EXE C:\Users\LEE&ST~1\AppData\Local\Temp\mslwaukm.dll,w
O4 – HKCU\..\Run: [PXXpEKijomnAXjk] C:\ProgramData\PXXpEKijomnAXjk.exe
College student, all programs that used to remove this malware are free and legitimate malware removal tools.
John, don`t worry about it. Try wait a few days, then update Malwarebytes and perform a fresh scan.
Guys, got the WIndows Repair virus a couple days ago – I’ve run through these steps and have gotten rid of my hidden files problem, but I’m still getting random audio of ads popping up and IE script error popups. When I click on a link in IE or firefox, it takes me to random advertisment sites as well, rather than the link. Here’s my Hijackthis log:
Running processes:
C:\WINDOWS\System32\smss.exe
C:\PROGRA~1\AVG\AVG10\avgchsvx.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\ehome\ehtray.exe
C:\WINDOWS\stsystra.exe
C:\Program Files\Intel\Intel Matrix Storage Manager\iaanotif.exe
C:\Program Files\Dell\Media Experience\DMXLauncher.exe
C:\WINDOWS\System32\DLA\DLACTRLW.EXE
C:\Program Files\AVG\AVG10\avgtray.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Digital Line Detect\DLG.exe
C:\Program Files\AVG\AVG10\Identity Protection\agent\bin\avgidsmonitor.exe
C:\PROGRA~1\COMMON~1\AOL\ACS\AOLacsd.exe
C:\Program Files\AVG\AVG10\avgwdsvc.exe
C:\WINDOWS\eHome\ehRecvr.exe
C:\WINDOWS\eHome\ehSched.exe
C:\Program Files\Intel\Intel Matrix Storage Manager\iaantmon.exe
C:\WINDOWS\system32\nvsvc32.exe
C:\WINDOWS\system32\PnkBstrA.exe
C:\Program Files\AVG\AVG10\Identity Protection\Agent\Bin\AVGIDSAgent.exe
C:\Program Files\AVG\AVG10\avgnsx.exe
C:\Program Files\AVG\AVG10\avgemcx.exe
C:\WINDOWS\system32\dllhost.exe
C:\WINDOWS\eHome\ehmsas.exe
C:\Documents and Settings\Taran Alexander\Application Data\mjusbsp\magicJack.exe
C:\PROGRA~1\AVG\AVG10\avgrsx.exe
C:\Program Files\AVG\AVG10\avgcsrvx.exe
C:\Program Files\Trend Micro\HiJackThis\HiJackThis.exe
R1 – HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.google.com/ig/dell?hl=en&client=dell-usuk&channel=us
R1 – HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 – HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 – HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 – HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R1 – HKLM\Software\Microsoft\Internet Explorer\Search,Default_Page_URL = http://www.google.com/ig/dell?hl=en&client=dell-usuk&channel=us
O2 – BHO: AcroIEHlprObj Class – {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} – C:\Program Files\Adobe\Acrobat 6.0\Reader\ActiveX\AcroIEHelper.dll
O2 – BHO: WormRadar.com IESiteBlocker.NavFilter – {3CA2F312-6F6E-4B53-A66E-4E65E497C8C0} – C:\Program Files\AVG\AVG10\avgssie.dll
O2 – BHO: DriveLetterAccess – {5CA3D70E-1895-11CF-8E15-001234567890} – C:\WINDOWS\System32\DLA\DLASHX_W.DLL
O2 – BHO: SSVHelper Class – {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} – C:\Program Files\Java\jre1.5.0_06\bin\ssv.dll
O2 – BHO: Browser Address Error Redirector – {CA6319C0-31B7-401E-A518-A07C3DB8F777} – C:\Program Files\BAE\BAE.dll
O4 – HKLM\..\Run: [ehTray] C:\WINDOWS\ehome\ehtray.exe
O4 – HKLM\..\Run: [SigmatelSysTrayApp] stsystra.exe
O4 – HKLM\..\Run: [IAAnotif] C:\Program Files\Intel\Intel Matrix Storage Manager\iaanotif.exe
O4 – HKLM\..\Run: [DMXLauncher] C:\Program Files\Dell\Media Experience\DMXLauncher.exe
O4 – HKLM\..\Run: [DLA] C:\WINDOWS\System32\DLA\DLACTRLW.EXE
O4 – HKLM\..\Run: [AVG_TRAY] C:\Program Files\AVG\AVG10\avgtray.exe
O4 – HKLM\..\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup
O4 – HKCU\..\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe
O4 – HKCU\..\Run: [cdloader] “C:\Documents and Settings\Taran Alexander\Application Data\mjusbsp\cdloader2.exe” MAGICJACK
O4 – HKCU\..\Run: [SUPERAntiSpyware] C:\Program Files\SUPERAntiSpyware\SUPERAntiSpyware.exe
O4 – Startup: MagicsilencePlugin.lnk = C:\Documents and Settings\Taran Alexander\Local Settings\Application Data\MagicsilencePlugin\MagicsilencePlugin.exe
O4 – Global Startup: Digital Line Detect.lnk = ?
O9 – Extra button: (no name) – {08B0E5C0-4FCB-11CF-AAA5-00401C608501} – C:\Program Files\Java\jre1.5.0_06\bin\ssv.dll
O9 – Extra ‘Tools’ menuitem: Sun Java Console – {08B0E5C0-4FCB-11CF-AAA5-00401C608501} – C:\Program Files\Java\jre1.5.0_06\bin\ssv.dll
O9 – Extra button: Real.com – {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} – C:\WINDOWS\system32\Shdocvw.dll
O9 – Extra button: (no name) – {e2e2dd38-d088-4134-82b7-f2ba38496583} – C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 – Extra ‘Tools’ menuitem: @xpsp3res.dll,-20001 – {e2e2dd38-d088-4134-82b7-f2ba38496583} – C:\WINDOWS\Network Diagnostic\xpnetdiag.exe
O9 – Extra button: Messenger – {FB5F1910-F110-11d2-BB9E-00C04F795683} – C:\Program Files\Messenger\msmsgs.exe
O9 – Extra ‘Tools’ menuitem: Windows Messenger – {FB5F1910-F110-11d2-BB9E-00C04F795683} – C:\Program Files\Messenger\msmsgs.exe
O18 – Protocol: linkscanner – {F274614C-63F8-47D5-A4D1-FBDDE494F8D1} – C:\Program Files\AVG\AVG10\avgpp.dll
O20 – Winlogon Notify: !SASWinLogon – C:\Program Files\SUPERAntiSpyware\SASWINLO.DLL
O22 – SharedTaskScheduler: Browseui preloader – {438755C2-A8BA-11D1-B96B-00A0C90312E1} – C:\WINDOWS\system32\browseui.dll
O22 – SharedTaskScheduler: Component Categories cache daemon – {8C7461EF-2B13-11d2-BE35-3078302C2030} – C:\WINDOWS\system32\browseui.dll
O23 – Service: AOL Connectivity Service (AOL ACS) – America Online, Inc. – C:\PROGRA~1\COMMON~1\AOL\ACS\AOLacsd.exe
O23 – Service: AVGIDSAgent – AVG Technologies CZ, s.r.o. – C:\Program Files\AVG\AVG10\Identity Protection\Agent\Bin\AVGIDSAgent.exe
O23 – Service: AVG WatchDog (avgwd) – AVG Technologies CZ, s.r.o. – C:\Program Files\AVG\AVG10\avgwdsvc.exe
O23 – Service: Intel® Quick Resume Technology Drivers (ELService) – Intel Corporation – C:\Program Files\Intel\IntelDH\Intel(R) Quick Resume Technology\ELService.exe
O23 – Service: Intel(R) Matrix Storage Event Monitor (IAANTMon) – Intel Corporation – C:\Program Files\Intel\Intel Matrix Storage Manager\iaantmon.exe
O23 – Service: Intel NCS NetService (NetSvc) – Intel(R) Corporation – C:\Program Files\Intel\PROSetWired\NCS\Sync\NetSvc.exe
O23 – Service: NVIDIA Display Driver Service (NVSvc) – NVIDIA Corporation – C:\WINDOWS\system32\nvsvc32.exe
O23 – Service: Trend Micro Central Control Component (PcCtlCom) – Unknown owner – C:\PROGRA~1\TRENDM~1\INTERN~1\PcCtlCom.exe (file missing)
O23 – Service: PnkBstrA – Unknown owner – C:\WINDOWS\system32\PnkBstrA.exe
O23 – Service: Trend Micro Real-time Service (Tmntsrv) – Unknown owner – C:\PROGRA~1\TRENDM~1\INTERN~1\Tmntsrv.exe (file missing)
O23 – Service: Trend Micro Personal Firewall (TmPfw) – Unknown owner – C:\PROGRA~1\TRENDM~1\INTERN~1\TmPfw.exe (file missing)
O23 – Service: Trend Micro Proxy Service (tmproxy) – Unknown owner – C:\PROGRA~1\TRENDM~1\INTERN~1\tmproxy.exe (file missing)
—
End of file – 6800 bytes
Thanks for your time.
Hi, thank you so much!!! with all your comments, expierence and suggestions i´m almost done with this annoying virus!!! you´re really helpful because i have no much idea of computers and following your instructions i could do it myself!!! many thanks to all!!!
Thank youuuuu so much for your help!!!!!!! it freaked me out when i got the virus… to learn how to unhide your files go to this link windows7themes.net/how-to-unhide-hidden-files-in-windows-7.html
After having removed the viruses/offending files, I cannot set anything as my desktop background. Is this related?
Also, several hours after the computer was fixed, my internet connection has been going in and out. Is this just a coincidence on the same day or could it be related?
Thanks.
Taran, looks like your computer is infected with a hidden trojan. To remove this malware, please ask for help in our Spyware removal forum.
Sally, try to check your computer with TDSSKiller and Kaspersky virus removal tool.
Just wanted to say a billion thanks for this very effective and easy to use guide for the removal(It at least looks like my computer is repaired) of the very, very vicious windows repair virus!!!!
I too have just gotten this Windows Repair virus. Except I am unable to even start my computer in safe mode. When tapping F8, nothing happens, the screen just stays black, or the virus starts anyway. I’ve tried to restart in safe mode manually by changing msconfig settings and now the computer is running but the screen is black. I cannot access anything.
Any suggestions??
I used malware aand unhid. I could not find a way to put my comp in safe mode. My files have returned but are not highlighted and there is still a Windows restore on my desktop. How can i correct this? Thanks!
Martin,
Im hoping you are still checking this board. I am having the same issue as you. It appears most of the virus is gone but I get that catalyst control error also. Did you find a fix for this?